|
OSSIM
OSSIM (Open Source Security Information Management) is an open source security information and event management system, integrating a selection of tools designed to aid network administrators in computer security, intrusion detection and prevention. The project began in 2003 as a collaboration between Dominique Karg, Julio Casal and later Alberto Román. In 2008 it became the basis for their company AlienVault. Following the acquisition of the Eureka project label and completion of R&D, AlienVault began selling a commercial derivative of OSSIM ('AlienVault Unified Security Management'). AlienVault was acquired by AT&T Communications and renamed AT&T Cybersecurity in 2019. OSSIM has had four major-version releases since its creation and is on a 5.x.x version numbering. An information visualization of the contributions to the source code for OSSIM was published a8 years of OSSIM The project has approximately 7.4 million lines of code. The current version of OSSIM is 5.7.5 and w ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
AT&T Cybersecurity
AT&T Cybersecurity is a developer of commercial and open-source services to manage cyber attacks, including the Open Threat Exchange, a crowd-sourced computer-security platform. In April 2015, the company claimed it had 26,000 participants who contributed more than 1 million threat indicators daily. The company has raised $120 million since it was founded as AlienVault in 2007. On July 10, 2018, it was acquired by AT&T Communications, becoming a wholly-owned subsidiary when the transaction was completed on August 22, 2018. In February 2019, AlienVault was renamed AT&T Cybersecurity. History The OSSIM project began in 2003 by Dominique Karg, Julio Casal, Ignacio Cabrera, and Alberto Román. It became the basis of AlienVault, founded in 2007 in Madrid, Spain. The company hired the management team of Hewlett-Packard's Fortify group in 2012, including AlienVault CEO Barmak Meftah, CTO Roger Thornton, and five others. In 2015, the company partnered with Intel to coordinate r ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Eureka (organisation)
Eureka (often abbreviated as E!, or Σ!) is an intergovernmental organisation for research and development funding and coordination. Eureka is an open platform for international cooperation in innovation. Organisations and companies applying through Eureka programmes can access funding and support from national and regional ministries or agencies for their international R&D projects. , Eureka has 43 full members, including the European Union (represented by the European Commission) and four associated members (Argentina, Chile, South Africa, and Singapore). All 27 EU Member States are also members of Eureka. Eureka is not an EU research programme, but rather an intergovernmental organisation of national ministries or agencies, of which the EU is a member. Cooperation and synergy are sought between Eureka and the research activities of the EU proper, such as with European Union's Horizon 2020 and the European Research Area. History Founded in 1985 by prominent European poli ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Operating System
An operating system (OS) is system software that manages computer hardware, software resources, and provides common services for computer programs. Time-sharing operating systems schedule tasks for efficient use of the system and may also include accounting software for cost allocation of processor time, mass storage, printing, and other resources. For hardware functions such as input and output and memory allocation, the operating system acts as an intermediary between programs and the computer hardware, although the application code is usually executed directly by the hardware and frequently makes system calls to an OS function or is interrupted by it. Operating systems are found on many devices that contain a computer from cellular phones and video game consoles to web servers and supercomputers. The dominant general-purpose personal computer operating system is Microsoft Windows with a market share of around 74.99%. macOS by Apple Inc. is in second place (14.84%), ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
MAC Address
A media access control address (MAC address) is a unique identifier assigned to a network interface controller (NIC) for use as a network address in communications within a network segment. This use is common in most IEEE 802 networking technologies, including Ethernet, Wi-Fi, and Bluetooth. Within the Open Systems Interconnection (OSI) network model, MAC addresses are used in the medium access control protocol sublayer of the data link layer. As typically represented, MAC addresses are recognizable as six groups of two hexadecimal digits, separated by hyphens, colons, or without a separator. MAC addresses are primarily assigned by device manufacturers, and are therefore often referred to as the burned-in address, or as an Ethernet hardware address, hardware address, or physical address. Each address can be stored in hardware, such as the card's read-only memory, or by a firmware mechanism. Many network interfaces, however, support changing their MAC address. The address ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Arpwatch
arpwatch is a computer software tool for monitoring Address Resolution Protocol traffic on a computer network. It generates a log of observed pairing of IP addresses with MAC addresses along with a timestamp when the pairing appeared on the network. It also has the option of sending an email to an administrator when a pairing changes or is added. Network administrators monitor ARP activity to detect ARP spoofing, network flip-flops, changed and new stations and address reuse. arpwatch was developed by Lawrence Berkeley National Laboratory, Network Research Group, as open-source software and is released under the BSD license BSD licenses are a family of permissive free software licenses, imposing minimal restrictions on the use and distribution of covered software. This is in contrast to copyleft licenses, which have share-alike requirements. The original BSD lice .... See also * ArpON * arping * Ettercap References External links Source files Free network management ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
OpenVAS
OpenVAS (''Open Vulnerability Assessment System'', originally known as ''GNessUs'') is the scanner component of Greenbone Vulnerability Manager (GVM), a software framework of several services and tools offering vulnerability scanning and vulnerability management. All Greenbone Vulnerability Manager products are free software, and most components are licensed under the GNU General Public License (GPL). Plugins for Greenbone Vulnerability Manager are written in the Nessus Attack Scripting Language, NASL. History Greenbone Vulnerability Manager began under the name of OpenVAS, and before that the name GNessUs, as a fork of the previously open source Nessus scanning tool, after its developers Tenable Network Security changed it to a proprietary (closed source) license in October 2005. OpenVAS was originally proposed by pentesters at SecuritySpace, discussed with pentesters at Portcullis Computer Security and then announced by Tim Brown on Slashdot. Greenbone Vulnerability ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Nagios
Nagios Core , formerly known as Nagios, is a free and open-source computer-software application that monitors systems, networks and infrastructure. Nagios offers monitoring and alerting services for servers, switches, applications and services. It alerts users when things go wrong and alerts them a second time when the problem has been resolved. Ethan Galstad and a group of developers originally wrote Nagios as ''NetSaint''. they actively maintain both the official and unofficial plugins. Nagios is a recursive acronym: "Nagios Ain't Gonna Insist On Sainthood" – "sainthood" makes reference to the original name ''NetSaint'', which changed in response to a legal challenge by owners of a similar trademark. " Agios" (or "hagios") also transliterates the Greek word ''άγιος'', which means "saint". Nagios was originally designed to run under Linux, but it also runs on other Unix variants. It is free software licensed under the terms of the GNU General Public License versio ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
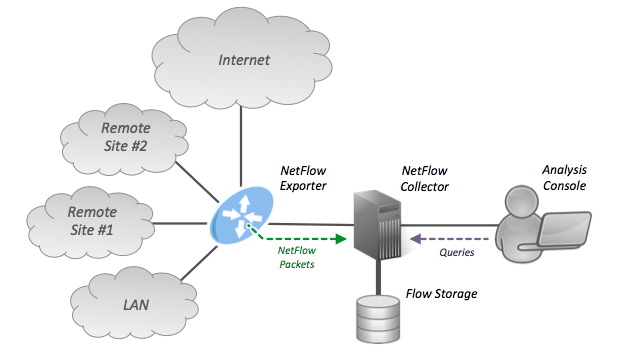
NetFlow
NetFlow is a feature that was introduced on Cisco routers around 1996 that provides the ability to collect IP network traffic as it enters or exits an interface. By analyzing the data provided by NetFlow, a network administrator can determine things such as the source and destination of traffic, class of service, and the causes of congestion. A typical flow monitoring setup (using NetFlow) consists of three main components: * Flow exporter: aggregates packets into flows and exports flow records towards one or more flow collectors. * Flow collector: responsible for reception, storage and pre-processing of flow data received from a flow exporter. * Analysis application: analyzes received flow data in the context of intrusion detection or traffic profiling, for example. Protocol description Routers and switches that support NetFlow can collect IP traffic statistics on all interfaces where NetFlow is enabled, and later export those statistics as NetFlow records toward at least on ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Munin (network Monitoring Application)
Munin is a free and open-source computer system monitoring, network monitoring and infrastructure monitoring software application. Munin is written in Perl and uses RRDtool to create graphs, which are accessible over a web interface. Its emphasis is on plug and play capabilities. About 500 monitoring plugins are currently available. It is intended to make it easy to determine "what's different today" when a performance problem happens and to provide visibility into capacity and utilization of resources. History Munin was started by Jimmy Olsen late 2003, based on RRDtool by Tobi Oetiker. Development has slowed since 2005, but Munin is a stable tool and is still maintained. “Its name is derived from Norse mythology. One of the two ravens who report the news of the world to the god Odin is called Munin, and the other is named Hugin. Munin is 'memory', and Hugin is 'thought'.” Architecture Plugins Plugins are the specialized programs that are called by Munin nodes to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Suricata (software)
Suricata is an open-source based intrusion detection system (IDS) and intrusion prevention system An intrusion detection system (IDS; also intrusion prevention system or IPS) is a device or software application that monitors a network or systems for malicious activity or policy violations. Any intrusion activity or violation is typically rep ... (IPS). It was developed by the Open Information Security Foundation (OISF). A beta version was released in December 2009, with the first standard release following in July 2010. Free intrusion detection systems * OSSEC HIDS * Prelude Hybrid IDS * Sagan * Snort * Zeek NIDS See also * Aanval References External links * Open Information Security Foundation* {{DEFAULTSORT:Suricata (Software) Computer security software Free security software Free network-related software Intrusion detection systems Linux security software Unix security-related software ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Intrusion Detection System
An intrusion detection system (IDS; also intrusion prevention system or IPS) is a device or software application that monitors a network or systems for malicious activity or policy violations. Any intrusion activity or violation is typically reported either to an administrator or collected centrally using a security information and event management (SIEM) system. A SIEM system combines outputs from multiple sources and uses alarm filtering techniques to distinguish malicious activity from false alarms. IDS types range in scope from single computers to large networks. The most common classifications are network intrusion detection systems (NIDS) and host-based intrusion detection systems (HIDS). A system that monitors important operating system files is an example of an HIDS, while a system that analyzes incoming network traffic is an example of an NIDS. It is also possible to classify IDS by detection approach. The most well-known variants are signature-based detection (recogni ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |