|
2020 United States Treasury And Department Of Commerce Data Breach
In 2020, a major cyberattack suspected to have been committed by a group backed by the Russian government penetrated thousands of organizations globally including multiple parts of the United States federal government, leading to a series of data breaches. The cyberattack and data breach were reported to be among the worst cyber-espionage incidents ever suffered by the U.S., due to the sensitivity and high profile of the targets and the long duration (eight to nine months) in which the hackers had access. Within days of its discovery, at least 200 organizations around the world had been reported to be affected by the attack, and some of these may also have suffered data breaches. Affected organizations worldwide included NATO, the U.K. government, the European Parliament, Microsoft and others. The attack, which had gone undetected for months, was first publicly reported on December 13, 2020, and was initially only known to have affected the U.S. Treasury Department and the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
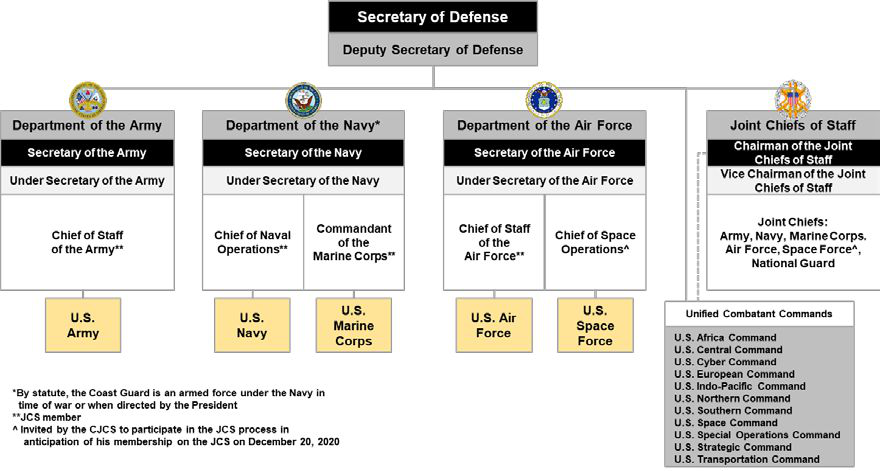
United States Department Of Defense
The United States Department of Defense (DoD, USDOD, or DOD) is an United States federal executive departments, executive department of the federal government of the United States, U.S. federal government charged with coordinating and supervising the six U.S. armed services: the United States Army, Army, United States Navy, Navy, United States Marine Corps, Marines, United States Air Force, Air Force, United States Space Force, Space Force, the United States Coast Guard, Coast Guard for some purposes, and related functions and agencies. As of November 2022, the department has over 1.4 million active-duty uniformed personnel in the six armed services. It also supervises over 778,000 National Guard (United States), National Guard and reservist personnel, and over 747,000 civilians, bringing the total to over 2.91 million employees. Headquartered at the Pentagon in Arlington County, Virginia, just outside Washington, D.C., the Department of Defense's stated mission is "to provid ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Software Bug
A software bug is a design defect ( bug) in computer software. A computer program with many or serious bugs may be described as ''buggy''. The effects of a software bug range from minor (such as a misspelled word in the user interface) to severe (such as frequent crashing). In 2002, a study commissioned by the US Department of Commerce's National Institute of Standards and Technology concluded that "software bugs, or errors, are so prevalent and so detrimental that they cost the US economy an estimated $59 billion annually, or about 0.6 percent of the gross domestic product". Since the 1950s, some computer systems have been designed to detect or auto-correct various software errors during operations. History Terminology ''Mistake metamorphism'' (from Greek ''meta'' = "change", ''morph'' = "form") refers to the evolution of a defect in the final stage of software deployment. Transformation of a ''mistake'' committed by an analyst in the early stages of the softw ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cyber-espionage
Cyber espionage, cyber spying, or cyber-collection is the act or practice of obtaining secrets and information without the permission and knowledge of the holder of the information using methods on the Internet, networks or individual computers through the use of proxy servers, hacker (computer security), cracking techniques and malicious software including Trojan horse (computing), Trojan horses and spyware. Cyber espionage can be used to target various actors – individuals, competitors, rivals, groups, governments, and others – in order to obtain personal, economic, political or military advantages. It may wholly be perpetrated online from computer desks of professionals on bases in far away countries or may involve infiltration at home by computer trained conventional Espionage, spies and mole (espionage), moles or in other cases may be the criminal handiwork of amateur malicious hackers and programmer, software programmers. History Cyber spying started as far back as 1996 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Federal Government Of The United States
The Federal Government of the United States of America (U.S. federal government or U.S. government) is the Federation#Federal governments, national government of the United States. The U.S. federal government is composed of three distinct branches: United States Congress, legislative, President of the United States, executive, and Federal judiciary of the United States, judicial. Powers of these three branches are defined and vested by the Constitution of the United States, U.S. Constitution, which has been in continuous effect since May 4, 1789. The powers and duties of these branches are further defined by Act of Congress, Acts of Congress, including the creation of United States federal executive departments, executive departments and courts subordinate to the Supreme Court of the United States, U.S. Supreme Court. In the Federalism in the United States, federal division of power, the federal government shares sovereignty with each of the 50 states in their respective t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cyberattack
A cyberattack (or cyber attack) occurs when there is an unauthorized action against computer infrastructure that compromises the confidentiality, integrity, or availability of its content. The rising dependence on increasingly complex and interconnected computer systems in most domains of life is the main factor that causes vulnerability to cyberattacks, since virtually all computer systems have bugs that can be exploited by attackers. Although it is impossible or impractical to create a perfectly secure system, there are many defense mechanisms that can make a system more difficult to attack, making information security a field of rapidly increasing importance in the world today. Perpetrators of a cyberattack can be criminals, hacktivists, or states. They attempt to find weaknesses in a system, exploit them and create malware to carry out their goals, and deliver it to the targeted system. Once installed, the malware can have a variety of effects depending on its purpose. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Foreign Intelligence Service (Russia)
The Foreign Intelligence Service (SVR) is the civilian foreign intelligence agency of Russia. The SVR succeeded the First Chief Directorate of the KGB in December 1991.The Security Organs of the Russian Federation: A Brief History 1991–2004' by Jonathan Littell, Psan Publishing House 2006. The SVR has its headquarters in the Yasenevo District of Moscow with its director reporting directly to the President of the Russian Federation. Unlike the Russian Federal Security Service (FSB), the SVR is tasked with intelligence and espionage activities outside the Russian Federation. A small service, it works collaboratively with its military intelligence counterpart, the Main Intelligence Directorate, better known as the GRU. As of 1997, the GRU reportedly deployed six times as many spies in foreign countries as the SVR. The SVR is authorized to negotiate intelligence-sharing arrangements with foreign governments, particularly on matters of counterterrorism, and is tasked with pr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Federal Security Service
The Federal Security Service of the Russian Federation �СБ, ФСБ России (FSB) is the principal security agency of Russia and the main successor agency to the Soviet Union's KGB; its immediate predecessor was the Federal Counterintelligence Service (FSK), which was reorganized into the FSB in 1995. The three major structural successor components of the former KGB that remain administratively independent of the FSB are the Foreign Intelligence Service (SVR), the Federal Protective Service (FSO), and the Main Directorate of Special Programs of the President of the Russian Federation (GUSP). The primary responsibilities are within the country and include counter-intelligence, internal and border security, counterterrorism, surveillance and investigating some other types of serious crimes and federal law violations. It is headquartered in Lubyanka Square, Moscow's center, in the main building of the former KGB. The director of the FSB is appointed by and direct ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cozy Bear
Cozy Bear is a Russian advanced persistent threat hacker group believed to be associated with intelligence agencies of Russia, Russian foreign intelligence by United States Intelligence Community, United States intelligence agencies and those of NATO, allied countries. Dutch General Intelligence and Security Service, signals intelligence (AIVD) and United States Intelligence Community, American intelligence had been monitoring the group since 2014 and was able to link the hacker group to the Russian Foreign Intelligence Service (Russia), foreign intelligence agency (SVR) after compromising security cameras in their office. CrowdStrike and Estonian Foreign Intelligence Service, Estonian intelligence reported a tentative link to the Russian Federal Security Service, domestic/foreign intelligence agency (FSB). Various groups designate it CozyCar, CozyDuke, Dark Halo, The Dukes, Midnight Blizzard, NOBELIUM, Office Monkeys, StellarParticle, UNC2452 with a tentative connection to Russ ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Berserk Bear
Berserk Bear (also known as BROMINE, Crouching Yeti, Dragonfly, Dragonfly 2.0, DYMALLOY, Energetic Bear, Ghost Blizzard, Havex, IRON LIBERTY, Koala, or TeamSpy) is a Russian cyber espionage group, sometimes known as an advanced persistent threat. According to the United States, the group is composed of "Federal Security Service, FSB hackers," either those directly employed by the FSB or Russian civilian, criminal hackers coerced into contracting as FSB hackers while still freelancing or Side job, moonlighting as criminal hackers. Four accused Berserk Bear participants, three FSB staff and one civilian, have been indicted in the United States and are regarded by the United States Department of Justice as fugitives. Activities Berserk Bear specializes in compromising utilities infrastructure, especially that belonging to companies responsible for water or energy distribution. It has performed these activities in at least Germany and the U.S. These operations are targeted towards surv ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Reuters
Reuters ( ) is a news agency owned by Thomson Reuters. It employs around 2,500 journalists and 600 photojournalists in about 200 locations worldwide writing in 16 languages. Reuters is one of the largest news agencies in the world. The agency was established in London in 1851 by Paul Reuter. The Thomson Corporation of Canada acquired the agency in a 2008 corporate merger, resulting in the formation of the Thomson Reuters Corporation. In December 2024, Reuters was ranked as the 27th most visited news site in the world, with over 105 million monthly readers. History 19th century Paul Julius Reuter worked at a book-publishing firm in Berlin and was involved in distributing radical pamphlets at the beginning of the Revolutions of 1848. These publications brought much attention to Reuter, who in 1850 developed a prototype news service in Aachen using homing pigeons and electric telegraphy from 1851 on, in order to transmit messages between Brussels and Aachen, in what today is Aa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
United States National Security Agency
The National Security Agency (NSA) is an intelligence agency of the United States Department of Defense, under the authority of the director of national intelligence (DNI). The NSA is responsible for global monitoring, collection, and processing of information and data for global intelligence and counterintelligence purposes, specializing in a discipline known as signals intelligence (SIGINT). The NSA is also tasked with the protection of U.S. communications networks and information systems. The NSA relies on a variety of measures to accomplish its mission, the majority of which are clandestine. The NSA has roughly 32,000 employees. Originating as a unit to decipher coded communications in World War II, it was officially formed as the NSA by President Harry S. Truman in 1952. Between then and the end of the Cold War, it became the largest of the U.S. intelligence organizations in terms of personnel and budget. Still, information available as of 2013 indicates that the Centr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Coordinated Vulnerability Disclosure
In computer security, coordinated vulnerability disclosure (CVD, sometimes known as responsible disclosure) is a vulnerability disclosure model in which a vulnerability or an issue is disclosed to the public only after the responsible parties have been allowed sufficient time to patch or remedy the vulnerability or issue. This coordination distinguishes the CVD model from the " full disclosure" model. Developers of hardware and software often require time and resources to repair their mistakes. Often, it is ethical hackers who find these vulnerabilities. Hackers and computer security scientists have the opinion that it is their social responsibility to make the public aware of vulnerabilities. Hiding problems could cause a feeling of false security. To avoid this, the involved parties coordinate and negotiate a reasonable period of time for repairing the vulnerability. Depending on the potential impact of the vulnerability, the expected time needed for an emergency fix or work ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |