|
Daemon (novel)
''Daemon'' is a 2006 novel by Daniel Suarez about a distributed persistent computer application that begins to change the real world after its original programmer's death. The story was concluded in a sequel, '' Freedom™'', in 2010. Plot Upon publication of the obituary for Matthew A. Sobol, a brilliant computer programmer and CTO of Cyberstorm Entertainment, a daemon is activated. When he was dying of brain cancer, he was fearful for humanity and began to envision a new world order. The Daemon becomes his tool to achieve that vision. The Daemon's first mission is to kill two programmers, Joseph Pavlos and Chopra Singh, who worked for CyberStorm Entertainment and unknowingly helped in the creation of the Daemon. The program secretly takes over hundreds of companies and provides financial and computing resources for recruiting real world agents and creating AutoM8s ( computer controlled driverless cars, used as transport and occasionally as weapons), Razorbacks (sword-wieldi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
WikiProject Novels
A WikiProject, or Wikiproject, is an affinity group for contributors with shared goals within the Wikimedia movement. WikiProjects are prevalent within the largest wiki, Wikipedia, and exist to varying degrees within Wikimedia project, sibling projects such as Wiktionary, Wikiquote, Wikidata, and Wikisource. They also exist in different languages, and translation of articles is a form of their collaboration. During the COVID-19 pandemic, CBS News noted the role of Wikipedia's WikiProject Medicine in maintaining the accuracy of articles related to the disease. Another WikiProject that has drawn attention is WikiProject Women Scientists, which was profiled by ''Smithsonian Magazine, Smithsonian'' for its efforts to improve coverage of women scientists which the profile noted had "helped increase the number of female scientists on Wikipedia from around 1,600 to over 5,000". On Wikipedia Some Wikipedia WikiProjects are substantial enough to engage in cooperative activities with outsi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Frame-up
In the United States criminal law, a frame-up (frameup) or setup is the act of falsely implicating (framing) someone in a crime by providing fabricated evidence or testimony. In British usage, to frame, stitch up, or fit-up, is to maliciously or dishonestly incriminate someone or set them up, in the sense trap or ensnare. While incriminating those who are innocent might be done out of sheer malice, framing is primarily used as a distraction. Generally, the person who is framing someone else is the actual perpetrator of the crime. In other cases it is an attempt by law enforcement to get around due process. Motives include getting rid of political dissidents or "correcting" what they see as the court's mistake. Some lawbreakers will try to claim they were framed as a defense strategy. Frameups may use conspiracy theories to hide the true crimes of the accused. Technique In labor disputes Frameups in labor disputes sometimes swing public opinion one way or the other. In Massac ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Propaganda
Propaganda is communication that is primarily used to influence or persuade an audience to further an agenda, which may not be objective and may be selectively presenting facts to encourage a particular synthesis or perception, or using loaded language to produce an emotional rather than a rational response to the information that is being presented. Propaganda can be found in a wide variety of different contexts. Beginning in the twentieth century, the English term ''propaganda'' became associated with a Psychological manipulation, manipulative approach, but historically, propaganda had been a neutral descriptive term of any material that promotes certain opinions or ideology, ideologies. A wide range of materials and media are used for conveying propaganda messages, which changed as new technologies were invented, including paintings, cartoons, posters, pamphlets, films, radio shows, TV shows, and websites. More recently, the digital age has given rise to new ways of dissemina ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
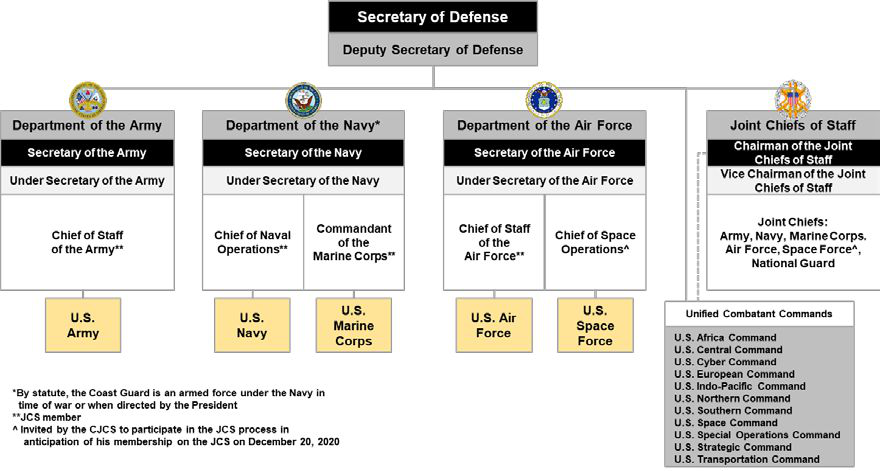
United States Department Of Defense
The United States Department of Defense (DoD, USDOD, or DOD) is an United States federal executive departments, executive department of the federal government of the United States, U.S. federal government charged with coordinating and supervising the six U.S. armed services: the United States Army, Army, United States Navy, Navy, United States Marine Corps, Marines, United States Air Force, Air Force, United States Space Force, Space Force, the United States Coast Guard, Coast Guard for some purposes, and related functions and agencies. As of November 2022, the department has over 1.4 million active-duty uniformed personnel in the six armed services. It also supervises over 778,000 National Guard (United States), National Guard and reservist personnel, and over 747,000 civilians, bringing the total to over 2.91 million employees. Headquartered at the Pentagon in Arlington County, Virginia, just outside Washington, D.C., the Department of Defense's stated mission is "to provid ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cybercrime
Cybercrime encompasses a wide range of criminal activities that are carried out using digital devices and/or Computer network, networks. It has been variously defined as "a crime committed on a computer network, especially the Internet"; Cybercriminals may exploit vulnerabilities in computer systems and networks to gain unauthorized access, steal sensitive information, disrupt services, and cause financial or reputational harm to individuals, organizations, and governments. In 2000, the tenth United Nations Congress on the Prevention of Crime and the Treatment of Offenders classified cyber crimes into five categories: unauthorized access, damage to computer data or programs, sabotage to hinder the functioning of a computer system or network, unauthorized interception of data within a system or network, and computer espionage. Internationally, both state and non-state actors engage in cybercrimes, including espionage, financial theft, and other cross-border crimes. Cybercrimes c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Identity Theft
Identity theft, identity piracy or identity infringement occurs when someone uses another's personal identifying information, like their name, identifying number, or credit card number, without their permission, to commit fraud or other crimes. The term ''identity theft'' was coined in 1964. Since that time, the definition of identity theft has been legally defined throughout both the UK and the United States, U.S. as the theft of personally identifiable information. Identity theft deliberately uses someone else's personally identifiable information, identity as a method to gain financial advantages or obtain credit and other benefits. The person whose identity has been stolen may suffer adverse consequences, especially if they are falsely held responsible for the perpetrator's actions. Personally identifiable information generally includes a person's name, date of birth, social security number, driver's license number, bank account or credit card numbers, Personal identification ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Gamer
A gamer is someone who plays interactive games, either video games, tabletop role-playing games, skill-based card games, or any combination thereof, and who often plays for extended periods of time. Originally a hobby, gaming has evolved into a profession for some, with some gamers routinely competing in games for money, prizes, or awards. In some countries, such as the US, UK, and Australia, the term "gaming" can refer to legalized gambling, which can take both traditional and digital forms, such as through online gambling. There are many different gamer communities around the world. Since the advent of the Internet, many communities take the form of Internet forums or YouTube or Twitch virtual communities, as well as in-person social clubs. In 2021, there were an estimated 3.24 billion gamers across the globe. Etymology The term ''gamer'' originally meant ''gambler'', and has been in use since at least 1422, when the town laws of Walsall, England, referred to "any dice ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Sociopath
Psychopathy, or psychopathic personality, is a personality construct characterized by impaired empathy and remorse, along with bold, disinhibited, and egocentric traits. These traits are often masked by superficial charm and immunity to stress, which create an outward appearance of apparent normalcy. Hervey M. Cleckley, an American psychiatrist, influenced the initial diagnostic criteria for antisocial personality reaction/disturbance in the ''Diagnostic and Statistical Manual of Mental Disorders'' (DSM), as did American psychologist George E. Partridge. The DSM and ''International Classification of Diseases'' (ICD) subsequently introduced the diagnoses of antisocial personality disorder (ASPD) and dissocial personality disorder (DPD) respectively, stating that these diagnoses have been referred to (or include what is referred to) as psychopathy or sociopathy. The creation of ASPD and DPD was driven by the fact that many of the classic traits of psychopathy were impossib ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptography
Cryptography, or cryptology (from "hidden, secret"; and ''graphein'', "to write", or ''-logy, -logia'', "study", respectively), is the practice and study of techniques for secure communication in the presence of Adversary (cryptography), adversarial behavior. More generally, cryptography is about constructing and analyzing Communication protocol, protocols that prevent third parties or the public from reading private messages. Modern cryptography exists at the intersection of the disciplines of mathematics, computer science, information security, electrical engineering, digital signal processing, physics, and others. Core concepts related to information security (confidentiality, data confidentiality, data integrity, authentication, and non-repudiation) are also central to cryptography. Practical applications of cryptography include electronic commerce, Smart card#EMV, chip-based payment cards, digital currencies, password, computer passwords, and military communications. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Red Herring
A red herring is something that misleads or distracts from a relevant or important question. It may be either a logical fallacy or a literary device that leads readers or audiences toward a false conclusion. A red herring may be used intentionally, as in mystery fiction or as part of rhetorical strategies (e.g., in politics), or may be used in argumentation inadvertently. The term was popularized in 1807 by English polemicist William Cobbett, who told a story of having used a strong-smelling smoked fish to divert and distract hounds from chasing a rabbit. Logical fallacy As an informal fallacy, the red herring falls into a broad class of relevance fallacies. Unlike the straw man, which involves a distortion of the other party's position, the red herring is a seemingly plausible, though ultimately irrelevant, diversionary tactic. According to the ''Oxford English Dictionary'', a red herring may be intentional or unintentional; it is not necessarily a conscious intent to mis ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
National Security Agency
The National Security Agency (NSA) is an intelligence agency of the United States Department of Defense, under the authority of the director of national intelligence (DNI). The NSA is responsible for global monitoring, collection, and processing of information and data for global intelligence and counterintelligence purposes, specializing in a discipline known as signals intelligence (SIGINT). The NSA is also tasked with the protection of U.S. communications networks and information systems. The NSA relies on a variety of measures to accomplish its mission, the majority of which are clandestine. The NSA has roughly 32,000 employees. Originating as a unit to decipher coded communications in World War II, it was officially formed as the NSA by President Harry S. Truman in 1952. Between then and the end of the Cold War, it became the largest of the U.S. intelligence organizations in terms of personnel and budget. Still, information available as of 2013 indicates that the C ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |