|
Cascade (computer Virus)
The Cascade virus (also known as ''Herbstlaub'', "autumn leaves" in Germany) is a prominent computer virus that was a resident written in assembly language, that was widespread in the 1980s and early 1990s. It infected .COM files and had the effect of making text on the screen fall (or cascade) down and form a heap at the bottom of the screen. It was notable for using an encryption algorithm to avoid being detected. However, one could see that infected files had their size increased by 1701 or 1704 bytes. In response, IBM developed its own antivirus software Antivirus software (abbreviated to AV software), also known as anti-malware, is a computer program used to prevent, detect, and remove malware. Antivirus software was originally developed to detect and remove computer viruses, hence the name .... The virus has a number of variants. Cascade-17Y4, which is reported to have originated in Yugoslavia, is almost identical to the most common 1704 byte variant. One byte has b ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
 |
Computer Virus
A computer virus is a type of malware that, when executed, replicates itself by modifying other computer programs and Code injection, inserting its own Computer language, code into those programs. If this replication succeeds, the affected areas are then said to be "infected" with a computer virus, a metaphor derived from biological viruses. Computer viruses generally require a Computer program, host program. The virus writes its own code into the host program. When the program runs, the written virus program is executed first, causing infection and damage. By contrast, a computer worm does not need a host program, as it is an independent program or code chunk. Therefore, it is not restricted by the Computer program, host program, but can run independently and actively carry out attacks. Virus writers use social engineering (security), social engineering deceptions and exploit detailed knowledge of vulnerability (computing), security vulnerabilities to initially infect systems an ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
 |
Malware
Malware (a portmanteau of ''malicious software'')Tahir, R. (2018)A study on malware and malware detection techniques . ''International Journal of Education and Management Engineering'', ''8''(2), 20. is any software intentionally designed to cause disruption to a computer, server (computing), server, Client (computing), client, or computer network, leak private information, gain unauthorized access to information or systems, deprive access to information, or which unknowingly interferes with the user's computer security and privacy. Researchers tend to classify malware into one or more sub-types (i.e. computer viruses, Computer worm, worms, Trojan horse (computing), Trojan horses, logic bombs, ransomware, spyware, adware, rogue software, Wiper (malware), wipers and keyloggers). Malware poses serious problems to individuals and businesses on the Internet. According to NortonLifeLock, Symantec's 2018 Internet Security Threat Report (ISTR), malware variants number has increased to 66 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
Assembly Language
In computing, assembly language (alternatively assembler language or symbolic machine code), often referred to simply as assembly and commonly abbreviated as ASM or asm, is any low-level programming language with a very strong correspondence between the instructions in the language and the architecture's machine code instructions. Assembly language usually has one statement per machine instruction (1:1), but constants, comments, assembler directives, symbolic labels of, e.g., memory locations, registers, and macros are generally also supported. The first assembly code in which a language is used to represent machine code instructions is found in Kathleen and Andrew Donald Booth's 1947 work, ''Coding for A.R.C.''. Assembly code is converted into executable machine code by a utility program referred to as an '' assembler''. The term "assembler" is generally attributed to Wilkes, Wheeler and Gill in their 1951 book '' The Preparation of Programs for an Electronic Dig ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
 |
IBM Personal Computer
The IBM Personal Computer (model 5150, commonly known as the IBM PC) is the first microcomputer released in the IBM PC model line and the basis for the IBM PC compatible ''de facto'' standard. Released on August 12, 1981, it was created by a team of engineers and designers at International Business Machines (IBM), directed by William C. Lowe and Philip Don Estridge in Boca Raton, Florida. Powered by an x86-architecture Intel 8088 processor, the machine was based on open architecture and third-party peripherals. Over time, expansion cards and software technology increased to support it. The PC had a substantial influence on the personal computer market; the specifications of the IBM PC became one of the most popular computer design standards in the world. The only significant competition it faced from a non-compatible platform throughout the 1980s was from Apple's Macintosh product line, as well as consumer-grade platforms created by companies like Commodore and Atari. Mo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
 |
IBM PC Compatibles
An IBM PC compatible is any personal computer that is hardware- and software-compatible with the IBM Personal Computer (IBM PC) and its subsequent models. Like the original IBM PC, an IBM PC–compatible computer uses an x86-based central processing unit, sourced either from Intel or a second source like AMD, Cyrix or other vendors such as Texas Instruments, Fujitsu, OKI, Mitsubishi or NEC and is capable of using interchangeable commodity hardware such as expansion cards. Initially such computers were referred to as PC clones, IBM clones or IBM PC clones, but the term "IBM PC compatible" is now a historical description only, as the vast majority of microcomputers produced since the 1990s are IBM compatible. IBM itself no longer sells personal computers, having sold its division to Lenovo in 2005. "Wintel" is a similar description that is more commonly used for modern computers. The designation "PC", as used in much of personal computer history, has not meant "personal c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
 |
Autumn
Autumn, also known as fall (especially in US & Canada), is one of the four temperate seasons on Earth. Outside the tropics, autumn marks the transition from summer to winter, in September (Northern Hemisphere) or March ( Southern Hemisphere). Autumn is the season when the duration of daylight becomes noticeably shorter and the temperature cools considerably. Day length decreases and night length increases as the season progresses until the winter solstice in December (Northern Hemisphere) and June (Southern Hemisphere). One of its main features in temperate climates is the striking change in colour of the leaves of deciduous trees as they prepare to shed. Date definitions Some cultures regard the autumnal equinox as "mid-autumn", while others with a longer temperature lag treat the equinox as the start of autumn. In the English-speaking world of high latitude countries, autumn traditionally began with Lammas Day and ended around Hallowe'en, the approximate mid-poin ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
 |
Computer Virus
A computer virus is a type of malware that, when executed, replicates itself by modifying other computer programs and Code injection, inserting its own Computer language, code into those programs. If this replication succeeds, the affected areas are then said to be "infected" with a computer virus, a metaphor derived from biological viruses. Computer viruses generally require a Computer program, host program. The virus writes its own code into the host program. When the program runs, the written virus program is executed first, causing infection and damage. By contrast, a computer worm does not need a host program, as it is an independent program or code chunk. Therefore, it is not restricted by the Computer program, host program, but can run independently and actively carry out attacks. Virus writers use social engineering (security), social engineering deceptions and exploit detailed knowledge of vulnerability (computing), security vulnerabilities to initially infect systems an ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
Assembly Language
In computing, assembly language (alternatively assembler language or symbolic machine code), often referred to simply as assembly and commonly abbreviated as ASM or asm, is any low-level programming language with a very strong correspondence between the instructions in the language and the architecture's machine code instructions. Assembly language usually has one statement per machine instruction (1:1), but constants, comments, assembler directives, symbolic labels of, e.g., memory locations, registers, and macros are generally also supported. The first assembly code in which a language is used to represent machine code instructions is found in Kathleen and Andrew Donald Booth's 1947 work, ''Coding for A.R.C.''. Assembly code is converted into executable machine code by a utility program referred to as an '' assembler''. The term "assembler" is generally attributed to Wilkes, Wheeler and Gill in their 1951 book '' The Preparation of Programs for an Electronic Dig ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
 |
COM File
A COM file is a type of simple executable file. On the Digital Equipment Corporation (DEC) VAX operating systems of the 1970s, .COM was used as a filename extension for text files containing commands to be issued to the operating system (similar to a batch file). With the introduction of Digital Research's CP/M (a microcomputer operating system modeled after TOPS-10 for the PDP-10), the type of files commonly associated with COM extension changed to that of executable files. This convention was later carried over to DOS. Even when complemented by the more general .exe, EXE file format for executables, the compact COM files remained viable and frequently used under DOS. The .COM file name extension has no relation to the .com (for "commercial") top-level Internet domain name. However, this similarity in name has been exploited by malware writers. DOS binary format The COM format is the original binary executable format used in CP/M (including SCP (operating system), SCP and M ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
Encryption
In Cryptography law, cryptography, encryption (more specifically, Code, encoding) is the process of transforming information in a way that, ideally, only authorized parties can decode. This process converts the original representation of the information, known as plaintext, into an alternative form known as ciphertext. Despite its goal, encryption does not itself prevent interference but denies the intelligible content to a would-be interceptor. For technical reasons, an encryption scheme usually uses a pseudo-random encryption Key (cryptography), key generated by an algorithm. It is possible to decrypt the message without possessing the key but, for a well-designed encryption scheme, considerable computational resources and skills are required. An authorized recipient can easily decrypt the message with the key provided by the originator to recipients but not to unauthorized users. Historically, various forms of encryption have been used to aid in cryptography. Early encryption ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
 |
Antivirus Software
Antivirus software (abbreviated to AV software), also known as anti-malware, is a computer program used to prevent, detect, and remove malware. Antivirus software was originally developed to detect and remove computer viruses, hence the name. However, with the proliferation of other malware, antivirus software started to protect against other computer threats. Some products also include protection from malicious URLs, spam, and phishing. History 1971–1980 period (pre-antivirus days) The first known computer virus appeared in 1971 and was dubbed the " Creeper virus". This computer virus infected Digital Equipment Corporation's ( DEC) PDP-10 mainframe computers running the TENEX operating system.From the first email to the first YouTube video: a d ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
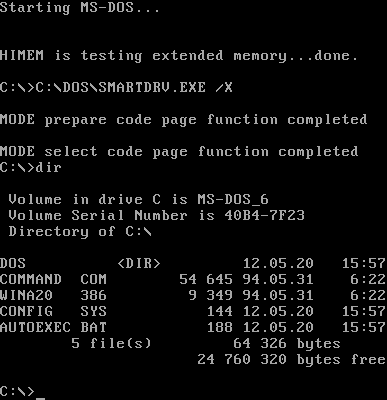 |
DOS File Viruses
DOS (, ) is a family of disk-based operating systems for IBM PC compatible computers. The DOS family primarily consists of IBM PC DOS and a rebranded version, Microsoft's MS-DOS, both of which were introduced in 1981. Later compatible systems from other manufacturers include DR-DOS (1988), ROM-DOS (1989), PTS-DOS (1993), and FreeDOS (1994). MS-DOS dominated the IBM PC compatible market between 1981 and 1995. Although the name has come to be identified specifically with MS-DOS and compatible operating systems, ''DOS'' is a platform-independent acronym for ''disk operating system'', whose use predates the IBM PC. Dozens of other operating systems also use the acronym, beginning with the mainframe DOS/360 from 1966. Others include Apple DOS, Apple ProDOS, Atari DOS, Commodore DOS, TRSDOS, and AmigaDOS. History Origins IBM PC DOS (and the separately sold MS-DOS) and its predecessor, 86-DOS, ran on Intel 8086 16-bit processors. It was developed to be similar to Digi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |