|
802.1aq
Shortest Path Bridging (SPB), specified in the IEEE 802.1aq standard, is a computer networking technology intended to simplify the creation and configuration of Ethernet networks while enabling multipath routing. It is the replacement for the older spanning tree protocols: IEEE 802.1D, IEEE 802.1w, IEEE 802.1s. These blocked any redundant paths that could result in a switching loop, whereas SPB allows all paths to be active with multiple equal cost paths, provides much larger topologies, supports faster convergence times, and improves the efficiency by allowing traffic to load share across all paths of a mesh network. It is designed to preserve the plug-and-play nature that established Ethernet as the de facto protocol at layer 2. The technology provides VLANs on native Ethernet infrastructures using a link-state protocol to advertise both topology and VLAN membership. Packets are encapsulated at the edge either in MAC-in-MAC per IEEE 802.1ah or tagged per IEEE 80 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Spanning Tree Protocol
The Spanning Tree Protocol (STP) is a network protocol that builds a loop-free logical topology for Ethernet networks. The basic function of STP is to prevent bridge loops and the broadcast radiation that results from them. Spanning tree also allows a network design to include backup links providing fault tolerance if an active link fails. As the name suggests, STP creates a spanning tree that characterizes the relationship of nodes within a network of connected layer-2 bridges, and disables those links that are not part of the spanning tree, leaving a single active path between any two network nodes. STP is based on an algorithm that was invented by Radia Perlman while she was working for Digital Equipment Corporation. In 2001, the IEEE introduced Rapid Spanning Tree Protocol (RSTP) as 802.1w. RSTP provides significantly faster recovery in response to network changes or failures, introducing new convergence behaviors and bridge port roles to do this. RSTP was designed t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Intermediate System To Intermediate System
Intermediate System to Intermediate System (IS-IS, also written ISIS) is a routing protocol designed to move information efficiently within a computer network, a group of physically connected computers or similar devices. It accomplishes this by determining the best route for data through a packet switching network. The IS-IS protocol is defined in ISO/IEC 10589:2002 as an international standard within the Open Systems Interconnection (OSI) reference design. The Internet Engineering Task Force (IETF) republished IS-IS in , but that RFC was later marked as ''historic'' by because it republished a draft rather than a final version of the (International Organization for Standardization) ISO standard, causing confusion. IS-IS has been called "the ''de facto'' standard for large service provider network backbones." Description IS-IS is an interior gateway protocol, designed for use within an administrative domain or network. This is in contrast to exterior gateway protocols ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Link-state Protocol
Link-state routing protocols are one of the two main classes of routing protocols used in packet switching networks for computer communications, the others being distance-vector routing protocols. Examples of link-state routing protocols include Open Shortest Path First (OSPF) and Intermediate System to Intermediate System (IS-IS). The link-state protocol is performed by every ''switching node'' in the network (i.e., nodes that are prepared to forward packets; in the Internet, these are called routers). The basic concept of link-state routing is that every node constructs a ''map'' of the connectivity to the network, in the form of a graph, showing which nodes are connected to which other nodes. Each node then independently calculates the next best logical ''path'' from it to every possible destination in the network. Each collection of best paths will then form each node's routing table. This contrasts with distance-vector routing protocols, which work by having each node share ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
IS-IS
Intermediate System to Intermediate System (IS-IS, also written ISIS) is a routing protocol designed to move information efficiently within a computer network, a group of physically connected computers or similar devices. It accomplishes this by determining the best route for data through a packet switching network. The IS-IS protocol is defined in ISO/IEC 10589:2002 as an international standard within the Open Systems Interconnection (OSI) reference design. The Internet Engineering Task Force (IETF) republished IS-IS in , but that RFC was later marked as ''historic'' by because it republished a draft rather than a final version of the (International Organization for Standardization) ISO standard, causing confusion. IS-IS has been called "the ''de facto'' standard for large service provider network backbones." Description IS-IS is an interior gateway protocol, designed for use within an administrative domain or network. This is in contrast to exterior gateway protocols, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
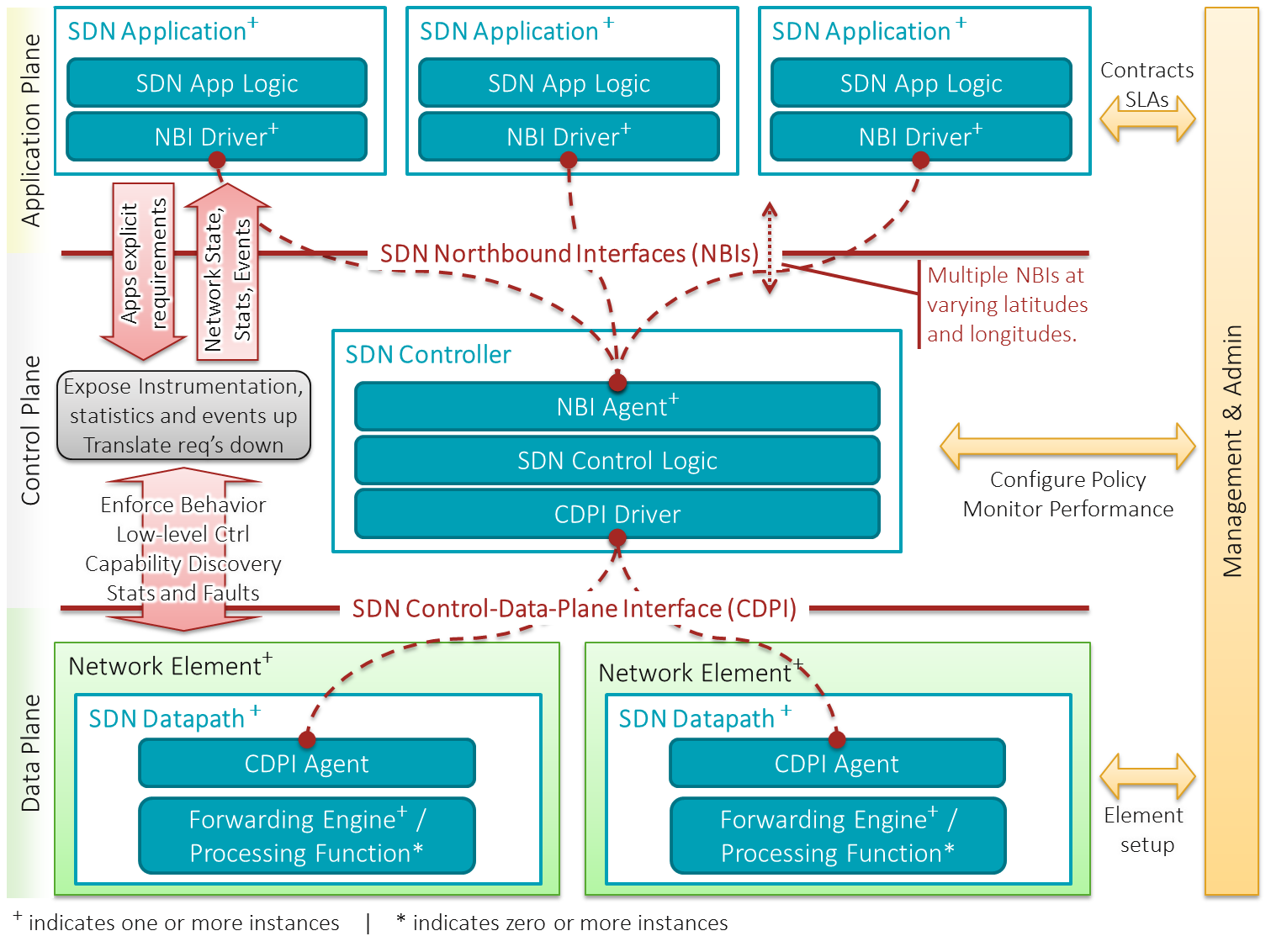
Software-defined Networking
Software-defined networking (SDN) technology is an approach to network management that enables dynamic, programmatically efficient network configuration in order to improve network performance and monitoring, making it more like cloud computing than traditional network management. SDN is meant to address the static architecture of traditional networks. SDN attempts to centralize network intelligence in one network component by disassociating the forwarding process of network packets (data plane) from the routing process ( control plane). The control plane consists of one or more controllers, which are considered the brain of the SDN network where the whole intelligence is incorporated. However, centralization has its own drawbacks when it comes to security, scalability and elasticity and this is the main issue of SDN. SDN was commonly associated with the OpenFlow protocol (for remote communication with network plane elements for the purpose of determining the path of network ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Multipath Routing
Multipath routing is a routing technique simultaneously using multiple alternative paths through a network. This can yield a variety of benefits such as fault tolerance, increased bandwidth, and improved security. Mobile networks To improve performance or fault tolerance, concurrent multipath routing (CMR) is often taken to mean simultaneous management and utilization of multiple available paths for the transmission of streams of data. The streams may be emanating from a single application or multiple applications. A stream is assigned a separate path, as uniquely possible given the number of paths available. If there are more streams than available paths, some streams will share paths. CMR provides better utilization of bandwidth by creating multiple transmission queues. It provides a degree of fault tolerance in that should a path fail, only the traffic assigned to that path is affected. There is also, ideally, an alternative path immediately available upon which to continue ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mesh Topology
A mesh network is a local area network topology in which the infrastructure nodes (i.e. bridges, switches, and other infrastructure devices) connect directly, dynamically and non-hierarchically to as many other nodes as possible and cooperate with one another to efficiently route data to and from clients. This lack of dependency on one node allows for every node to participate in the relay of information. Mesh networks dynamically self-organize and self-configure, which can reduce installation overhead. The ability to self-configure enables dynamic distribution of workloads, particularly in the event a few nodes should fail. This in turn contributes to fault-tolerance and reduced maintenance costs. Mesh topology may be contrasted with conventional star/tree local network topologies in which the bridges/switches are directly linked to only a small subset of other bridges/switches, and the links between these infrastructure neighbours are hierarchical. While star-and-tree topologi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
VLAN
A virtual local area network (VLAN) is any broadcast domain that is partitioned and isolated in a computer network at the data link layer ( OSI layer 2).IEEE 802.1Q-2011, ''1.4 VLAN aims and benefits'' In this context, virtual, refers to a physical object recreated and altered by additional logic, within the local area network. VLANs work by applying tags to network frames and handling these tags in networking systems – creating the appearance and functionality of network traffic that is physically on a single network but acts as if it is split between separate networks. In this way, VLANs can keep network applications separate despite being connected to the same physical network, and without requiring multiple sets of cabling and networking devices to be deployed. VLANs allow network administrators to group hosts together even if the hosts are not directly connected to the same network switch. Because VLAN membership can be configured through software, this can greatly simpli ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Interop
Interop is an annual information technology conference organised by Informa PLC. It takes place in the US and Tokyo (Japan) each year. 2016 marked Interop's (US) 30th anniversary and throughout that time, Interop has promoted interoperability and openness, beginning with IP networks and continuing in today's emerging cloud computing era. History The Las Vegas International Telecoms Show is called "the granddaddy of networking shows" because it was created in the late 1980s, a decade before the technology and internet bubble that made it a success. It reached a peak with 61,000 visitors at the 2001 edition, just before the bursting of this bubble, which resulted in a major stock market crash for this sector. This year's event was marked by innovation, and among the major telecom providers, the rivalry between Juniper Networks and Cisco Systems in the Terabit router market, while the so-called "alternative" operators, such as KPNQwest, Global Crossing and Carrier, launched revolut ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
2014 Winter Olympics
The 2014 Winter Olympics, officially called the XXII Olympic Winter Games (russian: XXII Олимпийские зимние игры, XXII Olimpiyskiye zimniye igry) and commonly known as Sochi 2014 (russian: Сочи 2014), was an international winter multi-sport event that was held from 7 to 23 February 2014 in Sochi, Russia. Opening rounds in certain events were held on 6 February 2014, the day before the opening ceremony. These were the first Olympic Games under the International Olympic Committee (IOC) presidency of Thomas Bach. Both the Olympics and Paralympics were organized by the Sochi Organizing Committee (SOOC). Sochi was selected as the host city in July 2007, during the 119th IOC Session held in Guatemala City. It was the first Olympics to be held in a CIS state after the breakup of the Soviet Union in 1991. The Soviet Union was previously the host nation for the 1980 Summer Olympics in Moscow. A record ninety-eight events in fifteen winter spo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Internet Engineering Task Force
The Internet Engineering Task Force (IETF) is a standards organization for the Internet and is responsible for the technical standards that make up the Internet protocol suite (TCP/IP). It has no formal membership roster or requirements and all its participants are volunteers. Their work is usually funded by employers or other sponsors. The IETF was initially supported by the federal government of the United States but since 1993 has operated under the auspices of the Internet Society, an international non-profit organization. Organization The IETF is organized into a large number of working groups and birds of a feather informal discussion groups, each dealing with a specific topic. The IETF operates in a bottom-up task creation mode, largely driven by these working groups. Each working group has an appointed chairperson (or sometimes several co-chairs); a charter that describes its focus; and what it is expected to produce, and when. It is open to all who want to part ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |