Ultrapeer on:
[Wikipedia]
[Google]
[Amazon]
Gnutella is a
Rasti, Stutzbach, Rejaie, 2006. See Figure 2a. In late 2007, it was the most popular file-sharing network on the Internet with an estimated market share of more than 40%.
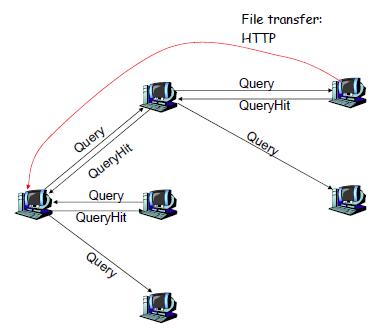 To envision how Gnutella originally worked, imagine a large circle of users ''(called nodes),'' each of whom has Gnutella client software. On initial startup, the client software must bootstrap and find at least one other node. Various methods have been used for this, including a pre-existing address list of possibly working nodes shipped with the software, using updated web caches of known nodes (called ''Gnutella Web Caches''), UDP host caches and, rarely, even
To envision how Gnutella originally worked, imagine a large circle of users ''(called nodes),'' each of whom has Gnutella client software. On initial startup, the client software must bootstrap and find at least one other node. Various methods have been used for this, including a pre-existing address list of possibly working nodes shipped with the software, using updated web caches of known nodes (called ''Gnutella Web Caches''), UDP host caches and, rarely, even
work-in-progress specifications
The Gnutella protocol remains under development. Despite attempts to make a clean break with the complexity inherited from the old Gnutella 0.4 and to design a clean new message architecture, it remains one of the most successful file-sharing protocols to date.
G2 Network Statistics
Population ~200,000 January 2010. It is difficult to compare the protocols in their current form. The choice of client, on either network, probably affects the end user just as much.
Gnutella Forums
Official user support boards
Gnutella Protocol Development Wiki
(on
Gnutella Protocol Development Portal
(on Internet Archive)
Gnutella official website
(on Internet Archive)
GnuFU
''Gnutella For Users: A description of the inner workings of the gnutella network in User-Friendly Style''
Glasnost
test Gnutella
peer-to-peer network
Peer-to-peer (P2P) computing or networking is a distributed application architecture that partitions tasks or workloads between peers. Peers are equally privileged, equipotent participants in the network. They are said to form a peer-to-peer ...
protocol. Founded in 2000, it was the first decentralized peer-to-peer network of its kind, leading to other, later networks adopting the model.
In June 2005, Gnutella's population was 1.81 million computers increasing to over three million nodes by January 2006.On the Long-term Evolution of the Two-Tier Gnutella OverlayRasti, Stutzbach, Rejaie, 2006. See Figure 2a. In late 2007, it was the most popular file-sharing network on the Internet with an estimated market share of more than 40%.
History
The first client (also called Gnutella) from which the network got its name was developed byJustin Frankel
Justin Frankel (born 1978) is an American computer programmer best known for his work on the Winamp media player application and for inventing the Gnutella peer-to-peer network. Frankel is also the founder of Cockos Incorporated, which creates ...
and Tom Pepper
Tom Pepper (born August 24, 1975 in Des Moines, Iowa) is a computer programmer best known for his collaboration with Justin Frankel on the Gnutella peer-to-peer system.Oram, Andrew ''Peer-to-peer: harnessing the benefits of a disruptive technolog ...
of Nullsoft
Nullsoft, Inc. was an American software house founded in Sedona, Arizona, in 1997 by Justin Frankel. Its products included the Winamp media player and the SHOUTcast MP3 streaming media server. In later years, their open source installer syst ...
in early 2000, soon after the company's acquisition by AOL
AOL (stylized as Aol., formerly a company known as AOL Inc. and originally known as America Online) is an American web portal and online service provider based in New York City. It is a brand marketed by the current incarnation of Yahoo! Inc. ...
. On March 14, the program was made available for download on Nullsoft's servers. The event was prematurely announced on Slashdot
''Slashdot'' (sometimes abbreviated as ''/.'') is a social news website that originally advertised itself as "News for Nerds. Stuff that Matters". It features news stories concerning science, technology, and politics that are submitted and evalu ...
, and thousands downloaded the program that day. The source code
In computing, source code, or simply code, is any collection of code, with or without comment (computer programming), comments, written using a human-readable programming language, usually as plain text. The source code of a Computer program, p ...
was to be released later, under the GNU General Public License
The GNU General Public License (GNU GPL or simply GPL) is a series of widely used free software licenses that guarantee end user
In product development, an end user (sometimes end-user) is a person who ultimately uses or is intended to ulti ...
(GPL); however, the original developers never got the chance to accomplish this purpose.
The next day, AOL stopped the availability of the program over legal concerns and restrained Nullsoft from doing any further work on the project. This did not stop Gnutella; after a few days, the protocol had been reverse engineered
Reverse engineering (also known as backwards engineering or back engineering) is a process or method through which one attempts to understand through deductive reasoning how a previously made device, process, system, or piece of software accompli ...
, and compatible free and open source
Free and open-source software (FOSS) is a term used to refer to groups of software consisting of both free software and open-source software where anyone is freely licensed to use, copy, study, and change the software in any way, and the source ...
clones began to appear. This parallel development of different clients by different groups remains the ''modus operandi
A ''modus operandi'' (often shortened to M.O.) is someone's habits of working, particularly in the context of business or criminal investigations, but also more generally. It is a Latin phrase, approximately translated as "mode (or manner) of o ...
'' of Gnutella development today.
Among the first independent Gnutella pioneers were Gene Kan Gene Kan (September 6, 1976 — June 29, 2002) was a British-born Chinese American peer-to-peer file-sharing programmer who was among the first programmers to produce an open-source version of the file-sharing application that implemented the Gn ...
and Spencer Kimball, who launched the first portal aimed to assemble the open-source community to work on Gnutella and also developed "GNUbile", one of the first open-source (GNU-GPL) programs to implement the Gnutella protocol.
The Gnutella network is a fully distributed alternative to such semi-centralized systems as FastTrack
FastTrack is a peer-to-peer (P2P) protocol that was used by the Kazaa, Grokster, iMesh and Morpheus file sharing programs. FastTrack was the most popular file sharing network in 2003, and used mainly for the exchange of music mp3 files. The netwo ...
( KaZaA) and the original Napster
Napster was a peer-to-peer file sharing application. It originally launched on June 1, 1999, with an emphasis on digital audio file distribution. Audio songs shared on the service were typically encoded in the MP3 format. It was founded by Sh ...
. The initial popularity of the network was spurred on by Napster's threatened legal demise in early 2001. This growing surge in popularity revealed the limits of the initial protocol's scalability. In early 2001, variations on the protocol (first implemented in proprietary and closed source
Proprietary software is software that is deemed within the free and open-source software to be non-free because its creator, publisher, or other rightsholder or rightsholder partner exercises a legal monopoly afforded by modern copyright and in ...
clients) allowed an improvement in scalability. Instead of treating every user as client and server, some users were now treated as ''ultrapeers'', routing search requests and responses for users connected to them.
This allowed the network to grow in popularity. In late 2001, the Gnutella client LimeWire
LimeWire was a free peer-to-peer file sharing client for Windows, MacOS, Linux and Solaris. Created by Mark Gorton in 2000, it was most prominently a tool used for the download and distribution of pirated materials, particularly pirated musi ...
Basic became free and open source. In February 2002, Morpheus
Morpheus ('Fashioner', derived from the grc, μορφή meaning 'form, shape') is a god associated with sleep and dreams. In Ovid's ''Metamorphoses'' he is the son of Somnus and appears in dreams in human form. From the Middle Ages, the name ...
, a commercial file sharing group, abandoned its FastTrack-based peer-to-peer software and released a new client based on the free and open source Gnutella client Gnucleus.
The word ''Gnutella'' today refers not to any one project or piece of software, but to the open protocol used by the various clients.
The name is a portmanteau
A portmanteau word, or portmanteau (, ) is a blend of wordsGNU
GNU () is an extensive collection of free software
Free software or libre software is computer software distributed under terms that allow users to run the software for any purpose as well as to study, change, and distribute it and any ...
'' and ''Nutella
Nutella (; ; ) is a brand of sweetened hazelnut cocoa spread. Nutella is manufactured by the Italian company Ferrero and was first introduced in 1964, although its first iteration dates to 1963.
History
Pietro Ferrero owned a bakery in Alba, ...
'', the brand name of an Italian hazelnut flavored spread: supposedly, Frankel and Pepper ate a lot of Nutella working on the original project, and intended to license their finished program under the GNU General Public License. Gnutella is not associated with the GNU
GNU () is an extensive collection of free software
Free software or libre software is computer software distributed under terms that allow users to run the software for any purpose as well as to study, change, and distribute it and any ...
project or GNU's own peer-to-peer network, GNUnet
GNUnet is a software framework for decentralized, peer-to-peer networking and an official GNU package. The framework offers link encryption, peer discovery, resource allocation, communication over many transports (such as TCP, UDP, HTTP, ...
.
On October 26, 2010, the popular Gnutella client
Client(s) or The Client may refer to:
* Client (business)
* Client (computing), hardware or software that accesses a remote service on another computer
* Customer or client, a recipient of goods or services in return for monetary or other valuabl ...
LimeWire
LimeWire was a free peer-to-peer file sharing client for Windows, MacOS, Linux and Solaris. Created by Mark Gorton in 2000, it was most prominently a tool used for the download and distribution of pirated materials, particularly pirated musi ...
was ordered shut down by Judge Kimba Wood
Kimba Maureen Wood (born January 21, 1944) is a Senior United States district judge of the United States District Court for the Southern District of New York. Wood has presided over many high-profile cases involving such figures as "Junk Bond Kin ...
of the United States District Court for the Southern District of New York
The United States District Court for the Southern District of New York (in case citations, S.D.N.Y.) is a federal trial court whose geographic jurisdiction encompasses eight counties of New York State. Two of these are in New York City: New ...
when she signed a Consent Decree to which recording industry plaintiffs and LimeWire had agreed. This event was the likely cause of a notable drop in the size of the network, because, while negotiating the injunction, LimeWire
LimeWire was a free peer-to-peer file sharing client for Windows, MacOS, Linux and Solaris. Created by Mark Gorton in 2000, it was most prominently a tool used for the download and distribution of pirated materials, particularly pirated musi ...
staff had inserted remote-disabling code into the software. As the injunction came into force, users who had installed affected versions (newer than 5.5.10) were cut off from the P2P network
Peer-to-peer (P2P) computing or networking is a distributed application architecture that partitions tasks or workloads between peers. Peers are equally privileged, equipotent participants in the network. They are said to form a peer-to-peer ...
. Since LimeWire was free software
Free software or libre software is computer software distributed under terms that allow users to run the software for any purpose as well as to study, change, and distribute it and any adapted versions. Free software is a matter of liberty, ...
, nothing had prevented the creation of forks
In cutlery or kitchenware, a fork (from la, furca 'pitchfork') is a utensil, now usually made of metal, whose long handle terminates in a head that branches into several narrow and often slightly curved tines with which one can spear foods eit ...
that omitted the disabling code, as long as LimeWire trademarks were not used. The shutdown did not affect, for example, FrostWire
FrostWire is a free and open-source BitTorrent client first released in September 2004, as a fork of LimeWire. It was initially very similar to LimeWire in appearance and functionality, but over time developers added more features, including supp ...
, a fork of LimeWire created in 2004 that carries neither the remote-disabling code nor adware
Adware, often called advertising-supported software by its developers, is software that generates revenue for its developer by automatically generating online advertisements in the user interface of the software or on a screen presented to the ...
.
On November 9, 2010, LimeWire was resurrected by a secret team of developers and named LimeWire Pirate Edition. It was based on LimeWire 5.6 BETA. This version had its server dependencies removed and all the PRO features enabled for free.
Design
IRC
Internet Relay Chat (IRC) is a text-based chat system for instant messaging. IRC is designed for Many-to-many, group communication in discussion forums, called ''#Channels, channels'', but also allows one-on-one communication via instant messa ...
. Once connected, the client requests a list of working addresses. The client tries to connect to the nodes it was shipped with, as well as nodes it receives from other clients until it reaches a certain quota. It connects to only that many nodes, locally caching the addresses which it has not yet tried and discarding the addresses which it tried and found to be invalid.
When the user wants to do a search, the client sends the request to each actively connected node. In version 0.4 of the protocol, the number of actively connected nodes for a client was quite small (around 5). In that version of the protocol, each node forwards the request to all its actively connected nodes, who, in turn, forward the request. This continues until the packet has reached a predetermined number of ''hops'' from the sender (maximum 7).
Since version 0.6 (2002), Gnutella is a composite network made of leaf nodes and ultra nodes (also called ultrapeers). The leaf nodes are connected to a small number of ultrapeers (typically 3) while each ultrapeer is connected to more than 32 other ultrapeers. With this higher outdegree
In mathematics, and more specifically in graph theory, a directed graph (or digraph) is a graph that is made up of a set of vertices connected by directed edges, often called arcs.
Definition
In formal terms, a directed graph is an ordered pai ...
, the maximum number of ''hops'' a query can travel was lowered to 4.
Leaves and ultrapeers use the Query Routing Protocol to exchange a Query Routing Table (QRT), a table of 64 Ki-slots and up to 2 Mi-slots consisting of hashed keywords. A leaf node sends its QRT to each of the ultrapeers to which it is connected, and ultrapeers merge the QRT of all their leaves (downsized to 128 Ki-slots) plus their own QRT (if they share files) and exchange that with their own neighbors. Query routing is then done by hashing the words of the query and seeing whether all of them match in the QRT. Ultrapeers do that check before forwarding a query to a leaf node, and also before forwarding the query to a peer ultra node provided this is the last hop the query can travel.
If a search request turns up a result, the node that has the result contacts the searcher. In the classic Gnutella protocol, response messages were sent back along the route taken by the query, as the query itself did not contain identifying information for the node. This scheme was later revised, to deliver search results over UDP, directly to the node that initiated the search, usually an ultrapeer of the node. Thus, in the current protocol, the queries carry the IP address
An Internet Protocol address (IP address) is a numerical label such as that is connected to a computer network that uses the Internet Protocol for communication.. Updated by . An IP address serves two main functions: network interface ident ...
and port number of either node. This lowers the amount of traffic routed through the Gnutella network, making it significantly more scalable.
If the user decides to download the file, they negotiate the file transfer File transfer is the transmission of a computer file through a communication channel from one computer system to another. Typically, file transfer is mediated by a communications protocol. In the history of computing, numerous file transfer protocol ...
. If the node which has the requested file is not firewalled, the querying node can connect to it directly. However, if the node is firewalled, stopping the source node from receiving incoming connections, the client wanting to download a file sends it a so-called ''push request'' to the server for the remote client to initiate the connection instead (to ''push'' the file). At first, these push requests were routed along the original chain it used to send the query. This was rather unreliable because routes would often break and routed packets are always subject to flow control. ''push proxies'' were introduced to address this problem. These are usually the ultrapeers of a leaf node and they are announced in search results. The client connects to one of these ''push proxies'' using an HTTP request and the proxy sends a ''push request'' to a leaf on behalf of the client. Normally, it is also possible to send a push request over UDP to the push proxy, which is more efficient than using TCP. Push proxies have two advantages: First, ultrapeer-leaf connections are more stable than routes. This makes push requests much more reliable. Second, it reduces the amount of traffic routed through the Gnutella network.
Finally, when a user disconnects, the client software saves a list of known nodes.
This contains the nodes to which the client was connected and the nodes learned from pong packets.
The client uses that as its seed list, when it next starts, thus becoming independent of bootstrap services.
In practice, this method of searching on the Gnutella network was often unreliable. Each node is a regular computer user; as such, they are constantly connecting and disconnecting, so the network is never completely stable. Also, the bandwidth cost of searching on Gnutella grew exponentially to the number of connected users, often saturating connections and rendering slower nodes useless. Therefore, search requests would often be dropped, and most queries reached only a very small part of the network. This observation identified the Gnutella network as an unscalable distributed system, and inspired the development of distributed hash table
A distributed hash table (DHT) is a distributed system that provides a lookup service similar to a hash table: key–value pairs are stored in a DHT, and any participating node can efficiently retrieve the value associated with a given key. The ...
s, which are much more scalable but support only exact-match, rather than keyword, search.
To address the problems of bottleneck
Bottleneck literally refers to the narrowed portion (neck) of a bottle near its opening, which limit the rate of outflow, and may describe any object of a similar shape. The literal neck of a bottle was originally used to play what is now known as ...
s, Gnutella developers implemented a tiered system of ''ultrapeers'' and ''leaves''. Instead of all nodes being considered equal, nodes entering the network were kept at the 'edge' of the network, as a leaf. Leaves don't provide routing. Nodes which are capable of routing messages are promoted to ultrapeers. Ultrapeers accept leaf connections and route searches and network maintenance messages. This allows searches to propagate further through the network and allows for numerous alterations in topology. This greatly improved efficiency and scalability.
Additionally, gnutella adopted a number of other techniques to reduce traffic overhead and make searches more efficient. Most notable are Query Routing Protocol (QRP) and Dynamic Querying (DQ). With QRP, a search reaches only those clients which are likely to have the files, so searches for rare files become far more efficient. With DQ, the search stops as soon as the program has acquired enough search results. This vastly reduces the amount of traffic caused by popular searches.
One of the benefits of having Gnutella so decentralized is to make it very difficult to shut the network down and to make it a network in which the users are the only ones who can decide which content will be available. Unlike Napster
Napster was a peer-to-peer file sharing application. It originally launched on June 1, 1999, with an emphasis on digital audio file distribution. Audio songs shared on the service were typically encoded in the MP3 format. It was founded by Sh ...
, where the entire network relied on the central server, Gnutella cannot be shut down by shutting down any one node. A decentralized network prevents bad actors from taking control of the contents of the network and/or manipulating data by controlling the central server.
Protocol features and extensions
Gnutella once operated on a purelyquery flooding
Query flooding is a method to search for a resource on a peer-to-peer network. It is simple and scales very poorly and thus is rarely used. Early versions of the Gnutella protocol operated by query flooding; newer versions use more efficient search ...
-based protocol. The outdated Gnutella version 0.4 network protocol
A communication protocol is a system of rules that allows two or more entities of a communications system to transmit information via any kind of variation of a physical quantity. The protocol defines the rules, syntax, semantics and synchroni ...
employs five different packet types, namely:
* ping: discover hosts on network
* pong: reply to ping
* query: search for a file
* query hit: reply to query
* push: download request for firewalled servants
These packets facilitate searches. File transfers are instead handled by HTTP
The Hypertext Transfer Protocol (HTTP) is an application layer protocol in the Internet protocol suite model for distributed, collaborative, hypermedia information systems. HTTP is the foundation of data communication for the World Wide Web, ...
.Dye, Mark. McDonald, Rick. Rufi, Antoon W., 'Network Fundamentals', Cisco Networking Academy, Cisco Press, Ch 3. p90
The development of the Gnutella protocol is currently led by the Gnutella Developers Forum (The GDF). Many protocol extensions have been and are being developed by the software vendors and by the free Gnutella developers of the GDF. These extensions include intelligent query routing, SHA-1
In cryptography, SHA-1 (Secure Hash Algorithm 1) is a cryptographically broken but still widely used hash function which takes an input and produces a 160-bit (20- byte) hash value known as a message digest – typically rendered as 40 hexadec ...
checksums, query hit transmission via UDP, querying via UDP, dynamic queries via TCP, file transfers via UDP, XML
Extensible Markup Language (XML) is a markup language and file format for storing, transmitting, and reconstructing arbitrary data. It defines a set of rules for encoding documents in a format that is both human-readable and machine-readable. ...
metadata, source exchange (also termed ''the download mesh'') and parallel downloading in slices (swarming).
There are efforts to finalize these protocol extensions in the Gnutella 0.6 specification, at the Gnutella protocol development website. The Gnutella 0.4 standard is outdated but it remains the latest protocol specification because all extensions, so far, exist as proposals. In fact, it is hard or impossible to connect today with 0.4 handshakes. According to developers in the GDF, version 0.6 is what new developers should pursue using thwork-in-progress specifications
The Gnutella protocol remains under development. Despite attempts to make a clean break with the complexity inherited from the old Gnutella 0.4 and to design a clean new message architecture, it remains one of the most successful file-sharing protocols to date.
Software
The following tables compare general and technical information for a number of applications supporting the Gnutella network. The tables do not attempt to give a complete list of Gnutella clients. The tables are limited to clients that can participate in the current Gnutella network.General specifications
Gnutella features
Notes
*Morpheus
Morpheus ('Fashioner', derived from the grc, μορφή meaning 'form, shape') is a god associated with sleep and dreams. In Ovid's ''Metamorphoses'' he is the son of Somnus and appears in dreams in human form. From the Middle Ages, the name ...
differs significantly and may have completely independent code from the GnucDNA engine. Morpheus can function as a ''modern'' ultrapeer whereas other GnucDNA clients cannot.
* Gnucleus and Kiwi Alpha use the GnucDNA
GnucDNA was a software library for building peer-to-peer applications. It provides developers with a common layer to create their own Gnutella or Gnutella2 client or network. As a separate component, GnucDNA can be updated independently of the ...
engine.
* BearFlix
BearShare was a peer-to-peer-file-sharing-application originally created by Free Peers, Inc. for Microsoft Windows and also a rebranded version of iMesh by MusicLab, LLC, tightly integrated with their music subscription service.
History
The pri ...
, a functionally limited version of the BearShare
BearShare was a peer-to-peer-file-sharing-application originally created by Free Peers, Inc. for Microsoft Windows and also a rebranded version of iMesh by MusicLab, LLC, tightly integrated with their music subscription service.
History
The pr ...
5.2 series, can search only for images or videos and shared videos are limited to a relatively short length.
* giFTcurs
A gift or a present is an item given to someone without the expectation of payment or anything in return. An item is not a gift if that item is already owned by the one to whom it is given. Although gift-giving might involve an expectation ...
, Apollon
Apollon may refer to:
* Apollo, ancient Greek god of light, healing and poetry
* Apollon (Formula One), Formula One constructor
* Apollon Kalamarias, Greek football club
* Apollon Athens, a Greek football club from Athens
* Apollon Limassol B.C., ...
, FilePipe, giFToxic
A gift or a present is an item given to someone without the expectation of payment or anything in return. An item is not a gift if that item is already owned by the one to whom it is given. Although gift-giving might involve an expectation ...
, giFTui, giFTwin32
A gift or a present is an item given to someone without the expectation of payment or anything in return. An item is not a gift if that item is already owned by the one to whom it is given. Although gift-giving might involve an expectation ...
, KCeasy, Poisoned, and Xfactor are GUI front-ends for the giFT
A gift or a present is an item given to someone without the expectation of payment or anything in return. An item is not a gift if that item is already owned by the one to whom it is given. Although gift-giving might involve an expectation ...
engine.
* etomi uses outdated Shareaza
Shareaza is a peer-to-peer file sharing client running under Microsoft Windows which supports the gnutella, Gnutella2 (G2), eDonkey, BitTorrent, FTP, HTTP and HTTPS network protocols and handles magnet links, ed2k links, and the now deprecated ...
networking code.
* MP3 Rocket, 360Share, LemonWire, MP3Torpedo, and DexterWire are variants of LimeWire
LimeWire was a free peer-to-peer file sharing client for Windows, MacOS, Linux and Solaris. Created by Mark Gorton in 2000, it was most prominently a tool used for the download and distribution of pirated materials, particularly pirated musi ...
.
* FrostWire
FrostWire is a free and open-source BitTorrent client first released in September 2004, as a fork of LimeWire. It was initially very similar to LimeWire in appearance and functionality, but over time developers added more features, including supp ...
(up to version 4.21.8) is nearly identical to LimeWire 4.18 but versions greater than 5.00 no longer use gnutella.
* Acquisition and Cabos are custom front-ends overlaying the LimeWire
LimeWire was a free peer-to-peer file sharing client for Windows, MacOS, Linux and Solaris. Created by Mark Gorton in 2000, it was most prominently a tool used for the download and distribution of pirated materials, particularly pirated musi ...
engine.
* LimeWire Pirate Edition (5.6.2) is a resurrected version of the unreleased LimeWire
LimeWire was a free peer-to-peer file sharing client for Windows, MacOS, Linux and Solaris. Created by Mark Gorton in 2000, it was most prominently a tool used for the download and distribution of pirated materials, particularly pirated musi ...
5.6.1 alpha, thus has similar features minus automatic updates (with nags) and centralized remote controls to disable core functions like searches and downloads were removed.
Gnutella2
The Gnutella2 protocol (often referred to as G2), despite its name, is not a successor protocol of Gnutella nor related to the original Gnutella project, but rather is a completely different protocol that forked from the original project and piggybacked on the Gnutella name. A sore point with many Gnutella developers is that the ''Gnutella2'' name conveys an upgrade or superiority, which led to a flame war. Other criticism included the use of the Gnutella network to bootstrap G2 peers and poor documentation of the G2 protocol. Additionally, the more frequent search retries of theShareaza
Shareaza is a peer-to-peer file sharing client running under Microsoft Windows which supports the gnutella, Gnutella2 (G2), eDonkey, BitTorrent, FTP, HTTP and HTTPS network protocols and handles magnet links, ed2k links, and the now deprecated ...
client, one of the initial G2 clients, could unnecessarily burden the Gnutella network.
Both protocols have undergone significant changes since the fork in 2002. G2 has advantages and disadvantages compared to Gnutella. An advantage often cited is that Gnutella2's hybrid search is more efficient than the original Gnutella's query flooding
Query flooding is a method to search for a resource on a peer-to-peer network. It is simple and scales very poorly and thus is rarely used. Early versions of the Gnutella protocol operated by query flooding; newer versions use more efficient search ...
. However, Gnutella replaced query flooding with more efficient search methods, starting with Query Routing in 2002. This was proposed in 2001 by Limewire developers. An advantage of Gnutella is its large user base, which numbers in the millions,. The G2 network is approximately an order of magnitude
An order of magnitude is an approximation of the logarithm of a value relative to some contextually understood reference value, usually 10, interpreted as the base of the logarithm and the representative of values of magnitude one. Logarithmic di ...
smaller.Population ~200,000 January 2010. It is difficult to compare the protocols in their current form. The choice of client, on either network, probably affects the end user just as much.
See also
* Bitzi *Gnutella crawler
A Gnutella crawler is a software program used to gather statistic information on the gnutella file sharing network, such as the number of users, the market share of different clients and the geographical distribution of the userbase.
Early crawler ...
* GNUnet
GNUnet is a software framework for decentralized, peer-to-peer networking and an official GNU package. The framework offers link encryption, peer discovery, resource allocation, communication over many transports (such as TCP, UDP, HTTP, ...
References
* Dye, Mark. McDonald, Rick. Rufi, Antoon W., 'Network Fundamentals', Cisco Networking Academy, Cisco Press, Ch 3. p91 * Dye, Mark. McDonald, Rick. Rufi, Antoon W., 'Network Fundamentals', Cisco Networking Academy, Cisco Press, Ch 3. p90External links
Gnutella Forums
Official user support boards
Gnutella Protocol Development Wiki
(on
Internet Archive
The Internet Archive is an American digital library with the stated mission of "universal access to all knowledge". It provides free public access to collections of digitized materials, including websites, software applications/games, music ...
, 2009)
Gnutella Protocol Development Portal
(on Internet Archive)
Gnutella official website
(on Internet Archive)
GnuFU
''Gnutella For Users: A description of the inner workings of the gnutella network in User-Friendly Style''
Glasnost
test Gnutella
traffic shaping
Traffic shaping is a bandwidth management technique used on computer networks which delays some or all datagrams to bring them into compliance with a desired ''traffic profile''. Traffic shaping is used to optimize or guarantee performance, imp ...
(Max Planck Institute for Software Systems
The Max Planck Institute for Software Systems (MPI-SWS) is a computer science research institute co-located in Saarbrücken and Kaiserslautern, Germany. The institute is chartered to conduct basic research in all areas related to the design, anal ...
)
{{File sharing protocols
File sharing networks
Application layer protocols
Hash based data structures