|
Action At Distance (computer Science)
Action at a distance is an anti-pattern in computer science in which behavior in one part of a program varies wildly based on difficult or impossible to identify operations in another part of the program. The way to avoid the problems associated with action at a distance is a proper design, which avoids global variables and alters data only in a controlled and local manner, or usage of a pure functional programming style with referential transparency. The term is based on the concept of action at a distance in physics, which may refer to a process that allows objects to interact without a mediator particle such as the gluon. In particular, Albert Einstein referred to quantum nonlocality as "spooky action at a distance". Software bugs due to action at a distance may arise because a program component is doing something at the wrong time, or affecting something it should not. It is very difficult, however, to track down which component is responsible. Side effects from inno ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
|
Anti-pattern
An anti-pattern in software engineering, project management, and business processes is a common response to a recurring problem that is usually ineffective and risks being highly counterproductive. The term, coined in 1995 by computer programmer Andrew Koenig (programmer), Andrew Koenig, was inspired by the book ''Design Patterns'' (which highlights a number of design patterns in software development that its authors considered to be highly reliable and effective) and first published in his article in the ''Journal of Object-Oriented Programming''. A further paper in 1996 presented by Michael Ackroyd at the Object World West Conference also documented anti-patterns. It was, however, the 1998 book ''AntiPatterns'' that both popularized the idea and extended its scope beyond the field of software design to include software architecture and project management. Other authors have extended it further since to encompass environmental, organizational, and cultural anti-patterns. Definiti ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
 |
Deprecation
Deprecation is the discouragement of use of something human-made, such as a term, feature, design, or practice. Typically something is deprecated because it is claimed to be inferior compared to other options available. Something may be deprecated when it cannot be controlled, such as a term. Even when it can be controlled, something may be deprecated even when it might be useful for example, to ensure compatibility and it may be removed or discontinued at some time after being deprecated. Etymology In general English usage, the verb "to deprecate" means "to express disapproval of (something)". It derives from the Latin deponent verb ''deprecari'', meaning "to ward off (a disaster) by prayer". An early documented usage of "deprecate" in this sense is in Usenet posts in 1984, referring to obsolete features in 4.2BSD and the C programming language. An expanded definition of "deprecate" was cited in the Jargon File in its 1991 revision, and similar definitions are found in ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
Loose Coupling
In computing and systems design, a loosely coupled system is one # in which components are weakly associated (have breakable relationships) with each other, and thus changes in one component least affect existence or performance of another component. # in which each of its components has, or makes use of, little or no knowledge of the definitions of other separate components. Subareas include the coupling of classes, interfaces, data, and services. Loose coupling is the opposite of tight coupling. Advantages and disadvantages Components in a loosely coupled system can be replaced with alternative implementations that provide the same services. Components in a loosely coupled system are less constrained to the same platform, language, operating system, or build environment. If systems are decoupled in time, it is difficult to also provide transactional integrity; additional coordination protocols are required. Data replication across different systems provides loose coupling ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
|
COMEFROM
In computer programming, COMEFROM (or COME FROM) is an obscure control flow structure used in some programming languages, originally as a joke. COMEFROM is the inverse of GOTO in that it can take the execution state from any arbitrary point in code to a COMEFROM statement. The point in code where the state transfer happens is usually given as a parameter to COMEFROM. Whether the transfer happens before or after the instruction at the specified transfer point depends on the language used. Depending on the language used, multiple COMEFROMs referencing the same departure point may be invalid, be non-deterministic, be executed in some sort of defined priority, or even induce parallel or otherwise concurrent execution as seen in Threaded Intercal. A simple example of a "COMEFROM x" statement is a label x (which does not need to be physically located anywhere near its corresponding COMEFROM) that acts as a "trap door". When code execution reaches the label, control gets passed to the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
|
Functional Programming
In computer science, functional programming is a programming paradigm where programs are constructed by Function application, applying and Function composition (computer science), composing Function (computer science), functions. It is a declarative programming paradigm in which function definitions are Tree (data structure), trees of Expression (computer science), expressions that map Value (computer science), values to other values, rather than a sequence of Imperative programming, imperative Statement (computer science), statements which update the State (computer science), running state of the program. In functional programming, functions are treated as first-class citizens, meaning that they can be bound to names (including local Identifier (computer languages), identifiers), passed as Parameter (computer programming), arguments, and Return value, returned from other functions, just as any other data type can. This allows programs to be written in a Declarative programming, d ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
|
God Object
In object-oriented programming, a god object (sometimes also called an omniscient or all-knowing object) is an object that references a large number of distinct types, has too many unrelated or uncategorized methods, or some combination of both. The god object is an example of an anti-pattern and a code smell. Characteristics A common programming technique is to separate a large problem into several smaller problems (a divide and conquer strategy) and create solutions for each of them. Once the smaller problems are solved, the big problem as a whole has been solved. Therefore a given object for a small problem only needs to know about itself. Likewise, there is only one set of problems an object needs to solve: its ''own'' problems. This also follows the single-responsibility principle. In contrast, a program that employs a god object does not follow this approach. Most of such a program's overall functionality is coded into a single "all-knowing" object, which maintains ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
|
Object Orgy
In computer programming, an object orgy is a situation in which objects are insufficiently encapsulated via information hiding, allowing unrestricted access to their internals. This is a common failure (or anti-pattern) in object-oriented design or object-oriented programming, and it can lead to increased maintenance needs and problems, and even unmaintainable complexity. Consequences The results of an object orgy are mainly a loss of the benefits of encapsulation, including: * Unrestricted access makes it hard for a reader to reason about the behaviour of an object. This is because direct access to its internal state means any other part of the system can manipulate it, increasing the amount of code to examine, and creating means for future abuse. * As a consequence of the difficulty of reasoning, design by contract is effectively impossible. * If much code takes advantage of the lack of encapsulation, the result is a scarcely maintainable maze of interactions, commonly known a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
|
Law Of Demeter
The Law of Demeter (LoD) or principle of least knowledge is a design guideline for developing software, particularly object-oriented programs. In its general form, the LoD is a specific case of loose coupling. The guideline was proposed by Ian Holland at Northeastern University towards the end of 1987, and the following three recommendations serve as a succinct summary: # Each unit should have only limited knowledge about other units: only units "closely" related to the current unit. # Each unit should only talk to its friends; don't talk to strangers. # Only talk to your immediate friends. The fundamental notion is that a given object should assume as little as possible about the structure or properties of anything else (including its subcomponents), in accordance with the principle of "information hiding". It may be viewed as a corollary to the principle of least privilege, which dictates that a module possess only the information and resources necessary for its legitimate purpos ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
|
Object-oriented Programming
Object-oriented programming (OOP) is a programming paradigm based on the concept of '' objects''. Objects can contain data (called fields, attributes or properties) and have actions they can perform (called procedures or methods and implemented in code). In OOP, computer programs are designed by making them out of objects that interact with one another. Many of the most widely used programming languages (such as C++, Java, and Python) support object-oriented programming to a greater or lesser degree, typically as part of multiple paradigms in combination with others such as imperative programming and declarative programming. Significant object-oriented languages include Ada, ActionScript, C++, Common Lisp, C#, Dart, Eiffel, Fortran 2003, Haxe, Java, JavaScript, Kotlin, Logo, MATLAB, Objective-C, Object Pascal, Perl, PHP, Python, R, Raku, Ruby, Scala, SIMSCRIPT, Simula, Smalltalk, Swift, Vala and Visual Basic.NET. History The idea of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
|
Mark Jason Dominus
''Higher-Order Perl: Transforming Programs with Programs'' () is a book about the Perl programming language written by Mark Jason Dominus with the goal to teach Perl programmers with a strong C and Unix background how to use techniques with roots in functional programming languages like Lisp that are available in Perl as well. In June 2013, a Chinese-language edition was published by China Machine Press. The full text of ''Higher Order Perl'' is available online in a variation of the Plain Old Documentation format (MOD) and in PDF. Reception The book has received reviews from sources including '' ACM Computing Reviews'', ''Linux Journal'', ''Weblabor'', ''Dr. Dobb's Journal ''Dr. Dobb's Journal'' (often shortened to ''Dr. Dobb's'' or DDJ) was a monthly magazine published in the United States by UBM Technology Group, part of UBM. It covered topics aimed at computer programmers. When launched in 1976, DDJ was the fi ...'', and ''The Prague Bulletin of Mathematical Linguis ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
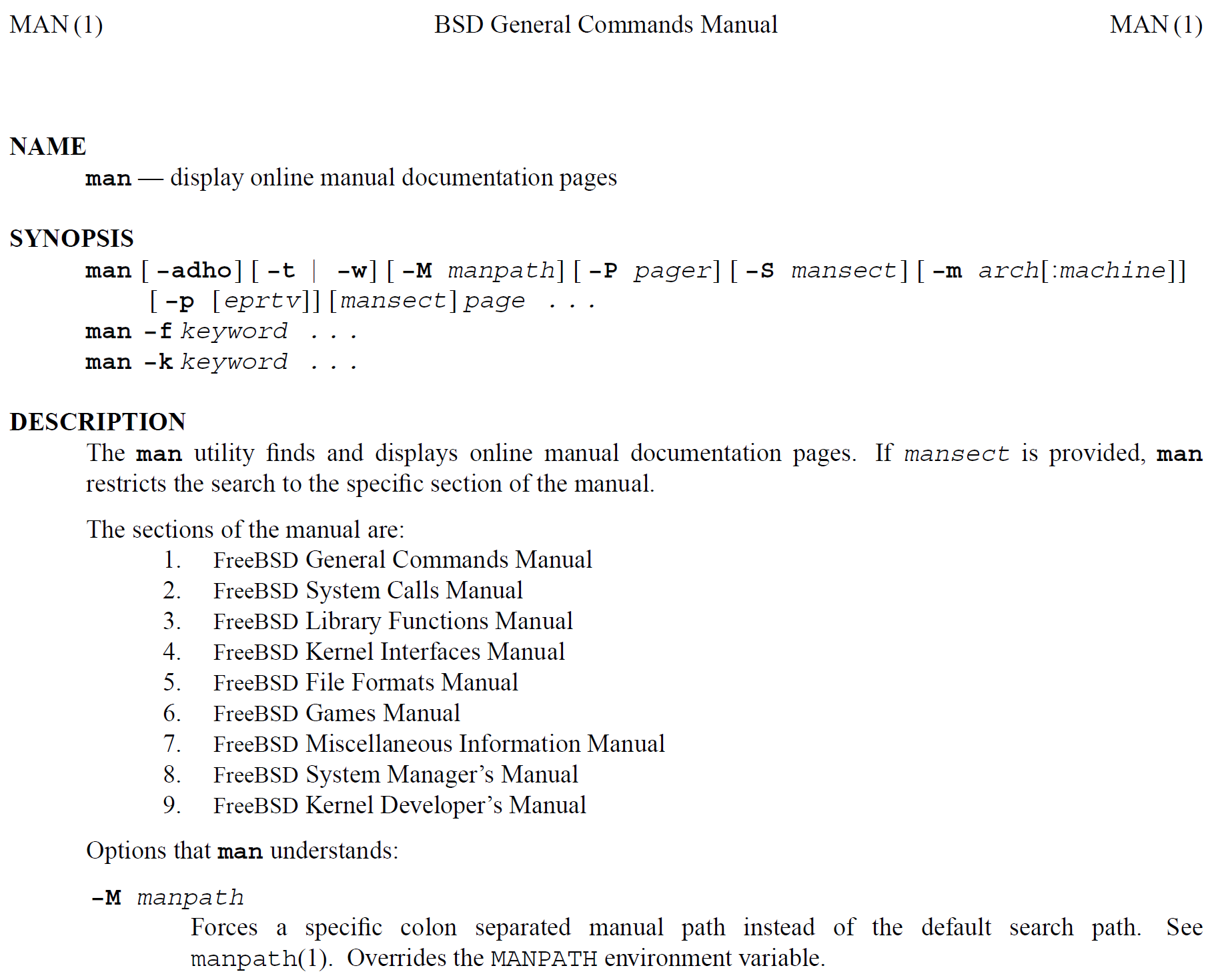 |
Man Page
A man page (short for manual page) is a form of software documentation found on Unix and Unix-like operating systems. Topics covered include programs, system libraries, system calls, and sometimes local system details. The local host administrators can create and install manual pages associated with the specific host. A manual end user may invoke a documentation page by issuing the man command followed by the name of the item for which they want the documentation. These manual pages are typically requested by end users, programmers and administrators doing real time work but can also be formatted for printing. By default, man typically uses a formatting program such as nroff with a macro package or mandoc, and also a terminal pager program such as more or less to display its output on the user's screen. Man pages are often referred to as an ''online'' form of software documentation, even though the man command does not require internet access. The environment variable M ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
Lua (programming Language)
Lua is a lightweight, high-level, multi-paradigm programming language designed mainly for embedded use in applications. Lua is cross-platform software, since the interpreter of compiled bytecode is written in ANSI C, and Lua has a relatively simple C application programming interface ( API) to embed it into applications. Lua originated in 1993 as a language for extending software applications to meet the increasing demand for customization at the time. It provided the basic facilities of most procedural programming languages, but more complicated or domain-specific features were not included; rather, it included mechanisms for extending the language, allowing programmers to implement such features. As Lua was intended to be a general embeddable extension language, the designers of Lua focused on improving its speed, portability, extensibility and ease-of-use in development. History Lua was created in 1993 by Roberto Ierusalimschy, Luiz Henrique de Figueiredo and Wa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |