|
Oligomorphic Code
Oligomorphic code, also known as semi-polymorphic code, is a method used by a computer virus to obfuscated code, obfuscate its decryptor by generating different versions of it, in order to evade detection by antivirus software. It is similar to, but less sophisticated than, polymorphic code. Oligomorphic code works by randomly selecting each piece of the decryptor from several predefined alternatives. At runtime (program lifecycle phase), run time, these components can be combined in various ways to create new, distinct versions of the decryptor. Having multiple possible decryptors makes it more difficult for a virus to be detected with anti-malware signatures. However, most oligomorphic viruses are only able to generate a limited amount of decryptors, around a few hundred, so detecting them with simple signatures is still possible. Another method to detect an oligomorphic decryptor is to make a signature for each possible piece of code, group pieces that can substitute each other ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Virus
A computer virus is a type of malware that, when executed, replicates itself by modifying other computer programs and Code injection, inserting its own Computer language, code into those programs. If this replication succeeds, the affected areas are then said to be "infected" with a computer virus, a metaphor derived from biological viruses. Computer viruses generally require a Computer program, host program. The virus writes its own code into the host program. When the program runs, the written virus program is executed first, causing infection and damage. By contrast, a computer worm does not need a host program, as it is an independent program or code chunk. Therefore, it is not restricted by the Computer program, host program, but can run independently and actively carry out attacks. Virus writers use social engineering (security), social engineering deceptions and exploit detailed knowledge of vulnerability (computing), security vulnerabilities to initially infect systems an ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Obfuscated Code
In software development, obfuscation is the practice of creating source or machine code that is intentionally difficult for humans or computers to understand. Similar to obfuscation in natural language, code obfuscation may involve using unnecessarily roundabout ways to write statements. Programmers often obfuscate code to conceal its purpose, logic, or embedded values. The primary reasons for doing so are to prevent tampering, deter reverse engineering, or to create a puzzle or recreational challenge to deobfuscate the code, a challenge often included in crackmes. While obfuscation can be done manually, it is more commonly performed using obfuscators. Overview The architecture and characteristics of some languages may make them easier to obfuscate than others. C, C++, and the Perl programming language are some examples of languages easy to obfuscate. Haskell is also quite obfuscatable despite being quite different in structure. The properties that make a language obfuscat ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Polymorphic Code
In computing, polymorphic code is code that uses a polymorphic engine to mutate while keeping the original algorithm intact - that is, the ''code'' changes itself every time it runs, but the ''function'' of the code (its semantics) stays the same. For example, the simple math expressions 3+1 and 6-2 both achieve the same result, yet run with different machine code in a CPU. This technique is sometimes used by computer viruses, shellcodes and computer worms to hide their presence. Encryption is the most common method to hide code. With encryption, the main body of the code (also called its payload) is encrypted and will appear meaningless. For the code to function as before, a decryption function is added to the code. When the code is ''executed'', this function reads the payload and decrypts it before executing it in turn. Encryption alone is not polymorphism. To gain polymorphic behavior, the encryptor/decryptor pair is mutated with each copy of the code. This allows differen ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
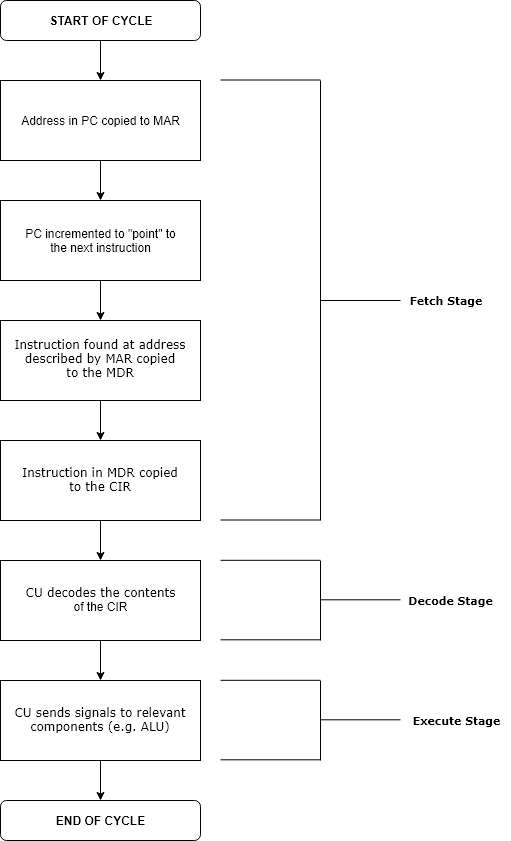
Runtime (program Lifecycle Phase)
Execution in computer engineering, computer and software engineering is the process by which a computer or virtual machine interprets and acts on the instructions of a computer program. Each instruction of a program is a description of a particular action which must be carried out, in order for a specific problem to be solved. Execution involves repeatedly following a "Instruction cycle, fetch–decode–execute" cycle for each instruction done by the control unit. As the executing machine follows the instructions, specific effects are produced in accordance with the Formal semantics of programming languages, semantics of those instructions. Programs for a computer may be executed in a Batch processing, batch process without human interaction or a User (computing), user may type Command (computing), commands in an Session (computer science), interactive session of an Interpreter (computing), interpreter. In this case, the "commands" are simply program instructions, whose executio ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Whale (computer Virus)
The Whale virus is a computer virus discovered on July 1, 1990. The file size, at 9,216 bytes, was for its time the largest virus ever discovered. It is known for using several advanced "stealth" methods. Description After the file becomes resident in the system memory below the 640K DOS boundary, system slow-down occurs as a result of the virus' polymorphic code. Symptoms include video flicker and output to screen appearing very slowly. Files may seem to "hang" even though they will eventually execute correctly. It was reported that one infected program displayed the following message when run: } Shifting the letters of "~knzyvo}" left in the ASCII table by 10 characters turns the string into "tadpoles". See also *Computer virus *Comparison of computer viruses Creating a unified list of computer viruses is challenging due to inconsistent naming conventions. To combat computer viruses and other malicious software, many security advisory organizations and anti ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Windows 95
Windows 95 is a consumer-oriented operating system developed by Microsoft and the first of its Windows 9x family of operating systems, released to manufacturing on July 14, 1995, and generally to retail on August 24, 1995. Windows 95 merged Microsoft's formerly separate MS-DOS and Microsoft Windows products into a single product and featured significant improvements over its predecessor, most notably in the graphical user interface (GUI) and in its simplified " plug-and-play" features. There were also major changes made to the core components of the operating system, such as moving from a mainly cooperatively multitasked 16-bit architecture of its predecessor Windows 3.1 to a 32-bit preemptive multitasking architecture. Windows 95 introduced numerous functions and features that were featured in later Windows versions, and continue in modern variations to this day, such as the taskbar, the notification area, file shortcuts on the desktop, plug and play driver integration, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Memorial (computer Virus)
A memorial is an object or place which serves as a focus for the memory or the commemoration of something, usually an influential, deceased person or a historical, tragic event. Popular forms of memorials include landmark objects such as homes or other sites, or works of art such as sculptures, statues, fountains or parks. Larger memorials may be known as monuments. Types The most common type of memorial is the gravestone or the memorial plaque. Also common are war memorials commemorating those who have died in wars. Memorials in the form of a cross are called intending crosses. Online memorials are often created on websites and social media to allow digital access as an alternative to physical memorials which may not be feasible or easily accessible. When somebody has died, the family may request that a memorial gift (usually money) be given to a designated charity, or that a tree be planted in memory of the person. Those temporary or makeshift memorials are also called gras ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Timeline Of Notable Computer Viruses And Worms
This timeline of computer viruses and worms presents a chronological timeline of noteworthy computer viruses, computer worms, Trojan horses, similar malware, related research and events. 1960s * John von Neumann's article on the "Theory of self-reproducing automata" is published in 1966. The article is based on lectures given by von Neumann at the University of Illinois about the "Theory and Organization of Complicated Automata" in 1949. 1970s 1970 * The first story written about a computer virus, ''The Scarred Man'' by Gregory Benford, was published in the May 1970 issue of '' Venture Science Fiction''. 1971 * The Creeper system, an experimental self-replicating program, is written by Bob Thomas at BBN Technologies to test John von Neumann's theory. Creeper infected DEC PDP-10 computers running the TENEX operating system. Creeper gained access via the ARPANET and copied itself to the remote system where the message "I'm the creeper, catch me if you can!" was disp ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Metamorphic Code
Metamorphic code is code that when run outputs a logically equivalent version of its own code under some interpretation. This is similar to a quine, except that a quine's source code is exactly equivalent to its own output. Metamorphic code also usually outputs machine code and not its own source code. Overview Metamorphic code is used by computer viruses to avoid the pattern recognition of anti-virus software. Metamorphic viruses often translate their own binary code into a temporary representation, editing the temporary representation of themselves and then translate the edited form back to machine code again. This procedure is done with the virus itself, and thus also the metamorphic engine itself undergoes changes, which means that no part of the virus stays the same. This differs from polymorphic code, where the polymorphic engine can not rewrite its own code. Metamorphic code is used by some viruses when they are about to infect new files, and the result is that the next gen ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Self-modifying Code
In computer science, self-modifying code (SMC or SMoC) is source code, code that alters its own instruction (computer science), instructions while it is execution (computing), executing – usually to reduce the instruction path length and improve computer performance, performance or simply to reduce otherwise duplicate code, repetitively similar code, thus simplifying software maintenance, maintenance. The term is usually only applied to code where the self-modification is intentional, not in situations where code accidentally modifies itself due to an error such as a buffer overflow. Self-modifying code can involve overwriting existing instructions or generating new code at run time and transferring control to that code. Self-modification can be used as an alternative to the method of "flag setting" and conditional program branching, used primarily to reduce the number of times a condition needs to be tested. The method is frequently used for conditionally invoking test/deb ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Alphanumeric Shellcode
In hacker (computer security), hacking, a shellcode is a small piece of code used as the Payload (computing), payload in the exploit (computer security), exploitation of a software Vulnerability (computing), vulnerability. It is called "shellcode" because it typically starts a Shell (computing), command shell from which the attacker can control the compromised machine, but any piece of code that performs a similar task can be called shellcode. Because the function of a payload is not limited to merely spawning a shell, some have suggested that the name shellcode is insufficient. However, attempts at replacing the term have not gained wide acceptance. Shellcode is commonly written in machine code. When creating shellcode, it is generally desirable to make it both small and executable, which allows it to be used in as wide a variety of situations as possible. In assembly code, the same function can be performed in a multitude of ways and there is some variety in the lengths of op ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |