|
Open Threat Exchange
Open Threat Exchange (OTX) is a crowd-sourced computer-security platform. It has more than 180,000 participants in 140 countries who share more than 19 million potential threats daily. It is free to use. Founded in 2012, OTX was created and is run by AlienVault (now AT&T Cybersecurity), a developer of commercial and open source solutions to manage cyber attacks. The collaborative threat exchange was created partly as a counterweight to criminal hackers successfully working together and sharing information about viruses, malware and other cyber attacks. Components OTX is cloud-hosted. Information sharing covers a wide range of issues related to security, including viruses, malware, intrusion detection and firewalls. Its automated tools cleanse, aggregate, validate and publish data shared by participants. The data is validated by the OTX platform then stripped of information identifying the participating contributor. In 2015, OTX 2.0 added a social network which enables members t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
AT&T Cybersecurity
LevelBlue (formerly AT&T Cybersecurity) is a managed security service provider. Cybersecurity investor WillJam Ventures officially launched LevelBlue, a joint venture with AT&T, to form a new, standalone managed cybersecurity services business at RSA Conference 2024. LevelBlue offers managed security services, consulting, threat intelligence and research. Products LevelBlue is a managed security services business. Product and services include: Cybersecurity Consulting Services that provide assessment, planning and advisory through the LevelBlue Consulting team. LevelBlue Consulting services include security strategy and build cyber resilience through Zero Trust, risk mitigation, and compliance assurance. Managed Security Services for Network Security, Threat Detection and Response, and Endpoint Security offer a strategic extension to help organizations simplify cybersecurity to deliver greater insights. LevelBlue Managed Security Services drive efficiency in security operati ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Security
Computer security (also cybersecurity, digital security, or information technology (IT) security) is a subdiscipline within the field of information security. It consists of the protection of computer software, systems and computer network, networks from Threat (security), threats that can lead to unauthorized information disclosure, theft or damage to computer hardware, hardware, software, or Data (computing), data, as well as from the disruption or misdirection of the Service (economics), services they provide. The significance of the field stems from the expanded reliance on computer systems, the Internet, and wireless network standards. Its importance is further amplified by the growth of smart devices, including smartphones, televisions, and the various devices that constitute the Internet of things (IoT). Cybersecurity has emerged as one of the most significant new challenges facing the contemporary world, due to both the complexity of information systems and the societi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
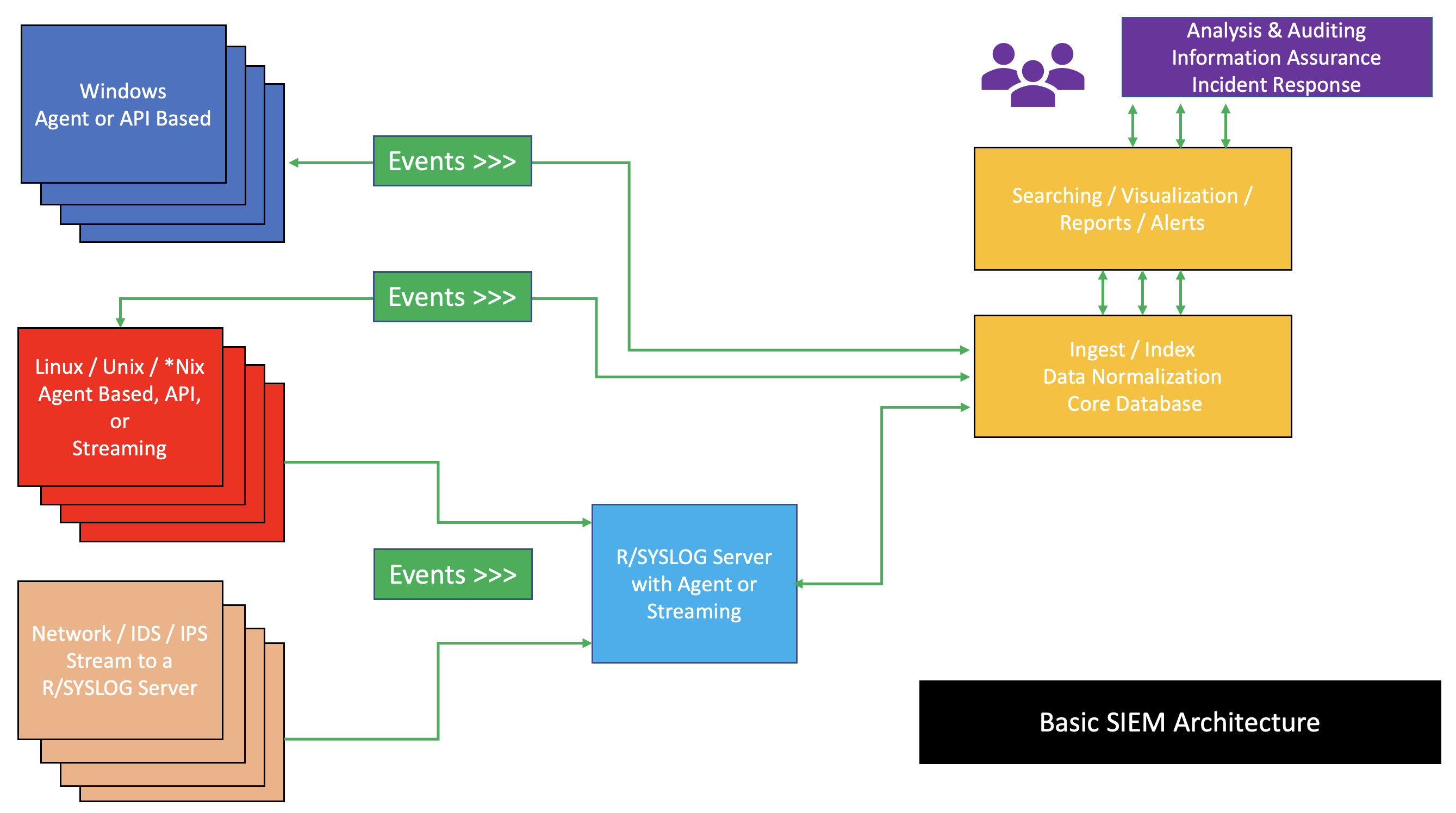
SIEM
Security information and event management (SIEM) is a field within computer security that combines security information management (SIM) and security event management (SEM) to enable real-time analysis of security alerts generated by applications and network hardware. SIEM systems are central to Security operations center, security operations centers (SOCs), where they are employed to detect, investigate, and respond to security incidents. SIEM technology collects and aggregates data from various systems, allowing organizations to meet compliance requirements while safeguarding against Cyberattack, threats. National Institute of Standards and Technology (NIST) definition for SIEM tool is application that provides the ability to gather security data from information system components and present that data as actionable information via a single interface. SIEM tools can be implemented as software, hardware, or managed services. SIEM systems log security events and generating reports to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Intel
Intel Corporation is an American multinational corporation and technology company headquartered in Santa Clara, California, and Delaware General Corporation Law, incorporated in Delaware. Intel designs, manufactures, and sells computer components such as central processing units (CPUs) and related products for business and consumer markets. It is one of the world's List of largest semiconductor chip manufacturers, largest semiconductor chip manufacturers by revenue, and ranked in the Fortune 500, ''Fortune'' 500 list of the List of largest companies in the United States by revenue, largest United States corporations by revenue for nearly a decade, from 2007 to 2016 Fiscal year, fiscal years, until it was removed from the ranking in 2018. In 2020, it was reinstated and ranked 45th, being the List of Fortune 500 computer software and information companies, 7th-largest technology company in the ranking. It was one of the first companies listed on Nasdaq. Intel supplies List of I ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hewlett Packard
The Hewlett-Packard Company, commonly shortened to Hewlett-Packard ( ) or HP, was an American multinational information technology company. It was founded by Bill Hewlett and David Packard in 1939 in a one-car garage in Palo Alto, California, where the company would remain headquartered for the remainder of its lifetime; this HP Garage is now a designated landmark and marked with a plaque calling it the "Birthplace of 'Silicon Valley. HP developed and provided a wide variety of hardware components, as well as software and related services, to consumers, small and medium-sized businesses ( SMBs), and fairly large companies, including customers in government sectors, until the company officially split into Hewlett Packard Enterprise and HP Inc. in 2015. HP initially produced a line of electronic test and measurement equipment. It won its first big contract in 1938 to provide the HP 200B, a variation of its first product, the HP 200A low-distortion frequency oscillator, for W ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Facebook
Facebook is a social media and social networking service owned by the American technology conglomerate Meta Platforms, Meta. Created in 2004 by Mark Zuckerberg with four other Harvard College students and roommates, Eduardo Saverin, Andrew McCollum, Dustin Moskovitz, and Chris Hughes, its name derives from the face book directories often given to American university students. Membership was initially limited to Harvard students, gradually expanding to other North American universities. Since 2006, Facebook allows everyone to register from 13 years old, except in the case of a handful of nations, where the age requirement is 14 years. , Facebook claimed almost 3.07 billion monthly active users worldwide. , Facebook ranked as the List of most-visited websites, third-most-visited website in the world, with 23% of its traffic coming from the United States. It was the most downloaded mobile app of the 2010s. Facebook can be accessed from devices with Internet connectivit ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Security Exploits
A computer is a machine that can be programmed to automatically carry out sequences of arithmetic or logical operations (''computation''). Modern digital electronic computers can perform generic sets of operations known as ''programs'', which enable computers to perform a wide range of tasks. The term computer system may refer to a nominally complete computer that includes the hardware, operating system, software, and peripheral equipment needed and used for full operation; or to a group of computers that are linked and function together, such as a computer network or computer cluster. A broad range of industrial and consumer products use computers as control systems, including simple special-purpose devices like microwave ovens and remote controls, and factory devices like industrial robots. Computers are at the core of general-purpose devices such as personal computers and mobile devices such as smartphones. Computers power the Internet, which links billions of computer ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Crowdsourcing
Crowdsourcing involves a large group of dispersed participants contributing or producing goods or services—including ideas, votes, micro-tasks, and finances—for payment or as volunteers. Contemporary crowdsourcing often involves digital platforms to attract and divide work between participants to achieve a cumulative result. Crowdsourcing is not limited to online activity, however, and there are various historical examples of crowdsourcing. The word crowdsourcing is a portmanteau of "crowd" and "outsourcing". In contrast to outsourcing, crowdsourcing usually involves less specific and more public groups of participants. Advantages of using crowdsourcing include lowered costs, improved speed, improved quality, increased flexibility, and/or increased scalability of the work, as well as promoting diversity. Crowdsourcing methods include competitions, virtual labor markets, open online collaboration and data donation. Some forms of crowdsourcing, such as in "idea competiti ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Security Databases
Security is protection from, or resilience against, potential harm (or other unwanted coercion). Beneficiaries (technically referents) of security may be persons and social groups, objects and institutions, ecosystems, or any other entity or phenomenon vulnerable to unwanted change. Security mostly refers to protection from hostile forces, but it has a wide range of other senses: for example, as the absence of harm (e.g., freedom from want); as the presence of an essential good (e.g., food security); as resilience against potential damage or harm (e.g. secure foundations); as secrecy (e.g., a secure telephone line); as containment (e.g., a secure room or cell); and as a state of mind (e.g., emotional security). Security is both a feeling and a state of reality. One might feel secure when one is not actually so; or might feel insecure despite being safe. This distinction is usually not very clear to express in the English language. The term is also used to refer to acts and ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |