|
Secureworks
Secureworks Inc. is an American cybersecurity company. The company has approximately 4,000 customers in more than 50 countries, ranging from Fortune 100 companies to mid-sized businesses in a variety of industries. It became part of Dell, Dell Technologies in February 2011 and was later the subject of an initial public offering to again become a publicly traded company in April 2016. It was majority-owned by Dell until 2025 when Secureworks was acquired by Sophos. History Secureworks was founded as a privately held company in 1998 by Michael Pearson and Joan Wilbanks. In 2002, Michael R. Cote became president and CEO. In 2005, and again in 2006, the company was named to the Inc. (magazine)#Inc. 500 and Inc. 5000, Inc. 500 and Inc. 5000 lists 2006 and Deloitte’s Fast 500. In 2006, Secureworks merged with LURHQ Corporation and the new entity continued under the Secureworks corporate name. LURHQ was founded in 1996 in Myrtle Beach, SC and provided managed security services to la ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Sophos
Sophos Limited is a British security software and hardware company. It develops and markets managed security services and cybersecurity software and hardware, such as managed detection and response, incident response and endpoint security software. Sophos was listed on the London Stock Exchange until it was acquired by Thoma Bravo, an American private equity firm in March 2020. History Sophos was founded by Jan Hruska and Peter Lammer and began producing its first antivirus and encryption products in 1985. During the late 1980s and into the 1990s, Sophos primarily developed and sold a range of security technologies in the UK, including encryption tools available for most users (private or business). In the late 1990s, Sophos concentrated its efforts on developing and selling antivirus technology and embarked on a program of international expansion. In 2010, the majority interest of Sophos was sold to Apax Partners. In 2011, Utimaco Safeware AG (acquired by Sophos in 20 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Managed Security Service
In computing, managed security services (MSS) are network security services that have been outsourced to a service provider. A company providing such a service is a managed security service provider (MSSP) The roots of MSSPs are in the Internet Service Providers (ISPs) in the mid to late 1990s. Initially, ISP(s) would sell customers a firewall appliance, as customer premises equipment (CPE), and for an additional fee would manage the customer-owned firewall over a dial-up connection. According to recent industry research, most organizations (74%) manage IT security in-house, but 82% of IT professionals said they have either already partnered with, or plan to partner with, a managed security service provider. Businesses turn to managed security services providers to alleviate the pressures they face daily related to information security such as targeted malware, customer data theft, skills shortages and resource constraints. Managed security services (MSS) are also consi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
VeriSign
Verisign, Inc. is an American company based in Reston, Virginia, that operates a diverse array of network infrastructure, including two of the Internet's thirteen root nameservers, the authoritative registry for the , , and generic top-level domains and the country-code top-level domains, and the back-end systems for the and sponsored top-level domains. In 2010, Verisign sold its authentication business unit – which included Secure Sockets Layer (SSL) certificate, public key infrastructure (PKI), Verisign Trust Seal, and Verisign Identity Protection (VIP) services – to NortonLifeLock, Symantec for $1.28 billion. The deal capped a multi-year effort by Verisign to narrow its focus to its core infrastructure and security business units. Symantec later sold this unit to DigiCert in 2017. On October 25, 2018, Neustar, NeuStar, Inc. acquired VeriSign's Security Service Customer Contracts. The acquisition effectively transferred Verisign Inc.'s Denial-of-service attack, Distrib ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Telemetry
Telemetry is the in situ collection of measurements or other data at remote points and their automatic transmission to receiving equipment (telecommunication) for monitoring. The word is derived from the Greek roots ''tele'', 'far off', and ''metron'', 'measure'. Systems that need external instructions and data to operate require the counterpart of telemetry: telecommand. Although the term commonly refers to wireless data transfer mechanisms (e.g., using radio, ultrasonic, or infrared systems), it also encompasses data transferred over other media such as a telephone or computer network, optical link or other wired communications like power line carriers. Many modern telemetry systems take advantage of the low cost and ubiquity of GSM networks by using SMS to receive and transmit telemetry data. A ''telemeter'' is a physical device used in telemetry. It consists of a sensor, a transmission path, and a display, recording, or control device. Electronic devices are widely u ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cyber Kill Chain
The cyber kill chain is the process by which perpetrators carry out cyberattacks. Lockheed Martin adapted the concept of the '' kill chain'' from a military setting to information security, using it as a method for modeling intrusions on a computer network. The cyber kill chain model has seen some adoption in the information security community. However, acceptance is not universal, with critics pointing to what they believe are fundamental flaws in the model. Attack phases and countermeasures Computer scientists at Lockheed-Martin corporation described a new "intrusion kill chain" framework or model to defend computer networks in 2011. They wrote that attacks may occur in phases and can be disrupted through controls established at each phase. Since then, the "cyber kill chain" has been adopted by data security organizations to define phases of cyberattacks. A cyber kill chain reveals the phases of a cyberattack: from early reconnaissance to the goal of data exfiltration. The k ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Private Sector
The private sector is the part of the economy which is owned by private groups, usually as a means of establishment for profit or non profit, rather than being owned by the government. Employment The private sector employs most of the workforce in some countries. In private sector, activities are guided by the motive to earn money, i.e. operate by capitalist standards. A 2013 study by the International Finance Corporation (part of the World Bank Group) identified that 90 percent of jobs in developing countries are in the private sector. Diversification In free enterprise countries, such as the United States, the private sector is wider, and the state places fewer constraints on firms. In countries with more government authority, such as China, the public sector makes up most of the economy. Regulation States legally regulate the private sector. Businesses operating within a country must comply with the laws in that country. In some cases, usually involving multinati ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Knowledge Base
In computer science, a knowledge base (KB) is a set of sentences, each sentence given in a knowledge representation language, with interfaces to tell new sentences and to ask questions about what is known, where either of these interfaces might use inference. It is a technology used to store complex structured data used by a computer system. The initial use of the term was in connection with expert systems, which were the first knowledge-based systems. Original usage of the term The original use of the term knowledge base was to describe one of the two sub-systems of an expert system. A knowledge-based system consists of a knowledge-base representing facts about the world and ways of reasoning about those facts to deduce new facts or highlight inconsistencies. Properties The term "knowledge-base" was coined to distinguish this form of knowledge store from the more common and widely used term ''database''. During the 1970s, virtually all large management information sy ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
ATT&CK
The Adversarial Tactics, Techniques, and Common Knowledge or MITRE ATT&CK is a guideline for classifying and describing cyberattacks and intrusions. It was created by the Mitre Corporation and released in 2013. Rather than looking at the results of an attack (aka an indicator of compromise (IoC)), it identifies tactics that indicate an attack is in progress. Tactics are the “why” of an attack technique. The framework consists of 14 tactics categories consisting of "technical objectives" of an adversary. Examples include privilege escalation and command and control. These categories are then broken down further into specific techniques and sub-techniques. The framework is an alternative to the cyber kill chain developed by Lockheed Martin. ATT&CK Matrix for Enterprise The ATT&CK Matrix for Enterprise is a comprehensive framework that is presented as a kanban board-style diagram. It defines 14 categories of tactics, techniques and procedures (TTPs) used by cybercriminals wit ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
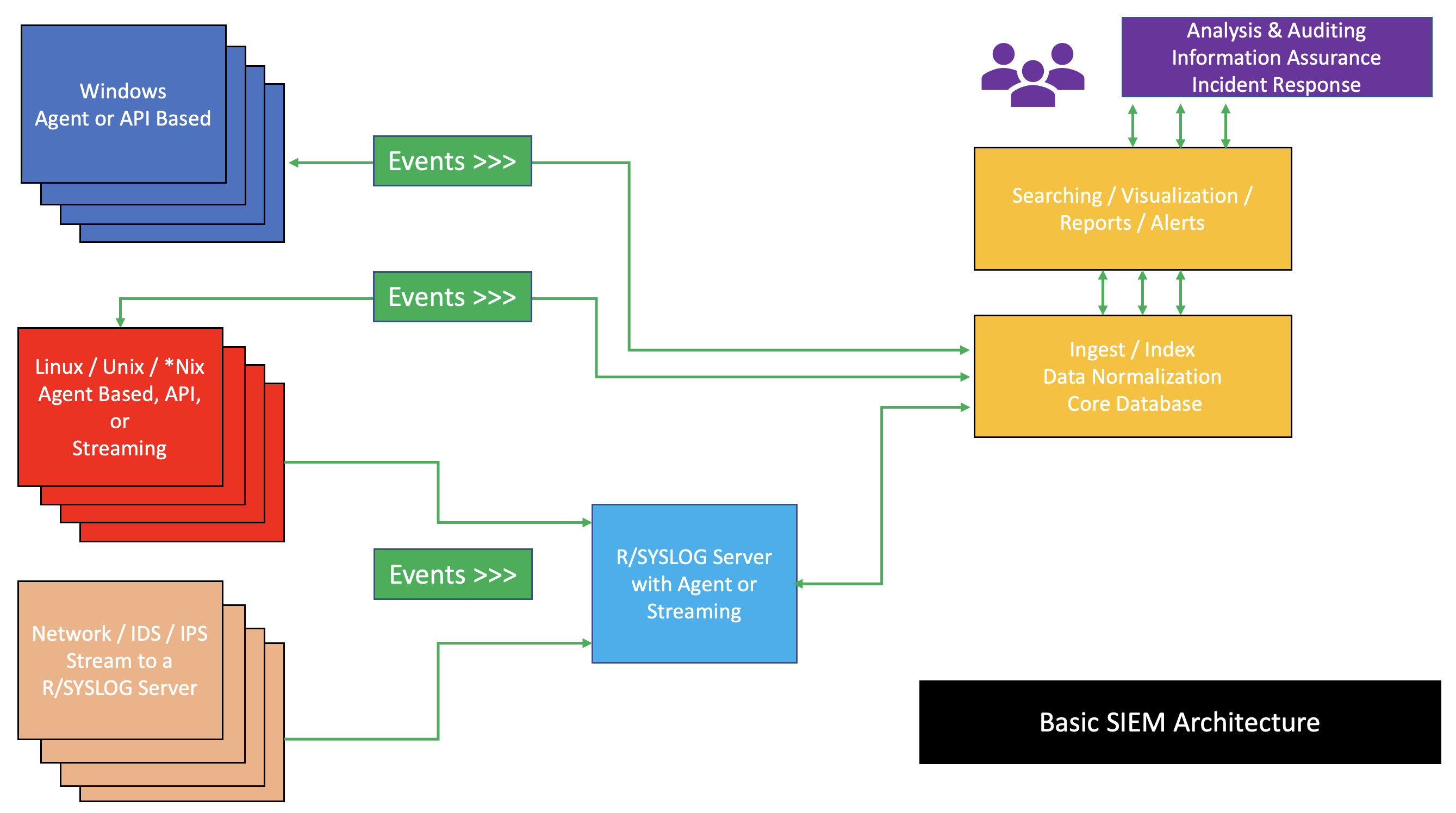
Security Information And Event Management
Security information and event management (SIEM) is a field within computer security that combines security information management (SIM) and security event management (SEM) to enable real-time analysis of security alerts generated by applications and network hardware. SIEM systems are central to Security operations center, security operations centers (SOCs), where they are employed to detect, investigate, and respond to security incidents. SIEM technology collects and aggregates data from various systems, allowing organizations to meet compliance requirements while safeguarding against Cyberattack, threats. National Institute of Standards and Technology (NIST) definition for SIEM tool is application that provides the ability to gather security data from information system components and present that data as actionable information via a single interface. SIEM tools can be implemented as software, hardware, or managed services. SIEM systems log security events and generating reports to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
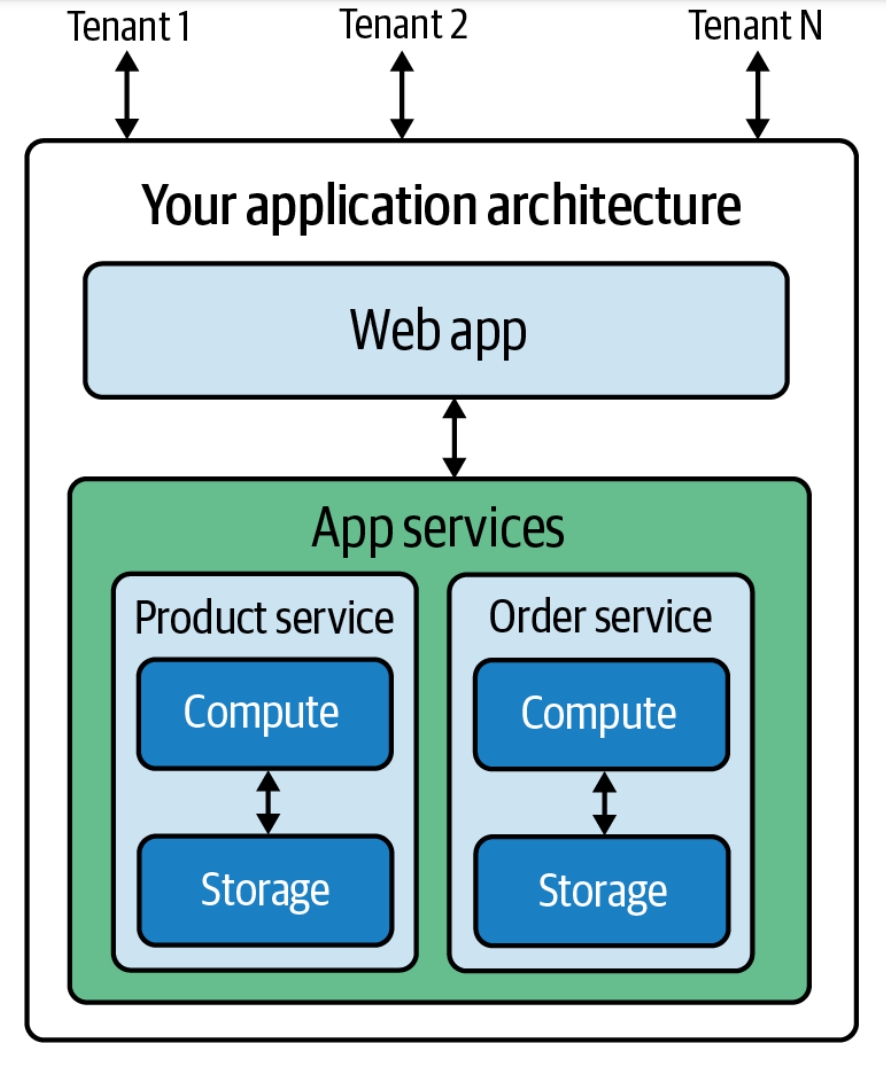
SaaS
Software as a service (SaaS ) is a cloud computing service model where the provider offers use of application software to a client and manages all needed physical and software resources. SaaS is usually accessed via a web application. Unlike other software delivery models, it separates "the possession and ownership of software from its use". SaaS use began around 2000, and by 2023 was the main form of software application deployment. Unlike most self-hosted software products, only one version of the software exists and only one operating system and configuration is supported. SaaS products typically run on rented infrastructure as a service (IaaS) or platform as a service (PaaS) systems including hardware and sometimes operating systems and middleware, to accommodate rapid increases in usage while providing instant and continuous availability to customers. SaaS customers have the abstraction of limitless computing resources, while economy of scale drives down the cost. SaaS ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cloud-based
Cloud computing is "a paradigm for enabling network access to a scalable and elastic pool of shareable physical or virtual resources with self-service provisioning and administration on-demand," according to International Organization for Standardization, ISO. Essential characteristics In 2011, the National Institute of Standards and Technology (NIST) identified five "essential characteristics" for cloud systems. Below are the exact definitions according to NIST: * On-demand self-service: "A consumer can unilaterally provision computing capabilities, such as server time and network storage, as needed automatically without requiring human interaction with each service provider." * Broad network access: "Capabilities are available over the network and accessed through standard mechanisms that promote use by heterogeneous thin or thick client platforms (e.g., mobile phones, tablets, laptops, and workstations)." * Pooling (resource management), Resource pooling: " The provider' ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Penetration Testing
A penetration test, colloquially known as a pentest, is an authorized simulated cyberattack on a computer system, performed to evaluate the security of the system; this is not to be confused with a vulnerability assessment. The test is performed to identify weaknesses (or vulnerabilities), including the potential for unauthorized parties to gain access to the system's features and data, as well as strengths, enabling a full risk assessment to be completed. The process typically identifies the target systems and a particular goal, then reviews available information and undertakes various means to attain that goal. A penetration test target may be a white box (about which background and system information are provided in advance to the tester) or a black box (about which only basic information other than the company name is provided). A gray box penetration test is a combination of the two (where limited knowledge of the target is shared with the auditor). A penetration test can ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |