|
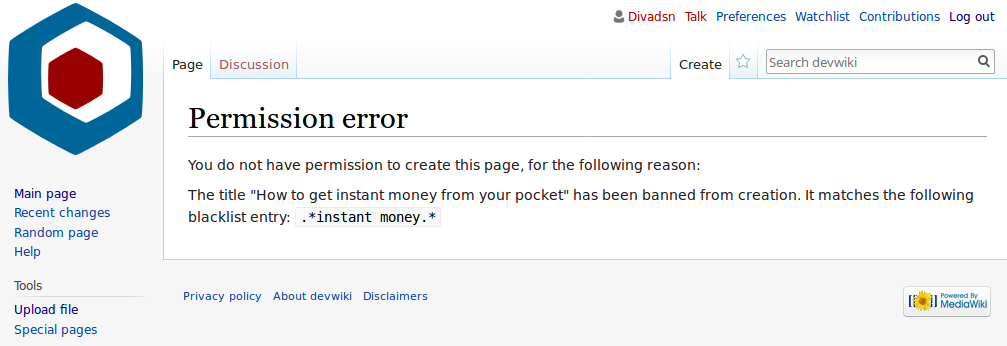
Blacklist (computing)
In computing, a blacklist, disallowlist, blocklist, or denylist is a basic access control mechanism that allows through all elements (email addresses, users, passwords, URLs, IP addresses, domain names, file hashes, etc.), except those explicitly mentioned. Those items on the list are denied access. The opposite is a whitelist, allowlist, or passlist, in which only items on the list are let through whatever gate is being used. A greylist contains items that are temporarily blocked (or temporarily allowed) until an additional step is performed. Blacklists can be applied at various points in a security architecture, such as a host, web proxy, DNS servers, email server, firewall, directory servers or application authentication gateways. The type of element blocked is influenced by the access control location. DNS servers may be well-suited to block domain names, for example, but not URLs. A firewall is well-suited for blocking IP addresses, but less so for blocking malicious fi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mail Filter
Email filtering is the processing of email to organize it according to specified criteria. The term can apply to the intervention of human intelligence, but most often refers to the automatic processing of messages at an SMTP server, possibly applying anti-spam techniques. Filtering can be applied to incoming emails as well as to outgoing ones. Depending on the calling environment, email filtering software can reject an item at the initial SMTP connection stage or pass it through unchanged for delivery to the user's mailbox. It is also possible to redirect the message for delivery elsewhere, quarantine it for further checking, modify it or 'tag' it in any other way. Motivation Common uses for mail filters include organizing incoming email and removal of spam and computer viruses. Mailbox providers filter outgoing email to promptly react to spam surges that may result from compromised accounts. A less common use is to inspect outgoing email at some companies to ensure that emplo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Content-control Software
An Internet filter is software that restricts or controls the content an Internet user is capable to access, especially when utilized to restrict material delivered over the Internet via the Web, Email, or other means. Content-control software determines what content will be available or be blocked. Such restrictions can be applied at various levels: a government can attempt to apply them nationwide (see Internet censorship), or they can, for example, be applied by an Internet service provider to its clients, by an employer to its personnel, by a school to its students, by a library to its visitors, by a parent to a child's computer, or by an individual users to their own computers. The motive is often to prevent access to content which the computer's owner(s) or other authorities may consider objectionable. When imposed without the consent of the user, content control can be characterised as a form of internet censorship. Some content-control software includes time control func ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Sucuri
GoDaddy Inc. is an American publicly traded Internet Domain name registrar, domain registrar and web hosting company headquartered in Tempe, Arizona, and incorporated in Delaware. , GoDaddy has more than 21 million customers and over 6,600 employees worldwide. The company is known for its advertising on TV and in the newspapers. It has been involved in several controversies related to unethical business practices and censorship. History GoDaddy was founded in 1997 in Phoenix, Arizona, by entrepreneur Bob Parsons. Prior to founding GoDaddy, Parsons had sold his financial software services company Parsons Technology to Intuit for $65 million in 1994. He came out of his retirement in 1997 to launch Jomax Technologies (named after a road in Phoenix Arizona) which became GoDaddy Group Inc. GoDaddy received a strategic investment, in 2011, from private equity funds, KKR, Silver Lake (investment firm), Silver Lake, and Technology Crossover Ventures. The company headquarters was locat ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
NortonLifeLock
Gen Digital Inc. (formerly Symantec Corporation and NortonLifeLock) is a multinational software company co-headquartered in Tempe, Arizona and Prague, Czech Republic. The company provides cybersecurity software and services. Gen is a Fortune 500 company and a member of the S&P 500 stock-market index. The company also has development centers in Pune, Chennai and Bangalore. Its portfolio includes Norton, Avast, LifeLock, Avira, AVG, ReputationDefender, and CCleaner. On October 9, 2014, Symantec declared it would split into two independent publicly traded companies by the end of 2015. One company would focus on security, the other on information management. On January 29, 2016, Symantec sold its information-management subsidiary, named Veritas Technologies, and which Symantec had acquired in 2004, to The Carlyle Group. On August 9, 2019, Broadcom Inc. announced they would be acquiring the Enterprise Security software division of Symantec for $10.7 billion, and the company became ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Google
Google LLC () is an American Multinational corporation, multinational technology company focusing on Search Engine, search engine technology, online advertising, cloud computing, software, computer software, quantum computing, e-commerce, artificial intelligence, and Computer hardware, consumer electronics. It has been referred to as "the most powerful company in the world" and one of the world's List of most valuable brands, most valuable brands due to its market dominance, data collection, and technological advantages in the area of artificial intelligence. Its parent company Alphabet Inc., Alphabet is considered one of the Big Tech, Big Five American information technology companies, alongside Amazon (company), Amazon, Apple Inc., Apple, Meta Platforms, Meta, and Microsoft. Google was founded on September 4, 1998, by Larry Page and Sergey Brin while they were Doctor of Philosophy, PhD students at Stanford University in California. Together they own about 14% of its publicl ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Comparison Of DNS Blacklists
__NOTOC__ The following table lists technical information for assumed reputable DNS blacklists used for blocking spam. Notes "Collateral listings"—Deliberately listing non-offending IP addresses, in order to coerce ISPs to take action against spammers under their control. "Notifies upon listing"—Warns registrants of listed IP addresses or domains (so registrants can take actions to fix problems). Suspect RBL providers Suspect RBL providers are those who employ well-documented patterns of questionable or reckless practices or have questionable actors based on statements or communications from the RBL's principal management to official forums. These practices usually include acceptance of de-listing payments (also known as ransom payments) - which incentivizes fraud - such as is the case with UCEPROTECT/Whitelisted.org. Often, these RBL providers use circular rhetoric such as "only spammers would claim we are illegitimate" in furtherance of their scheme. These RBL providers ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
RESTful API Modeling Language
RESTful API Modeling Language (RAML) is a YAML-based language for describing static APIs (but not REST APIs). It provides all the information necessary to describe APIs on the level 2 of the Richardson Maturity Model. Although designed with RESTful APIs in mind, RAML is not capable of describing APIs that not obey all constraints of REST. It encourages reuse, enables discovery and pattern-sharing and aims for merit-based emergence of best practices. History RAML was first proposed in 2013. The initial RAML specification was authored by Uri Sarid, Emiliano Lesende, Santiago Vacas and Damian Martinez, and garnered support from technology leaders like MuleSoft, AngularJS, Intuit, Box, PayPal, Programmable Web and API Web Science, Kin Lane, SOA Software, and Cisco. Development is managed by the RAML Workgroup. The current workgroup signatories include technology leaders from MuleSoft (Uri Sarid, CTO), AngularJS (Misko Hevery, Project Founder), Intuit (Ivan Lazarov, Chief Enterpri ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hypertext Transfer Protocol
The Hypertext Transfer Protocol (HTTP) is an application layer protocol in the Internet protocol suite model for distributed, collaborative, hypermedia information systems. HTTP is the foundation of data communication for the World Wide Web, where hypertext documents include hyperlinks to other resources that the user can easily access, for example by a mouse click or by tapping the screen in a web browser. Development of HTTP was initiated by Tim Berners-Lee at CERN in 1989 and summarized in a simple document describing the behavior of a client and a server using the first HTTP protocol version that was named 0.9. That first version of HTTP protocol soon evolved into a more elaborated version that was the first draft toward a far future version 1.0. Development of early HTTP Requests for Comments (RFCs) started a few years later and it was a coordinated effort by the Internet Engineering Task Force (IETF) and the World Wide Web Consortium (W3C), with work later movi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Rsync
rsync is a utility for efficiently transferring and synchronizing files between a computer and a storage drive and across networked computers by comparing the modification times and sizes of files. It is commonly found on Unix-like operating systems and is under the GPL-3.0-or-later license. Rsync is written in C as a single threaded application. The rsync algorithm is a type of delta encoding, and is used for minimizing network usage. Zlib may be used for additional data compression, and SSH or stunnel can be used for security. Rsync is typically used for synchronizing files and directories between two different systems. For example, if the command rsync local-file user@remote-host:remote-file is run, rsync will use SSH to connect as user to remote-host. Once connected, it will invoke the remote host's rsync and then the two programs will determine what parts of the local file need to be transferred so that the remote file matches the local one. One application of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Domain Name System
The Domain Name System (DNS) is a hierarchical and distributed naming system for computers, services, and other resources in the Internet or other Internet Protocol (IP) networks. It associates various information with domain names assigned to each of the associated entities. Most prominently, it translates readily memorized domain names to the numerical IP addresses needed for locating and identifying computer services and devices with the underlying network protocols. The Domain Name System has been an essential component of the functionality of the Internet since 1985. The Domain Name System delegates the responsibility of assigning domain names and mapping those names to Internet resources by designating authoritative name servers for each domain. Network administrators may delegate authority over sub-domains of their allocated name space to other name servers. This mechanism provides distributed and fault-tolerant service and was designed to avoid a single large central ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
DNSBL
A Domain Name System blocklist, Domain Name System-based blackhole list, Domain Name System blacklist (DNSBL) or real-time blackhole list (RBL) is a service for operation of mail servers to perform a check via a Domain Name System (DNS) query whether a sending host's IP address is blacklisted for email spam. Most mail server software can be configured to check such lists, typically rejecting or flagging messages from such sites. A DNSBL is a software mechanism, rather than a specific list or policy. Dozens of DNSBLs exist. They use a wide array of criteria for listing and delisting addresses. These may include listing the addresses of zombie computers or other machines being used to send spam, Internet service providers (ISPs) who willingly host spammers, or those which have sent spam to a honeypot system. Since the creation of the first DNSBL in 1998, the operation and policies of these lists have frequently been controversial, both in Internet advocacy circles and occasionally ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |