|
Bluesnarfing
Bluesnarfing is the unauthorized access of information from a wireless device through a Bluetooth connection, often between phones, desktops, laptops, and PDAs (personal digital assistant). This allows access to calendars, contact lists, emails and text messages, and on some phones, users can copy pictures and private videos. Both Bluesnarfing and Bluejacking exploit others' Bluetooth connections without their knowledge. While Bluejacking is essentially harmless as it only transmits data to the target device, Bluesnarfing is the theft of information from the target device. For a Bluesnarfing attack to succeed, the attacker generally needs to be within a maximum range of 10 meters from the target device. In some cases, though, attackers can initiate a Bluesnarfing attack from a greater distance. Description Bluesnarfing exploits vulnerabilities in the OBject EXchange protocol used for Bluetooth device communication, involving hackers who use tools like Bluediving to detect su ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Pod Slurping
Pod slurping is the act of using a portable data storage device such as an iPod digital audio player to illicitly download large quantities of confidential data by directly plugging it into a computer where the data are held, and which may be on the inside of a firewall. The phrase "pod slurping" was introduced by Abe Usher. It pertains to a malicious program embedded in a USB storage device, which activates automatically upon being connected to a host. There has been some work in the development of fixes to the problem, including a number of third-party security products that allow companies to set security policies related to USB device use, and features within operating systems that allow IT administrators or users to disable the USB port altogether. Unix-based or Unix-like systems can easily prevent users from mounting storage devices, and Microsoft has released instructions for preventing users from installing USB mass storage devices on its operating systems. Additional m ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Bluebugging
Bluebugging is a form of Bluetooth attack often caused by a lack of awareness. It was developed after the onset of bluejacking and bluesnarfing. Similar to bluesnarfing, bluebugging accesses and uses all phone features but is limited by the transmitting power of class 2 Bluetooth radios, normally capping its range at 10–15 meters. However, the operational range can be increased with the use of a directional antenna. History Bluebugging was developed by the German researcher Martin Herfurt in 2004, one year after the advent of bluejacking. Initially a threat against laptops with Bluetooth capability, ''Seclists.org''; retrieved 3 April 2011 it later targeted mobile phones and PDAs. Bluebugging manipulates a target phone into compro ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
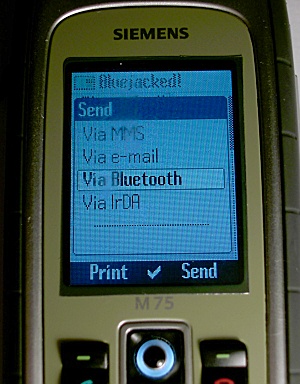
Bluejacking
__NOTOC__ Bluejacking is the sending of unsolicited messages over Bluetooth to Bluetooth-enabled devices such as mobile phones, PDAs or laptop computers, sending a vCard which typically contains a message in the name field (i.e., for bluedating) to another Bluetooth-enabled device via the OBEX protocol. Bluetooth has a very limited range, usually around on mobile phones, but laptops can reach up to with powerful ( Class 1) transmitters. Origins Bluejacking was reportedly first carried out between 2001 and 2003 by a Malaysian IT consultant who used his phone to advertise Ericsson to a single Nokia 7650 phone owner in a Malaysian bank. He also invented the name, which he claims is an amalgam of Bluetooth and ''ajack'', his username on Esato, a Sony Ericsson fan online forum. ''Jacking'' is, however, an extremely common shortening of "hijack', the act of taking over something. Ajack's original posts are hard to find, but references to the exploit are common in 2003 posts. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Snarfing
Snarf is a term used by computer programmers and the UNIX community meaning to copy a file or data over a network, for any purpose, with additional specialist meanings to access data without appropriate permission. It also refers to using command line tools to transfer files through the HTTP, gopher, finger, and FTP protocols without user interaction, and to a method of achieving cache coherence in a multiprocessing computer architecture through observation of writes to cached data. Example An example of a snarf is the Evil twin attack, using a simple shell script running software like AirSnarf to create a wireless hotspot complete with a captive portal. Wireless clients that associate to a snarf access point will receive an IP, DNS, and gateway and appear completely normal. Users will have all of their DNS queries resolve to the attacker's IP number, regardless of their DNS settings, so any website they attempt to visit will bring up a snarf "splash page", requesting a use ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Bluetooth
Bluetooth is a short-range wireless technology standard that is used for exchanging data between fixed and mobile devices over short distances and building personal area networks (PANs). In the most widely used mode, transmission power is limited to 2.5 milliwatts, giving it a very short range of up to . It employs Ultra high frequency, UHF radio waves in the ISM bands, from 2.402GHz to 2.48GHz. It is mainly used as an alternative to wired connections to exchange files between nearby portable devices and connect cell phones and music players with wireless headphones, wireless speakers, HIFI systems, car audio and wireless transmission between TVs and soundbars. Bluetooth is managed by the Bluetooth Special Interest Group (SIG), which has more than 35,000 member companies in the areas of telecommunication, computing, networking, and consumer electronics. The Institute of Electrical and Electronics Engineers, IEEE standardized Bluetooth as IEEE 802.15.1 but no longer maintains ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data Theft
Data theft is the unauthorized duplication or deletion of an organization's electronic information. Data theft is a growing phenomenon primarily caused by system administrators and office workers with access to technology such as database servers, desktop computers and a growing list of hand-held devices capable of storing digital information, such as USB flash drives, iPods and even digital cameras. Since employees often spend a considerable amount of time developing contacts, confidential, and copyrighted information for the company they work for, they may feel they have some right to the information and are inclined to copy or delete part of it when they leave the company, or misuse it while they are still in employment. Information can be sold and bought and then used by criminals and criminal organizations. Alternatively, an employee may choose to deliberately abuse trusted access to information for the purpose of exposing misconduct by the employer. From the perspective of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Wired (magazine)
''Wired'' is a bi-monthly American magazine that focuses on how emerging technologies affect culture, the economy, and politics. It is published in both print and Online magazine, online editions by Condé Nast. The magazine has been in publication since its launch in January 1993. Its editorial office is based in San Francisco, California, with its business headquarters located in New York City. ''Wired'' quickly became recognized as the voice of the emerging digital economy and culture and a pace setter in print design and web design. From 1998 until 2006, the magazine and its website, ''Wired.com'', experienced separate ownership before being fully consolidated under Condé Nast in 2006. It has won multiple National Magazine Awards and has been credited with shaping discourse around the digital revolution. The magazine also coined the term Crowdsourcing, ''crowdsourcing'', as well as its annual tradition of handing out Vaporware Awards. ''Wired'' has launched several in ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Person Of Interest (TV Series)
''Person of Interest'' is an American science fiction crime drama television series that aired on CBS from September 22, 2011, to June 21, 2016, with its five seasons consisting of 103 episodes. The series was created by Jonathan Nolan; executive producers were Nolan, J. J. Abrams, Bryan Burk, Greg Plageman, Denise Thé, and Chris Fisher. The series centers on a mysterious reclusive billionaire computer programmer, Harold Finch ( Michael Emerson), who has developed a computer program for the federal government known as "the Machine" that is capable of collating all sources of information to predict terrorist acts and to identify people planning them. Finch hires John Reese ( Jim Caviezel), a former Special Forces soldier and CIA operative, to be his field agent in preventing small everyday crimes ("irrelevant" in terms of national security). The series raises an array of moral issues, from questions of privacy and "the greater good", the concept of justifiable homicide, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Ruger 10/22
The Ruger 10/22 is a series of semi-automatic rifles produced by American firearm manufacturer Sturm, Ruger & Co., chambered for the .22 Long Rifle rimfire cartridge. It uses a patented 10-round rotary magazine, though higher capacity box magazines are also available. The standard carbine version of the Ruger 10/22 has been in production continuously since 1964,Wood, J.B., ''Firearms Assembly / Disassembly Part III: Rimfire Rifles Revised Edition'', DBI Books, 1994, p.331 making it one of the most successful rimfire rifle designs in history, with numerous third party manufacturers making parts and accessories for upgrading and customization. The 10/22's aftermarket is so prolific that a complete 10/22 can be built without using any Ruger-made components. A magnum version of the 10/22, known as the 10/22 Magnum, chambered for the .22 WMR cartridge, was made from 1998 to 2006. A .17 HMR version, the 10/17, was announced in 2004, but was only listed in the catalog for t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Personal Computer
A personal computer, commonly referred to as PC or computer, is a computer designed for individual use. It is typically used for tasks such as Word processor, word processing, web browser, internet browsing, email, multimedia playback, and PC game, gaming. Personal computers are intended to be operated directly by an end user, rather than by a computer expert or technician. Unlike large, costly minicomputers and mainframes, time-sharing by many people at the same time is not used with personal computers. The term home computer has also been used, primarily in the late 1970s and 1980s. The advent of personal computers and the concurrent Digital Revolution have significantly affected the lives of people. Institutional or corporate computer owners in the 1960s had to write their own programs to do any useful work with computers. While personal computer users may develop their applications, usually these systems run commercial software, free-of-charge software ("freeware"), which i ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Linux
Linux ( ) is a family of open source Unix-like operating systems based on the Linux kernel, an kernel (operating system), operating system kernel first released on September 17, 1991, by Linus Torvalds. Linux is typically package manager, packaged as a Linux distribution (distro), which includes the kernel and supporting system software and library (computing), libraries—most of which are provided by third parties—to create a complete operating system, designed as a clone of Unix and released under the copyleft GPL license. List of Linux distributions, Thousands of Linux distributions exist, many based directly or indirectly on other distributions; popular Linux distributions include Debian, Fedora Linux, Linux Mint, Arch Linux, and Ubuntu, while commercial distributions include Red Hat Enterprise Linux, SUSE Linux Enterprise, and ChromeOS. Linux distributions are frequently used in server platforms. Many Linux distributions use the word "Linux" in their name, but the Free ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
The Screen Savers
''The Screen Savers'' is an American TV show that aired on TechTV from 1998 to 2005. The show launched concurrently with the channel ZDTV (later known as TechTV) on May 11, 1998. ''The Screen Savers'' originally centered on computers, new technologies, and their adaptations in the world. However, after it was taken over by G4, the show became more general-interest oriented and focused somewhat less on technology. The final episode of ''The Screen Savers'' aired on March 18, 2005. Repeat episodes continued to air until March 25, 2005, when its replacement program '' Attack of the Show!'' began three days later on March 28, 2005. Two spiritual successors to The Screen Savers, '' This Week in Tech'' on the TWiT Network with Leo Laporte and Tekzilla on Revision3 with Patrick Norton, were started after the original show concluded. On April 19, 2015, Leo Laporte announced ''The New Screen Savers'', which began airing on TWiT network May 2, 2015. History 1998–2000 ''The Screen Sav ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |