|
Inter-domain Routing
Inter-domain routing is data flow control and interaction between Primary Domain Controller (PDC) computers. This type of computer uses various computer protocols and services to operate. It is most commonly used to multicast between internet domains. Internet use An Internet service provider, ISP, is provided with a unique URL access address. This address is a unique number. The number for each ISP is stored within a DNS server. The DNS servers interpret the ISP URL Domain name and provide the appropriate IP address number. The Domain is under the control of a specialized computer, called a PDC, (primary domain controller). This computer holds records of all the user accounts within the domain, their rights to access information, and lists of approved System Operatives. This PDC is backed up by an SDC, (a secondary domain controller), this computer synchronises itself with the PDC and takes over the role in the event of a PDC failure. Multiple replication servers connect to t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Active Directory
Active Directory (AD) is a directory service developed by Microsoft for Windows domain networks. Windows Server operating systems include it as a set of processes and services. Originally, only centralized domain management used Active Directory. However, it ultimately became an umbrella title for various directory-based identity-related services. A domain controller is a server running the Active Directory Domain Services (AD DS) role. It authenticates and authorizes all users and computers in a Windows domain-type network, assigning and enforcing security policies for all computers and installing or updating software. For example, when a user logs into a computer which is part of a Windows domain, Active Directory checks the submitted username and password and determines whether the user is a system administrator or a non-admin user. Furthermore, it allows the management and storage of information, provides authentication and authorization mechanisms, and establishes a f ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Protocol (computing)
A communication protocol is a system of rules that allows two or more entities of a communications system to transmit information via any variation of a physical quantity. The protocol defines the rules, syntax, semantics, and synchronization of communication and possible error recovery methods. Protocols may be implemented by hardware, software, or a combination of both. Communicating systems use well-defined formats for exchanging various messages. Each message has an exact meaning intended to elicit a response from a range of possible responses predetermined for that particular situation. The specified behavior is typically independent of how it is to be implemented. Communication protocols have to be agreed upon by the parties involved. To reach an agreement, a protocol may be developed into a technical standard. A programming language describes the same for computations, so there is a close analogy between protocols and programming languages: ''protocols are to communica ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Autonomous System (Internet)
An autonomous system (AS) is a collection of connected Internet protocol address, Internet Protocol (IP) routing prefixes under the control of one or more network operators on behalf of a single administrative entity or domain, that presents a common and clearly defined routing policy to the Internet. Each AS is assigned an autonomous system number (ASN), for use in Border Gateway Protocol (BGP) routing. Autonomous System Numbers are assigned to Regional_Internet_registry#Local_Internet_registry, local Internet registries (LIRs) and end-user organizations by their respective Regional Internet registry, regional Internet registries (RIRs), which in turn receive blocks of ASNs for reassignment from the Internet Assigned Numbers Authority (IANA). The IANA also maintains a registry of ASNs which are reserved for private use (and should therefore not be announced to the global Internet). Originally, the definition required control by a single entity, typically an Internet service provid ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Digital Information
Digital data, in information theory and information systems, is information represented as a string of Discrete mathematics, discrete symbols, each of which can take on one of only a finite number of values from some alphabet (formal languages), alphabet, such as letters or digits. An example is a text document, which consists of a string of alphanumeric characters. The most common form of digital data in modern information systems is ''binary data'', which is represented by a string of binary digits (bits) each of which can have one of two values, either 0 or 1. Digital data can be contrasted with ''analog data'', which is represented by a value from a continuous variable, continuous range of real numbers. Analog data is transmitted by an analog signal, which not only takes on continuous values but can vary continuously with time, a continuous real-valued function of time. An example is the air pressure variation in a sound wave. The word ''digital'' comes from the same sour ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Web Browser
A web browser, often shortened to browser, is an application for accessing websites. When a user requests a web page from a particular website, the browser retrieves its files from a web server and then displays the page on the user's screen. Browsers can also display content stored locally on the user's device. Browsers are used on a range of devices, including desktops, laptops, tablets, smartphones, smartwatches and consoles. As of 2024, the most used browsers worldwide are Google Chrome (~66% market share), Safari (~16%), Edge (~6%), Firefox (~3%), Samsung Internet (~2%), and Opera (~2%). As of 2023, an estimated 5.4 billion people had used a browser. Function The purpose of a web browser is to fetch content and display it on the user's device. This process begins when the user inputs a Uniform Resource Locator (URL), such as ''https://en.wikipedia.org/'', into the browser's address bar. Virtually all URLs on the Web start with either ''http:'' or ''h ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Windows Internet Name Service
Windows Internet Name Service (WINS) is a Microsoft name resolution service, introduced in 1994 with Windows NT 3.5, for translating NetBIOS names to IP addresses. NetBIOS names are an older naming convention used for local name resolution before DNS became ubiquitous. WINS is mostly unnecessary for modern networks unless legacy systems require it. The rise of DNS, especially through Microsoft's Active Directory service's DNS support, made WINS effectively obsolete by the mid-2000s. Microsoft documentation advises not to use WINS on networks not requiring it. Details WINS is Microsoft's implementation of the NetBIOS Name Service (NBNS), a name server and service for NetBIOS computer names. Effectively, WINS is to NetBIOS names what DNS is to domain names — a central mapping of host names to network addresses. Like the DNS, it is implemented in two parts, a server service (that manages the embedded Jet Database, server to server replication, service requests, and conflicts) ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Program
A computer program is a sequence or set of instructions in a programming language for a computer to Execution (computing), execute. It is one component of software, which also includes software documentation, documentation and other intangible components. A ''computer program'' in its human-readable form is called source code. Source code needs another computer program to Execution (computing), execute because computers can only execute their native machine instructions. Therefore, source code may be Translator (computing), translated to machine instructions using a compiler written for the language. (Assembly language programs are translated using an Assembler (computing), assembler.) The resulting file is called an executable. Alternatively, source code may execute within an interpreter (computing), interpreter written for the language. If the executable is requested for execution, then the operating system Loader (computing), loads it into Random-access memory, memory and ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Protocol Independent Multicast
image:IGMP basic architecture.png, 400px, Example of a multicast network architecture Protocol-Independent Multicast (PIM) is a family of multicast routing protocols for Internet Protocol (IP) networks that provide Point-to-multipoint communication, one-to-many and many-to-many distribution of data over a LAN, Wide area network, WAN or the Internet. It is termed ''protocol-independent'' because PIM does not include its own network topology, topology discovery mechanism, but instead uses routing information supplied by other routing protocols. PIM is not dependent on a specific unicast routing protocol; it can make use of any unicast routing protocol in use on the network. PIM does not build its own routing tables. PIM uses the unicast routing table for reverse-path forwarding. There are four variants of PIM: * PIM Sparse Mode (PIM-SM) explicitly builds unidirectional shared trees rooted at a ''rendezvous point'' (RP) per group, and optionally creates shortest-path trees per sourc ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Multicast Source Discovery Protocol
Multicast Source Discovery Protocol (MSDP) is a Protocol Independent Multicast (PIM) family multicast routing protocol defined by Experimental RFC 3618. Despite becoming the IPv4 de facto standard for inter-domain multicast, development of the protocol stopped in 2006 and it was decided by the authors not to proceed with making it a proposed standard. MSDP interconnects multiple IPv4 PIM Sparse-Mode (PIM-SM) domains which enables PIM-SM to have Rendezvous Point (RP) redundancy and inter-domain multicasting RFC 4611. MSDP uses TCP as its transport protocol. Each multicast tree needs to have its own RP. All of the RPs are peers (directly or through other MSDP peers). Messages contain the sender (source) address and the multicast group address (S,G). If an RP on its own domain receives a message, it determines if there are listeners for this group. If listeners exist, it triggers a PIM join into the source domain towards the data source. In a peering relationship, one MSDP pee ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Classless Inter-Domain Routing
Classless Inter-Domain Routing (CIDR ) is a method for allocating IP addresses for IP routing. The Internet Engineering Task Force introduced CIDR in 1993 to replace the previous classful network addressing architecture on the Internet. Its goal was to slow the growth of routing tables on routers across the Internet, and to help slow the rapid exhaustion of IPv4 addresses. IP addresses are described as consisting of two groups of bits in the address: the most significant bits are the network prefix, which identifies a whole network or subnet, and the least significant set forms the ''host identifier'', which specifies a particular interface of a host on that network. This division is used as the basis of traffic routing between IP networks and for address allocation policies. Whereas classful network design for IPv4 sized the network prefix as one or more 8-bit groups, resulting in the blocks of Class A, B, or C addresses, under CIDR address space is allocated to Internet ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Border Gateway Multicast Protocol
The Border Gateway Multicast Protocol (BGMP) was an IETF The Internet Engineering Task Force (IETF) is a standards organization for the Internet standard, Internet and is responsible for the technical standards that make up the Internet protocol suite (TCP/IP). It has no formal membership roster ... project which attempted to design a true inter-domain multicast routing protocol. BGMP was planned to be able to scale in order to operate in the global Internet. References External links *RFC 3913: Border Gateway Multicast Protocol] BGMP Protocol Specification. September 2004.Border Gateway Multicast Protocol IETF charter Internet Standards [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
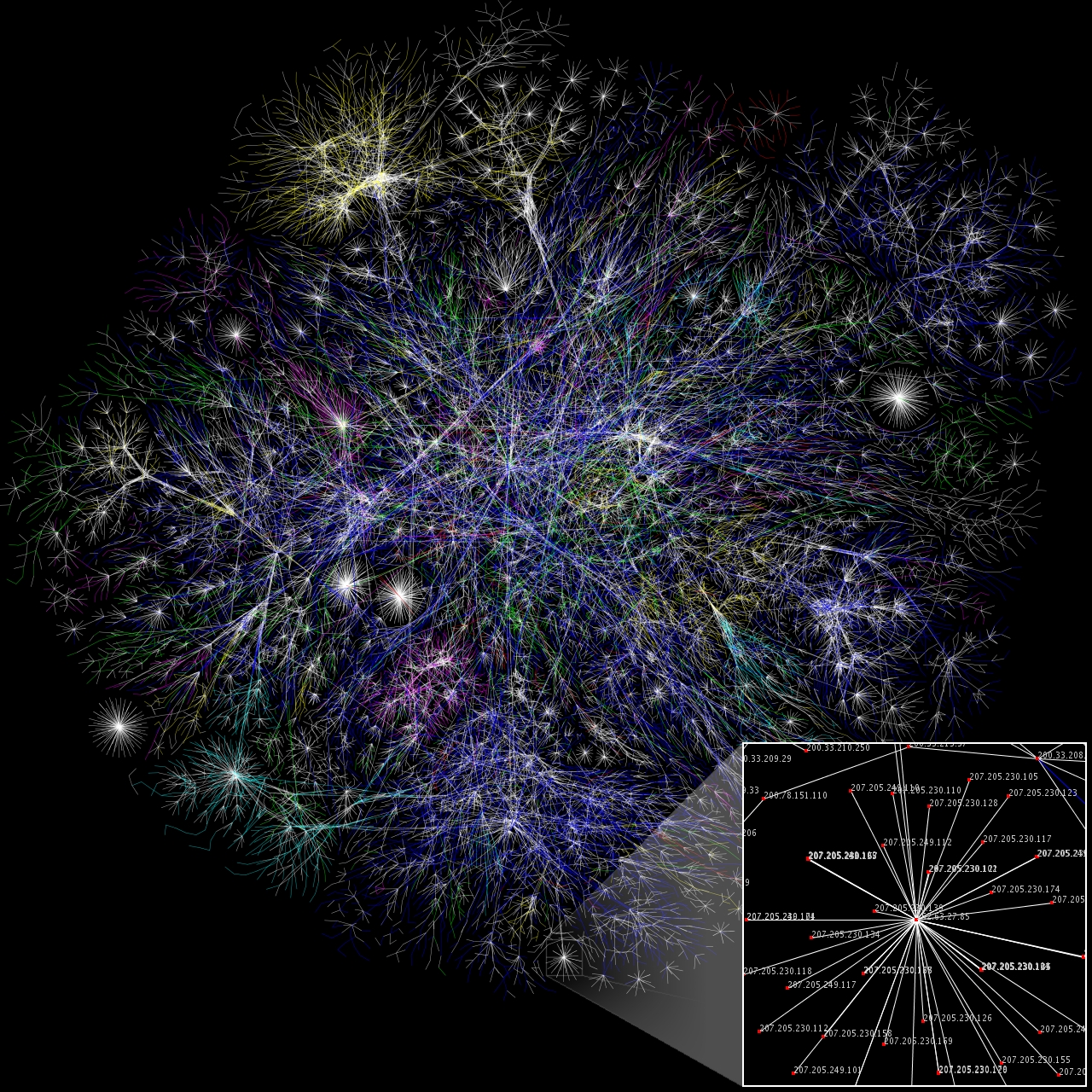
Internet Backbone
The Internet backbone is the principal data routes between large, strategically interconnected computer networks and core routers of the Internet. These data routes are hosted by commercial, government, academic and other high-capacity network centers as well as the Internet exchange points and network access points, which exchange Internet traffic internationally. Internet service providers (ISPs) participate in Internet backbone traffic through privately negotiated interconnection agreements, primarily governed by the principle of settlement-free peering. The Internet, and consequently its backbone networks, do not rely on central control or coordinating facilities, nor do they implement any global network policies. The resilience of the Internet results from its principal architectural features, such as the idea of placing as few network state and control functions as possible in the network elements, instead relying on the endpoints of communication to handle most of the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |