|
Biba Model
The Biba Model or Biba Integrity Model developed by Kenneth J. Biba in 1975, is a formal state transition system of computer security policy that describes a set of access control rules designed to ensure data integrity. Data and subjects are grouped into ordered levels of integrity. The model is designed so that subjects may not corrupt data in a level ranked higher than the subject, or be corrupted by data from a lower level than the subject. In general the model was developed to address integrity as the core principle, which is the direct inverse of the Bell–LaPadula model which focuses on confidentiality. Features In general, preservation of data ''integrity'' has three goals: * Prevent data modification by unauthorized parties * Prevent unauthorized data modification by authorized parties * Maintain internal and external consistency (i.e. data reflects the real world) This security model is directed toward data ''integrity'' (rather than ''confidentiality'') and is char ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Discretionary Access Control
In computer security, discretionary access control (DAC) is a type of access control defined by the Trusted Computer System Evaluation Criteria (TCSEC) as a means of restricting access to objects based on the identity of subjects and/or groups to which they belong. The controls are discretionary in the sense that a subject with a certain access permission is capable of passing that permission (perhaps indirectly) on to any other subject (unless restrained by mandatory access control). Discretionary access control is commonly discussed in contrast to mandatory access control (MAC). Occasionally, a system as a whole is said to have "discretionary" or "purely discretionary" access control when that system lacks mandatory access control. On the other hand, systems can implement both MAC and DAC simultaneously, where DAC refers to one category of access controls that subjects can transfer among each other, and MAC refers to a second category of access controls that imposes constrain ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Take-grant Protection Model
The take-grant protection model is a formal model used in the field of computer security to establish or disprove the safety of a given computer system that follows specific rules. It shows that even though the question of safety is in general undecidable, for specific systems it is decidable in linear time. The model represents a system as directed graph In mathematics, and more specifically in graph theory, a directed graph (or digraph) is a graph that is made up of a set of vertices connected by directed edges, often called arcs. Definition In formal terms, a directed graph is an ordered pa ..., where vertices are either subjects or objects. The edges between them are labeled and the label indicates the rights that the source of the edge has over the destination. Two rights occur in every instance of the model: ''take'' and ''grant''. They play a special role in the graph rewriting rules describing admissible changes of the graph. There are a total of four such rules: * ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Security Modes
Generally, security modes refer to information systems security modes of operations used in mandatory access control (MAC) systems. Often, these systems contain information at various levels of security classification. The mode of operation is determined by: * The type of users who will be directly or indirectly accessing the system. * The type of data, including classification levels, compartments, and categories, that are processed on the system. * The type of levels of users, their need to know, and formal access approvals that the users will have. Dedicated security mode In this mode of operation, all users must have: * Signed NDA for ''ALL'' information on the system. * Proper clearance for ''ALL'' information on the system. * Formal access approval for ''ALL'' information on the system. * A valid need to know for ''ALL'' information on the system. All users can access ''ALL'' data. System high security mode In system high mode of operation, all users must have: * Signe ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
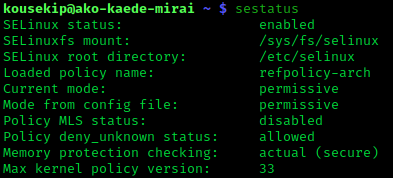
Security-Enhanced Linux
Security-Enhanced Linux (SELinux) is a Linux kernel security module that provides a mechanism for supporting access control security policies, including mandatory access controls (MAC). SELinux is a set of kernel modifications and user-space tools that have been added to various Linux distributions. Its architecture strives to separate enforcement of security decisions from the security policy, and streamlines the amount of software involved with security policy enforcement. The key concepts underlying SELinux can be traced to several earlier projects by the United States National Security Agency (NSA). Overview The NSA Security-enhanced Linux Team describes NSA SELinux as a set of patches to the Linux kernel and utilities to provide a strong, flexible, mandatory access control (MAC) architecture into the major subsystems of the kernel. It provides an enhanced mechanism to enforce the separation of information based on confidentiality and integrity requirements, which all ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Multilevel Security
Multilevel security or multiple levels of security (MLS) is the application of a computer system to process information with incompatible classifications (i.e., at different security levels), permit access by users with different security clearances and needs-to-know, and prevent users from obtaining access to information for which they lack authorization. There are two contexts for the use of multilevel security. One is to refer to a system that is adequate to protect itself from subversion and has robust mechanisms to separate information domains, that is, trustworthy. Another context is to refer to an application of a computer that will require the computer to be strong enough to protect itself from subversion and possess adequate mechanisms to separate information domains, that is, a system we must trust. This distinction is important because systems that need to be trusted are not necessarily trustworthy. Trusted operating systems An MLS operating environment often requ ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mandatory Access Control
In computer security, mandatory access control (MAC) refers to a type of access control by which the operating system or database constrains the ability of a ''subject'' or ''initiator'' to access or generally perform some sort of operation on an ''object'' or ''target''. In the case of operating systems, a subject is usually a process or thread; objects are constructs such as files, directories, TCP/ UDP ports, shared memory segments, IO devices, etc. Subjects and objects each have a set of security attributes. Whenever a subject attempts to access an object, an authorization rule enforced by the operating system kernel examines these security attributes and decides whether the access can take place. Any operation by any subject on any object is tested against the set of authorization rules (aka ''policy'') to determine if the operation is allowed. A database management system, in its access control mechanism, can also apply mandatory access control; in this case, the object ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Graham–Denning Model
The Graham–Denning model is a computer security model that shows how subjects and objects should be securely created and deleted. It also addresses how to assign specific access rights. It is mainly used in access control mechanisms for distributed systems. There are three main parts to the model: A set of subjects, a set of objects, and a set of eight rules. A subject may be a process or a user that makes a request to access a resource. An object is the resource that a user or process wants to access. Features This model addresses the security issues associated with how to define a set of basic rights on how specific subjects can execute security functions on an object. The model has eight basic protection rules (actions) that outline: * How to securely create an object. * How to securely create a subject. * How to securely delete an object. * How to securely delete a subject. * How to securely provide the read access right. * How to securely provide the grant access r ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
XTS-400
The XTS-400 is a multilevel secure computer operating system. It is multiuser and multitasking that uses multilevel scheduling in processing data and information. It works in networked environments and supports Gigabit Ethernet and both IPv4 and IPv6. The XTS-400 is a combination of Intel x86 hardware and the Secure Trusted Operating Program (STOP) operating system. XTS-400 was developed by BAE Systems, and originally released as version 6.0 in December 2003. STOP provides ''high-assurance'' security and was the first general-purpose operating system with a Common Criteria assurance level rating of EAL5 or above. The XTS-400 can host, and be trusted to separate, multiple, concurrent data sets, users, and networks at different sensitivity levels. The XTS-400 provides both an ''untrusted'' environment for normal work and a trusted environment for administrative work and for privileged applications. The untrusted environment is similar to traditional Unix environments. It pro ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
State Transition System
In theoretical computer science, a transition system is a concept used in the study of computation. It is used to describe the potential behavior of discrete systems. It consists of states and transitions between states, which may be labeled with labels chosen from a set; the same label may appear on more than one transition. If the label set is a singleton, the system is essentially unlabeled, and a simpler definition that omits the labels is possible. Transition systems coincide mathematically with abstract rewriting systems (as explained further in this article) and directed graphs. They differ from finite-state automata in several ways: * The set of states is not necessarily finite, or even countable. * The set of transitions is not necessarily finite, or even countable. * No "start" state or "final" states are given. Transition systems can be represented as directed graphs. Formal definition Formally, a transition system is a pair (S, \rightarrow) where S is a set of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Linux
Linux ( or ) is a family of open-source Unix-like operating systems based on the Linux kernel, an operating system kernel first released on September 17, 1991, by Linus Torvalds. Linux is typically packaged as a Linux distribution, which includes the kernel and supporting system software and libraries, many of which are provided by the GNU Project. Many Linux distributions use the word "Linux" in their name, but the Free Software Foundation uses the name "GNU/Linux" to emphasize the importance of GNU software, causing some controversy. Popular Linux distributions include Debian, Fedora Linux, and Ubuntu, the latter of which itself consists of many different distributions and modifications, including Lubuntu and Xubuntu. Commercial distributions include Red Hat Enterprise Linux and SUSE Linux Enterprise. Desktop Linux distributions include a windowing system such as X11 or Wayland, and a desktop environment such as GNOME or KDE Plasma. Distributions inten ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
FreeBSD
FreeBSD is a free and open-source Unix-like operating system descended from the Berkeley Software Distribution (BSD), which was based on Research Unix. The first version of FreeBSD was released in 1993. In 2005, FreeBSD was the most popular open-source BSD operating system, accounting for more than three-quarters of all installed and permissively licensed BSD systems. FreeBSD has similarities with Linux, with two major differences in scope and licensing: FreeBSD maintains a complete system, i.e. the project delivers a kernel, device drivers, userland utilities, and documentation, as opposed to Linux only delivering a kernel and drivers, and relying on third-parties for system software; FreeBSD source code is generally released under a permissive BSD license, as opposed to the copyleft GPL used by Linux. The FreeBSD project includes a security team overseeing all software shipped in the base distribution. A wide range of additional third-party applications may be i ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
.jpg)
