|
Ian Avrum Goldberg
Ian Avrum Goldberg (born March 31, 1973) is a cryptographer and cypherpunk. He is best known for breaking Netscape's implementation of SSL (with David Wagner), and for his role as chief scientist of Radialpoint (formerly Zero Knowledge Systems), a Canadian software company. Goldberg is currently a professor at the Faculty of Mathematics of the David R. Cheriton School of Computer Science within the University of Waterloo, and the Canada Research Chair in Privacy Enhancing Technologies. He was formerly Tor Project board of directors chairman, and is one of the designers of off the record messaging. Education Goldberg attended high school at the University of Toronto Schools, graduating in 1991. In 1995, he received a B.Math from the University of Waterloo in pure mathematics and computer science. He obtained a Ph.D. from the University of California, Berkeley in December 2000. His thesis was entitled ''A Pseudonymous Communications Infrastructure for the Internet''. His a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
University Of California, Berkeley
The University of California, Berkeley (UC Berkeley, Berkeley, Cal, or California), is a Public university, public Land-grant university, land-grant research university in Berkeley, California, United States. Founded in 1868 and named after the Anglo-Irish philosopher George Berkeley, it is the state's first land-grant university and is the founding campus of the University of California system. Berkeley has an enrollment of more than 45,000 students. The university is organized around fifteen schools of study on the same campus, including the UC Berkeley College of Chemistry, College of Chemistry, the UC Berkeley College of Engineering, College of Engineering, UC Berkeley College of Letters and Science, College of Letters and Science, and the Haas School of Business. It is Carnegie Classification of Institutions of Higher Education, classified among "R1: Doctoral Universities – Very high research activity". Lawrence Berkeley National Laboratory was originally founded as par ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
International Mathematical Olympiad
The International Mathematical Olympiad (IMO) is a mathematical olympiad for pre-university students, and is the oldest of the International Science Olympiads. It is widely regarded as the most prestigious mathematical competition in the world. The first IMO was held in Romania in 1959. It has since been held annually, except in 1980. More than 100 countries participate. Each country sends a team of up to six students, plus one team leader, one deputy leader, and observers. Awards are given to approximately the top-scoring 50% of the individual contestants. Teams are not officially recognized—all scores are given only to individual contestants, but team scoring is unofficially compared more than individual scores. Question type The content ranges from extremely difficult algebra and pre-calculus problems to problems in branches of mathematics not conventionally covered in secondary or high school and often not at university level either, such as projective and complex geo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Bitcoin
Bitcoin (abbreviation: BTC; Currency symbol, sign: ₿) is the first Decentralized application, decentralized cryptocurrency. Based on a free-market ideology, bitcoin was invented in 2008 when an unknown entity published a white paper under the pseudonym of Satoshi Nakamoto. Use of bitcoin as a currency began in 2009, with the release of its open-source software, open-source implementation. In 2021, Bitcoin in El Salvador, El Salvador adopted it as legal tender. It is mostly seen as an investment and has been described by some scholars as an economic bubble. As bitcoin is pseudonymous, Cryptocurrency and crime, its use by criminals has attracted the attention of regulators, leading to Legality of cryptocurrency by country or territory, its ban by several countries . Bitcoin works through the collaboration of computers, each of which acts as a Node (networking), node in the peer-to-peer bitcoin network. Each node maintains an independent copy of a public distributed ledger of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Neal Stephenson
Neal Town Stephenson (born October 31, 1959) is an American writer known for his works of speculative fiction. His novels have been categorized as science fiction, historical fiction, cyberpunk, and baroque. Stephenson's work explores mathematics, cryptography, linguistics, philosophy, currency, and the history of science. He also writes nonfiction articles about technology in publications such as ''Wired (magazine), Wired''. He has written novels with his uncle, George Jewsbury ("J. Frederick George"), under the collective pseudonym Stephen Bury. Stephenson has worked part-time as an advisor for Blue Origin, a company (founded by Jeff Bezos) developing a spacecraft and a space launch system, and also co-founded the Subutai Corporation, whose first offering is the interactive fiction project ''The Mongoliad''. He was Magic Leap's Chief Futurist from 2014 to 2020. Early life Born on October 31, 1959, in Fort Meade, Maryland, Stephenson came from a family of engineers and scienti ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptonomicon
''Cryptonomicon'' is a 1999 novel by American author Neal Stephenson, set in two different time periods. One group of characters are World War II–era Allied codebreakers and tactical-deception operatives affiliated with the British Government Code and Cypher School at Bletchley Park, and disillusioned Axis military and intelligence figures. The second narrative is set in the late 1990s, with characters that are (in part) descendants of those of the earlier time period, who employ cryptologic, telecom, and computer technology to build an underground data haven in the fictional Sultanate of Kinakuta. Their goal is to facilitate anonymous Internet banking using electronic money and (later) digital gold currency, with a long-term objective to distribute Holocaust Education and Avoidance Pod (HEAP) media for instructing genocide-target populations on defensive warfare. Genre and subject matter ''Cryptonomicon'' is closer to the genres of historical fiction and contemporary ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Perl
Perl is a high-level, general-purpose, interpreted, dynamic programming language. Though Perl is not officially an acronym, there are various backronyms in use, including "Practical Extraction and Reporting Language". Perl was developed by Larry Wall in 1987 as a general-purpose Unix scripting language to make report processing easier. Since then, it has undergone many changes and revisions. Perl originally was not capitalized and the name was changed to being capitalized by the time Perl 4 was released. The latest release is Perl 5, first released in 1994. From 2000 to October 2019 a sixth version of Perl was in development; the sixth version's name was changed to Raku. Both languages continue to be developed independently by different development teams which liberally borrow ideas from each other. Perl borrows features from other programming languages including C, sh, AWK, and sed. It provides text processing facilities without the arbitrary data-length limits of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
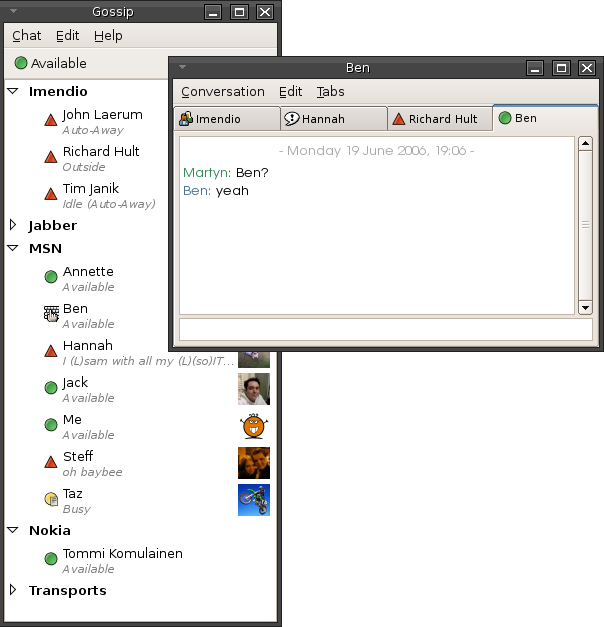
Instant Messaging
Instant messaging (IM) technology is a type of synchronous computer-mediated communication involving the immediate ( real-time) transmission of messages between two or more parties over the Internet or another computer network. Originally involving simple text message exchanges, modern IM applications and services (also called "social messengers", "messaging apps", "chat apps" or "chat clients") tend to also feature the exchange of multimedia, emojis, file transfer, VoIP (voice calling), and video chat capabilities. Instant messaging systems facilitate connections between specified known users (often using a contact list also known as a "buddy list" or "friend list") or in chat rooms, and can be standalone apps or integrated into a wider social media platform, or in a website where it can, for instance, be used for conversational commerce. Originally the term "instant messaging" was distinguished from " text messaging" by being run on a computer network instead of a cellula ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Nikita Borisov
Nikita Borisov is a cryptographer and computer security researcher, currently a professor at the University of Illinois at Urbana-Champaign. His notable work includes one of the first cryptanalyses of the WEP wireless encryption protocol together with Ian Goldberg and David Wagner, and the design of the Off-the-Record Messaging protocol with Goldberg. Borisov received a B. Math in computer science and pure math in 1997 from the University of Waterloo. He received an M.S. and a Ph.D. in computer science from the University of California, Berkeley The University of California, Berkeley (UC Berkeley, Berkeley, Cal, or California), is a Public university, public Land-grant university, land-grant research university in Berkeley, California, United States. Founded in 1868 and named after t ... in 2002 and 2005, respectively. References External linksNikita Borisov's page at the University of Illinois Living people 1977 births Modern cryptographers Cypherpunks Com ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Wired Equivalent Privacy
Wired Equivalent Privacy (WEP) is an obsolete, and insecure security algorithm for 802.11 wireless networks. It was introduced as part of the original IEEE 802.11 standard ratified in 1997. The intention was to provide a level of security and privacy comparable to that of a traditional wired network. WEP, recognizable by its key of 10 or 26 hexadecimal digits (40 or 104 bits), was at one time widely used, and was often the first security choice presented to users by router configuration tools. After a severe design flaw in the algorithm was disclosed in 2001, WEP was no longer considered a secure method of wireless connection; however, in the vast majority of cases, Wi-Fi hardware devices relying on WEP security could not be upgraded to secure operation. Some of WEP's design flaws were addressed in WEP2, but it also proved insecure, and never saw wide adoption or standardization. In 2003, the Wi-Fi Alliance announced that WEP and WEP2 had been superseded by Wi-Fi Protected Acc ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Netscape Navigator
The 1990s releases of the Netscape (web browser), Netscape line referred to as Netscape Navigator were a series of now discontinued web browsers. from versions 1 to 4.08. It was the Core product, flagship product of the Netscape, Netscape Communications Corporation and was the dominant web browser in terms of Usage share of web browsers, usage share in the 1990s, but by around 2003 its user base had all but disappeared. This was partly because of Microsoft's bundling of Internet Explorer with the Microsoft Windows, Windows operating system. The business demise of Netscape was a central premise of United States v. Microsoft Corp., Microsoft's antitrust trial, wherein the Court ruled that Microsoft's bundling of Internet Explorer with the Microsoft Windows, Windows operating system was a monopoly, monopolistic and illegal business practice. The decision came too late for Netscape, however, as Internet Explorer had by then become the dominant web browser in Windows. The Netscape ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Random Number Generator
Random number generation is a process by which, often by means of a random number generator (RNG), a sequence of numbers or symbols is generated that cannot be reasonably predicted better than by random chance. This means that the particular outcome sequence will contain some patterns detectable in hindsight but impossible to foresee. True random number generators can be '' hardware random-number generators'' (HRNGs), wherein each generation is a function of the current value of a physical environment's attribute that is constantly changing in a manner that is practically impossible to model. This would be in contrast to so-called "random number generations" done by ''pseudorandom number generators'' (PRNGs), which generate numbers that only look random but are in fact predetermined—these generations can be reproduced simply by knowing the state of the PRNG. Various applications of randomness have led to the development of different methods for generating random data. Some of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
ACM Fellow
ACM Fellowship is an award and fellowship that recognises outstanding members of the Association for Computing Machinery (ACM). The title of ACM Fellow A fellow is a title and form of address for distinguished, learned, or skilled individuals in academia, medicine, research, and industry. The exact meaning of the term differs in each field. In learned society, learned or professional society, p ... indicates excellence, as evinced by technical, professional and leadership contributions that: * advance computing * promote the free exchange of ideas * advance the objectives of ACM At most 1% of the ACM membership may be elected as Fellows. New fellows are elected annually since 1993. See also * Fellows of the ACM (by year) * Fellows of the ACM (category) References {{authority control ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |