|
Surveillance Video Cameras, Gdynia
Surveillance is the monitoring of behavior, many activities, or information for the purpose of information gathering, influencing, managing or directing. This can include observation from a distance by means of electronic equipment, such as closed-circuit television (CCTV), or interception of electronically transmitted information like Internet traffic. It can also include simple technical methods, such as human intelligence gathering and postal interception. Surveillance is used by citizens for protecting their neighborhoods. And by governments for intelligence gathering - including espionage, prevention of crime, the protection of a process, person, group or object, or the investigation of crime. It is also used by criminal organizations to plan and commit crimes, and by businesses to gather intelligence on criminals, their competitors, suppliers or customers. Religious organisations charged with detecting heresy and heterodoxy may also carry out surveillance. Auditors car ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Surveillance Video Cameras, Gdynia
Surveillance is the monitoring of behavior, many activities, or information for the purpose of information gathering, influencing, managing or directing. This can include observation from a distance by means of electronic equipment, such as closed-circuit television (CCTV), or interception of electronically transmitted information like Internet traffic. It can also include simple technical methods, such as human intelligence gathering and postal interception. Surveillance is used by citizens for protecting their neighborhoods. And by governments for intelligence gathering - including espionage, prevention of crime, the protection of a process, person, group or object, or the investigation of crime. It is also used by criminal organizations to plan and commit crimes, and by businesses to gather intelligence on criminals, their competitors, suppliers or customers. Religious organisations charged with detecting heresy and heterodoxy may also carry out surveillance. Auditors car ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Espionage
Espionage, spying, or intelligence gathering is the act of obtaining secret or confidential information (intelligence) from non-disclosed sources or divulging of the same without the permission of the holder of the information for a tangible benefit. A person who commits espionage is called an ''espionage agent'' or ''spy''. Any individual or spy ring (a cooperating group of spies), in the service of a government, company, criminal organization, or independent operation, can commit espionage. The practice is clandestine, as it is by definition unwelcome. In some circumstances, it may be a legal tool of law enforcement and in others, it may be illegal and punishable by law. Espionage is often part of an institutional effort by a government or commercial concern. However, the term tends to be associated with state spying on potential or actual enemies for military purposes. Spying involving corporations is known as industrial espionage. One of the most effective ways ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Van Eck Phreaking
Van Eck phreaking, also known as Van Eck radiation, is a form of eavesdropping in which special equipment is used to pick up side-band electromagnetic emissions from electronic devices that correlate to hidden signals or data to recreate these signals or data to spy on the electronic device. Side-band electromagnetic radiation emissions are present in (and with the proper equipment, can be captured from) keyboards, computer displays, printers, and other electronic devices. In 1985, Wim van Eck published the first unclassified technical analysis of the security risks of emanations from computer monitors. This paper caused some consternation in the security community, which had previously believed that such monitoring was a highly sophisticated attack available only to governments; van Eck successfully eavesdropped on a real system, at a range of hundreds of metres, using just $15 worth of equipment plus a television set. As a consequence of this research, such emanations are someti ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
CIPAV
The Computer and Internet Protocol Address Verifier (CIPAV) is a data gathering tool that the Federal Bureau of Investigation (FBI) uses to track and gather location data on suspects under electronic surveillance. The software operates on the target computer much like other forms of spyware, whereas it is unknown to the operator that the software has been installed and is monitoring and reporting on their activities. The CIPAV captures location-related information, such as: IP address, MAC address, open ports, running programs, operating system and installed application registration and version information, default web browser, and last visited URL. Once that initial inventory is conducted, the CIPAV slips into the background and silently monitors all outbound communication, logging every IP address to which the computer connects, and time and date stamping each. The CIPAV made headlines in July, 2007, when its use was exposed in open court during an investigation of a teen who ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Magic Lantern (software)
Magic Lantern is keystroke logging software created by the United States' Federal Bureau of Investigation (FBI). Magic Lantern was first reported in a column by Bob Sullivan of MSNBC on November 20, 2001 and by Ted Bridis of the Associated Press. Methodology Magic Lantern can reportedly be installed remotely, via an e-mail attachment or by exploiting common operating system vulnerabilities, unlike previous keystroke logger programs used by the FBI. It has been described as a virus and a Trojan horse. It is not known how the program might store or communicate the recorded keystrokes. Purpose In response to a Freedom of Information Act request filed in 2000 by the Electronic Privacy Information Center, the FBI released a series of unclassified documents relating to Carnivore, which included the "Enhanced Carnivore Project Plan". Sullivan's confidential source said that redacted portions of that document mention "Cyber Knight", Example deployment method The FBI intends to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
ECHELON
ECHELON, originally a secret government code name, is a surveillance program (signals intelligence/SIGINT collection and analysis network) operated by the five signatory states to the UKUSA Security Agreement:Given the 5 dialects that use the terms, UKUSA can be pronounced from "You-Q-SA" to "Oo-Coo-SA", AUSCANNZUKUS can be pronounced from "Oz-Can-Zuke-Us" to "Orse-Can-Zoo-Cuss". :From Talk:UKUSA Agreement: "Per documents officially released by both the Government Communications Headquarters and the National Security Agency, this agreement is referred to as the UKUSA Agreement. This name is subsequently used by media sources reporting on the story, as written in new references used for the article. The NSA press release provides a pronunciation guide, indicating that "UKUSA" should not be read as two separate entities.(National Security Agency)" Australia, Canada, New Zealand, the United Kingdom and the United States, also known as the Five Eyes. Created in the late 196 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Narus (company)
Narus Inc. was a software company and vendor of big data analytics for cybersecurity. History In 1997, Ori Cohen, Vice President of Business and Technology Development for VDONet, founded Narus with Stas Khirman in Israel. Presently, they are employed with Deutsche Telekom AG and are not members of Narus' Executive Team. In 2010, Narus became a subsidiary of Boeing, located in Sunnyvale, California. In 2015, Narus was sold to Symantec. Management In 2004, Narus employed former Deputy Director of the National Security Agency, William Crowell as a director. From the Press Release announcing this: Narus Software Narus software primarily captures various computer network traffic in real-time and analyzes results. Before 9/11 Narus built carrier-grade tools to analyze IP network traffic for billing purposes, to prevent what Narus called "revenue leakage". Post-9/11 Narus added more "semantic monitoring abilities" for surveillance. Mobile Narus provided Telecom Egypt wit ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Carnivore (FBI)
Carnivore, later renamed DCS1000, was a system implemented by the Federal Bureau of Investigation (FBI) that was designed to monitor email and electronic communications. It used a customizable packet sniffer that could monitor all of a target user's Internet traffic. Carnivore was implemented in October 1997. By 2005 it had been replaced with improved commercial software. Development Carnivore grew out of an earlier FBI project called "Omnivore", which itself replaced an older undisclosed (at the time) surveillance tool migrated from the US Navy by FBI Director of Integrity and Compliance, Patrick W. Kelley. In September 1998, the FBI's Data Intercept Technology Unit (DITU) in Quantico, Virginia, launched a project to migrate Omnivore from Sun's Solaris operating system to a Windows NT platform. This was done to facilitate the miniaturization of the system and support a wider range of personal computer (PC) equipment. The migration project was called "Triple Phoenix" and the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
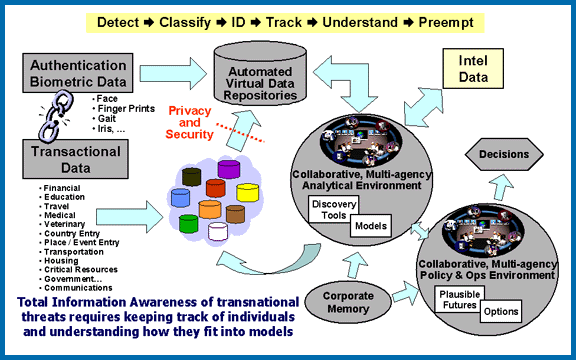
Information Awareness Office
The Information Awareness Office (IAO) was established by the United States Defense Advanced Research Projects Agency (DARPA) in January 2002 to bring together several DARPA projects focused on applying surveillance and information technology to track and monitor terrorists and other asymmetric threats to U.S. national security by achieving "Total Information Awareness" (TIA). It was achieved by creating enormous computer databases to gather and store the personal information of everyone in the United States, including personal e-mails, social networks, credit card records, phone calls, medical records, and numerous other sources, without any requirement for a search warrant. The information was then analyzed for suspicious activities, connections between individuals, and "threats".Total Information Awareness (TIA) ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Communications Assistance For Law Enforcement Act
The Communications Assistance for Law Enforcement Act (CALEA), also known as the "Digital Telephony Act," is a United States wiretapping law passed in 1994, during the presidency of Bill Clinton (Pub. L. No. 103-414, 108 Stat. 4279, codified at 47 USC 1001-1010). CALEA's purpose is to enhance the ability of law enforcement agencies to conduct lawful interception of communication by requiring that telecommunications carriers and manufacturers of telecommunications equipment modify and design their equipment, facilities, and services to ensure that they have built-in capabilities for targeted surveillance, allowing federal agencies to selectively wiretap any telephone traffic; it has since been extended to cover broadband Internet and VoIP traffic. Some government agencies argue that it covers mass surveillance of communications rather than just tapping specific lines and that not all CALEA-based access requires a warrant. The original reason for adopting CALEA was the Federal Burea ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Internet
The Internet (or internet) is the global system of interconnected computer networks that uses the Internet protocol suite (TCP/IP) to communicate between networks and devices. It is a '' network of networks'' that consists of private, public, academic, business, and government networks of local to global scope, linked by a broad array of electronic, wireless, and optical networking technologies. The Internet carries a vast range of information resources and services, such as the inter-linked hypertext documents and applications of the World Wide Web (WWW), electronic mail, telephony, and file sharing. The origins of the Internet date back to the development of packet switching and research commissioned by the United States Department of Defense in the 1960s to enable time-sharing of computers. The primary precursor network, the ARPANET, initially served as a backbone for interconnection of regional academic and military networks in the 1970s to enable resource shari ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Traffic Analysis
Traffic analysis is the process of intercepting and examining messages in order to deduce information from patterns in communication, it can be performed even when the messages are encrypted. In general, the greater the number of messages observed, the greater information be inferred. Traffic analysis can be performed in the context of military intelligence, counter-intelligence, or pattern-of-life analysis, and is also a concern in computer security. Traffic analysis tasks may be supported by dedicated computer software programs. Advanced traffic analysis techniques which may include various forms of social network analysis. Traffic analysis has historically been a vital technique in cryptanalysis, especially when the attempted crack depends on successfully seeding a known-plaintext attack, which often requires an inspired guess based on how specific the operational context might likely influence what an adversary communicates, which may be sufficient to establish a short cr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |

_(349115665).jpg)