|
Trusted Platform Module
Trusted Platform Module (TPM, also known as ISO/IEC 11889) is an international standard for a secure cryptoprocessor, a dedicated microcontroller designed to secure hardware through integrated cryptographic keys. The term can also refer to a chip conforming to the standard. TPM is used for digital rights management (DRM), Windows Defender, Windows Domain logon, protection and enforcement of software licenses, and prevention of cheating in online games. One of Windows 11's system requirements is TPM 2.0. Microsoft has stated that this is to help increase security against firmware and ransomware attacks. History Trusted Platform Module (TPM) was conceived by a computer industry consortium called Trusted Computing Group (TCG). It evolved into ''TPM Main Specification Version 1.2'' which was standardized by International Organization for Standardization (ISO) and International Electrotechnical Commission (IEC) in 2009 as ISO/IEC 11889:2009. ''TPM Main Specification Version 1. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
International Organization For Standardization
The International Organization for Standardization (ISO ) is an international standard development organization composed of representatives from the national standards organizations of member countries. Membership requirements are given in Article 3 of the ISO Statutes. ISO was founded on 23 February 1947, and (as of November 2022) it has published over 24,500 international standards covering almost all aspects of technology and manufacturing. It has 809 Technical committees and sub committees to take care of standards development. The organization develops and publishes standardization in all technical and nontechnical fields other than Electrical engineering, electrical and electronic engineering, which is handled by the International Electrotechnical Commission, IEC.Editors of Encyclopedia Britannica. 3 June 2021.International Organization for Standardization" ''Encyclopedia Britannica''. Retrieved 2022-04-26. It is headquartered in Geneva, Switzerland, and works in 167 coun ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
RSA (algorithm)
RSA (Rivest–Shamir–Adleman) is a public-key cryptosystem that is widely used for secure data transmission. It is also one of the oldest. The acronym "RSA" comes from the surnames of Ron Rivest, Adi Shamir and Leonard Adleman, who publicly described the algorithm in 1977. An equivalent system was developed secretly in 1973 at Government Communications Headquarters (GCHQ) (the British signals intelligence agency) by the English mathematician Clifford Cocks. That system was declassified in 1997. In a public-key cryptosystem, the encryption key is public and distinct from the decryption key, which is kept secret (private). An RSA user creates and publishes a public key based on two large prime numbers, along with an auxiliary value. The prime numbers are kept secret. Messages can be encrypted by anyone, via the public key, but can only be decoded by someone who knows the prime numbers. The security of RSA relies on the practical difficulty of factoring the product of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Trusted Execution Technology
Intel Trusted Execution Technology (Intel TXT, formerly known as LaGrande Technology) is a computer hardware technology whose primary goals are: * Attestation of the authenticity of a platform and its operating system. * Assuring that an authentic operating system starts in a trusted environment, which can then be considered trusted. * Provision of a trusted operating system with additional security capabilities not available to an unproven one. Intel TXT uses a Trusted Platform Module (TPM) and cryptographic techniques to provide measurements of software and platform components so that system software as well as local and remote management applications may use those measurements to make trust decisions. It complements Intel Management Engine. This technology is based on an industry initiative by the Trusted Computing Group (TCG) to promote safer computing. It defends against software-based attacks aimed at stealing sensitive information by corrupting system or BIOS code, or mod ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Microsoft Office 365
Microsoft 365 is a product family of productivity software, collaboration and cloud-based services owned by Microsoft. It encompasses online services such as Outlook.com, OneDrive, Microsoft Teams, programs formerly marketed under the name Microsoft Office (including applications such as Word, Excel, PowerPoint, and Outlook on Microsoft Windows, macOS, mobile devices, and on the web), enterprise products and services associated with these products such as Exchange Server, SharePoint, and Yammer. It also covers subscription plans encompassing these products, including those that include subscription-based licenses to desktop and mobile software, and hosted email and intranet services. The branding Office 365 was first introduced in 2010 to refer to a subscription-based software as a service platform for the corporate market, including hosted services such as Exchange, SharePoint, and Lync Server, and Office on the web. Some plans also included licenses for the Microsoft Offic ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
PrivateCore
PrivateCore is a venture-backed startup located in Palo Alto, California that develops software to secure server data through server attestation and memory encryption. The company's attestation and memory encryption technology fills a gap that exists between “ data in motion” encryption ( TLS, email encryption) and “ data at rest” encryption (disk encryption, tape encryption) by protecting “data in use” ( random access memory). PrivateCore memory encryption technology protects against threats to servers such as cold boot attacks, hardware advanced persistent threats, rootkits/bootkits, computer hardware supply chain attacks, and physical threats to servers from insiders. PrivateCore was acquired by Facebook (now Meta Platforms) on 7 August 2014. History PrivateCore was founded in 2011 by security veterans from VMware and Google with seed funding from Foundation Capital. PrivateCore “virtualizes” physical security and enables service providers and enterprises de ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
BitLocker
BitLocker is a full volume encryption feature included with Microsoft Windows versions starting with Windows Vista. It is designed to protect data by providing encryption for entire volumes. By default, it uses the AES encryption algorithm in cipher block chaining (CBC) or XTS mode with a 128-bit or 256-bit key. CBC is not used over the whole disk; it is applied to each individual sector. History BitLocker originated as a part of Microsoft's Next-Generation Secure Computing Base architecture in 2004 as a feature tentatively codenamed "Cornerstone" and was designed to protect information on devices, particularly if a device was lost or stolen; another feature, titled "Code Integrity Rooting", was designed to validate the integrity of Microsoft Windows boot and system files. When used in conjunction with a compatible Trusted Platform Module (TPM), BitLocker can validate the integrity of boot and system files before decrypting a protected volume; an unsuccessful validation ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
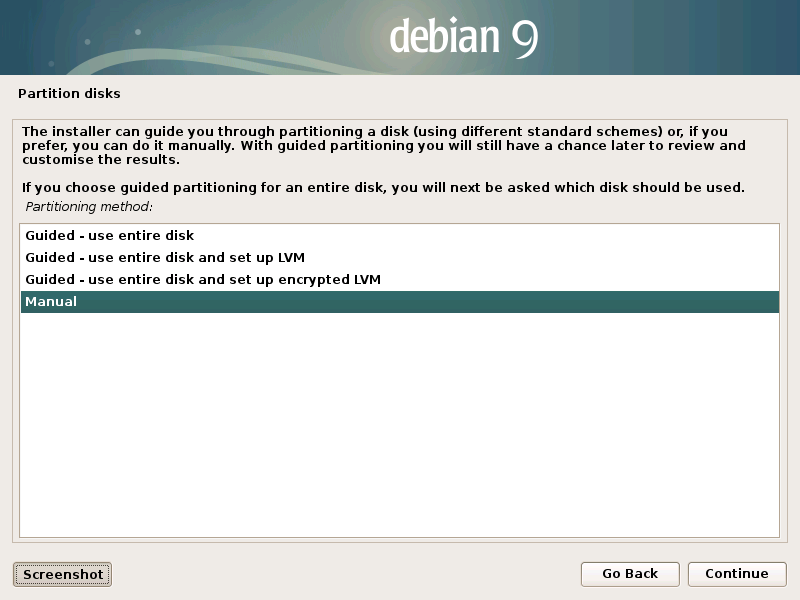
Linux Unified Key Setup
The Linux Unified Key Setup (LUKS) is a disk encryption specification created by Clemens Fruhwirth in 2004 and was originally intended for Linux. While most disk encryption software implements different, incompatible, and undocumented formats, LUKS implements a platform-independent standard on-disk format for use in various tools. This not only facilitates compatibility and interoperability among different programs, but also assures that they all implement password management in a secure and documented manner. Description LUKS is used to encrypt a block device. The contents of the encrypted device are arbitrary, and therefore any filesystem can be encrypted, including swap partitions. There is an unencrypted header at the beginning of an encrypted volume, which allows up to 8 (LUKS1) or 32 (LUKS2) encryption keys to be stored along with encryption parameters such as cipher type and key size. The presence of this header is a major difference between LUKS and plain dm-crypt, s ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Root Of Trust
In cryptographic systems with hierarchical structure, a trust anchor is an authoritative entity for which trust is assumed and not derived. In the X.509 architecture, a root certificate would be the trust anchor from which the whole chain of trust is derived. The trust anchor must be in the possession of the trusting party beforehand to make any further certificate path validation possible. Most operating systems provide a built-in list of self-signed root certificates to act as trust anchors for applications. The Firefox Mozilla Firefox, or simply Firefox, is a free and open-source web browser developed by the Mozilla Foundation and its subsidiary, the Mozilla Corporation. It uses the Gecko rendering engine to display web pages, which implements current ... web browser also provides its own list of trust anchors. The end-user of an operating system or web browser is implicitly trusting in the correct operation of that software, and the software manufacturer in tur ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Unified Extensible Firmware Interface
UEFI (Unified Extensible Firmware Interface) is a set of specifications written by the UEFI Forum. They define the architecture of the platform firmware used for booting and its interface for interaction with the operating system. Examples of firmware that implement these specifications are AMI Aptio, Phoenix SecureCore, TianoCore EDK II and InsydeH2O. UEFI replaces the BIOS which was present in the boot ROM of all personal computers that are IBM PC-compatible, although it can provide backwards compatibility with the BIOS using CSM booting. Intel developed the original ''Extensible Firmware Interface'' (''EFI'') specifications. Some of the EFI's practices and data formats mirror those of Microsoft Windows. In 2005, UEFI deprecated EFI 1.10 (the final release of EFI). UEFI is independent of platform and programming language, but C is used for the reference implementation TianoCore EDKII. History The original motivation for EFI came during early development of the first ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Application Software
Application may refer to: Mathematics and computing * Application software, computer software designed to help the user to perform specific tasks ** Application layer, an abstraction layer that specifies protocols and interface methods used in a communications network * Function application, in mathematics and computer science Processes and documents * Application for employment, a form or forms that an individual seeking employment must fill out * College application, the process by which prospective students apply for entry into a college or university * Patent application, a document filed at a patent office to support the grant of a patent Other uses * Application (virtue), a characteristic encapsulated in diligence * Topical application A topical medication is a medication that is applied to a particular place on or in the body. Most often topical medication means application to body surfaces such as the skin or mucous membranes to treat ailments via a large range ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Boot Process
In computing, booting is the process of starting a computer as initiated via hardware such as a button or by a software command. After it is switched on, a computer's central processing unit (CPU) has no software in its main memory, so some process must load software into memory before it can be executed. This may be done by hardware or firmware in the CPU, or by a separate processor in the computer system. Restarting a computer also is called rebooting, which can be "hard", e.g. after electrical power to the CPU is switched from off to on, or "soft", where the power is not cut. On some systems, a soft boot may optionally clear RAM to zero. Both hard and soft booting can be initiated by hardware such as a button press or by a software command. Booting is complete when the operative runtime system, typically the operating system and some applications,Including daemons. is attained. The process of returning a computer from a state of sleep (suspension) does not involve b ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |