|
KeeLoq
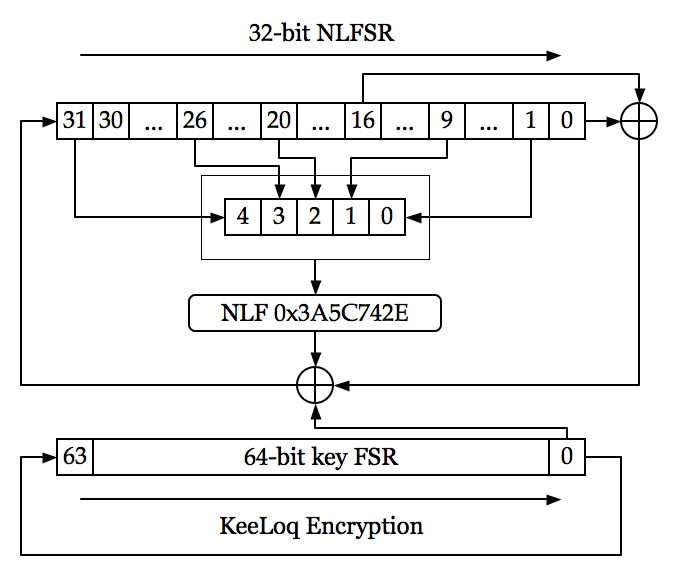
KeeLoq is a proprietary hardware-dedicated block cipher that uses a non-linear feedback shift register (NLFSR). The uni-directional command transfer protocol was designed by Frederick Bruwer of Nanoteq (Pty) Ltd., the cryptographic algorithm was created by Gideon Kuhn at the University of Pretoria, and the silicon implementation was by Willem Smit at Nanoteq Pty Ltd (South Africa) in the mid-1980s. KeeLoq was sold to Microchip Technology Inc in 1995 for $10 million. It is used in " code hopping" encoders and decoders such as NTQ105/106/115/125D/129D, HCS101/2XX/3XX/4XX/5XX and MCS31X2. KeeLoq is or was used in many remote keyless entry systems by such companies as Chrysler, Daewoo, Fiat, GM, Honda, Toyota, Volvo, Volkswagen Group, Clifford, Shurlok, and Jaguar. Description KeeLoq "code hopping" encoders encrypt a 0-filled 32-bit block with KeeLoq cipher to produce a 32-bit " hopping code". A 32-bit initialization vector is linearly added ( XORed) to the 32 least signifi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
KeeLoq
KeeLoq is a proprietary hardware-dedicated block cipher that uses a non-linear feedback shift register (NLFSR). The uni-directional command transfer protocol was designed by Frederick Bruwer of Nanoteq (Pty) Ltd., the cryptographic algorithm was created by Gideon Kuhn at the University of Pretoria, and the silicon implementation was by Willem Smit at Nanoteq Pty Ltd (South Africa) in the mid-1980s. KeeLoq was sold to Microchip Technology Inc in 1995 for $10 million. It is used in " code hopping" encoders and decoders such as NTQ105/106/115/125D/129D, HCS101/2XX/3XX/4XX/5XX and MCS31X2. KeeLoq is or was used in many remote keyless entry systems by such companies as Chrysler, Daewoo, Fiat, GM, Honda, Toyota, Volvo, Volkswagen Group, Clifford, Shurlok, and Jaguar. Description KeeLoq "code hopping" encoders encrypt a 0-filled 32-bit block with KeeLoq cipher to produce a 32-bit " hopping code". A 32-bit initialization vector is linearly added ( XORed) to the 32 least signifi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hopping Code
A rolling code (or sometimes called a hopping code) is used in keyless entry systems to prevent replay attacks, where an eavesdropper records the transmission and replays it at a later time to cause the receiver to 'unlock'. Such systems are typical in garage door openers and keyless car entry systems. Techniques * Common PRNG (pseudorandom number generator) — preferably cryptographically secure — in both transmitter and receiver * Transmitter sends 'next' code in sequence * Receiver compares 'next' to its calculated 'next' code. * A typical implementation compares within the next 256 codes in case receiver missed some transmitted keypresses. HMAC-based one-time password employed widely in multi-factor authentication uses similar approach, but with pre-shared secret key and HMAC instead of PRNG and pre-shared random seed. Application in RF remote control A rolling code transmitter is useful in a security system for providing secure encrypted radio frequency ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hopping Code
A rolling code (or sometimes called a hopping code) is used in keyless entry systems to prevent replay attacks, where an eavesdropper records the transmission and replays it at a later time to cause the receiver to 'unlock'. Such systems are typical in garage door openers and keyless car entry systems. Techniques * Common PRNG (pseudorandom number generator) — preferably cryptographically secure — in both transmitter and receiver * Transmitter sends 'next' code in sequence * Receiver compares 'next' to its calculated 'next' code. * A typical implementation compares within the next 256 codes in case receiver missed some transmitted keypresses. HMAC-based one-time password employed widely in multi-factor authentication uses similar approach, but with pre-shared secret key and HMAC instead of PRNG and pre-shared random seed. Application in RF remote control A rolling code transmitter is useful in a security system for providing secure encrypted radio frequency ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Microchip Technology
Microchip Technology Inc. is a publicly-listed American corporation that manufactures microcontroller, mixed-signal, analog and Flash-IP integrated circuits. Its products include microcontrollers ( PIC, dsPIC, AVR and SAM), Serial EEPROM devices, Serial SRAM devices, embedded security devices, radio frequency (RF) devices, thermal, power and battery management analog devices, as well as linear, interface and wireless products. Its corporate headquarters is located in Chandler, Arizona. Its wafer fabs are located in Tempe, Arizona, Gresham, Oregon, and Colorado Springs, Colorado. Its assembly/test facilities are in Chachoengsao, Thailand, and Calamba and Cabuyao, Philippines. Sales for the fiscal year ending on March 31, 2019 were $5.35 billion. Microchip Technology offers support and reso ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
NLFSR
A nonlinear-feedback shift register (NLFSR) is a shift register whose input bit is a non-linear function of its previous state. For an n-bit shift register ''r'' its next state is defined as: r_(b_0, b_1, b_2, \ldots, b_)=r_(b_1, b_2, \ldots, f(b_0, b_1, b_2, \ldots, b_)), where ''f'' is the non-linear feedback function. Applications Nonlinear-feedback shift registers are components in modern stream ciphers, especially in RFID and smartcard applications. NLFSRs are known to be more resistant to cryptanalytic attacks than Linear Feedback Shift Registers (LFSRs). Generating It is known how to generate an ''n''-bit NLFSR of maximal length ''2n'', generating a De Bruijn sequence, by extending a maximal-length LFSR with ''n'' stages; but the construction of other large NLFSRs with guaranteed long periods remains an open problem. Using bruteforce methods, a list of maximum-period ''n''-bit NLFSRs for n ≤ 25 has been made as well as for n=27. New methods suggest usage of evolution ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Tech Insider
''Insider'', previously named ''Business Insider'' (''BI''), is an American financial and business news website founded in 2007. Since 2015, a majority stake in ''Business Insider''s parent company Insider Inc. has been owned by the German publishing house Axel Springer. It operates several international editions, including one in the United Kingdom. ''Insider'' publishes original reporting and aggregates material from other outlets. , it maintained a liberal policy on the use of anonymous sources. It has also published native advertising and granted sponsors editorial control of its content. The outlet has been nominated for several awards, but is criticized for using factually incorrect clickbait headlines to attract viewership. In 2015, Axel Springer SE acquired 88 percent of the stake in Insider Inc. for $343 million (€306 million), implying a total valuation of $442 million. In February 2021, the brand was renamed simply ''Insider''. History ''Bus ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Samy Kamkar
Samy may refer to: *Samy (director) (active from 2006), Tamil film director *Samy (XSS), a computer worm *Samy (Mobile Marketing) ''MobileBits Corporation'' is an American marketing technology/advertising company that operated a pure brand mobile marketing and engagement network called Samy and which markets a software platform for developing mobile shopping applications. ... * * Sami (other) {{Disambig ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Replay Attack
A replay attack (also known as a repeat attack or playback attack) is a form of network attack in which valid data transmission is maliciously or fraudulently repeated or delayed. This is carried out either by the originator or by an adversary who intercepts the data and re-transmits it, possibly as part of a spoofing attack by IP packet substitution. This is one of the lower-tier versions of a man-in-the-middle attack. Replay attacks are usually passive in nature. Another way of describing such an attack is: "an attack on a security protocol using a replay of messages from a different context into the intended (or original and expected) context, thereby fooling the honest participant(s) into thinking they have successfully completed the protocol run." Example Suppose Alice wants to prove her identity to Bob. Bob requests her password as proof of identity, which Alice dutifully provides (possibly after some transformation like hashing, or even salting, the password); meanwhil ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Least Significant Bit
In computing, bit numbering is the convention used to identify the bit positions in a binary number. Bit significance and indexing In computing, the least significant bit (LSB) is the bit position in a binary integer representing the binary 1s place of the integer. Similarly, the most significant bit (MSB) represents the highest-order place of the binary integer. The LSB is sometimes referred to as the ''low-order bit'' or ''right-most bit'', due to the convention in positional notation of writing less significant digits further to the right. The MSB is similarly referred to as the ''high-order bit'' or ''left-most bit''. In both cases, the LSB and MSB correlate directly to the least significant digit and most significant digit of a decimal integer. Bit indexing correlates to the positional notation of the value in base 2. For this reason, bit index is not affected by how the value is stored on the device, such as the value's byte order. Rather, it is a property of the n ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptographic Nonce
In cryptography, a nonce is an arbitrary number that can be used just once in a cryptographic communication. It is often a random or pseudo-random number issued in an authentication protocol to ensure that old communications cannot be reused in replay attacks. They can also be useful as initialization vectors and in cryptographic hash functions. Definition A nonce is an arbitrary number used only once in a cryptographic communication, in the spirit of a nonce word. They are often random or pseudo-random numbers. Many nonces also include a timestamp to ensure exact timeliness, though this requires clock synchronisation between organisations. The addition of a client nonce ("cnonce") helps to improve the security in some ways as implemented in digest access authentication. To ensure that a nonce is used only once, it should be time-variant (including a suitably fine-grained timestamp in its value), or generated with enough random bits to ensure a insignificantly low chance ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
DEF CON
DEF CON (also written as DEFCON, Defcon or DC) is a hacker convention held annually in Las Vegas, Nevada. The first DEF CON took place in June 1993 and today many attendees at DEF CON include computer security professionals, journalists, lawyers, federal government employees, security researchers, students, and hackers with a general interest in software, computer architecture, hardware modification, conference badges, and anything else that can be "hacked". The event consists of several tracks of speakers about computer- and hacking-related subjects, as well as cyber-security challenges and competitions (known as hacking wargames). Contests held during the event are extremely varied, and can range from creating the longest Wi-Fi connection to finding the most effective way to cool a beer in the Nevada heat. Other contests, past and present, include lockpicking, robotics-related contests, art, slogan, coffee wars, scavenger hunt and Capture the Flag. Capture the Flag (CTF ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Replay Attack
A replay attack (also known as a repeat attack or playback attack) is a form of network attack in which valid data transmission is maliciously or fraudulently repeated or delayed. This is carried out either by the originator or by an adversary who intercepts the data and re-transmits it, possibly as part of a spoofing attack by IP packet substitution. This is one of the lower-tier versions of a man-in-the-middle attack. Replay attacks are usually passive in nature. Another way of describing such an attack is: "an attack on a security protocol using a replay of messages from a different context into the intended (or original and expected) context, thereby fooling the honest participant(s) into thinking they have successfully completed the protocol run." Example Suppose Alice wants to prove her identity to Bob. Bob requests her password as proof of identity, which Alice dutifully provides (possibly after some transformation like hashing, or even salting, the password); meanwhil ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |