|
CompTIA Linux
The Computing Technology Industry Association, more commonly known as CompTIA, is an American Industry trade group, trade association that issues temporary vendor-neutral professional certifications for the information technology (IT) industry. Certifications All certifications issued by CompTIA expire 3 years after obtainment, reissuance requires repurchase and retesting. However, certifications issued prior to January 1, 2011 do not expire.CompTIA Good-for-Life Certifications access date April 3, 2018. Almost all certifications have accreditation from the American National Standards Institute (ANSI) on dates valid from 2008 till 2028 available on the ANSI website. Basic certifications *IT Fundamentals+ (ITF+): ...[...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
|
Downers Grove, Illinois
Downers Grove is a village in DuPage County, Illinois, United States. It was founded in 1832 by Pierce Downer, whose surname serves as the eponym for the village. Per the 2020 United States census, 2020 census, the population of the village was 50,248. It is a south-western suburb of Chicago located between Interstate 88 (Illinois), I-88 and Interstate 55 in Illinois, I-55. History Downers Grove was founded in 1832 by Pierce Downer, a farmer who traveled to Illinois from Rutland, New York, but was originally from Vermont. Downers Grove was named for a lush grove of old-growth Quercus macrocarpa, bur oak trees surrounding the village, which stood out from the local Oak savanna, savanna landscape. Its other early settlers included the Blodgett, Curtiss, Blanchard, Stanley, Lyman, and Carpenter families. The original settlers were mostly migrants from the Northeastern United States and Northern Europe. In 1839, Reverend Orange Lyman, a presbyterian minister, and his wife Maria Dew ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
|
Penetration Test
A penetration test, colloquially known as a pentest, is an authorized simulated cyberattack on a computer system, performed to evaluate the security of the system; this is not to be confused with a vulnerability assessment. The test is performed to identify weaknesses (or vulnerabilities), including the potential for unauthorized parties to gain access to the system's features and data, as well as strengths, enabling a full risk assessment to be completed. The process typically identifies the target systems and a particular goal, then reviews available information and undertakes various means to attain that goal. A penetration test target may be a white box (about which background and system information are provided in advance to the tester) or a black box (about which only basic information other than the company name is provided). A gray box penetration test is a combination of the two (where limited knowledge of the target is shared with the auditor). A penetration test ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
|
Payment Card Industry Data Security Standard
The Payment Card Industry Data Security Standard (PCI DSS) is an information security standard used to handle credit cards from major card brands. The standard is administered by the Payment Card Industry Security Standards Council, and its use is mandated by the card brands. It was created to better control cardholder data and reduce credit card fraud. Validation of compliance is performed annually or quarterly with a method suited to the volume of transactions: * Self-assessment questionnaire (SAQ) * Firm-specific Internal Security Assessor (ISA) * External Qualified Security Assessor (QSA) History The major card brands had five different security programs: * Visa's Cardholder Information Security Program * Mastercard's Site Data Protection *American Express's Data Security Operating Policy * Discover's Information Security and Compliance * JCB's Data Security Program The intentions of each were roughly similar: to create an additional level of protection for card issuers ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
 |
National Institute Of Standards And Technology
The National Institute of Standards and Technology (NIST) is an agency of the United States Department of Commerce whose mission is to promote American innovation and industrial competitiveness. NIST's activities are organized into Outline of physical science, physical science laboratory programs that include Nanotechnology, nanoscale science and technology, engineering, information technology, neutron research, material measurement, and physical measurement. From 1901 to 1988, the agency was named the National Bureau of Standards. History Background The Articles of Confederation, ratified by the colonies in 1781, provided: The United States in Congress assembled shall also have the sole and exclusive right and power of regulating the alloy and value of coin struck by their own authority, or by that of the respective states—fixing the standards of weights and measures throughout the United States. Article 1, section 8, of the Constitution of the United States, ratified i ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
Trustmark (commerce)
A trustmark is an image, logo, or badge that is typically displayed on an E-commerce website, indicating that the site has passed certain digital security tests or is operated by a member of a professional organization. The trustmark is intended to show approval of the brand by a recognizable third party. Customers gain confidence and may be more inclined to transact business with a brand bearing a trustmark. One of the oldest familiar trustmarks, the Good Housekeeping Seal of Approval, was established in 1909 as a way for the magazine's Research Institute to endorse specific products backed by a two-year warranty. In the modern era, digital trustmarks can be a machine-readable authentication feature within an identity trust framework. In the United Kingdom since 2006, there is a non-profit entity called TrustMark that under a master agreement from the Department for Business, Energy and Industrial Strategy licenses and audits businesses that register to carry out work inside and ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
|
Technical Trainer
A technical trainer is an educator or teacher who trains or coaches others in some field of technology. The task requires a certain set of competencies, but many technical trainers do not hold specific technical-training qualifications. Although there are professional organizations and publications of relevance to technical trainers, few of these are specifically focused on that profession. Types of technical trainers Although a generic professional description can be applied to all technical trainers, as is true of any profession, many specializations exist. These include information technology topics such as Computer applications and Computer Architecture and Design; biomedical technology; educational technology; Aerospace technology; and topics in the field of engineering. History The need for technical training existed before computers or even electronics, but the term "technical trainer" has only been in the common lexicon since the mid-20th century. For example, RAF ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
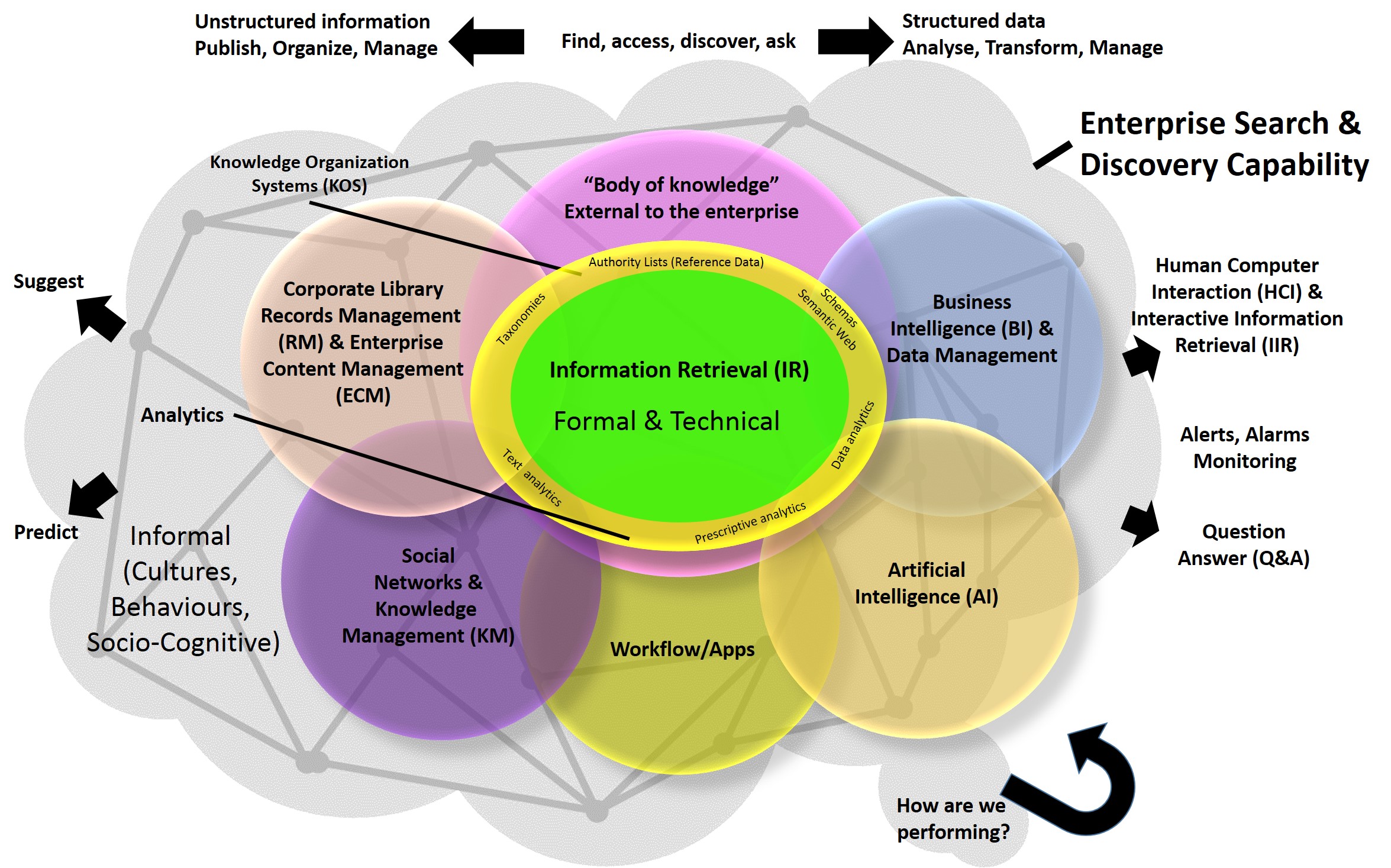 |
Enterprise Content Management
Enterprise content management (ECM) extends the concept of content management by adding a timeline for each content item and, possibly, enforcing processes for its creation, approval, and distribution. Systems using ECM generally provide a secure repository for managed items, analog or digital. They also include one (or more) methods for importing content to manage new items, and several presentation methods to make items available for use. Although ECM content may be protected by digital rights management (DRM), it is not required. ECM is distinguished from general content management by its cognizance of the processes and procedures of the enterprise for which it is created. Definitions * Late 2005: The technology was used to capture, manage, store, preserve, and deliver content and documents related to organizational processes * Early 2006: ECM tools and strategies allowed the management of an organization's unstructured information, wherever that information exists. * Early 2 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |