|
Spring Framework
The Spring Framework is an application framework and inversion of control container for the Java platform. The framework's core features can be used by any Java application, but there are extensions for building web applications on top of the Java EE (Enterprise Edition) platform. Although the framework does not impose any specific programming model, it has become popular in the Java community as an addition to the Enterprise JavaBeans (EJB) model. The Spring Framework is open source. Version history The first version was written by Rod Johnson, who released the framework with the publication of his book ''Expert One-on-One J2EE Design and Development'' in October 2002. The framework was first released under the Apache 2.0 license in June 2003. The first production release, 1.0, was released in March 2004. The Spring 1.2.6 framework won a Jolt productivity award and a JAX Innovation Award in 2006. Spring 2.0 was released in October 2006, Spring 2.5 in November 2007, Spri ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
VMware
VMware, Inc. is an American cloud computing and virtualization technology company with headquarters in Palo Alto, California. VMware was the first commercially successful company to virtualize the x86 architecture. VMware's desktop software runs on Microsoft Windows, Linux, and macOS. VMware ESXi, its enterprise software hypervisor, is an operating system that runs on server hardware. In May 2022, Broadcom Inc. announced an agreement to acquire VMware in a cash-and-stock transaction valued at $61 billion. History Early history In 1998, VMware was founded by Diane Greene, Mendel Rosenblum, Scott Devine, Ellen Wang and Edouard Bugnion. Greene and Rosenblum were both graduate students at the University of California, Berkeley. Edouard Bugnion remained the chief architect and CTO of VMware until 2005, and went on to found Nuova Systems (now part of Cisco). For the first year, VMware operated in stealth mode, with roughly 20 employees by the end of 1998. The company wa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Aspect-oriented Programming
In computing, aspect-oriented programming (AOP) is a programming paradigm that aims to increase modularity by allowing the separation of cross-cutting concerns. It does so by adding behavior to existing code (an advice) ''without'' modifying the code itself, instead separately specifying which code is modified via a " pointcut" specification, such as "log all function calls when the function's name begins with 'set. This allows behaviors that are not central to the business logic (such as logging) to be added to a program without cluttering the code core to the functionality. AOP includes programming methods and tools that support the modularization of concerns at the level of the source code, while aspect-oriented software development refers to a whole engineering discipline. Aspect-oriented programming entails breaking down program logic into distinct parts (so-called ''concerns'', cohesive areas of functionality). Nearly all programming paradigms support some level of group ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Inversion Of Control
In software engineering, inversion of control (IoC) is a design pattern in which custom-written portions of a computer program receive the flow of control from a generic framework. A software architecture with this design inverts control as compared to traditional procedural programming: in traditional programming, the custom code that expresses the purpose of the program calls into reusable libraries to take care of generic tasks, but with inversion of control, it is the framework that calls into the custom, or task-specific, code. Inversion of control is used to increase modularity of the program and make it extensible, and has applications in object-oriented programming and other programming paradigms. The term was used by Michael Mattsson in a thesis, taken from there by Stefano Mazzocchi and popularized by him in 1999 in a defunct Apache Software Foundation project, Avalon, then further popularized in 2004 by Robert C. Martin and Martin Fowler. The term is related to, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
NoSQL
A NoSQL (originally referring to "non- SQL" or "non-relational") database provides a mechanism for storage and retrieval of data that is modeled in means other than the tabular relations used in relational databases. Such databases have existed since the late 1960s, but the name "NoSQL" was only coined in the early 21st century, triggered by the needs of Web 2.0 companies. NoSQL databases are increasingly used in big data and real-time web applications. NoSQL systems are also sometimes called Not only SQL to emphasize that they may support SQL-like query languages or sit alongside SQL databases in polyglot-persistent architectures. Motivations for this approach include simplicity of design, simpler "horizontal" scaling to clusters of machines (which is a problem for relational databases), finer control over availability and limiting the object-relational impedance mismatch. The data structures used by NoSQL databases (e.g. key–value pair, wide column, graph, or docum ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Java Database Connectivity
Java Database Connectivity (JDBC) is an application programming interface (API) for the programming language Java, which defines how a client may access a database. It is a Java-based data access technology used for Java database connectivity. It is part of the Java Standard Edition platform, from Oracle Corporation. It provides methods to query and update data in a database, and is oriented toward relational databases. A JDBC-to- ODBC bridge enables connections to any ODBC-accessible data source in the Java virtual machine (JVM) host environment. History and implementation Sun Microsystems released JDBC as part of Java Development Kit (JDK) 1.1 on February 19, 1997. Since then it has been part of the Java Platform, Standard Edition (Java SE). The JDBC classes are contained in the Java package and . Starting with version 3.1, JDBC has been developed under the Java Community Process. JSR 54 specifies JDBC 3.0 (included in J2SE 1.4), JSR 114 specifies the JDBC Rowset addi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
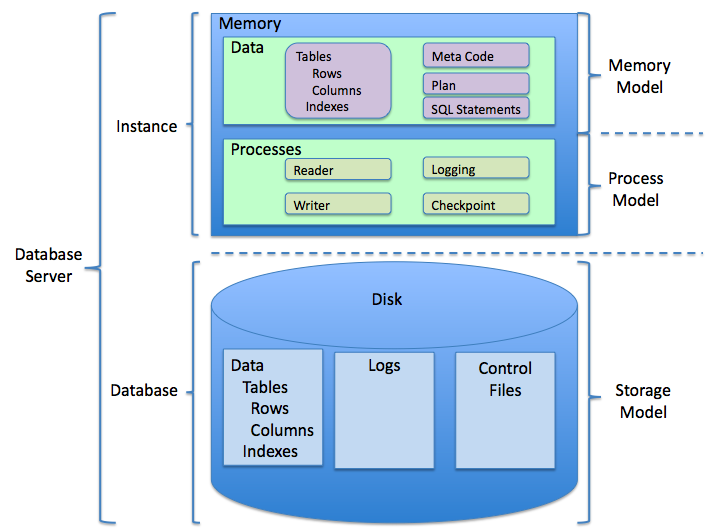
RDBMS
A relational database is a (most commonly digital) database based on the relational model of data, as proposed by E. F. Codd in 1970. A system used to maintain relational databases is a relational database management system (RDBMS). Many relational database systems are equipped with the option of using the SQL (Structured Query Language) for querying and maintaining the database. History The term "relational database" was first defined by E. F. Codd at IBM in 1970. Codd introduced the term in his research paper "A Relational Model of Data for Large Shared Data Banks". In this paper and later papers, he defined what he meant by "relational". One well-known definition of what constitutes a relational database system is composed of Codd's 12 rules. However, no commercial implementations of the relational model conform to all of Codd's rules, so the term has gradually come to describe a broader class of database systems, which at a minimum: # Present the data to the user as rel ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data Access
Data access is a generic term referring to a process which has both an IT-specific meaning and other connotations involving access rights in a broader legal and/or political sense. In the former it typically refers to software and activities related to storing, retrieving, or acting on data housed in a database or other repository. Details Two fundamental types of data access exist: # sequential access (as in magnetic tape, for example) # random access (as in indexed media) Data access crucially involves authorization to access different data repositories. Data access can help distinguish the abilities of administrators and users. For example, administrators may have the ability to remove, edit and add data, while general users may not even have "read" rights if they lack access to particular information. Historically, each repository (including each different database, file system, etc.), might require the use of different methods and languages, and many of these repositories ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Spring Roo
Spring Roo is an open-source software tool that uses convention-over-configuration principles to provide rapid application development of Java-based enterprise software. The resulting applications use common Java technologies such as Spring Framework, Java Persistence API, Thymeleaf, Apache Maven and AspectJ. Spring Roo is a member of the Spring portfolio of projects. Motivation and history Spring Roo's mission statement is to ''"fundamentally improve Java developer productivity without compromising engineering integrity or flexibility"''. The technology was first demonstrated during the opening keynote at the SpringOne Europe developer conference on 27 April 2009, with an initial alpha release concurrently being published. During the keynote an application was built live on-stage that would be used by conference attendees to vote on the preferred name for the project (which at that time was codenamed "Roo" within SpringSource). Ultimately the name "Spring Roo" was preferred ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Convention Over Configuration
Convention over configuration (also known as coding by convention) is a software design paradigm used by software frameworks that attempts to decrease the number of decisions that a developer using the framework is required to make without necessarily losing flexibility and don't repeat yourself (DRY) principles. The concept was introduced by David Heinemeier Hansson to describe the philosophy of the Ruby on Rails web framework, but is related to earlier ideas like the concept of "sensible defaults" and the principle of least astonishment in user interface design. The phrase essentially means a developer only needs to specify unconventional aspects of the application. For example, if there is a class Sales in the model, the corresponding table in the database is called "sales" by default. It is only if one deviates from this convention, such as the table "product sales", that one needs to write code regarding these names. When the convention implemented by the tool matches th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Spring Security
Spring Security is a Java/Java EE framework that provides authentication, authorization and other security features for enterprise applications. The project was started in late 2003 as 'Acegi Security' (pronounced ''Ah-see-gee'' , whose letters are the first, third, fifth, seventh, and ninth characters from the English alphabet, in order to prevent name conflicts) by Ben Alex, with it being publicly released under the Apache License in March 2004. Subsequently, Acegi was incorporated into the Spring portfolio as Spring Security, an official Spring sub-project. The first public release under the new name was Spring Security 2.0.0 in April 2008, with commercial support and training available from SpringSource. Authentication flow Diagram 1 shows the basic flow of an authentication request using the Spring Security system. It shows the different filters and how they interact from the initial browser request, to either a successful authentication or an HTTP 403 error. Key authen ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |