|
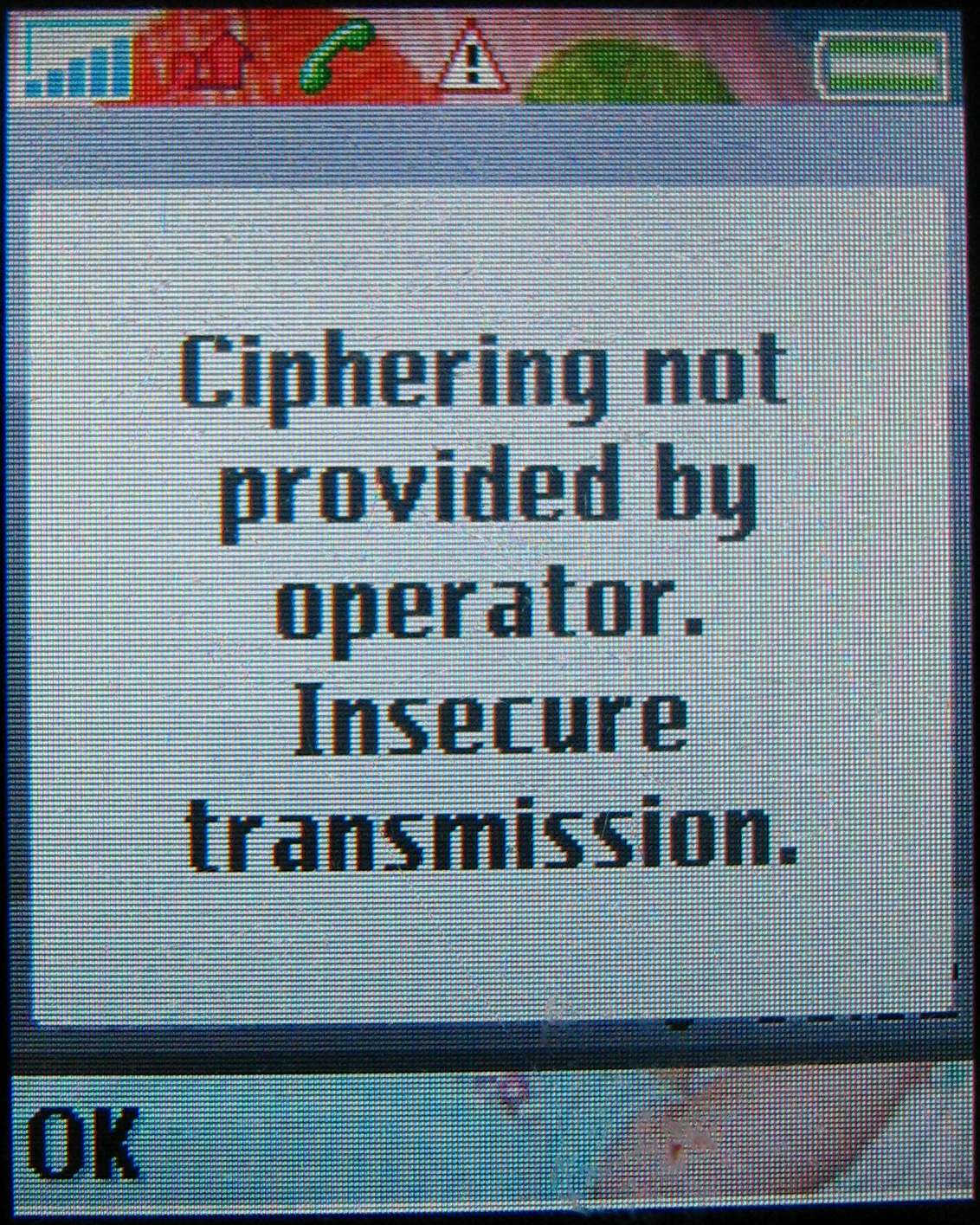
CMEA (cipher)
In cryptography, the Cellular Message Encryption Algorithm (CMEA) is a block cipher which was used for securing mobile phones in the United States. CMEA is one of four cryptographic primitives specified in a Telecommunications Industry Association (TIA) standard, and is designed to encrypt the control channel, rather than the voice data. In 1997, a group of cryptographers published attacks on the cipher showing it had several weaknesses which give it a trivial effective strength of a 24-bit to 32-bit cipher. Some accusations were made that the NSA had pressured the original designers into crippling CMEA, but the NSA has denied any role in the design or selection of the algorithm. The ECMEA and SCEMA ciphers are derived from CMEA. CMEA is described in . It is byte-oriented, with variable block size, typically 2 to 6 bytes. The key size is only 64 bits. Both of these are unusually small for a modern cipher. The algorithm consists of only 3 passes over the data: a non-linear left- ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
James A
James may refer to: People * James (given name) * James (surname) * James (musician), aka Faruq Mahfuz Anam James, (born 1964), Bollywood musician * James, brother of Jesus * King James (other), various kings named James * Prince James (other) * Saint James (other) Places Canada * James Bay, a large body of water * James, Ontario United Kingdom * James College, York, James College, a college of the University of York United States * James, Georgia, an unincorporated community * James, Iowa, an unincorporated community * James City, North Carolina * James City County, Virginia ** James City (Virginia Company) ** James City Shire * James City, Pennsylvania * St. James City, Florida Film and television * James (2005 film), ''James'' (2005 film), a Bollywood film * James (2008 film), ''James'' (2008 film), an Irish short film * James (2022 film), ''James'' (2022 film), an Indian Kannada-language film * "James", a television Adventure Time (season 5)#ep42, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
PostScript
PostScript (PS) is a page description language and dynamically typed, stack-based programming language. It is most commonly used in the electronic publishing and desktop publishing realm, but as a Turing complete programming language, it can be used for many other purposes as well. PostScript was created at Adobe Systems by John Warnock, Charles Geschke, Doug Brotz, Ed Taft and Bill Paxton from 1982 to 1984. The most recent version, PostScript 3, was released in 1997. History The concepts of the PostScript language were seeded in 1976 by John Gaffney at Evans & Sutherland, a computer graphics company. At that time, Gaffney and John Warnock were developing an interpreter for a large three-dimensional graphics database of New York Harbor. Concurrently, researchers at Xerox PARC had developed the first laser printer and had recognized the need for a standard means of defining page images. In 1975–76 Bob Sproull and William Newman developed the Press format, whic ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
ORYX
''Oryx'' ( ) is a genus consisting of four large antelope species called oryxes. Their pelage is pale with contrasting dark markings in the face and on the legs, and their long horns are almost straight and annulated. The exception is the scimitar oryx, which lacks dark markings on the legs, only has faint dark markings on the head, has an ochre neck, and has horns that are clearly decurved. All oryx species prefer near-desert conditions and can survive without water for long periods. The Arabian oryx was only saved from extinction through a captive-breeding program and reintroduction to the wild. The scimitar oryx, which was listed as extinct in the wild, also relied on a captive-breeding program for its survival.Database entry includes justification for why this species is listed as extinct in the wild. Etymology The term "oryx" comes from the Greek word ''óryx'' meaning "pickaxe", because its long and pointed horns look similar to the tool's end. The Greek plural f ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
A5/1
A5/1 is a stream cipher used to provide over-the-air communication privacy in the Global System for Mobile Communications, GSM Cell phone, cellular telephone standard. It is one of several implementations of the A5 security protocol. It was initially kept secret, but became public knowledge through leaks and reverse engineering. A number of serious weaknesses in the cipher have been identified. History and usage A5/1 is used in Europe and the United States. A5/2 was a deliberate weakening of the algorithm for certain export regions. A5/1 was developed in 1987, when GSM was not yet considered for use outside Europe, and A5/2 was developed in 1989. Though both were initially kept secret, the general design was leaked in 1994 and the algorithms were entirely reverse engineered in 1999 by Marc Briceno from a GSM telephone. In 2000, around 130 million GSM customers relied on A5/1 to protect the confidentiality of their voice communications. Security researcher Ross J. Anderson, Ross And ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Known-plaintext Attack
The known-plaintext attack (KPA) is an attack model for cryptanalysis where the attacker has access to both the plaintext (called a crib) and its encrypted version (ciphertext). These can be used to reveal secret keys and code books. The term "crib" originated at Bletchley Park, the British World War II decryption operation, where it was defined as: History The usage "crib" was adapted from a slang term referring to cheating (e.g., "I cribbed my answer from your test paper"). A "crib" originally was a literal or interlinear translation of a foreign-language text—usually a Latin or Greek text—that students might be assigned to translate from the original language. The idea behind a crib is that cryptologists were looking at incomprehensible ciphertext, but if they had a clue about some word or phrase that might be expected to be in the ciphertext, they would have a "wedge," a test to break into it. If their otherwise random attacks on the cipher managed to sometimes produce ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Chosen-plaintext Attack
A chosen-plaintext attack (CPA) is an attack model for cryptanalysis which presumes that the attacker can obtain the ciphertexts for arbitrary plaintexts.Ross Anderson, ''Security Engineering: A Guide to Building Dependable Distributed Systems''. The first edition (2001): http://www.cl.cam.ac.uk/~rja14/book.html The goal of the attack is to gain information that reduces the security of the encryption scheme. Modern ciphers aim to provide semantic security, also known as ''ciphertext indistinguishability under chosen-plaintext attack'', and they are therefore, by design, generally immune to chosen-plaintext attacks if correctly implemented. Introduction In a chosen-plaintext attack the adversary can (possibly adaptively) ask for the ciphertexts of arbitrary plaintext messages. This is formalized by allowing the adversary to interact with an encryption oracle, viewed as a black box. The attacker’s goal is to reveal all or a part of the secret encryption key. It may seem infe ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Involution (mathematics)
In mathematics, an involution, involutory function, or self-inverse function is a function that is its own inverse, : for all in the domain of . Equivalently, applying twice produces the original value. General properties Any involution is a bijection. The identity map is a trivial example of an involution. Examples of nontrivial involutions include negation (), reciprocation (), and complex conjugation () in arithmetic; reflection, half-turn rotation, and circle inversion in geometry; complementation in set theory; and reciprocal ciphers such as the ROT13 transformation and the Beaufort polyalphabetic cipher. The composition of two involutions and is an involution if and only if they commute: . Involutions on finite sets The number of involutions, including the identity involution, on a set with elements is given by a recurrence relation found by Heinrich August Rothe in 1800: : a_0 = a_1 = 1 and a_n = a_ + (n - 1)a_ for n > 1. The first few terms of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Lookup Table
In computer science, a lookup table (LUT) is an array data structure, array that replaces runtime (program lifecycle phase), runtime computation of a mathematical function (mathematics), function with a simpler array indexing operation, in a process termed as ''direct addressing''. The savings in processing time can be significant, because retrieving a value from memory is often faster than carrying out an "expensive" computation or input/output operation. The tables may be precomputation, precalculated and stored in static memory allocation, static program storage, calculated (or prefetcher, "pre-fetched") as part of a program's initialization phase (''memoization''), or even stored in hardware in application-specific platforms. Lookup tables are also used extensively to validate input values by matching against a list of valid (or invalid) items in an array and, in some programming languages, may include pointer functions (or offsets to labels) to process the matching input. Fiel ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Key Size
In cryptography, key size or key length refers to the number of bits in a key used by a cryptographic algorithm (such as a cipher). Key length defines the upper-bound on an algorithm's security (i.e. a logarithmic measure of the fastest known attack against an algorithm), because the security of all algorithms can be violated by brute-force attacks. Ideally, the lower-bound on an algorithm's security is by design equal to the key length (that is, the algorithm's design does not detract from the degree of security inherent in the key length). Most symmetric-key algorithms are designed to have security equal to their key length. However, after design, a new attack might be discovered. For instance, Triple DES was designed to have a 168-bit key, but an attack of complexity 2112 is now known (i.e. Triple DES now only has 112 bits of security, and of the 168 bits in the key the attack has rendered 56 'ineffective' towards security). Nevertheless, as long as the security (understood ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Block Size (cryptography)
In modern cryptography, symmetric key ciphers are generally divided into stream ciphers and block ciphers. Block ciphers operate on a fixed length string of bits. The length of this bit string is the block size. Both the input ( plaintext) and output (ciphertext) are the same length; the output cannot be shorter than the input this follows logically from the pigeonhole principle and the fact that the cipher must be reversibleand it is undesirable for the output to be longer than the input. Until the announcement of NIST's AES contest, the majority of block ciphers followed the example of the DES in using a block size of 64 bits (8 bytes). However, the birthday paradox In probability theory, the birthday problem asks for the probability that, in a set of randomly chosen people, at least two will share the same birthday. The birthday paradox is the counterintuitive fact that only 23 people are needed for that ... indicates that after accumulating several blocks equal ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Byte-oriented
Byte-oriented framing protocol is "a communications protocol in which full bytes are used as control codes. Also known as character-oriented protocol." For example UART communication is byte-oriented. The term "character-oriented" is deprecated, since the notion of character has changed. An ASCII character fits to one byte (octet) in terms of the amount of information. With the internationalization of computer software, wide characters became necessary, to handle texts in different languages. In particular, Unicode characters (or strictly speaking code points) can be 1, 2, 3 or 4 bytes in UTF-8, and other encodings of Unicode use two or four bytes per code point. See also * Bit-oriented protocol A bit-oriented protocol is a communications protocol that sees the transmitted data as an ''opaque'' stream of bits with no semantics, or meaning. Control codes are defined in terms of bit sequences instead of characters. Bit oriented protocol can ... References Data transmission [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |