|
Bandwidth Throttling
Bandwidth throttling consists in the limitation of the communication speed (bytes or kilobytes per second), of the ingoing (received) or outgoing (sent) data in a network node or in a network device such as computers and mobile phones. The data speed and rendering may be limited depending on various parameters and conditions. Bandwidth throttling should be done along with rate limiting pattern to minimize the number of throttling errors. Overview Limiting the speed of data sent by a data originator (a client computer or a server computer) is much more efficient than limiting the speed in an intermediate network device between client and server because while in the first case usually no network packets are lost, in the second case network packets can be lost / discarded whenever ingoing data speed overcomes the bandwidth limit or the capacity of device and data packets cannot be temporarily stored in a buffer queue (because it is full or it does not exist); the usage of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data
Data ( , ) are a collection of discrete or continuous values that convey information, describing the quantity, quality, fact, statistics, other basic units of meaning, or simply sequences of symbols that may be further interpreted formally. A datum is an individual value in a collection of data. Data are usually organized into structures such as tables that provide additional context and meaning, and may themselves be used as data in larger structures. Data may be used as variables in a computational process. Data may represent abstract ideas or concrete measurements. Data are commonly used in scientific research, economics, and virtually every other form of human organizational activity. Examples of data sets include price indices (such as the consumer price index), unemployment rates, literacy rates, and census data. In this context, data represent the raw facts and figures from which useful information can be extracted. Data are collected using technique ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
File Sharing
File sharing is the practice of distributing or providing access to digital media, such as computer programs, multimedia (audio, images and video), documents or electronic books. Common methods of storage, transmission and dispersion include removable media, centralized servers on computer networks, Internet-based hyperlinked documents, and the use of distributed peer-to-peer networking. File sharing technologies, such as BitTorrent, are integral to modern media piracy, as well as the sharing of scientific data and other free content. History Files were first exchanged on removable media. Computers were able to access remote files using filesystem mounting, bulletin board systems (1978), Usenet (1979), and FTP servers (1970's). Internet Relay Chat (1988) and Hotline (1997) enabled users to communicate remotely through chat and to exchange files. The mp3 encoding, which was standardized in 1991 and substantially reduced the size of audio files, grew to widespread use ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Comcast
Comcast Corporation, formerly known as Comcast Holdings,Before the AT&T Broadband, AT&T merger in 2001, the parent company was Comcast Holdings Corporation. Comcast Holdings Corporation now refers to a subsidiary of Comcast Corporation, not the parent company (seeBloomberg profile on Comcast Holdings Corporation. Technically, the current parent company was founded December 7, 2001 as CAB Holdings Corporation, which changed its name to AT&T Comcast Corporation before finally taking on the Comcast Corporation name (seeNov 2002 8K/A Form anNov 2002 S-4). is an American Multinational corporation, multinational mass media, telecommunications, and entertainment conglomerate. Headquartered at the Comcast Center in Philadelphia, the company was ranked 51st in the Forbes Global 2000, ''Forbes'' Global 2000 in 2023. It is the List of telephone operating companies, fourth-largest telecommunications company by worldwide revenue, after Deutsche Telekom, China Mobile, and Verizon. Comcast i ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Traffic Shaping
Traffic shaping is a bandwidth management technique used on computer networks which delays some or all datagrams to bring them into compliance with a desired ''traffic profile''. Traffic shaping is used to optimize or guarantee performance, improve latency, or increase usable bandwidth for some kinds of packets by delaying other kinds. It is often confused with traffic policing, the distinct but related practice of packet dropping and packet marking. The most common type of traffic shaping is application-based traffic shaping. In application-based traffic shaping, fingerprinting tools are first used to identify applications of interest, which are then subject to shaping policies. Some controversial cases of application-based traffic shaping include bandwidth throttling of peer-to-peer file sharing traffic. Many application protocols use encryption to circumvent application-based traffic shaping. Another type of traffic shaping is route-based traffic shaping. Route-based traf ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Deep Packet Inspection
Deep packet inspection (DPI) is a type of data processing that inspects in detail the data (Network packet, packets) being sent over a computer network, and may take actions such as alerting, blocking, re-routing, or logging it accordingly. Deep packet inspection is often used for baselining application behavior, analyzing network usage, troubleshooting network performance, ensuring that data is in the correct format, checking for malicious code, Man-in-the-middle attack, eavesdropping, and internet censorship, among other purposes. There are multiple headers for Internet Protocol, IP packets; network equipment only needs to use the first of these (the IPv4 header, IP header) for normal operation, but use of the second header (such as IPv4#Data, TCP or UDP) is normally considered to be shallow packet inspection (usually called stateful packet inspection) despite this definition. There are multiple ways to acquire packets for deep packet inspection. Using port mirroring (sometimes ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Transmission Control Protocol
The Transmission Control Protocol (TCP) is one of the main communications protocol, protocols of the Internet protocol suite. It originated in the initial network implementation in which it complemented the Internet Protocol (IP). Therefore, the entire suite is commonly referred to as TCP/IP. TCP provides reliability (computer networking), reliable, ordered, and error detection and correction, error-checked delivery of a reliable byte stream, stream of octet (computing), octets (bytes) between applications running on hosts communicating via an IP network. Major internet applications such as the World Wide Web, email, remote administration, and file transfer rely on TCP, which is part of the transport layer of the TCP/IP suite. Transport Layer Security, SSL/TLS often runs on top of TCP. TCP is Connection-oriented communication, connection-oriented, meaning that sender and receiver firstly need to establish a connection based on agreed parameters; they do this through three-way Ha ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Kilobyte
The kilobyte is a multiple of the unit byte for Computer data storage, digital information. The International System of Units (SI) defines the prefix ''kilo-, kilo'' as a multiplication factor of 1000 (103); therefore, one kilobyte is 1000 bytes.International Standard IEC 80000-13 Quantities and Units – Part 13: Information science and technology, International Electrotechnical Commission (2008). The internationally recommended unit symbol for the kilobyte is kB. In some areas of information technology, particularly in reference to random-access memory capacity, ''kilobyte'' instead often refers to 1024 (210) bytes. This arises from the prevalence of sizes that are powers of two in modern digital memory architectures, coupled with the coincidence that 210 differs from 103 by less than 2.5%. The kibibyte is defined as 1024 bytes, avoiding the ambiguity issues of the ''kilobyte''.International Standard IEC 80000-13 Quantities and Units – Part 13: Information scien ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mbit
The bit is the most basic unit of information in computing and digital communication. The name is a portmanteau of binary digit. The bit represents a logical state with one of two possible values. These values are most commonly represented as either , but other representations such as ''true''/''false'', ''yes''/''no'', ''on''/''off'', or ''+''/''−'' are also widely used. The relation between these values and the physical states of the underlying storage or device is a matter of convention, and different assignments may be used even within the same device or program. It may be physically implemented with a two-state device. A contiguous group of binary digits is commonly called a ''bit string'', a bit vector, or a single-dimensional (or multi-dimensional) ''bit array''. A group of eight bits is called one ''byte'', but historically the size of the byte is not strictly defined. Frequently, half, full, double and quadruple words consist of a number of bytes which is a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Megabyte
The megabyte is a multiple of the unit byte for digital information. Its recommended unit symbol is MB. The unit prefix ''mega'' is a multiplier of (106) in the International System of Units (SI). Therefore, one megabyte is one million bytes of information. This definition has been incorporated into the International System of Quantities. In the computer and information technology fields, other definitions have been used that arose for historical reasons of convenience. A common usage has been to designate one megabyte as (220 B), a quantity that conveniently expresses the binary architecture of digital computer memory. Standards bodies have deprecated this binary usage of the mega- prefix in favor of a new set of binary prefixes, by means of which the quantity 220 B is named mebibyte (symbol MiB). Definitions The unit megabyte is commonly used for 10002 (one million) bytes or 10242 bytes. The interpretation of using base 1024 originated as technical jargon for the byte m ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
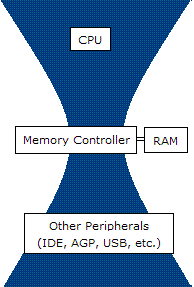
Bottleneck (engineering)
In engineering, a bottleneck is a phenomenon by which the performance or capacity of an entire system is severely limited by a single component. The component is sometimes called a bottleneck point. The term is metaphorically derived from the neck of a bottle, where the flow speed of the liquid is limited by its neck. Formally, a bottleneck lies on a system's critical path and provides the lowest throughput. Bottlenecks are usually avoided by system designers, also a great amount of effort is directed at locating and tuning them. Bottleneck may be for example a processor, a communication link, a data processing software, etc. Bottlenecks in software In computer programming, tracking down bottlenecks (sometimes known as "hot spots" - sections of the code that execute most frequently - i.e. have the highest execution count) is called performance analysis. Reduction is usually achieved with the help of specialized tools, known as performance analyzers or profilers. The objec ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Client (computing)
is a computer that gets information from another computer called server in the context of client–server model of computer networks. The server is often (but not always) on another computer system, in which case the client accesses the service by way of a network. A client is a program that, as part of its operation, relies on sending a request to another program or a computer hardware or software that accesses a service made available by a server (which may or may not be located on another computer). For example, web browsers are clients that connect to web servers and retrieve web pages for display. Email clients retrieve email from mail servers. Online chat uses a variety of clients, which vary on the chat protocol being used. Multiplayer video games or online video games may run as a client on each computer. The term "client" may also be applied to computers or devices that run the client software or users that use the client software. A client is part of a cl ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Server (computing)
A server is a computer that provides information to other computers called " clients" on a computer network. This architecture is called the client–server model. Servers can provide various functionalities, often called "services", such as sharing data or resources among multiple clients or performing computations for a client. A single server can serve multiple clients, and a single client can use multiple servers. A client process may run on the same device or may connect over a network to a server on a different device. Typical servers are database servers, file servers, mail servers, print servers, web servers, game servers, and application servers. Client–server systems are usually most frequently implemented by (and often identified with) the request–response model: a client sends a request to the server, which performs some action and sends a response back to the client, typically with a result or acknowledgment. Designating a computer as "server-class hardwa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |