|
Alina (malware)
Alina is a Point of Sale Malware or POS RAM Scraper that is used by cybercriminals to scrape credit card and debit card information from the point of sale system. It first started to scrape information in late 2012. It resembles JackPOS Malware. Process of Alina POS RAM Scraper Once executed, it gets installed on the user's computer A computer is a machine that can be programmed to Execution (computing), carry out sequences of arithmetic or logical operations (computation) automatically. Modern digital electronic computers can perform generic sets of operations known as C ... and checks for updates. If an update is found, it removes the existing Alina code and installs the latest version. Then, for new installations, it adds the file path to an AutoStart runkey to maintain persistence. Finally, it adds java.exe to the %APPDATA% directory and executes it using the parameter alina= for new installations or, update=; for upgrades. Alina inspects the user's processes with the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Point-of-sale Malware
Point-of-sale malware (POS malware) is usually a type of malicious software (malware) that is used by cybercriminals to target point of sale (POS) and payment terminals with the intent to obtain credit card and debit card information, a card's track 1 or track 2 data and even the CVV code, by various man-in-the-middle attacks, that is the interception of the processing at the retail checkout point of sale system. The simplest, or most evasive, approach is RAM-scraping, accessing the system's memory and exporting the copied information via a remote access trojan (RAT) as this minimizes any software or hardware tampering, potentially leaving no footprints. POS attacks may also include the use of various bits of hardware: dongles, trojan card readers, (wireless) data transmitters and receivers. Being at the gateway of transactions, POS malware enables hackers to process and steal thousands, even millions, of transaction payment data, depending upon the target, the number of devices a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
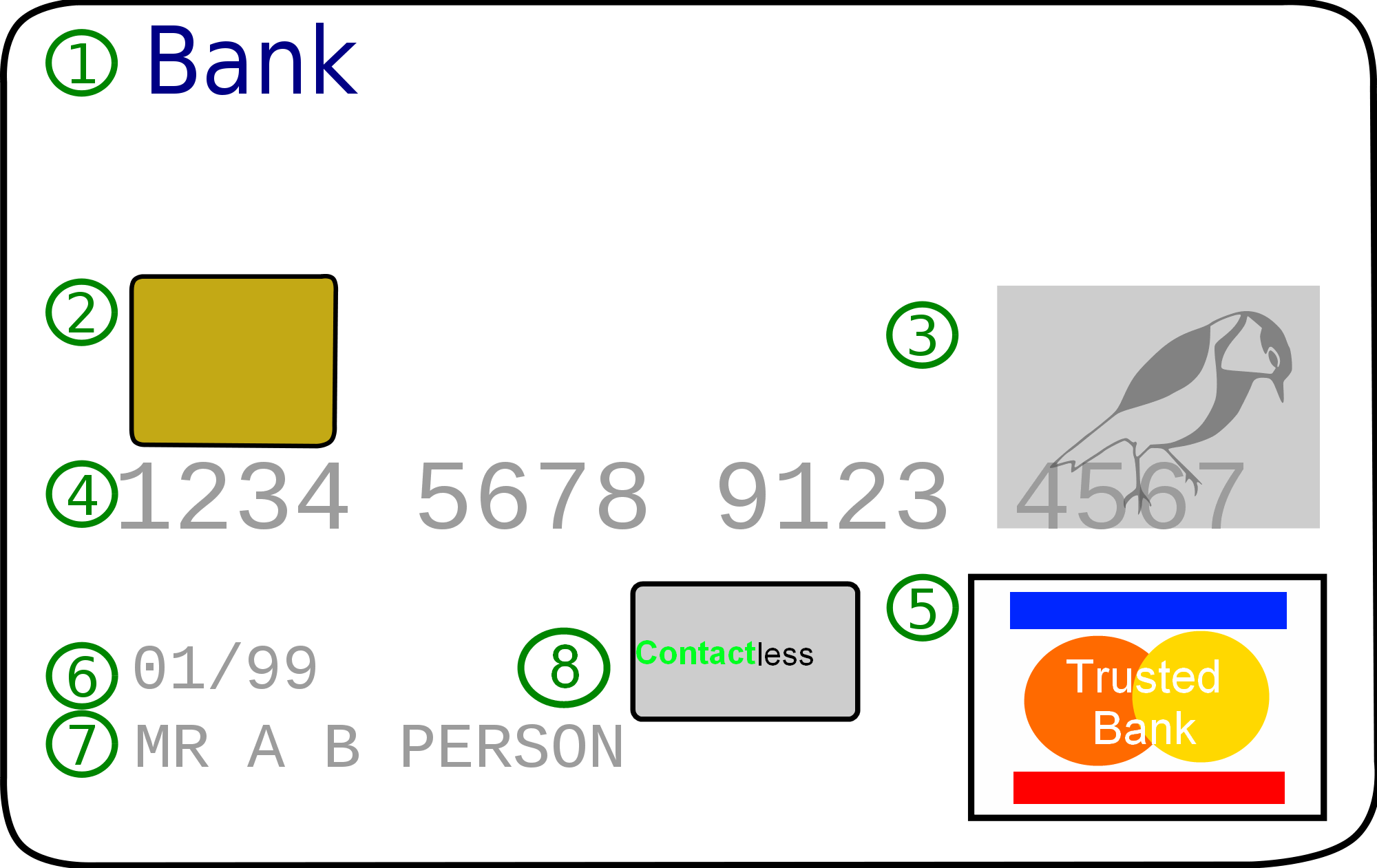
Credit Card
A credit card is a payment card issued to users (cardholders) to enable the cardholder to pay a merchant for goods and services based on the cardholder's accrued debt (i.e., promise to the card issuer to pay them for the amounts plus the other agreed charges). The card issuer (usually a bank or credit union) creates a revolving account and grants a line of credit to the cardholder, from which the cardholder can borrow money for payment to a merchant or as a cash advance. There are two credit card groups: consumer credit cards and business credit cards. Most cards are plastic, but some are metal cards (stainless steel, gold, palladium, titanium), and a few gemstone-encrusted metal cards. A regular credit card is different from a charge card, which requires the balance to be repaid in full each month or at the end of each statement cycle. In contrast, credit cards allow the consumers to build a continuing balance of debt, subject to interest being charged. A credit car ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Debit Card
A debit card, also known as a check card or bank card is a payment card that can be used in place of cash to make purchases. The term ''#Plastic card, plastic card'' includes the above and as an identity document. These are similar to a credit card, but unlike a credit card, the money for the purchase must be in the cardholder's bank account at the time of a purchase and is immediately transferred directly from that account to the merchant's account to pay for the purchase. Some debit cards carry a Stored-value card, stored value with which a payment is made (prepaid card), but most relay a message to the cardholder's bank to withdraw funds from the cardholder's designated bank account. In some cases, the payment card number is assigned exclusively for use on the Internet and there is no physical card. This is referred to as a virtual card. In many countries, the use of debit cards has become so widespread they have overtaken cheque, checks in volume, or have entirely replace ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Point Of Sale
The point of sale (POS) or point of purchase (POP) is the time and place at which a retail transaction is completed. At the point of sale, the merchant calculates the amount owed by the customer, indicates that amount, may prepare an invoice for the customer (which may be a cash register printout), and indicates the options for the customer to make payment. It is also the point at which a customer makes a payment to the merchant in exchange for goods or after provision of a service. After receiving payment, the merchant may issue a receipt for the transaction, which is usually printed but can also be dispensed with or sent electronically. To calculate the amount owed by a customer, the merchant may use various devices such as weighing scales, barcode scanners, and cash registers (or the more advanced "POS cash registers", which are sometimes also called "POS systems"). To make a payment, payment terminals, touch screens, and other hardware and software options are available ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer
A computer is a machine that can be programmed to Execution (computing), carry out sequences of arithmetic or logical operations (computation) automatically. Modern digital electronic computers can perform generic sets of operations known as Computer program, programs. These programs enable computers to perform a wide range of tasks. A computer system is a nominally complete computer that includes the Computer hardware, hardware, operating system (main software), and peripheral equipment needed and used for full operation. This term may also refer to a group of computers that are linked and function together, such as a computer network or computer cluster. A broad range of Programmable logic controller, industrial and Consumer electronics, consumer products use computers as control systems. Simple special-purpose devices like microwave ovens and remote controls are included, as are factory devices like industrial robots and computer-aided design, as well as general-purpose devi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
File Path
A path is a string of characters used to uniquely identify a location in a directory structure. It is composed by following the directory tree hierarchy in which components, separated by a delimiting character, represent each directory. The delimiting character is most commonly the slash ("/"), the backslash character ("\"), or colon (":"), though some operating systems may use a different delimiter. Paths are used extensively in computer science to represent the directory/file relationships common in modern operating systems and are essential in the construction of Uniform Resource Locators (URLs). Resources can be represented by either ''absolute'' or ''relative'' paths. History Multics first introduced a hierarchical file system with directories (separated by ">") in the mid-1960s. Around 1970, Unix introduced the slash character ("/") as its directory separator. In 1981, the first version of Microsoft DOS was released. MS-DOS 1.0 did not support file directories. Also, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Blacklisting
Blacklisting is the action of a group or authority compiling a blacklist (or black list) of people, countries or other entities to be avoided or distrusted as being deemed unacceptable to those making the list. If someone is on a blacklist, they are seen by a government or other organization as being one of a number of people who cannot be trusted or who is considered to have done something wrong. As a verb, blacklist can mean to put an individual or entity on such a list. Origins of the term The English dramatist Philip Massinger used the phrase "black list" in his 1639 tragedy ''The Unnatural Combat''. After the restoration of the English monarchy brought Charles II of England to the throne in 1660, a list of regicides named those to be punished for the execution of his father. The state papers of Charles II say "If any innocent soul be found in this black list, let him not be offended at me, but consider whether some mistaken principle or interest may not have misled ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
POST (HTTP)
In computing, POST is a request method supported by HTTP used by the World Wide Web. By design, the POST request method requests that a web server accept the data enclosed in the body of the request message, most likely for storing it. It is often used when uploading a file or when submitting a completed web form. In contrast, the HTTP GET request method retrieves information from the server. As part of a GET request, some data can be passed within the URL's query string, specifying (for example) search terms, date ranges, or other information that defines the query. As part of a POST request, an arbitrary amount of data of any type can be sent to the server in the body of the request message. A header field in the POST request usually indicates the message body's Internet media type. Posting data The world wide Web and HTTP are based on a number of request methods or 'verbs', including POST and GET as well as PUT, DELETE, and several others. Web browsers normally use only G ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cyber Security Standards
IT security standards or cyber security standards are techniques generally outlined in published materials that attempt to protect the cyber environment of a user or organization. This environment includes users themselves, networks, devices, all software, processes, information in storage or transit, applications, services, and systems that can be connected directly or indirectly to networks. The principal objective is to reduce the risks, including preventing or mitigating cyber-attacks. These published materials consist of tools, policies, security concepts, security safeguards, guidelines, risk management approaches, actions, training, best practices, assurance and technologies. History Cybersecurity standards have existed over several decades as users and providers have collaborated in many domestic and international forums to effect the necessary capabilities, policies, and practices – generally emerging from work at the Stanford Consortium for Research on Information Sec ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
List Of Cyber Attack Threat Trends
A cyberattack is any offensive maneuver that targets computer information systems, computer networks, infrastructures, or personal computer devices. An attacker is a person or process that attempts to access data, functions, or other restricted areas of the system without authorization, potentially with malicious intent. Depending on the context, cyberattacks can be part of cyber warfare or cyberterrorism. A cyberattack can be employed by sovereign states, individuals, groups, societies or organisations and it may originate from an anonymous source. A product that facilitates a cyberattack is sometimes called a cyber weapon. Cyber attacks have increased with an alarming rate for the last few years A cyberattack may steal, alter, or destroy a specified target by hacking into a susceptible system. Cyberattacks can range from installing spyware on a personal computer to attempting to destroy the infrastructure of entire nations. Legal experts are seeking to limit the use of the t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Carding (fraud)
Carding is a term describing the trafficking and unauthorized use of credit cards. The stolen credit cards or credit card numbers are then used to buy prepaid gift cards to cover up the tracks. Activities also encompass exploitation of personal data, and money laundering techniques. Modern carding sites have been described as full-service commercial entities. Acquisition There are a great many of methods to acquire credit card and associated financial and personal data. The earliest known carding methods have also included "trashing" for financial data, raiding mail boxes and working with insiders. Some bank card numbers can be semi-automatically generated based on known sequences via a "BIN attack". Carders might attempt a "distributed guessing attack" to discover valid numbers by submitting numbers across a high number of ecommerce sites simultaneously. Today, various methodologies include skimmers at ATMs, hacking or web skimming an ecommerce or payment process ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cyberwarfare
Cyberwarfare is the use of cyber attacks against an enemy state, causing comparable harm to actual warfare and/or disrupting vital computer systems. Some intended outcomes could be espionage, sabotage, propaganda, manipulation or economic warfare. There is significant debate among experts regarding the definition of cyberwarfare, and even if such a thing exists. One view is that the term is a misnomer, since no cyber attacks to date could be described as war. An alternative view is that it is a suitable label for cyber attacks which cause physical damage to people and objects in the real world. Many countries including the United States, United Kingdom, Russia, China, Israel, Iran, and North Korea have active cyber capabilities for offensive and defensive operations. As states explore the use of cyber operations and combine capabilities, the likelihood of physical confrontation and violence playing out as a result of, or part of, a cyber operation is increased. However, meet ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |

.jpg)