|
American Fuzzy Lop (software)
American Fuzzy Lop (AFL), stylized in all lowercase as , is a free software fuzzer that employs genetic algorithms in order to efficiently increase code coverage of the test cases. So far it has detected hundreds of significant software bugs in major free software projects, including X.Org Server, PHP, OpenSSL, pngcrush, bash, Firefox, BIND, Qt, and SQLite. Initially released in November 2013, AFL quickly became one of the most widely used fuzzers in security research. For many years after its release, AFL has been considered a "state of the art" fuzzer. AFL is considered "a de-facto standard for fuzzing", and the release of AFL contributed significantly to the development of fuzzing as a research area. AFL is widely used in academia; academic fuzzers are often forks of AFL, and AFL is commonly used as a baseline to evaluate new techniques. The source code of American fuzzy lop is published on GitHub. Its name is a reference to a breed of rabbit, the American Fuzzy Lop. Ov ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Michał Zalewski
Michał Zalewski (born 19 January 1981), also known by the user name lcamtuf, is a computer security expert and " white hat" hacker from Poland. He is a former Google Inc. employee (until 2018), and currently the VP of Security Engineering at Snap Inc. He has been a prolific vulnerability researcher and a frequent Bugtraq poster since the mid-1990s, and has written a number of programs for Unix-like operating systems. In 2005, Zalewski wrote ''Silence on the Wire: A Field Guide to Passive Reconnaissance and Indirect Attacks'', a computer security book published by No Starch Press and subsequently translated into a number of languages. In 2011, Zalewski wrote '' The Tangled Web: A Guide to Securing Modern Web Applications'', also published by No Starch Press. For his continued research on browser security, he was named one of the 15 most influential people in security and among the 100 most influential people in IT. Zalewski was one of the original creators of Argante, a vi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Firefox
Mozilla Firefox, or simply Firefox, is a free and open-source web browser developed by the Mozilla Foundation and its subsidiary, the Mozilla Corporation. It uses the Gecko rendering engine to display web pages, which implements current and anticipated web standards. Firefox is available for Windows 10 or later versions of Windows, macOS, and Linux. Its unofficial ports are available for various Unix and Unix-like operating systems, including FreeBSD, OpenBSD, NetBSD, and other operating systems, such as ReactOS. Firefox is also available for Android and iOS. However, as with all other iOS web browsers, the iOS version uses the WebKit layout engine instead of Gecko due to platform requirements. An optimized version is also available on the Amazon Fire TV as one of the two main browsers available with Amazon's Silk Browser. Firefox is the spiritual successor of Netscape Navigator, as the Mozilla community was created by Netscape in 1998, before its acqui ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Control Flow
In computer science, control flow (or flow of control) is the order in which individual statements, instructions or function calls of an imperative program are executed or evaluated. The emphasis on explicit control flow distinguishes an ''imperative programming'' language from a ''declarative programming'' language. Within an imperative programming language, a ''control flow statement'' is a statement that results in a choice being made as to which of two or more paths to follow. For non-strict functional languages, functions and language constructs exist to achieve the same result, but they are usually not termed control flow statements. A set of statements is in turn generally structured as a block, which in addition to grouping, also defines a lexical scope. Interrupts and signals are low-level mechanisms that can alter the flow of control in a way similar to a subroutine, but usually occur as a response to some external stimulus or event (that can occur asynchr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Instrumentation (computer Programming)
In computer programming, instrumentation is the act of modifying software so that analysis can be performed on it. Generally, instrumentation either modifies source code or binary code. Execution environments like the JVM provide separate interfaces to add instrumentation to program executions, such as the JVMTI, which enables instrumentation during program start. Instrumentation enables profiling: measuring dynamic behavior during a test run. This is useful for properties of a program that cannot be analyzed statically with sufficient precision, such as performance and alias analysis. Instrumentation can include: * Logging events such as failures and operation start and end * Measuring and logging the duration of operations Limitations Instrumentation is limited by execution coverage. If the program never reaches a particular point of execution, then instrumentation at that point collects no data. For instance, if a word processor application is instrumented, but the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Utility Program
Utility software is a program specifically designed to help manage and tune system or application software. It is used to support the computer infrastructure - in contrast to application software, which is aimed at directly performing tasks that benefit ordinary users. However, utilities often form part of the application . For example, a batch job may run user-written code to update a database and may then include a step that runs a utility to back up the database, or a job may run a utility to compress a disk before copying files. Although a basic set of utility programs is usually distributed with an operating system (OS), and this first party utility software is often considered part of the operating system, users often install replacements or additional utilities. Those utilities may provide additional facilities to carry out tasks that are beyond the capabilities of the operating system. Many utilities that might affect the entire computer system require the user to have ele ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Compilation (computing)
In computing, a compiler is a computer program that translates Translation is the communication of the semantics, meaning of a #Source and target languages, source-language text by means of an Dynamic and formal equivalence, equivalent #Source and target languages, target-language text. The English la ... computer code written in one programming language (the ''source'' language) into another language (the ''target'' language). The name "compiler" is primarily used for programs that translate source code from a high-level programming language to a lower level language, low-level programming language (e.g. assembly language, object code, or machine code) to create an executable program.Compilers: Principles, Techniques, and Tools by Alfred V. Aho, Ravi Sethi, Jeffrey D. Ullman - Second Edition, 2007 There are many different types of compilers which produce output in different useful forms. A ''cross-compiler'' produces code for a different Central processing unit, CPU ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Security Vulnerability
Vulnerabilities are flaws or weaknesses in a system's design, implementation, or management that can be exploited by a malicious actor to compromise its security. Despite a system administrator's best efforts to achieve complete correctness, virtually all hardware and software contain bugs where the system does not behave as expected. If the bug could enable an attacker to compromise the confidentiality, integrity, or availability of system resources, it can be considered a vulnerability. Insecure software development practices as well as design factors such as complexity can increase the burden of vulnerabilities. Vulnerability management is a process that includes identifying systems and prioritizing which are most important, scanning for vulnerabilities, and taking action to secure the system. Vulnerability management typically is a combination of remediation, mitigation, and acceptance. Vulnerabilities can be scored for severity according to the Common Vulnerability Scorin ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hang (computing)
In computing, a hang or freeze occurs when either a process or system ceases to respond to inputs. A typical example is when computer's graphical user interface (such as Microsoft Windows) no longer responds to the user typing on the keyboard or moving the mouse. The term covers a wide range of behaviors in both clients and servers, and is not limited to graphical user interface issues. Hangs have varied causes and symptoms, including software or hardware defects, such as an infinite loop or long-running uninterruptible computation, resource exhaustion ( thrashing), under-performing hardware ( throttling), external events such as a slow computer network, misconfiguration, and compatibility problems. The fundamental reason is typically resource exhaustion: resources necessary for some part of the system to run are not available, due to being in use by other processes or simply insufficient. Often the cause is an interaction of multiple factors, making "hang" a loose umbrella ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
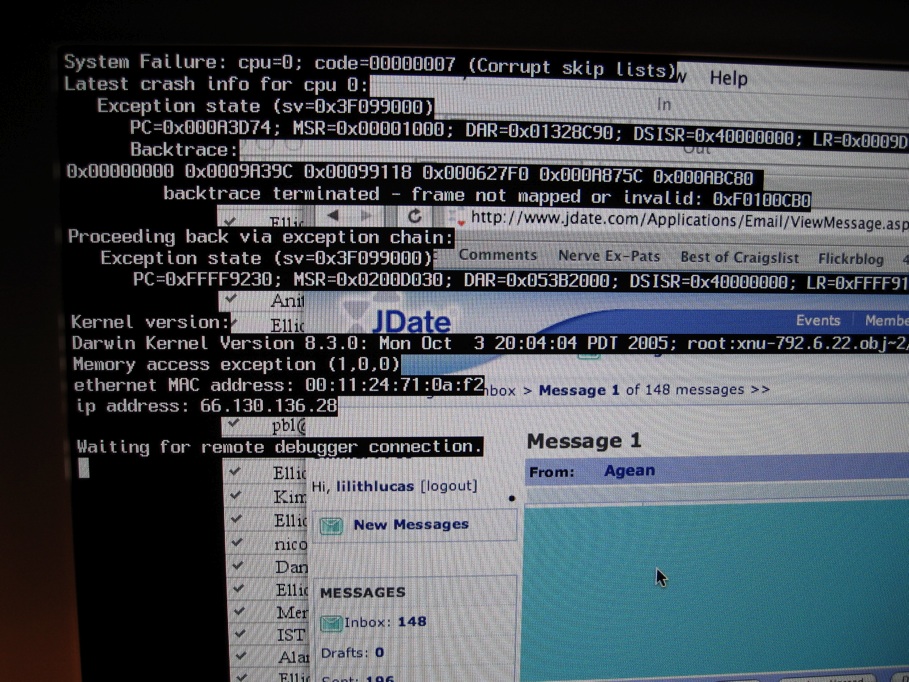
Crash (computing)
In computing, a crash, or system crash, occurs when a computer program such as a software application or an operating system stops functioning properly and exits. On some operating systems or individual applications, a crash reporting service will report the crash and any details relating to it (or give the user the option to do so), usually to the developer(s) of the application. If the program is a critical part of the operating system, the entire system may crash or hang, often resulting in a kernel panic or fatal system error. Most crashes are the result of a software bug. Typical causes include accessing invalid memory addresses, incorrect address values in the program counter, buffer overflow, overwriting a portion of the affected program code due to an earlier bug, executing invalid machine instructions (an illegal or unauthorized opcode), or triggering an unhandled exception. The original software bug that started this chain of events is typically considere ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
American Fuzzy Lop
The American Fuzzy Lop is a rabbit breed recognized by the American Rabbit Breeders Association (ARBA). It is similar in appearance to a Holland Lop. However, the American Fuzzy Lop is a wool breed and will have wool similar to the Angora breeds although the wool will be shorter than that of a commercial Angora. The American fuzzy lop has to weigh up to four pounds in order to be shown. History The background of the American Fuzzy Lop is interwoven with the history of the Holland Lop. When first introduced, the Holland Lop rabbit was only available in solid colors, and some breeders wanted to add the broken pattern to the Holland Lop gene pool. To do this, they bred their Holland Lops with English Spots. While they achieved the goal of producing broken pattern rabbits, they failed to keep the rollback fur the Holland must have. The offspring instead had the flyback fur of the English Spot. The breeders then bred Holland Lops with French Angoras, a breed that has a very gentle rol ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Source Code
In computing, source code, or simply code or source, is a plain text computer program written in a programming language. A programmer writes the human readable source code to control the behavior of a computer. Since a computer, at base, only understands machine code, source code must be Translator (computing), translated before a computer can Execution (computing), execute it. The translation process can be implemented three ways. Source code can be converted into machine code by a compiler or an assembler (computing), assembler. The resulting executable is machine code ready for the computer. Alternatively, source code can be executed without conversion via an interpreter (computing), interpreter. An interpreter loads the source code into memory. It simultaneously translates and executes each statement (computer science), statement. A method that combines compilation and interpretation is to first produce bytecode. Bytecode is an intermediate representation of source code tha ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Fork (software Development)
In software development, a fork is a codebase that is created by duplicating an existing codebase and, generally, is subsequently modified independently of the original. Software built from a fork initially has identical behavior as software built from the original code, but as the source code is increasingly modified, the resulting software tends to have increasingly different behavior compared to the original. A fork is a form of branching, but generally involves storing the forked files separately from the original; not in the repository. Reasons for forking a codebase include user preference, stagnated or discontinued development of the original software or a schism in the developer community. Forking proprietary software (such as Unix) is prohibited by copyright law without explicit permission, but free and open-source software, by definition, may be forked without permission. Etymology The word ''fork'' has been used to mean "to divide in branches, go separate ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |