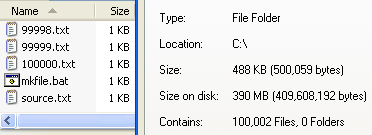
|
Apple Software Restore
Apple Software Restore or asr is a command line utility in Mac OS X used to apply a DMG disk image to a selected partition or mount point on a file system. It is often used for cloning large numbers of Macintosh computers. Apple Software Restore can read an image locally or from a server via HTTP or its own multicast asr:// URI. asr has two methods it can use to restore an image to a volume: it can either copy items in a file-by-file mode, or it can directly block-copy the image. As the latter method does not need to go through the OS filesystem, it is much faster, typically being limited only by the speed of the drives or network connections involved. But in order to use this faster method the .dmg file involved must first be checksummed, and in some cases the files re-ordered inside the image. This is also done by the same tool. The graphical Disk Utility uses asr processes in the background to perform restores. See also * Disk cloning * List of disk cloning software A ''list ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Apple Computer
Apple Inc. is an American multinational technology company headquartered in Cupertino, California, United States. Apple is the largest technology company by revenue (totaling in 2021) and, as of June 2022, is the world's biggest company by market capitalization, the fourth-largest personal computer vendor by unit sales and second-largest mobile phone manufacturer. It is one of the Big Five American information technology companies, alongside Alphabet, Amazon, Meta, and Microsoft. Apple was founded as Apple Computer Company on April 1, 1976, by Steve Wozniak, Steve Jobs and Ronald Wayne to develop and sell Wozniak's Apple I personal computer. It was incorporated by Jobs and Wozniak as Apple Computer, Inc. in 1977 and the company's next computer, the Apple II, became a best seller and one of the first mass-produced microcomputers. Apple went public in 1980 to instant financial success. The company developed computers featuring innovative graphical user interface ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mac OS X
macOS (; previously OS X and originally Mac OS X) is a Unix operating system developed and marketed by Apple Inc. since 2001. It is the primary operating system for Apple's Mac computers. Within the market of desktop and laptop computers it is the second most widely used desktop OS, after Microsoft Windows and ahead of ChromeOS. macOS succeeded the classic Mac OS, a Mac operating system with nine releases from 1984 to 1999. During this time, Apple cofounder Steve Jobs had left Apple and started another company, NeXT, developing the NeXTSTEP platform that would later be acquired by Apple to form the basis of macOS. The first desktop version, Mac OS X 10.0, was released in March 2001, with its first update, 10.1, arriving later that year. All releases from Mac OS X 10.5 Leopard and after are UNIX 03 certified, with an exception for OS X 10.7 Lion. Apple's other operating systems (iOS, iPadOS, watchOS, tvOS, audioOS) are derivatives of macOS. A prominent pa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Disk Image
A disk image, in computing, is a computer file containing the contents and structure of a disk volume or of an entire data storage device, such as a hard disk drive, tape drive, floppy disk, optical disc, or USB flash drive. A disk image is usually made by creating a sector-by-sector copy of the source medium, thereby perfectly replicating the structure and contents of a storage device independent of the file system. Depending on the disk image format, a disk image may span one or more computer files. The file format may be an open standard, such as the ISO image format for optical disc images, or a disk image may be unique to a particular software application. The size of a disk image can be large because it contains the contents of an entire disk. To reduce storage requirements, if an imaging utility is filesystem-aware it can omit copying unused space, and it can compress the used space. History Disk images were originally (in the late 1960s) used for backup and disk c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Command Line
A command-line interpreter or command-line processor uses a command-line interface (CLI) to receive commands from a user in the form of lines of text. This provides a means of setting parameters for the environment, invoking executables and providing information to them as to what actions they are to perform. In some cases the invocation is conditional based on conditions established by the user or previous executables. Such access was first provided by computer terminals starting in the mid-1960s. This provided an interactive environment not available with punched cards or other input methods. Today, many users rely upon graphical user interfaces and menu-driven interactions. However, some programming and maintenance tasks may not have a graphical user interface and use a command line. Alternatives to the command-line interface include text-based user interface menus (for example, IBM AIX SMIT), keyboard shortcuts, and various desktop metaphors centered on the pointer (usu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Software Utility
Utility software is software designed to help analyze, configure, optimize or maintain a computer. It is used to support the computer infrastructure - in contrast to application software, which is aimed at directly performing tasks that benefit ordinary users. However, utilities often form part of the application . For example, a batch job may run user-written code to update a database and may then include a step that runs a utility to back up the database, or a job may run a utility to compress a disk before copying files. Although a basic set of utility programs is usually distributed with an operating system (OS), and this first party utility software is often considered part of the operating system, users often install replacements or additional utilities. Those utilities may provide additional facilities to carry out tasks that are beyond the capabilities of the operating system. Many utilities that might affect the entire computer system require the user to have elevated pr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mount Point
Mounting is a process by which a computer's operating system makes files and directories on a storage device (such as hard drive, CD-ROM, or network share) available for users to access via the computer's file system. In general, the process of mounting comprises the operating system acquiring access to the storage medium; recognizing, reading, and processing file system structure and metadata on it before registering them to the virtual file system (VFS) component. The location in the VFS to which the newly mounted medium was registered is called a mount point; when the mounting process is completed, the user can access files and directories on the medium from there. An opposite process of mounting is called unmounting, in which the operating system cuts off all user access to files and directories on the mount point, writes the remaining queue of user data to the storage device, refreshes file system metadata, then relinquishes access to the device, making the storage device ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
File System
In computing, file system or filesystem (often abbreviated to fs) is a method and data structure that the operating system uses to control how data is stored and retrieved. Without a file system, data placed in a storage medium would be one large body of data with no way to tell where one piece of data stopped and the next began, or where any piece of data was located when it was time to retrieve it. By separating the data into pieces and giving each piece a name, the data are easily isolated and identified. Taking its name from the way a paper-based data management system is named, each group of data is called a " file". The structure and logic rules used to manage the groups of data and their names is called a "file system." There are many kinds of file systems, each with unique structure and logic, properties of speed, flexibility, security, size and more. Some file systems have been designed to be used for specific applications. For example, the ISO 9660 file system is desi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Macintosh
The Mac (known as Macintosh until 1999) is a family of personal computers designed and marketed by Apple Inc. Macs are known for their ease of use and minimalist designs, and are popular among students, creative professionals, and software engineers. The current lineup includes the MacBook Air and MacBook Pro laptops, as well as the iMac, Mac Mini, Mac Studio and Mac Pro desktops. Macs run the macOS operating system. The first Mac was released in 1984, and was advertised with the highly-acclaimed "1984" ad. After a period of initial success, the Mac languished in the 1990s, until co-founder Steve Jobs returned to Apple in 1997. Jobs oversaw the release of many successful products, unveiled the modern Mac OS X, completed the 2005-06 Intel transition, and brought features from the iPhone back to the Mac. During Tim Cook's tenure as CEO, the Mac underwent a period of neglect, but was later reinvigorated with the introduction of popular high-end Macs and the ongoing Appl ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
HTTP
The Hypertext Transfer Protocol (HTTP) is an application layer protocol in the Internet protocol suite model for distributed, collaborative, hypermedia information systems. HTTP is the foundation of data communication for the World Wide Web, where hypertext documents include hyperlinks to other resources that the user can easily access, for example by a mouse click or by tapping the screen in a web browser. Development of HTTP was initiated by Tim Berners-Lee at CERN in 1989 and summarized in a simple document describing the behavior of a client and a server using the first HTTP protocol version that was named 0.9. That first version of HTTP protocol soon evolved into a more elaborated version that was the first draft toward a far future version 1.0. Development of early HTTP Requests for Comments (RFCs) started a few years later and it was a coordinated effort by the Internet Engineering Task Force (IETF) and the World Wide Web Consortium (W3C), with work later moving t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Multicast
In computer networking, multicast is group communication where data transmission is addressed to a group of destination computers simultaneously. Multicast can be one-to-many or many-to-many distribution. Multicast should not be confused with physical layer point-to-multipoint communication. Group communication may either be application layer multicast or network-assisted multicast, where the latter makes it possible for the source to efficiently send to the group in a single transmission. Copies are automatically created in other network elements, such as routers, switches and cellular network base stations, but only to network segments that currently contain members of the group. Network assisted multicast may be implemented at the data link layer using one-to-many addressing and switching such as Ethernet multicast addressing, Asynchronous Transfer Mode (ATM), point-to-multipoint virtual circuits (P2MP) or InfiniBand multicast. Network-assisted multicast may also b ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Disk Utility
A disk utility is a utility program that allows a user to perform various functions on a computer disk, such as disk partitioning and logical volume management, as well as multiple smaller tasks such as changing drive letters and other mount points, renaming volumes, disk checking, and disk formatting, which are otherwise handled separately by multiple other built-in commands. Each operating system (OS) has its own basic disk utility, and there are also separate programs which can recognize and adjust the different filesystems of multiple OSes. Types of disk utilities include disk checkers, disk cleaners and disk space analyzers Disk cleaners Disk cleaners are computer programs that find and delete potentially unnecessary or potentially unwanted files from a computer. The purpose of such deletion may be to free up disk space, to eliminate clutter or to protect privacy. Disk space consuming unnecessary files include temporary files, trash, old backups and web caches made ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Disk Cloning
Disk cloning is the process of creating a 1-to-1 copy of a hard disk drive (HDD) or solid-state drive (SSD), not just its files. Disk cloning may be used for upgrading a disk or replacing an aging disk with a fresh one. In this case, the clone can replace the original disk in its host computer. Disk cloning may also be used for disaster recovery or forensics. In the context of backup software, disk cloning is very similar to disk imaging; in case of the latter, a 1-to-1 copy of a disk is created inside a disk image file. Disk cloning may be done with specialized cloning software, backup software, disk imaging software that has the necessary features, or specialized hardware. Operating environment A disk cloning program needs to be able to read even protected operating system files on the source disk, and must guarantee that the system is in a consistent state at the time of reading. It must also overwrite any operating system already present on the destination disk. To simplify ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |