|
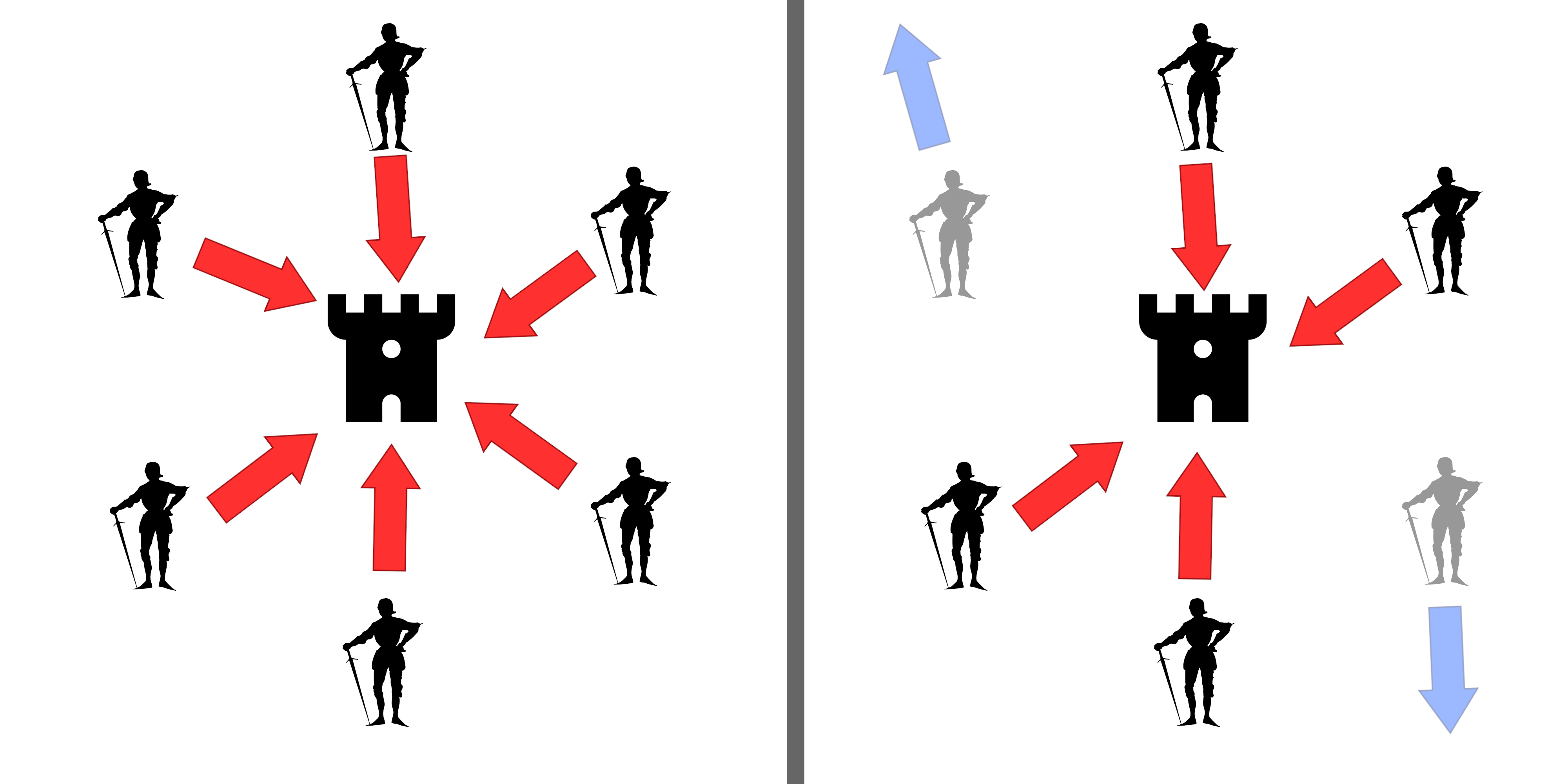
Byzantine Generals
A Byzantine fault is a condition of a system, particularly a distributed computing system, where a fault occurs such that different symptoms are presented to different observers, including imperfect information on whether a system component has failed. The term takes its name from an allegory, the "Byzantine generals problem", developed to describe a situation in which, to avoid catastrophic failure of a system, the system's actors must agree on a strategy, but some of these actors are unreliable in such a way as to cause other (good) actors to disagree on the strategy and they may be unaware of the disagreement. A Byzantine fault is also known as a Byzantine generals problem, a Byzantine agreement problem, or a Byzantine failure. Byzantine fault tolerance (BFT) is the resilience of a fault-tolerant computer system or similar system to such conditions. Definition A Byzantine fault is any fault presenting different symptoms to different observers. A Byzantine failure is the los ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Distributed Computing
Distributed computing is a field of computer science that studies distributed systems, defined as computer systems whose inter-communicating components are located on different networked computers. The components of a distributed system communicate and coordinate their actions by passing messages to one another in order to achieve a common goal. Three significant challenges of distributed systems are: maintaining concurrency of components, overcoming the lack of a global clock, and managing the independent failure of components. When a component of one system fails, the entire system does not fail. Examples of distributed systems vary from SOA-based systems to microservices to massively multiplayer online games to peer-to-peer applications. Distributed systems cost significantly more than monolithic architectures, primarily due to increased needs for additional hardware, servers, gateways, firewalls, new subnets, proxies, and so on. Also, distributed systems are prone to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Security
Security is protection from, or resilience against, potential harm (or other unwanted coercion). Beneficiaries (technically referents) of security may be persons and social groups, objects and institutions, ecosystems, or any other entity or phenomenon vulnerable to unwanted change. Security mostly refers to protection from hostile forces, but it has a wide range of other senses: for example, as the absence of harm (e.g., freedom from want); as the presence of an essential good (e.g., food security); as resilience against potential damage or harm (e.g. secure foundations); as secrecy (e.g., a secure telephone line); as containment (e.g., a secure room or cell); and as a state of mind (e.g., emotional security). Security is both a feeling and a state of reality. One might feel secure when one is not actually so; or might feel insecure despite being safe. This distinction is usually not very clear to express in the English language. The term is also used to refer to acts ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Fault Coverage
Fault coverage refers to the percentage of some type of fault that can be detected during the test of any engineered system. High fault coverage is particularly valuable during manufacturing test, and techniques such as Design For Test (DFT) and automatic test pattern generation are used to increase it. Applications Digital electronics In digital electronics, fault coverage refers to stuck-at fault coverage.{{Cite book , last=Williams , first=Thomas W. , title=How Should Fault Coverage Be Defined? , last2=Sunter , first2=Stephen K. , publisher=18th IEEE VLSI Test Symposium (VTS 2000), 30 April - 4 May 2000, Montreal, Canada , year=2000 , pages=325-328 , doi=10.1109/VTS.2000.10003 It is measured by sticking each pin of the hardware model at logic '0' and logic '1', respectively, and running the test vectors. If at least one of the outputs differs from what is to be expected, the fault is said to be detected. Conceptually, the total number of simulation runs is twice the numbe ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
NASA
The National Aeronautics and Space Administration (NASA ) is an independent agencies of the United States government, independent agency of the federal government of the United States, US federal government responsible for the United States's civil list of government space agencies, space program, aeronautics research and outer space, space research. National Aeronautics and Space Act, Established in 1958, it succeeded the National Advisory Committee for Aeronautics (NACA) to give the American space development effort a distinct civilian orientation, emphasizing peaceful applications in space science. It has since led most of America's space exploration programs, including Project Mercury, Project Gemini, the 1968–1972 Apollo program missions, the Skylab space station, and the Space Shuttle. Currently, NASA supports the International Space Station (ISS) along with the Commercial Crew Program and oversees the development of the Orion (spacecraft), Orion spacecraft and the Sp ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
International Conference On Distributed Computing Systems
The International Conference on Distributed Computing Systems (ICDCS) is the oldest conference in the field of distributed computing systems in the world. It was launched by the IEEE Computer Society Technical Committee on Distributed Processing (TCDP) in October 1979, and is sponsored by such committee. It was started as an 18-month conference until 1983 and became an annual conference since 1984. The ICDCS has a long history of significant achievements and worldwide visibility, and has recently celebrated its 37th year. Location history * 2019: Dallas, Texas, United States * 2018: Vienna, Austria * 2017: Atlanta, GA, United States * 2016: Nara, Japan * 2015: Columbus, Ohio, United States * 2014: Madrid, Spain * 2013: Philadelphia, Pennsylvania, United States * 2012: Macau, China * 2011: Minneapolis, Minnesota, United States * 2010: Genoa, Italy * 2009: Montreal, Quebec, Canada * 2008: Beijing, China * 2007: Toronto, Ontario, Canada * 2006: Lisbon, Portugal * 2005: Columbus, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
USENIX
USENIX is an American 501(c)(3) nonprofit membership organization based in Berkeley, California and founded in 1975 that supports advanced computing systems, operating system (OS), and computer networking research. It organizes several conferences in these fields. History USENIX was established in 1975 under the name "Unix Users Group," focusing primarily on the study and development of the Unix OS family and similar systems. In June 1977, a lawyer from AT&T Corporation informed the group that they could not use the word "Unix" in their name as it was a trademark of Western Electric (the manufacturing arm of AT&T until 1995), which led to the change of name to USENIX. Since its founding, it has published a technical journal titled '' ;login:''. USENIX was started as a technical organization. As commercial interest grew, a number of separate groups started in parallel, most notably the Software Tools Users Group (STUG), a technical adjunct for Unix-like tools and interfac ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Association For Computing Machinery
The Association for Computing Machinery (ACM) is a US-based international learned society for computing. It was founded in 1947 and is the world's largest scientific and educational computing society. The ACM is a non-profit professional membership group, reporting nearly 110,000 student and professional members . Its headquarters are in New York City. The ACM is an umbrella organization for academic and scholarly interests in computer science (informatics). Its motto is "Advancing Computing as a Science & Profession". History In 1947, a notice was sent to various people: On January 10, 1947, at the Symposium on Large-Scale Digital Calculating Machinery at the Harvard computation Laboratory, Professor Samuel H. Caldwell of Massachusetts Institute of Technology spoke of the need for an association of those interested in computing machinery, and of the need for communication between them. ..After making some inquiries during May and June, we believe there is ample interest to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Barbara Liskov
Barbara Liskov (born November 7, 1939, as Barbara Jane Huberman) is an American computer scientist who has made pioneering contributions to programming languages and distributed computing. Her notable work includes the introduction of abstract data types and the accompanying principle of data abstraction, along with the Liskov substitution principle, which applies these ideas to object-oriented programming, subtyping, and inheritance. Her work was recognized with the 2008 Turing Award, the highest distinction in computer science. Liskov is one of the earliest women to have been granted a doctorate in computer science in the United States, and the second woman to receive the Turing award. She is currently an Institute Professor and Ford Professor of Engineering at the Massachusetts Institute of Technology.Barbara Liskov Programming Methodology Grou ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cyclic Redundancy Check
A cyclic redundancy check (CRC) is an error-detecting code commonly used in digital networks and storage devices to detect accidental changes to digital data. Blocks of data entering these systems get a short ''check value'' attached, based on the remainder of a polynomial division of their contents. On retrieval, the calculation is repeated and, in the event the check values do not match, corrective action can be taken against data corruption. CRCs can be used for error correction (see bitfilters). CRCs are so called because the ''check'' (data verification) value is a ''redundancy'' (it expands the message without adding information) and the algorithm is based on ''cyclic'' codes. CRCs are popular because they are simple to implement in binary hardware, easy to analyze mathematically, and particularly good at detecting common errors caused by noise in transmission channels. Because the check value has a fixed length, the function that generates it is occasionally used as ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Safety-critical System
A safety-critical system or life-critical system is a system whose failure or malfunction may result in one (or more) of the following outcomes: * death or serious injury to people * loss or severe damage to equipment/property * environmental harm A safety-related system (or sometimes safety-involved system) comprises everything (hardware, software, and human aspects) needed to perform one or more safety functions, in which failure would cause a significant increase in the safety risk for the people or environment involved. Safety-related systems are those that do not have full responsibility for controlling hazards such as loss of life, severe injury or severe environmental damage. The malfunction of a safety-involved system would only be that hazardous in conjunction with the failure of other systems or human error. Some safety organizations provide guidance on safety-related systems, for example the Health and Safety Executive in the United Kingdom. Risks of this sort are ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Public-key Cryptography
Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a public key and a corresponding private key. Key pairs are generated with cryptographic algorithms based on mathematical problems termed one-way functions. Security of public-key cryptography depends on keeping the private key secret; the public key can be openly distributed without compromising security. There are many kinds of public-key cryptosystems, with different security goals, including digital signature, Diffie–Hellman key exchange, Key encapsulation mechanism, public-key key encapsulation, and public-key encryption. Public key algorithms are fundamental security primitives in modern cryptosystems, including applications and protocols that offer assurance of the confidentiality and authenticity of electronic communications and data storage. They underpin numerous Internet standards, such as Transport Layer Security, T ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Critical System
A critical system is a system which must be highly reliable and retain this reliability as it evolves without incurring prohibitive costs. There are four types of critical systems: safety critical, mission critical, business critical and security critical. Description For such systems, trusted methods and techniques must be used for development. Consequently, critical systems are usually developed using well-tested techniques rather than newer techniques that have not been subject to extensive practical experience. Developers of critical systems are naturally conservative, preferring to use older techniques whose strengths and weaknesses are understood, rather than new techniques which may appear to be better, but whose long-term problems are unknown. Expensive software engineering techniques that are not cost-effective for non-critical systems may sometimes be used for critical systems development. For example, formal mathematical methods of software development have been ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |