|
802.22
IEEE 802.22, is a International standard, standard for wireless regional area network (WRAN) using White space (telecommunications), white spaces in the television (TV) frequency spectrum. The development of the IEEE 802.22 WRAN standard is aimed at using cognitive radio (CR) techniques to allow sharing of geographically unused spectrum allocated to the television broadcast service, on a non-interfering basis, to bring broadband access to hard-to-reach, low population density areas, typical of rural environments, and is therefore timely and has the potential for a wide applicability worldwide. It is the first worldwide effort to define a standardized air interface based on CR techniques for the opportunistic use of TV bands on a non-interfering basis. IEEE 802.22 WRANs are designed to operate in the TV broadcast bands while assuring that no harmful interference is caused to the incumbent operation: digital TV and analog TV broadcasting, and low power licensed devices such as wireless ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cognitive Radio
A cognitive radio (CR) is a radio that can be programmed and configured dynamically to use the best channels in its vicinity to avoid user interference and congestion. Such a radio automatically detects available channels, then accordingly changes its transmission or reception parameters to allow more concurrent wireless communications in a given band at one location. This process is a form of dynamic spectrum management. Description In response to the operator's commands, the cognitive engine is capable of configuring radio-system parameters. These parameters include " waveform, protocol, operating frequency, and networking". This functions as an autonomous unit in the communications environment, exchanging information about the environment with the networks it accesses and other cognitive radios (CRs). A CR "monitors its own performance continuously", in addition to "reading the radio's outputs"; it then uses this information to "determine the RF environment, channel condit ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
White Space (telecommunications)
In telecommunications, white spaces refer to frequency, radio frequencies allocated to a broadcasting service but not used locally. National and international bodies assign frequencies for specific uses and, in most cases, license the rights to broadcast over these frequencies. This frequency allocation process creates a bandplan which for technical reasons assigns white space between used radio bands or Channel (broadcasting), channels to avoid Interference (communication), interference. In this case, while the frequencies are unused, they have been specifically assigned for a purpose, such as a guard band. Most commonly however, these white spaces exist naturally between used channels, since assigning nearby transmissions to immediately adjacent channels will cause destructive interference to both. In addition to white space assigned for technical reasons, there is also unused radio spectrum which has either never been used, or is becoming free as a result of technical changes. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Dynamic Frequency Hopping
One of the key challenges of the cognitive radio based wireless networks, such as IEEE 802.22 wireless regional area networks (WRAN), is to address two apparently conflicting requirements: assuring Quality of Services (QoS) satisfaction for services provided by the cognitive radio networks, while providing reliable spectrum sensing for guaranteeing licensed user protection. To perform reliable sensing, in the basic operation mode on a single frequency band (the so-called "listenbefore-talk" mode) one has to allocate Quiet Times, in which no data transmission is permitted. Such periodic interruption of data transmission could impair the QoS of cognitive radio systems. This issue is addressed by an alternative operation mode proposed in IEEE 802.22 called Dynamic Frequency Hopping Frequency-hopping spread spectrum (FHSS) is a method of transmitting radio signals by rapidly changing the carrier frequency among many frequencies occupying a large spectral band. The changes are co ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
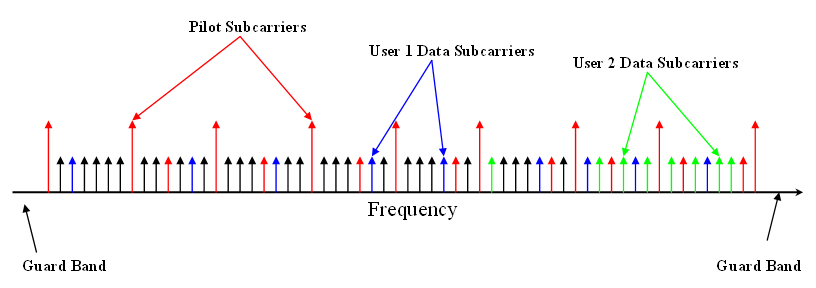
OFDMA
Orthogonal frequency-division multiple access (OFDMA) is a multi-user version of the popular orthogonal frequency-division multiplexing (OFDM) digital modulation scheme. Multiple access is achieved in OFDMA by assigning subsets of subcarriers to individual users. This allows simultaneous low-data-rate transmission from several users. Comparisons OFDMA is often compared to the combination of OFDM with statistical time-division multiplexing. The advantages and disadvantages summarized below are further discussed in the Characteristics and principles of operation section. See also the list of OFDM key features. Advantages * Allows simultaneous low-data-rate transmission from several users. * Pulsed carrier can be avoided. * Lower maximal transmission power for low-data-rate users * Shorter delay and constant delay * Contention-based multiple access (collision avoidance) is simplified. * Further improves OFDM robustness to fading and interference * Combat narrow-band interfe ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
EAP-TTLS
Extensible Authentication Protocol (EAP) is an authentication framework frequently used in network and internet connections. It is defined in , which made obsolete, and is updated by . EAP is an authentication framework for providing the transport and usage of material and parameters generated by EAP methods. There are many methods defined by RFCs, and a number of vendor-specific methods and new proposals exist. EAP is not a wire protocol; instead it only defines the information from the interface and the formats. Each protocol that uses EAP defines a way to encapsulate by the user EAP messages within that protocol's messages. EAP is in wide use. For example, in IEEE 802.11 (Wi-Fi) the WPA and WPA2 standards have adopted IEEE 802.1X (with various EAP types) as the canonical authentication mechanism. Methods EAP is an authentication framework, not a specific authentication mechanism. It provides some common functions and negotiation of authentication methods called EAP methods. The ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Advanced Encryption Standard
The Advanced Encryption Standard (AES), also known by its original name Rijndael (), is a specification for the encryption of electronic data established by the U.S. National Institute of Standards and Technology (NIST) in 2001. AES is a variant of the Rijndael block cipher developed by two Belgium, Belgian cryptographers, Joan Daemen and Vincent Rijmen, who submitted a proposal to NIST during the Advanced Encryption Standard process, AES selection process. Rijndael is a family of ciphers with different key size, key and Block size (cryptography), block sizes. For AES, NIST selected three members of the Rijndael family, each with a block size of 128 bits, but three different key lengths: 128, 192 and 256 bits. AES has been adopted by the Federal government of the United States, U.S. government. It supersedes the Data Encryption Standard (DES), which was published in 1977. The algorithm described by AES is a symmetric-key algorithm, meaning the same key is used for both encrypting ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Galois/Counter Mode
In cryptography, Galois/Counter Mode (GCM) is a mode of operation for symmetric-key cryptographic block ciphers which is widely adopted for its performance. GCM throughput rates for state-of-the-art, high-speed communication channels can be achieved with inexpensive hardware resources. The GCM algorithm provides both data authenticity (integrity) and confidentiality and belongs to the class of authenticated encryption with associated data (AEAD) methods. This means that as input it takes a key K, some plaintext P, and some associated data AD; it then encrypts the plaintext using the key to produce ciphertext C, and computes an authentication tag T from the ciphertext and the associated data (which remains unencrypted). A recipient with knowledge of K, upon reception of AD, C and T, can decrypt the ciphertext to recover the plaintext P and can check the tag T to ensure that neither ciphertext nor associated data were tampered with. GCM uses a block cipher with block size 128 bi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Authenticated Encryption
Authenticated Encryption (AE) is an encryption scheme which simultaneously assures the data confidentiality (also known as privacy: the encrypted message is impossible to understand without the knowledge of a secret key) and authenticity (in other words, it is unforgeable: the encrypted message includes an authentication tag that the sender can calculate only while possessing the secret key). Examples of encryption modes that provide AE are GCM, CCM. Many (but not all) AE schemes allow the message to contain "associated data" (AD) which is not made confidential, but its integrity is protected (i.e., it is readable, but tampering with it will be detected). A typical example is the header of a network packet that contains its destination address. To properly route the packet, all intermediate nodes in the message path need to know the destination, but for security reasons they cannot possess the secret key. Schemes that allow associated data provide authenticated encryption wi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
EAP-TLS
Extensible Authentication Protocol (EAP) is an authentication framework frequently used in network and internet connections. It is defined in , which made obsolete, and is updated by . EAP is an authentication framework for providing the transport and usage of material and parameters generated by EAP methods. There are many methods defined by RFCs, and a number of vendor-specific methods and new proposals exist. EAP is not a wire protocol; instead it only defines the information from the interface and the formats. Each protocol that uses EAP defines a way to encapsulate by the user EAP messages within that protocol's messages. EAP is in wide use. For example, in IEEE 802.11 (Wi-Fi) the WPA and WPA2 standards have adopted IEEE 802.1X (with various EAP types) as the canonical authentication mechanism. Methods EAP is an authentication framework, not a specific authentication mechanism. It provides some common functions and negotiation of authentication methods called EAP methods. T ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
International Standard
An international standard is a technical standard developed by one or more international standards organizations. International standards are available for consideration and use worldwide. The most prominent such organization is the International Organization for Standardization (ISO). Other prominent international standards organizations including the International Telecommunication Union (ITU) and the International Electrotechnical Commission (IEC). Together, these three organizations have formed the World Standards Cooperation alliance. Purpose International standards can be applied directly or adapted to meet local conditions. When adopted, they lead to the creation of national standards that are either equivalent to or largely align with the international standards in technical content, though they may have: (i) editorial variations, such as differences in appearance, the use of symbols, measurement units, or the choice of a point over a comma as the decimal marker, and (ii) va ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Authentication
Authentication (from ''authentikos'', "real, genuine", from αὐθέντης ''authentes'', "author") is the act of proving an Logical assertion, assertion, such as the Digital identity, identity of a computer system user. In contrast with identification, the act of indicating a person or thing's identity, authentication is the process of verifying that identity. Authentication is relevant to multiple fields. In art, antiques, and anthropology, a common problem is verifying that a given artifact was produced by a certain person, or in a certain place (i.e. to assert that it is not counterfeit), or in a given period of history (e.g. by determining the age via carbon dating). In computer science, verifying a user's identity is often required to allow access to confidential data or systems. It might involve validating personal identity documents. In art, antiques and anthropology Authentication can be considered to be of three types: The ''first'' type of authentication is accep ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
MAC Address
A MAC address (short for medium access control address or media access control address) is a unique identifier assigned to a network interface controller (NIC) for use as a network address in communications within a network segment. This use is common in most IEEE 802 networking technologies, including Ethernet, Wi-Fi, and Bluetooth. Within the Open Systems Interconnection (OSI) network model, MAC addresses are used in the medium access control protocol sublayer of the data link layer. As typically represented, MAC addresses are recognizable as six groups of two hexadecimal digits, separated by hyphens, colons, or without a separator. MAC addresses are primarily assigned by device manufacturers, and are therefore often referred to as the burned-in address, or as an Ethernet hardware address, hardware address, or physical address. Each address can be stored in the interface hardware, such as its read-only memory, or by a firmware mechanism. Many network interfaces, however, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |