|
Privilege Escalation
Privilege escalation is the act of exploiting a bug, a design flaw, or a configuration oversight in an operating system or software application to gain elevated access to resources that are normally protected from an application or user. The result is that an application or user with more privileges than intended by the application developer or system administrator can perform unauthorized actions. Background Most computer systems are designed for use with multiple user accounts, each of which has abilities known as privileges. Common privileges include viewing and editing files or modifying system files. Privilege escalation means users receive privileges they are not entitled to. These privileges can be used to delete files, view private information, or install unwanted programs such as viruses. It usually occurs when a system has a bug that allows security to be bypassed or, alternatively, has flawed design assumptions about how it will be used. Privilege escalation occurs ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Privilege Escalation Diagram
Privilege may refer to: Arts and entertainment * Privilege (film), ''Privilege'' (film), a 1967 film directed by Peter Watkins * Privilege (Ivor Cutler album), ''Privilege'' (Ivor Cutler album), 1983 * Privilege (Television Personalities album), ''Privilege'' (Television Personalities album), 1990 * ''Privilege (Abridged)'', an album by Parenthetical Girls, 2013 * "Privilege (Set Me Free)", a 1978 song by the Patti Smith Group * Privilege (Law & Order: Criminal Intent), "Privilege" (''Law & Order: Criminal Intent''), a television episode * "Privilege", a short story by Frederick Forsyth included in the collection ''No Comebacks'' * "Privilege", a song by Kevin Federline from the album Playing with Fire (Kevin Federline album), ''Playing with Fire'' (Kevin Federline album) Business * Privilege (insurance company), a division of the Royal Bank of Scotland * Privilege Ibiza, a nightclub in Ibiza, Spain * Privilege Style, a Spanish charter airline * Printing privilege, a precursor ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Kill (Unix)
In computing, kill is a command that is used in several popular operating systems to send signals to running processes. Implementations Unix and Unix-like In Unix and Unix-like operating systems, kill is a command used to send a signal to a process. By default, the message sent is the termination signal, which requests that the process exit. But ''kill'' is something of a misnomer; the signal sent may have nothing to do with process killing. The kill command is a wrapper around the kill() system call, which sends signals to processes or process groups on the system, referenced by their numeric process IDs (PIDs) or process group IDs (PGIDs). kill is always provided as a standalone utility as defined by the POSIX standard. However, most shells have built-in kill commands that may slightly differ from it. There are many different signals that can be sent (see ''signal'' for a full list), although the signals in which users are generally most interested are SIGTER ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Core Dump
In computing, a core dump, memory dump, crash dump, storage dump, system dump, or ABEND dump consists of the recorded state of the working Computer storage, memory of a computer program at a specific time, generally when the program has crash (computing), crashed or otherwise terminated abnormally. In practice, other key pieces of Context switch, program state are usually dumped at the same time, including the processor registers, which may include the program counter and stack pointer, memory management information, and other processor and operating system flags and information. A snapshot dump (or snap dump) is a memory dump requested by the computer operator or by the running program, after which the program is able to continue. Core dumps are often used to assist in diagnosing and debugging errors in computer programs. On many operating systems, a fatal exception in a program automatically triggers a core dump. By extension, the phrase "to dump core" has come to mean in many ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Linux Kernel
The Linux kernel is a Free and open-source software, free and open source Unix-like kernel (operating system), kernel that is used in many computer systems worldwide. The kernel was created by Linus Torvalds in 1991 and was soon adopted as the kernel for the GNU operating system (OS) which was created to be a free software, free replacement for Unix. Since the late 1990s, it has been included in many Linux distributions, operating system distributions, many of which are called Linux. One such Linux kernel operating system is Android (operating system), Android which is used in many mobile and embedded devices. Most of the kernel code is written in C (programming language), C as supported by the GNU compiler collection (GCC) which has extensions beyond standard C. The code also contains assembly language, assembly code for architecture-specific logic such as optimizing memory use and task execution. The kernel has a Modular programming, modular design such that modules can be inte ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
National Vulnerability Database
The National Vulnerability Database (NVD) is the U.S. government repository of standards-based vulnerability management data represented using the Security Content Automation Protocol (SCAP). This data enables automation of vulnerability management, security measurement, and compliance. NVD includes databases of security checklists, security related software flaws, misconfigurations, product names, and impact metrics. NVD supports the Information Security Automation Program (ISAP). NVD is managed by the U.S. government agency the National Institute of Standards and Technology The National Institute of Standards and Technology (NIST) is an agency of the United States Department of Commerce whose mission is to promote American innovation and industrial competitiveness. NIST's activities are organized into Outline of p ... (NIST). On Friday March 8, 2013, the database was taken offline after it was discovered that the system used to run multiple government sites had been compromi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
NIST
The National Institute of Standards and Technology (NIST) is an agency of the United States Department of Commerce whose mission is to promote American innovation and industrial competitiveness. NIST's activities are organized into physical science laboratory programs that include nanoscale science and technology, engineering, information technology, neutron research, material measurement, and physical measurement. From 1901 to 1988, the agency was named the National Bureau of Standards. History Background The Articles of Confederation, ratified by the colonies in 1781, provided: The United States in Congress assembled shall also have the sole and exclusive right and power of regulating the alloy and value of coin struck by their own authority, or by that of the respective states—fixing the standards of weights and measures throughout the United States. Article 1, section 8, of the Constitution of the United States, ratified in 1789, granted these powers to the new Co ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
TrustedInstaller
Windows Resource Protection is a feature first introduced in Windows Vista and Windows Server 2008. It is available in all subsequent Windows operating systems, and replaces Windows File Protection. Windows Resource Protection prevents the replacement of critical system files, registry keys and folders. Protecting these resources prevents system crashes. The way it protects resources differs entirely from the method used by Windows File Protection. Overview Windows Resource Protection (WRP) works by registering for notification of file changes in Winlogon. If any changes are detected to a protected system file, the modified file is restored from a cached copy located in . Windows Resource Protection works by setting discretionary access control lists (DACLs) and access control lists (ACLs) defined for protected resources. Permission for full access to modify WRP-protected resources is restricted to the processes using the ''Windows Modules Installer service'' (TrustedInstalle ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Driver (software)
A driver in software provides a programming interface to control and manage specific lower-level interfaces that are often linked to a specific type of hardware, or other low-level service. In the case of hardware, the specific subclass of drivers controlling physical or virtual hardware devices are known as device drivers. Example A client library for connecting to a database is often known as a driver, for example, the MySQL MySQL () is an Open-source software, open-source relational database management system (RDBMS). Its name is a combination of "My", the name of co-founder Michael Widenius's daughter My, and "SQL", the acronym for Structured Query Language. A rel ... native driver for PHP. References Computing terminology Application programming interfaces Computer libraries {{Software-type-stub ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Windows Registry
The Windows Registry is a hierarchical database that stores low-level settings for the Microsoft Windows operating system and for applications that opt to use the registry. The kernel, device drivers, services, Security Accounts Manager, and user interfaces can all use the registry. The registry also allows access to counters for profiling system performance. In other words, the registry or Windows Registry contains information, settings, options, and other values for programs and hardware installed on all versions of Microsoft Windows operating systems. For example, when a program is installed, a new subkey containing settings such as a program's location, its version, and how to start the program, are all added to the Windows Registry. When introduced with Windows 3.1, the Windows Registry primarily stored configuration information for COM-based components. Windows 95 and Windows NT extended its use to rationalize and centralize the information in the profusion of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Executable
In computer science, executable code, an executable file, or an executable program, sometimes simply referred to as an executable or binary, causes a computer "to perform indicated tasks according to encoded instruction (computer science), instructions", as opposed to a data (computing), data file that must be interpreted (parser, parsed) by an interpreter (computing), interpreter to be functional. The exact interpretation depends upon the use. "Instructions" is traditionally taken to mean machine code instructions for a physical central processing unit, CPU. In some contexts, a file containing scripting instructions (such as bytecode) may also be considered executable. Generation of executable files Executable files can be hand-coded in machine language, although it is far more convenient to develop software as source code in a high-level language that can be easily understood by humans. In some cases, source code might be specified in assembly language instead, which rema ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
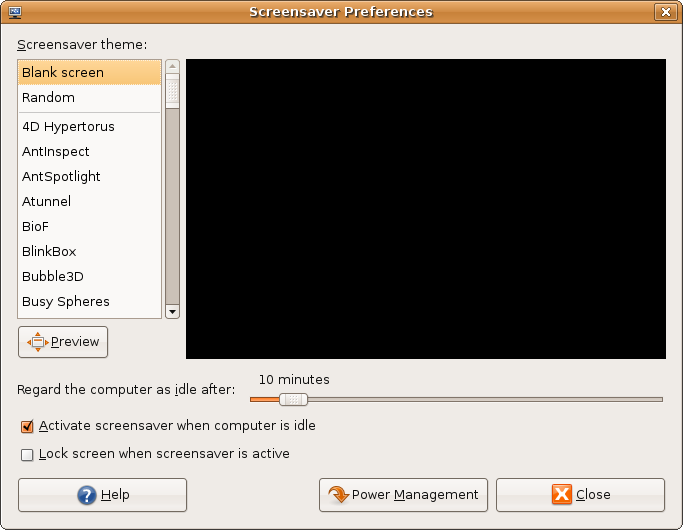
Screensaver
A screensaver (or screen saver) is a computer program that blanks the display screen or fills it with moving images or patterns when the computer has been idle for a designated time. The original purpose of screensavers was to prevent phosphor screen burn-in, burn-in on Cathode-ray tube, CRT or plasma display, plasma computer monitors (hence the name). Though most modern monitors are not susceptible to this issue (with the notable exception of OLED technology, which has individual pixels vulnerable to burnout), screensaver programs are still used for other purposes. Screensavers are often set up to offer a basic layer of computer security, security by requiring a password to re-access the device. Some screensaver programs also use otherwise-idle computer resources to do useful work, such as processing for volunteer computing projects. As well as computers, modern television operating systems, media players, and other digital entertainment systems may include optional screensavers ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |