|
Crypt (C)
crypt is a C POSIX librar, POSIX C library function. It is typically used to compute the cryptographic hash function, hash of user account passwords. The function outputs a text string which also code, encodes the salt (cryptography), salt (usually the first two characters are the salt itself and the rest is the hashed result), and identifies the hash algorithm used Detailing to the Traditional one explained be This output string forms a password which is usually stored in a text file. More formally, crypt provides cryptographic key derivation functions for password validation and storage on Unix systems. Relationship to Unix crypt utility There is an unrelated Crypt (Unix), crypt utility in Unix, which is often confused with the C library function. To distinguish between the two, writers often refer to the utility program as ''crypt(1)'', because it is documented in section 1 of the Unix Manual page (Unix), manual pages, and refer to the C library function as ''crypt(3)'', be ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
C POSIX Librar
C, or c, is the third letter of the Latin alphabet, used in the modern English alphabet, the alphabets of other western European languages and others worldwide. Its name in English is ''cee'' (pronounced ), plural ''cees''. History "C" comes from the same letter as "G". The Semites named it gimel. The sign is possibly adapted from an Egyptian hieroglyph for a staff sling, which may have been the meaning of the name ''gimel''. Another possibility is that it depicted a camel, the Semitic name for which was ''gamal''. Barry B. Powell, a specialist in the history of writing, states "It is hard to imagine how gimel = "camel" can be derived from the picture of a camel (it may show his hump, or his head and neck!)". In the Etruscan language, plosive consonants had no contrastive voicing, so the Greek ' Γ' (Gamma) was adopted into the Etruscan alphabet to represent . Already in the Western Greek alphabet, Gamma first took a '' form in Early Etruscan, then '' in Classical E ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Base64
In computer programming, Base64 is a group of binary-to-text encoding schemes that transforms binary data into a sequence of printable characters, limited to a set of 64 unique characters. More specifically, the source binary data is taken 6 bits at a time, then this group of 6 bits is mapped to one of 64 unique characters. As with all binary-to-text encoding schemes, Base64 is designed to carry data stored in binary formats across channels that only reliably support text content. Base64 is particularly prevalent on the World Wide Web where one of its uses is the ability to embed image files or other binary assets inside textual assets such as HTML and CSS files. Base64 is also widely used for sending e-mail attachments, because SMTP – in its original form – was designed to transport 7-bit ASCII characters only. Encoding an attachment as Base64 before sending, and then decoding when received, assures older SMTP servers will not interfere with the attachment. Ba ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
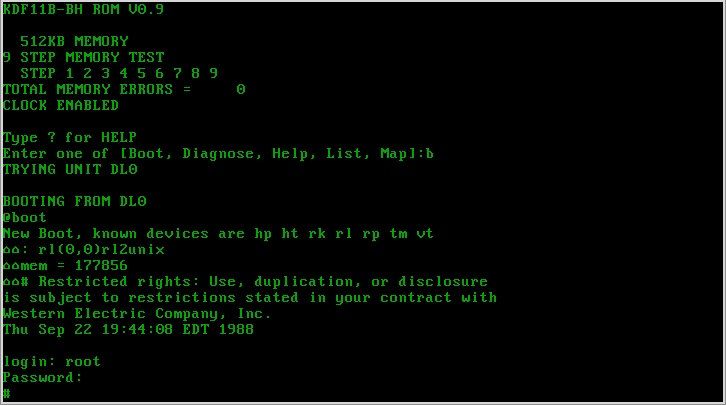
Seventh Edition Unix
Version 7 Unix, also called Seventh Edition Unix, Version 7 or just V7, was an important early release of the Unix operating system. V7, released in 1979, was the last Bell Laboratories release to see widespread distribution before the commercialization of Unix by AT&T Corporation in the early 1980s. V7 was originally developed for Digital Equipment Corporation's PDP-11 minicomputers and was later ported to other platforms. Overview Unix versions from Bell Labs were designated by the edition of the user's manual with which they were accompanied. Released in 1979, the Seventh Edition was preceded by Sixth Edition, which was the first version licensed to commercial users. Development of the Research Unix line continued with the Eighth Edition, which incorporated development from 4.1BSD, through the Tenth Edition, after which the Bell Labs researchers concentrated on developing Plan 9. V7 was the first readily portable version of Unix. As this was the era of minicomputers, wit ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Password
A password, sometimes called a passcode, is secret data, typically a string of characters, usually used to confirm a user's identity. Traditionally, passwords were expected to be memorized, but the large number of password-protected services that a typical individual accesses can make memorization of unique passwords for each service impractical. Using the terminology of the NIST Digital Identity Guidelines, the secret is held by a party called the ''claimant'' while the party verifying the identity of the claimant is called the ''verifier''. When the claimant successfully demonstrates knowledge of the password to the verifier through an established authentication protocol, the verifier is able to infer the claimant's identity. In general, a password is an arbitrary String (computer science), string of character (computing), characters including letters, digits, or other symbols. If the permissible characters are constrained to be numeric, the corresponding secret is sometimes ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
M-209
In cryptography, the M-209, designated CSP-1500 by the United States Navy (C-38 by the manufacturer) is a portable, mechanical cipher machine used by the US military primarily in World War II, though it remained in active use through the Korean War. The M-209 was designed by Swedish cryptographer Boris Hagelin in response to a request for such a portable cipher machine, and was an improvement of an earlier machine, the C-36 (cipher machine), C-36. The M-209 is about the size of a lunchbox, in its final form measuring and weighing (plus for the case). It represented a brilliant achievement for pre-electronic technology. It was a rotor machine similar to a telecipher machine, such as the Lorenz cipher and the Geheimfernschreiber. Basic operation Basic operation of the M-209 is relatively straightforward. Six adjustable ''key wheels'' on top of the box each display a letter of the alphabet. These six wheels comprise the external key (cryptography), key for the machine, providi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Yescrypt
yescrypt is a cryptographic key derivation function function used for password hashing on Fedora Linux, Debian, Ubuntu, and Arch Linux. The function is more resistant to offline password-cracking attacks than SHA-512. It is based on Scrypt. See also * crypt (C) crypt is a C POSIX librar, POSIX C library function. It is typically used to compute the cryptographic hash function, hash of user account passwords. The function outputs a text string which also code, encodes the salt (cryptography), salt (usual ... * Lyra2 * Password hashing * Password Hashing Competition References External links Project website Cryptographic hash functions {{Crypto-stub Key derivation functions ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
SHA-1
In cryptography, SHA-1 (Secure Hash Algorithm 1) is a hash function which takes an input and produces a 160-bit (20-byte) hash value known as a message digest – typically rendered as 40 hexadecimal digits. It was designed by the United States National Security Agency, and is a U.S. Federal Information Processing Standard. The algorithm has been cryptographically broken but is still widely used. Since 2005, SHA-1 has not been considered secure against well-funded opponents; as of 2010 many organizations have recommended its replacement. NIST formally deprecated use of SHA-1 in 2011 and disallowed its use for digital signatures in 2013, and declared that it should be phased out by 2030. , chosen-prefix attacks against SHA-1 are practical. As such, it is recommended to remove SHA-1 from products as soon as possible and instead use SHA-2 or SHA-3. Replacing SHA-1 is urgent where it is used for digital signatures. All major web browser vendors ceased acceptance of SHA-1 SSL certifi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
PBKDF1
In cryptography, PBKDF1 and PBKDF2 (Password-Based Key Derivation Function 1 and 2) are key derivation functions with a sliding computational cost, used to reduce vulnerability to brute-force attacks. PBKDF2 is part of RSA Laboratories' Public-Key Cryptography Standards (PKCS) series, specifically PKCS#5 v2.0, also published as Internet Engineering Task Force's RFC2898. It supersedes PBKDF1, which could only produce derived keys up to 160 bits long. RFC8018 (PKCS#5 v2.1), published in 2017, recommends PBKDF2 for password hashing. Purpose and operation PBKDF2 applies a pseudorandom function, such as hash-based message authentication code (HMAC), to the input password or passphrase along with a salt value and repeats the process many times to produce a ''derived key'', which can then be used as a cryptographic key in subsequent operations. The added computational work makes password cracking much more difficult, and is known as key stretching. When the standard was written in ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
SHA-256
SHA-2 (Secure Hash Algorithm 2) is a set of cryptographic hash functions designed by the United States National Security Agency (NSA) and first published in 2001. They are built using the Merkle–Damgård construction, from a one-way compression function itself built using the Davies–Meyer structure from a specialized block cipher. SHA-2 includes significant changes from its predecessor, SHA-1. The SHA-2 family consists of six hash functions with digests (hash values) that are 224, 256, 384 or 512 bits: SHA-224, SHA-256, SHA-384, SHA-512, SHA-512/224, SHA-512/256. SHA-256 and SHA-512 are hash functions whose digests are eight 32-bit and 64-bit words, respectively. They use different shift amounts and additive constants, but their structures are otherwise virtually identical, differing only in the number of rounds. SHA-224 and SHA-384 are truncated versions of SHA-256 and SHA-512 respectively, computed with different initial values. SHA-512/224 and SHA-512/256 are also trunc ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
PBKDF2
In cryptography, PBKDF1 and PBKDF2 (Password-Based Key Derivation Function 1 and 2) are key derivation functions with a sliding computational cost, used to reduce vulnerability to brute-force attacks. PBKDF2 is part of RSA Laboratories' Public-Key Cryptography Standards (PKCS) series, specifically PKCS#5 v2.0, also published as Internet Engineering Task Force's RFC2898. It supersedes PBKDF1, which could only produce derived keys up to 160 bits long. RFC8018 (PKCS#5 v2.1), published in 2017, recommends PBKDF2 for password hashing. Purpose and operation PBKDF2 applies a pseudorandom function, such as hash-based message authentication code (HMAC), to the input password or passphrase along with a salt value and repeats the process many times to produce a ''derived key'', which can then be used as a cryptographic key in subsequent operations. The added computational work makes password cracking much more difficult, and is known as key stretching. When the standard was written ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Scrypt
In cryptography, scrypt (pronounced "ess crypt") is a password-based key derivation function created by Colin Percival in March 2009, originally for the Tarsnap online backup service. The algorithm was specifically designed to make it costly to perform large-scale custom hardware attacks by requiring large amounts of memory. In 2016, the scrypt algorithm was published by Internet Engineering Task Force, IETF as RFC 7914. A simplified version of scrypt is used as a proof-of-work scheme by a number of Cryptocurrency, cryptocurrencies, first implemented by an anonymous programmer called ArtForz in Tenebrix and followed by Fairbrix and Litecoin soon after. Introduction A password-based key derivation function (password-based KDF) is generally designed to be computationally intensive, so that it takes a relatively long time to compute (say on the order of several hundred milliseconds). Legitimate users only need to perform the function once per operation (e.g., authentication), a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
NTLM Authentication
Integrated Windows Authentication (IWA) is a term associated with Microsoft products that refers to the SPNEGO, Kerberos, and NTLMSSP authentication protocols with respect to SSPI functionality introduced with Microsoft Windows 2000 and included with later Windows NT-based operating systems. The term is used more commonly for the automatically authenticated connections between Microsoft Internet Information Services, Internet Explorer, and other Active Directory aware applications. IWA is also known by several names like ''HTTP Negotiate authentication'', ''NT Authentication'', ''NTLM Authentication'', ''Domain authentication'', ''Windows Integrated Authentication'', ''Windows NT Challenge/Response authentication'', or simply ''Windows Authentication''. Overview Integrated Windows Authentication uses the security features of Windows clients and servers. Unlike Basic Authentication or Digest Authentication, initially, it does not prompt users for a user name and password. The c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |