|
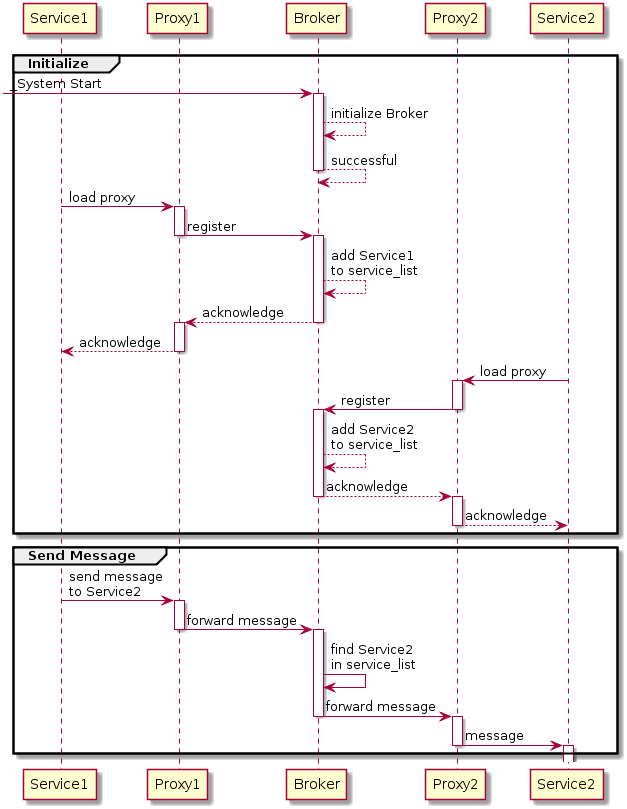
Broker Injection
Broker injection attack is a type of vulnerability that exploits misconfigured brokers, potentially allowing an attacker to read, write and inject information from/into their flow. Description There are many scenarios in which a broker is used to transport the information between tasks. One of the most typical use cases is send e-mails in background. In this scenario we'll have two actors: * An information producer (a website, for example). * A worker or background process who actually sends the e-mail. The producer needs an asynchronous and non-blocking way to send the email information to the worker. This system is usually a broker. It takes the information from the web front-end and passes it to the worker, generating a new task in the worker. So, the worker has all the information to send the e-mail. Taking the above scenario as an example, if we could access the broker, we would be able to make the worker generate new tasks with arbitrary data, unleashing a broker injec ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Vulnerability (computing)
Vulnerabilities are flaws or weaknesses in a system's design, implementation, or management that can be exploited by a malicious actor to compromise its security. Despite a system administrator's best efforts to achieve complete correctness, virtually all hardware and software contain bugs where the system does not behave as expected. If the bug could enable an attacker to compromise the confidentiality, integrity, or availability of system resources, it can be considered a vulnerability. Insecure software development practices as well as design factors such as complexity can increase the burden of vulnerabilities. Vulnerability management is a process that includes identifying systems and prioritizing which are most important, scanning for vulnerabilities, and taking action to secure the system. Vulnerability management typically is a combination of remediation, mitigation, and acceptance. Vulnerabilities can be scored for severity according to the Common Vulnerability S ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Spain
Spain, or the Kingdom of Spain, is a country in Southern Europe, Southern and Western Europe with territories in North Africa. Featuring the Punta de Tarifa, southernmost point of continental Europe, it is the largest country in Southern Europe and the fourth-most populous European Union member state. Spanning across the majority of the Iberian Peninsula, its territory also includes the Canary Islands, in the Eastern Atlantic Ocean, the Balearic Islands, in the Western Mediterranean Sea, and the Autonomous communities of Spain#Autonomous cities, autonomous cities of Ceuta and Melilla, in mainland Africa. Peninsular Spain is bordered to the north by France, Andorra, and the Bay of Biscay; to the east and south by the Mediterranean Sea and Gibraltar; and to the west by Portugal and the Atlantic Ocean. Spain's capital and List of largest cities in Spain, largest city is Madrid, and other major List of metropolitan areas in Spain, urban areas include Barcelona, Valencia, Seville, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Redis
Redis (; Remote Dictionary Server) is an in-memory key–value database, used as a distributed cache and message broker, with optional durability. Because it holds all data in memory and because of its design, Redis offers low- latency reads and writes, making it particularly suitable for use cases that require a cache. Redis is the most popular NoSQL database, and one of the most popular databases overall. The project was developed and maintained by Salvatore Sanfilippo, starting in 2009. From 2015 until 2020, he led a project core team sponsored by Redis Ltd. Salvatore Sanfilippo left Redis as the maintainer in 2020. In 2021 Redis Labs dropped the Labs from its name and now is known simply as "Redis". In 2018, some modules for Redis adopted a modified Apache 2.0 with a Commons Clause. In 2024, the main Redis code switched from the open-source BSD-3 license to being dual-licensed under the Redis Source Available License v2 and the Server Side Public License v1. On May ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
RabbitMQ
RabbitMQ is an open-source message-broker software (sometimes called message-oriented middleware) that originally implemented the Advanced Message Queuing Protocol (AMQP) and has since been extended with a plug-in architecture to support Streaming Text Oriented Messaging Protocol (STOMP), MQ Telemetry Transport (MQTT), and other protocols. Written in Erlang, the RabbitMQ server is built on the Open Telecom Platform framework for clustering and failover. Client libraries to interface with the broker are available for all major programming languages. The source code is released under the Mozilla Public License. Since November 2020, there are commercial offerings available of RabbitMQ, for support and enterprise features: "VMware RabbitMQ OVA", "VMware RabbitMQ" and "VMware RabbitMQ for Kubernetes" (different feature levels) Open-Source RabbitMQ is also packaged by Bitnami and commercially for VMware's Tanzu Application Service. History Originally developed by Rabbit Tec ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
ZeroMQ
ZeroMQ (also spelled ØMQ, 0MQ or ZMQ) is an asynchronous messaging library, aimed at use in distributed or concurrent applications. It provides a message queue, but unlike message-oriented middleware, a ZeroMQ system can run without a dedicated message broker; the zero in the name is for "zero broker". The library's API is designed to resemble Berkeley sockets. ZeroMQ is developed by a large community of contributors, founded by iMatix, which holds the domain name and trademarks. There are third-party bindings for many popular programming languages. Technology The ZeroMQ API provides ''sockets'' (a kind of generalization over the traditional IP and Unix domain sockets), each of which can represent a many-to-many connection between endpoints. Operating with a message-wise granularity, they require that a messaging pattern be used, and are particularly optimized for that kind of pattern. The basic ZeroMQ patterns are: ; Request–reply :Connects a set of clients to a set of se ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Message Broker
A message broker (also known as an integration broker or interface engine) is an intermediary computer program module that translates a message from the formal messaging protocol of the sender to the formal messaging protocol of the receiver. Message brokers are elements in telecommunication or computer networks where software applications communicate by exchanging formally-defined messages. Message brokers are a building block of message-oriented middleware (MOM) but are typically not a replacement for traditional middleware like MOM and remote procedure call (RPC). Overview A message broker is an architectural pattern for message validation, transformation, and routing. It mediates communication among applications, minimizing the mutual awareness that applications should have of each other in order to be able to exchange messages, effectively implementing decoupling. Purpose The primary purpose of a broker is to take incoming messages from applications and perform some acti ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Celery (software)
Celery is an open source asynchronous task queue or job queue which is based on distributed message passing. While it supports scheduling, its focus is on operations in real time. Overview The execution units, called ''tasks'', are executed concurrently on one or more worker nodes using multiprocessing, or . Tasks can execute asynchronously (in the background) or synchronously (wait until ready). Celery is used in production systems, for services such as Instagram, to process millions of tasks every day. Technology Celery is written in Python, but the protocol can be implemented in any language. It can also operate with other languages using webhooks. There is also a Ruby-Client called RCelery, a PHP client, a Go client, a Rust client, and a Node.js client. Celery requires a message broker to run. As of October 2024, Redis and RabbitMQ are supported and actively maintained and monitored. Amazon SQS is supported and maintained but does not support worker inspection and mana ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hacking (computer Security)
Hacking may refer to: Places * Hacking, an area within Hietzing, Vienna, Austria People * David Hacking, 3rd Baron Hacking (born 1938), British barrister and peer * Douglas Hewitt Hacking, 1st Baron Hacking (1884–1950), British Conservative politician * Ian Hacking (1936–2023), Canadian philosopher of science * Philip Hacking (1931–2024), English Anglican priest, and itinerant evangelical speaker Sports * Hacking (falconry), the practice of raising falcons in captivity then later releasing into the wild * Hacking (rugby), tripping an opposing player * Pleasure riding, horseback riding for purely recreational purposes, also called hacking * Shin-kicking, an English martial art also called hacking Technology * Hacker, a computer expert with advanced technical knowledge ** Hacker culture, activity within the computer programmer subculture * Security hacker, someone who breaches defenses in a computer system ** Cybercrime, which involves security hacking * Phone hacki ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Machine Code
In computer programming, machine code is computer code consisting of machine language instructions, which are used to control a computer's central processing unit (CPU). For conventional binary computers, machine code is the binaryOn nonbinary machines it is, e.g., a decimal representation. representation of a computer program that is actually read and interpreted by the computer. A program in machine code consists of a sequence of machine instructions (possibly interspersed with data). Each machine code instruction causes the CPU to perform a specific task. Examples of such tasks include: # Load a word from memory to a CPU register # Execute an arithmetic logic unit (ALU) operation on one or more registers or memory locations # Jump or skip to an instruction that is not the next one In general, each architecture family (e.g., x86, ARM) has its own instruction set architecture (ISA), and hence its own specific machine code language. There are exceptions, such as the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Injection Exploits
Injection or injected may refer to: Science and technology * Injective function, a mathematical function mapping distinct arguments to distinct values * Injection (medicine), insertion of liquid into the body with a syringe * Injection, in broadcasting, the level at which a subcarrier is sent by the transmitter, expressed as a percent of total modulation * Injection quill, used in the petrochemical industry to insert chemicals, typically inhibitors, for proper mixture within a base chemical * Fuel injection, a means of metering fuel into an internal combustion engine * Orbit injection, changing a stable orbit into a transfer orbit * Injection, in construction, insertion of consolidation materials (i.e., cement grout mixtures, gravel) by means of dry type rotary shortcrete high pressure pumps * Injection well * Injection moulding, a technique for making parts from plastic material Computing * Code injection, a security violation technique using unexpected program modification * De ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |