|
Cdb (software)
cdb, short for "constant database", refers to both a library and data format created by Daniel J. Bernstein. cdb acts as an on-disk associative array, mapping keys to values, and allows multiple values to be stored for a single key. A constant database allows only two operations: creation and reading. Both operations are designed to be very fast and highly reliable. Since the database does not change while it is in use, multiple processes can access a single database without locking. Additionally, since all modifications create a replacement database, it can take advantage of UNIX filesystem semantics to provide a guarantee of reliability. Record positions, key and value lengths, and hash values are 32-bit quantities and therefore must fit into 4 gigabytes. cdb is used by djbdns, fastforward, mess822, qmail and ucspi-tcp to provide highly efficient, reliable, and simple data access. Structure A database contains an entire data set (e.g. a single associative array) in a single ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Library (computing)
In computer science, a library is a collection of non-volatile resources used by computer programs, often for software development. These may include configuration data, documentation, help data, message templates, pre-written code and subroutines, classes, values or type specifications. In IBM's OS/360 and its successors they are referred to as partitioned data sets. A library is also a collection of implementations of behavior, written in terms of a language, that has a well-defined interface by which the behavior is invoked. For instance, people who want to write a higher-level program can use a library to make system calls instead of implementing those system calls over and over again. In addition, the behavior is provided for reuse by multiple independent programs. A program invokes the library-provided behavior via a mechanism of the language. For example, in a simple imperative language such as C, the behavior in a library is invoked by using C's normal functi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Algorithm
In mathematics and computer science, an algorithm () is a finite sequence of rigorous instructions, typically used to solve a class of specific problems or to perform a computation. Algorithms are used as specifications for performing calculations and data processing. More advanced algorithms can perform automated deductions (referred to as automated reasoning) and use mathematical and logical tests to divert the code execution through various routes (referred to as automated decision-making). Using human characteristics as descriptors of machines in metaphorical ways was already practiced by Alan Turing with terms such as "memory", "search" and "stimulus". In contrast, a heuristic is an approach to problem solving that may not be fully specified or may not guarantee correct or optimal results, especially in problem domains where there is no well-defined correct or optimal result. As an effective method, an algorithm can be expressed within a finite amount of space ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
DBM (computing)
In computing, a DBM is a library and file format providing fast, single-keyed access to data. A key-value database from the original Unix, ''dbm'' is an early example of a NoSQL system. History The original ''dbm'' library and file format was a simple database engine, originally written by Ken Thompson and released by AT&T in 1979. The name is a three letter acronym for ''DataBase Manager'', and can also refer to the family of database engines with APIs and features derived from the original ''dbm''. The ''dbm'' library stores arbitrary data by use of a single key (a primary key) in fixed-size buckets and uses hashing techniques to enable fast retrieval of the data by key. The hashing scheme used is a form of extendible hashing, so that the hashing scheme expands as new buckets are added to the database, meaning that, when nearly empty, the database starts with one bucket, which is then split when it becomes full. The two resulting child buckets will themselves split when the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
License-free Software
License-free software is computer software that is not explicitly in the public domain, but the authors appear to intend free use, modification, distribution and distribution of the modified software, similar to the freedoms defined for free software. Since the author of the software has not made the terms of the license explicit, the software is technically copyrighted according to the Berne convention and as such is proprietary. Examples Examples of license-free software formerly included programs written by Daniel J. Bernstein, such as qmail, djbdns, daemontools, and ucspi-tcp. Bernstein held the copyright and distributed these works without license until 2007. From December 28, 2007, onwards, he started placing his software in the public domain with an explicit waiver statement. Additionally, small scripts are frequently released without specifying a license. For example, the website Userscripts.org hosts more than 52,000 Greasemonkey user scripts, the majority of which h ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Public Domain
The public domain (PD) consists of all the creative work to which no exclusive intellectual property rights apply. Those rights may have expired, been forfeited, expressly waived, or may be inapplicable. Because those rights have expired, anyone can legally use or reference those works without permission. As examples, the works of William Shakespeare, Ludwig van Beethoven, Leonardo da Vinci and Georges Méliès are in the public domain either by virtue of their having been created before copyright existed, or by their copyright term having expired. Some works are not covered by a country's copyright laws, and are therefore in the public domain; for example, in the United States, items excluded from copyright include the formulae of Newtonian physics, cooking recipes,Copyright Protection ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Exclusive Or
Exclusive or or exclusive disjunction is a logical operation that is true if and only if its arguments differ (one is true, the other is false). It is symbolized by the prefix operator J and by the infix operators XOR ( or ), EOR, EXOR, , , , , , and . The negation of XOR is the logical biconditional, which yields true if and only if the two inputs are the same. It gains the name "exclusive or" because the meaning of "or" is ambiguous when both operands are true; the exclusive or operator ''excludes'' that case. This is sometimes thought of as "one or the other but not both". This could be written as "A or B, but not, A and B". Since it is associative, it may be considered to be an ''n''-ary operator which is true if and only if an odd number of arguments are true. That is, ''a'' XOR ''b'' XOR ... may be treated as XOR(''a'',''b'',...). Truth table The truth table of A XOR B shows that it outputs true whenever the inputs differ: Equivalences, elimination, and introdu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
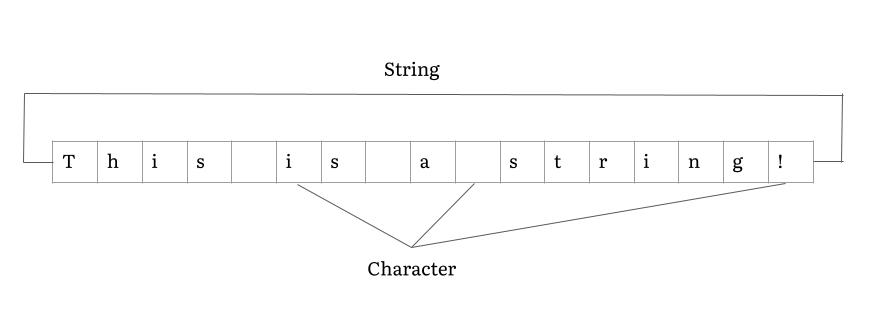
String (computer Science)
In computer programming, a string is traditionally a sequence of characters, either as a literal constant or as some kind of variable. The latter may allow its elements to be mutated and the length changed, or it may be fixed (after creation). A string is generally considered as a data type and is often implemented as an array data structure of bytes (or words) that stores a sequence of elements, typically characters, using some character encoding. ''String'' may also denote more general arrays or other sequence (or list) data types and structures. Depending on the programming language and precise data type used, a variable declared to be a string may either cause storage in memory to be statically allocated for a predetermined maximum length or employ dynamic allocation to allow it to hold a variable number of elements. When a string appears literally in source code, it is known as a string literal or an anonymous string. In formal languages, which are used in ma ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Little Endian
In computing, endianness, also known as byte sex, is the order or sequence of bytes of a word of digital data in computer memory. Endianness is primarily expressed as big-endian (BE) or little-endian (LE). A big-endian system stores the most significant byte of a word at the smallest memory address and the least significant byte at the largest. A little-endian system, in contrast, stores the least-significant byte at the smallest address. Bi-endianness is a feature supported by numerous computer architectures that feature switchable endianness in data fetches and stores or for instruction fetches. Other orderings are generically called middle-endian or mixed-endian. Endianness may also be used to describe the order in which the bits are transmitted over a communication channel, e.g., big-endian in a communications channel transmits the most significant bits first. Bit-endianness is seldom used in other contexts. Etymology Danny Cohen introduced the terms ''big-endian' ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Integer
An integer is the number zero (), a positive natural number (, , , etc.) or a negative integer with a minus sign ( −1, −2, −3, etc.). The negative numbers are the additive inverses of the corresponding positive numbers. In the language of mathematics, the set of integers is often denoted by the boldface or blackboard bold \mathbb. The set of natural numbers \mathbb is a subset of \mathbb, which in turn is a subset of the set of all rational numbers \mathbb, itself a subset of the real numbers \mathbb. Like the natural numbers, \mathbb is countably infinite. An integer may be regarded as a real number that can be written without a fractional component. For example, 21, 4, 0, and −2048 are integers, while 9.75, , and are not. The integers form the smallest group and the smallest ring containing the natural numbers. In algebraic number theory, the integers are sometimes qualified as rational integers to distinguish them from the more general algebraic in ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Storage Record
In computer science{{citation needed, date=July 2016, a storage record is: * A group of related data, words, or fields treated as a meaningful unit; for instance, a Name, Address, and Telephone Number can be a "Personal Record". * A self-contained collection of information about a single object; a record is made up of a number of distinct items, called fields. * In IBM mainframes, a ''record'' is a basic unit of device-to-program data transfers. Mainframe files, properly called data sets, are traditionally structured collections of records, as opposed to modern byte stream access files. Records may have a fixed length or variable length. In Unix-like systems, a number of programs (for example, awk, join, and sort) are designed to process data consisting of records (called lines) each separated by newlines, where each record may contain a number of fields separated by spaces, commas, or some other character. See also * Block (data storage) * Object composition * Record (compu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hash Table
In computing, a hash table, also known as hash map, is a data structure that implements an associative array or dictionary. It is an abstract data type that maps keys to values. A hash table uses a hash function to compute an ''index'', also called a ''hash code'', into an array of ''buckets'' or ''slots'', from which the desired value can be found. During lookup, the key is hashed and the resulting hash indicates where the corresponding value is stored. Ideally, the hash function will assign each key to a unique bucket, but most hash table designs employ an imperfect hash function, which might cause hash '' collisions'' where the hash function generates the same index for more than one key. Such collisions are typically accommodated in some way. In a well-dimensioned hash table, the average time complexity for each lookup is independent of the number of elements stored in the table. Many hash table designs also allow arbitrary insertions and deletions of key–value pa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Daniel J
Daniel is a masculine given name and a surname of Hebrew origin. It means "God is my judge"Hanks, Hardcastle and Hodges, ''Oxford Dictionary of First Names'', Oxford University Press, 2nd edition, , p. 68. (cf. Gabriel—"God is my strength"), and derives from two early biblical figures, primary among them Daniel from the Book of Daniel. It is a common given name for males, and is also used as a surname. It is also the basis for various derived given names and surnames. Background The name evolved into over 100 different spellings in countries around the world. Nicknames ( Dan, Danny) are common in both English and Hebrew; "Dan" may also be a complete given name rather than a nickname. The name "Daniil" (Даниил) is common in Russia. Feminine versions ( Danielle, Danièle, Daniela, Daniella, Dani, Danitza) are prevalent as well. It has been particularly well-used in Ireland. The Dutch names "Daan" and "Daniël" are also variations of Daniel. A related surname d ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |