|
Ricochet Chollima
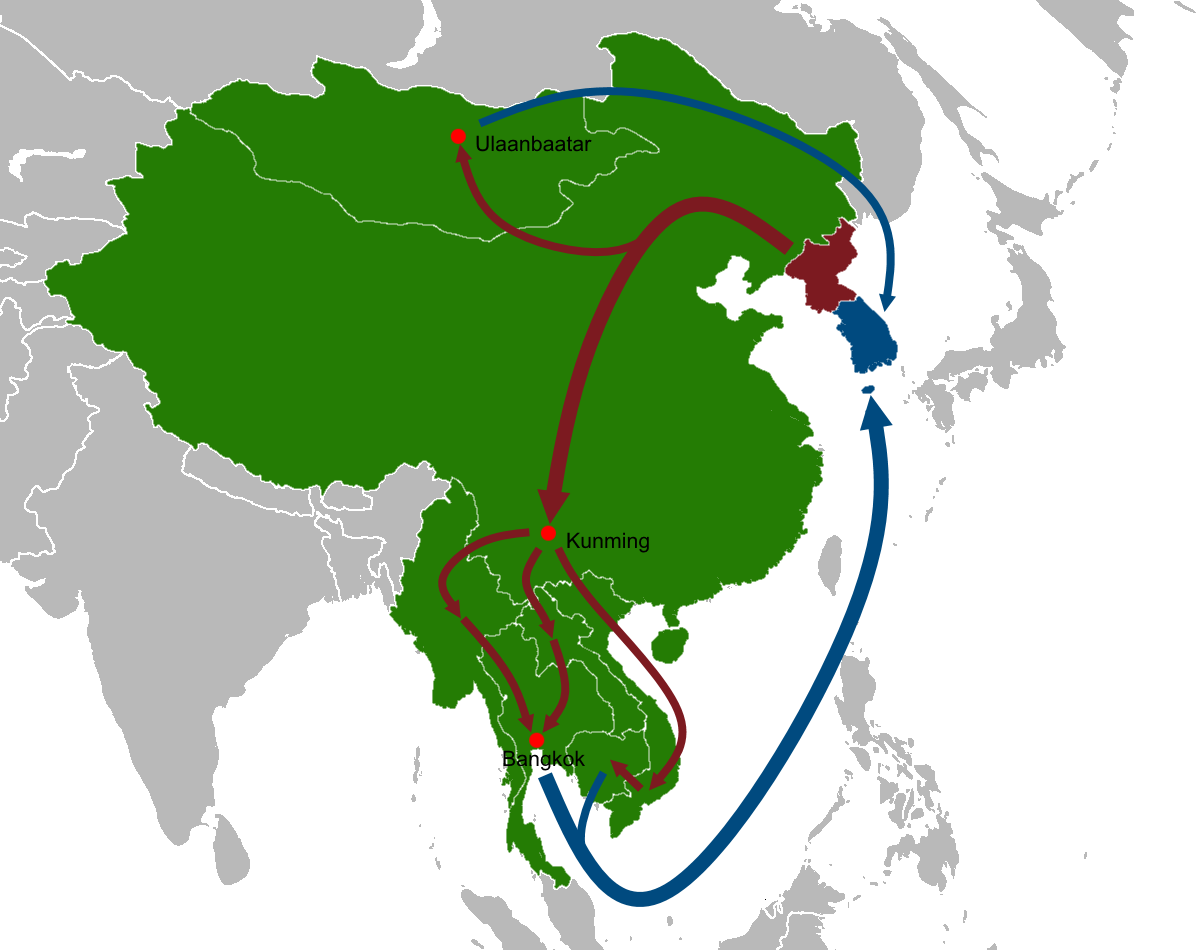
Ricochet Chollima (also known as APT 37, Reaper, and ScarCruft) is a North Korean state backed hacker group that is believed to have created sometime before 2016 and is typically involved in operations against financial institutions to generate assets for North Korea. But also conducts attacks on the industrial sector in other countries. CrowdStrike has stated that the group mainly attacks a variety of South Korean organizations and individuals, including academics, journalists, and North Korean defectors. But also stated the group has also engaged in attacks against Japan, Vietnam, Hong Kong, the Middle East, Russia, and the United States. FireEye has called the group "the overlooked North Korean threat actor." History The group is believed to have been founded sometime around 2012, according to FireEye. In January 2021 the group was found to be using a Trojan horse for a spear-phishing campaign that targeted the South Korean government. See also *Lazarus Group *Kimsuky Kimsu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
CrowdStrike
CrowdStrike Holdings, Inc. is an American cybersecurity technology company based in Austin, Texas. It provides cloud workload and endpoint security, threat intelligence, and cyberattack response services. The company has been involved in investigations of several high-profile cyberattacks, including the 2014 Sony Pictures hack, the 2015–16 cyber attacks on the Democratic National Committee (DNC), and the 2016 email leak involving the DNC. History CrowdStrike was co-founded by George Kurtz (CEO), Dmitri Alperovitch (former CTO), and Gregg Marston (CFO, retired) in 2011. In 2012, Shawn Henry, a former Federal Bureau of Investigation (FBI) official, was hired to lead the subsidiary CrowdStrike Services, Inc., which focused on proactive and incident response services. In June 2013, the company launched its first product, CrowdStrike Falcon, which provided endpoint protection, threat intelligence and attribution. In May 2014, CrowdStrike's reports assisted the United States ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
North Korean Defectors
Since the division of Korea after the end of World War II, North Koreans have fled from the country in spite of legal punishment for political, ideological, religious, economic, moral, personal, or nutritional reasons. Such North Koreans are referred to as North Korean defectors by the North Korean regime. Alternative terms in South Korea, where the defectors often end up, include "northern refugees" ( ko, 탈북자, ''talbukja'' or , ''talbukmin'') and "new settlers" (, ''saeteomin''). During the North Korean famine of the 1990s, there was an increase in defections, reaching a peak in 1998 and 1999. Some of the main reasons for the falling number of defectors, especially since 2000, are the strict border patrols and inspections, forced deportations, and the rising cost of defection. The most common strategy of North Korean defectors is to cross the Chinese border into Jilin and Liaoning provinces in northeast China. About 76% to 84% of defectors interviewed in China or S ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
FireEye
Trellix (formerly FireEye and McAfee Enterprise) is a privately held cybersecurity company founded in 2022. It has been involved in the detection and prevention of major cyber attacks. It provides hardware, software, and services to investigate cybersecurity attacks, protect against malicious software, and analyze IT security risks. In March 2021, Symphony Technology Group (STG) announced its acquisition of McAfee Enterprise in an all-cash transaction for $4.0 billion. STG completed the acquisition of McAfee’s Enterprise business in July 2021 with plans for re-branding. In June 2021, FireEye sold its name and products business to STG for $1.2 billion. STG combined FireEye with its acquisition of McAfee's enterprise business to launch Trellix, an extended detection and response (XDR) company. Meanwhile, McAfee Enterprise's security service edge (SSE) business would operate as a separate company to be known as Skyhigh Security. History FireEye was founded in 2004 by Ashar ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Trojan Horse (computing)
In computing, a Trojan horse is any malware that misleads users of its true intent. The term is derived from the Ancient Greek story of the deceptive Trojan Horse that led to the fall of the city of Troy. Trojans generally spread by some form of social engineering; for example, where a user is duped into executing an email attachment disguised to appear innocuous (e.g., a routine form to be filled in), or by clicking on some fake advertisement on social media or anywhere else. Although their payload can be anything, many modern forms act as a backdoor, contacting a controller who can then have unauthorized access to the affected computer. Ransomware attacks are often carried out using a Trojan. Unlike computer viruses and worms, Trojans generally do not attempt to inject themselves into other files or otherwise propagate themselves. Use of the term It's not clear where or when the concept, and this term for it, was first used, but by 1971 the first Unix manual assumed it ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Phishing
Phishing is a type of social engineering where an attacker sends a fraudulent (e.g., spoofed, fake, or otherwise deceptive) message designed to trick a person into revealing sensitive information to the attacker or to deploy malicious software on the victim's infrastructure like ransomware. Phishing attacks have become increasingly sophisticated and often transparently mirror the site being targeted, allowing the attacker to observe everything while the victim is navigating the site, and transverse any additional security boundaries with the victim. As of 2020, phishing is by far the most common attack performed by cybercriminals, the FBI's Internet Crime Complaint Centre recording over twice as many incidents of phishing than any other type of computer crime. The first recorded use of the term "phishing" was in the cracking toolkit AOHell created by Koceilah Rekouche in 1995; however, it is possible that the term was used before this in a print edition of the hacker maga ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Lazarus Group
Lazarus Group (also known by other monikers such as Guardians of Peace or Whois Team ) is a cybercrime group made up of an unknown number of individuals run by the government of North Korea. While not much is known about the Lazarus Group, researchers have attributed many cyberattacks to them between 2010 and 2021. Originally a criminal group, the group has now been designated as an advanced persistent threat due to intended nature, threat, and wide array of methods used when conducting an operation. Names given by cybersecurity organizations include Hidden Cobra (used by the United States Department of Homeland Security to refer to malicious cyber activity by the North Korean government in general) and Zinc (by Microsoft). The Lazarus Group has strong links to North Korea. The United States Federal Bureau of Investigation says that the Lazarus Group is a North Korean "state-sponsored hacking organization". According to North Korean defector Kim Kuk-song, the unit is internally k ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Kimsuky
Kimsuky (also known as Velvet Chollima and Black Banshee) is a North Korean state backed hacker group that targets South Korean think tanks, industry, nuclear power operators, and the South Korean Ministry of Unification for espionage purposes. In recent years Kimsuky has expanded their operations to include states such as Russia, the United States, and European nations. History According to the U.S. Cybersecurity and Infrastructure Security Agency Kimsuky has likely been active since 2012. In March 2015 it was reported that South Korea claimed Kimsuky stole data from Korea Hydro & Nuclear Power. In August 2019 it was reported that Kimsuky was targeting retired South Korean diplomats, government, and military officials, in an attack called "the first of its kind." In September 2020 it was reported that Kimsuky attempted to hack 11 officials of the United Nations Security Council. A lawmaker from the People Power Party reported that, in May 2021, Kimsuky was detected within t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
North Korean Advanced Persistent Threat Groups
North is one of the four compass points or cardinal directions. It is the opposite of south and is perpendicular to east and west. ''North'' is a noun, adjective, or adverb indicating direction or geography. Etymology The word ''north'' is related to the Old High German ''nord'', both descending from the Proto-Indo-European unit *''ner-'', meaning "left; below" as north is to left when facing the rising sun. Similarly, the other cardinal directions are also related to the sun's position. The Latin word ''borealis'' comes from the Greek '' boreas'' "north wind, north", which, according to Ovid, was personified as the wind-god Boreas, the father of Calais and Zetes. ''Septentrionalis'' is from ''septentriones'', "the seven plow oxen", a name of ''Ursa Major''. The Greek ἀρκτικός (''arktikós'') is named for the same constellation, and is the source of the English word ''Arctic''. Other languages have other derivations. For example, in Lezgian, ''kefer'' can mean bot ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hacking In The 2010s
Hacking may refer to: Places * Hacking, an area within Hietzing, Vienna, Austria People * Douglas Hewitt Hacking, 1st Baron Hacking (1884–1950), British Conservative politician * Ian Hacking (born 1936), Canadian philosopher of science * David Hacking, 3rd Baron Hacking (born 1938), British barrister and peer Sports * Hacking (falconry), the practice of raising falcons in captivity then later releasing into the wild * Hacking (rugby), tripping an opposing player * Pleasure riding, horseback riding for purely recreational purposes, also called hacking * Shin-kicking, an English martial art also called hacking Technology * Hacker, a computer expert with advanced technical knowledge ** Hacker culture, activity within the computer programmer subculture * Security hacker, someone who breaches defenses in a computer system ** Cybercrime, which involves security hacking * Phone hacking, gaining unauthorized access to phones * ROM hacking, the process of modifying a video game's ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hacker Groups
Hacker groups are informal communities that began to flourish in the early 1980s, with the advent of the home computer. Overview Prior to that time, the term ''hacker'' was simply a referral to any computer hobbyist. The hacker groups were out to make names for themselves, and were often spurred on by their own press. This was a heyday of hacking, at a time before there was much law against computer crime. Hacker groups provided access to information and resources, and a place to learn from other members. Hackers could also gain credibility by being affiliated with an elite group. The names of hacker groups often parody large corporations, governments, police and criminals; and often used specialized orthography An orthography is a set of conventions for writing a language, including norms of spelling, hyphenation, capitalization, word breaks, emphasis, and punctuation. Most transnational languages in the modern period have a writing system, and mo .... See also * List ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |