Spearphish on:
[Wikipedia]
[Google]
[Amazon]
Phishing is a form of social engineering and a
Federal Bureau of Investigation Compromised streaming service accounts may also be sold on
 SMS phishing or smishing is a type of phishing attack that uses
SMS phishing or smishing is a type of phishing attack that uses
 Phishing often uses social engineering techniques to trick users into performing actions such as clicking a link or opening an attachment, or revealing sensitive information. It often involves pretending to be a trusted entity and creating a sense of urgency, like threatening to close or seize a victim's bank or insurance account.
An alternative technique to impersonation-based phishing is the use of
Phishing often uses social engineering techniques to trick users into performing actions such as clicking a link or opening an attachment, or revealing sensitive information. It often involves pretending to be a trusted entity and creating a sense of urgency, like threatening to close or seize a victim's bank or insurance account.
An alternative technique to impersonation-based phishing is the use of
 Effective phishing education, including conceptual knowledge and feedback, is an important part of any organization's anti-phishing strategy. While there is limited data on the effectiveness of education in reducing susceptibility to phishing, much information on the threat is available online.
Simulated phishing campaigns, in which organizations test their employees' training by sending fake phishing emails, are commonly used to assess their effectiveness. One example is a study by the
Effective phishing education, including conceptual knowledge and feedback, is an important part of any organization's anti-phishing strategy. While there is limited data on the effectiveness of education in reducing susceptibility to phishing, much information on the threat is available online.
Simulated phishing campaigns, in which organizations test their employees' training by sending fake phishing emails, are commonly used to assess their effectiveness. One example is a study by the
 Another popular approach to fighting phishing is to maintain a list of known phishing sites and to check websites against the list. One such service is the Safe Browsing service. Web browsers such as
Another popular approach to fighting phishing is to maintain a list of known phishing sites and to check websites against the list. One such service is the Safe Browsing service. Web browsers such as
Anti-Phishing Working Group
Center for Identity Management and Information Protection
– Utica College
Plugging the "phishing" hole: legislation versus technology
() – '' Duke Law & Technology Review''
Example of a Phishing Attempt with Screenshots and Explanations
– StrategicRevenue.com
A Profitless Endeavor: Phishing as Tragedy of the Commons
– Microsoft Corporation
Database for information on phishing sites reported by the public
– PhishTank
The Impact of Incentives on Notice and Take-down
− Computer Laboratory, University of Cambridge (PDF, 344 kB) {{Authority control Confidence tricks Cybercrime Deception Fraud Identity theft Internet terminology Organized crime activity Social engineering (security) Spamming Types of cyberattacks
scam
A scam, or a confidence trick, is an attempt to defraud a person or group after first gaining their Trust (emotion), trust. Confidence tricks exploit victims using a combination of the victim's credulity, naivety, compassion, vanity, confidence ...
where attackers deceive people into revealing sensitive information or installing malware
Malware (a portmanteau of ''malicious software'')Tahir, R. (2018)A study on malware and malware detection techniques . ''International Journal of Education and Management Engineering'', ''8''(2), 20. is any software intentionally designed to caus ...
such as viruses
A virus is a submicroscopic infectious agent that replicates only inside the living cells of an organism. Viruses infect all life forms, from animals and plants to microorganisms, including bacteria and archaea. Viruses are found in almo ...
, worms
The World Register of Marine Species (WoRMS) is a taxonomic database that aims to provide an authoritative and comprehensive catalogue and list of names of marine organisms.
Content
The content of the registry is edited and maintained by scien ...
, adware
Adware, often called advertising-supported software by its developers, is software that generates revenue by automatically displaying Online advertising, online advertisements in the user interface or on a screen presented during the installatio ...
, or ransomware
Ransomware is a type of malware that Encryption, encrypts the victim's personal data until a ransom is paid. Difficult-to-trace Digital currency, digital currencies such as paysafecard or Bitcoin and other cryptocurrency, cryptocurrencies are com ...
. Phishing attacks have become increasingly sophisticated and often transparently mirror the site being targeted, allowing the attacker to observe everything while the victim navigates the site, and transverses any additional security boundaries with the victim. As of 2020, it is the most common type of cybercrime
Cybercrime encompasses a wide range of criminal activities that are carried out using digital devices and/or Computer network, networks. It has been variously defined as "a crime committed on a computer network, especially the Internet"; Cyberc ...
, with the Federal Bureau of Investigation
The Federal Bureau of Investigation (FBI) is the domestic Intelligence agency, intelligence and Security agency, security service of the United States and Federal law enforcement in the United States, its principal federal law enforcement ag ...
's Internet Crime Complaint Center
The Internet Crime Complaint Center (IC3) is a division of the Federal Bureau of Investigation (FBI) concerning suspected Internet-facilitated criminal activity. The IC3 gives victims a convenient and easy-to-use reporting mechanism that alerts ...
reporting more incidents of phishing than any other type of cybercrime.
The term "phishing" was first recorded in 1995 in the cracking toolkit AOHell
AOHell was a Windows application that was used to simplify ' cracking' (computer hacking) using AOL. The program contained a very early use of the term phishing. It was created by a teenager under the pseudonym Da Chronic, whose expressed motiv ...
, but may have been used earlier in the hacker magazine '' 2600''. It is a variation of ''fishing'' and refers to the use of lures to "fish" for sensitive information.
Measures to prevent or reduce the impact of phishing attacks include legislation
Legislation is the process or result of enrolling, enacting, or promulgating laws by a legislature, parliament, or analogous governing body. Before an item of legislation becomes law it may be known as a bill, and may be broadly referred ...
, user education, public awareness, and technical security measures. The importance of phishing awareness has increased in both personal and professional settings, with phishing attacks among businesses rising from 72% in 2017 to 86% in 2020, already rising to 94% in 2023.
Types
Email phishing
Phishing attacks, often delivered viaemail spam
Email spam, also referred to as junk email, spam mail, or simply spam, refers to unsolicited messages sent in bulk via email. The term originates from a Spam (Monty Python), Monty Python sketch, where the name of a canned meat product, "Spam (food ...
, attempt to trick individuals into giving away sensitive information or login credentials. Most attacks are "bulk attacks" that are not targeted and are instead sent in bulk to a wide audience. The goal of the attacker can vary, with common targets including financial institutions, email and cloud productivity providers, and streaming services. The stolen information or access may be used to steal money, install malware
Malware (a portmanteau of ''malicious software'')Tahir, R. (2018)A study on malware and malware detection techniques . ''International Journal of Education and Management Engineering'', ''8''(2), 20. is any software intentionally designed to caus ...
, or spear phish others within the target organization.Spoofing and PhishingFederal Bureau of Investigation Compromised streaming service accounts may also be sold on
darknet market
A darknet market is a commercial website on the dark web that operates via darknets such as Tor and I2P. They function primarily as black markets, selling or brokering transactions involving drugs, cyber-arms, weapons, counterfeit currency, ...
s.
This type of social engineering attack can involve sending fraudulent emails or messages that appear to be from a trusted source, such as a bank or government agency. These messages typically redirect to a fake login page where users are prompted to enter their credentials.
Spear phishing
Spear phishing is a targeted phishing attack that uses personalized messaging, especially e‑mails, to trick a specific individual or organization into believing they are legitimate. It often utilizes personal information about the target to increase the chances of success. These attacks often target executives or those in financial departments with access to sensitive financial data and services. Accountancy and audit firms are particularly vulnerable to spear phishing due to the value of the information their employees have access to. The Russian government-run Threat Group-4127 (Fancy Bear) (GRU Unit 26165) targetedHillary Clinton
Hillary Diane Rodham Clinton ( Rodham; born October 26, 1947) is an American politician, lawyer and diplomat. She was the 67th United States secretary of state in the administration of Barack Obama from 2009 to 2013, a U.S. senator represent ...
's 2016 presidential campaign with spear phishing attacks on over 1,800 Google
Google LLC (, ) is an American multinational corporation and technology company focusing on online advertising, search engine technology, cloud computing, computer software, quantum computing, e-commerce, consumer electronics, and artificial ...
accounts, using the domain to threaten targeted users.
A study on spear phishing susceptibility among different age groups found that 43% of youth aged 18–25 years and 58% of older users clicked on simulated phishing links in daily e‑mails over 21 days. Older women had the highest susceptibility, while susceptibility in young users declined during the study, but remained stable among older users.
Voice phishing (Vishing)
Voice over IP
Voice over Internet Protocol (VoIP), also known as IP telephony, is a set of technologies used primarily for voice communication sessions over Internet Protocol (IP) networks, such as the Internet. VoIP enables voice calls to be transmitted as ...
(VoIP) is used in vishing or voice phishing attacks, where attackers make automated phone calls to large numbers of people, often using text-to-speech
Speech synthesis is the artificial production of human speech. A computer system used for this purpose is called a speech synthesizer, and can be implemented in software or Computer hardware, hardware products. A text-to-speech (TTS) system conv ...
synthesizers, claiming fraudulent activity on their accounts. The attackers spoof the calling phone number to appear as if it is coming from a legitimate bank or institution. The victim is then prompted to enter sensitive information or connected to a live person who uses social engineering tactics to obtain information. Vishing takes advantage of the public's lower awareness and trust in voice telephony compared to email phishing.
SMS phishing (smishing)
text messages
Text messaging, or texting, is the act of composing and sending electronic messages, typically consisting of alphabetic and numeric characters, between two or more users of mobile phones, tablet computers, smartwatches, desktop computer, des ...
from a cell phone or smartphone
A smartphone is a mobile phone with advanced computing capabilities. It typically has a touchscreen interface, allowing users to access a wide range of applications and services, such as web browsing, email, and social media, as well as multi ...
to deliver a bait message. The victim is usually asked to click a link, call a phone number, or contact an email
Electronic mail (usually shortened to email; alternatively hyphenated e-mail) is a method of transmitting and receiving Digital media, digital messages using electronics, electronic devices over a computer network. It was conceived in the ...
address provided by the attacker. They may then be asked to provide private information
Privacy (, ) is the ability of an individual or group to seclude themselves or information about themselves, and thereby express themselves selectively.
The domain of privacy partially overlaps with security, which can include the concepts of a ...
, such as login credentials for other websites.
The difficulty in identifying illegitimate links can be compounded on mobile devices due to the limited display of URLs in mobile browsers.
Smishing can be just as effective as email phishing, as many smartphones have fast internet connectivity. Smishing messages may also come from unusual phone numbers.
Page hijacking
Page hijacking involves redirecting users to malicious websites orexploit kit
An exploit kit is a tool used for automatically managing and deploying Exploit (computer security), exploits against a target computer. Exploit kits allow attackers to deliver malware without having advanced knowledge of the exploits being used. ...
s through the compromise of legitimate web pages, often using cross site scripting
Cross-site scripting (XSS) is a type of security vulnerability that can be found in some web applications. XSS attacks enable attackers to inject client-side scripts into web pages viewed by other users. A cross-site scripting vulnerability may be ...
. Hacker
A hacker is a person skilled in information technology who achieves goals and solves problems by non-standard means. The term has become associated in popular culture with a security hackersomeone with knowledge of bug (computing), bugs or exp ...
s may insert exploit kits such as MPack into compromised websites to exploit legitimate users visiting the server. Page hijacking can also involve the insertion of malicious inline frames, allowing exploit kits to load. This tactic is often used in conjunction with watering hole
A watering hole or waterhole is a geological depression in which a body of water forms, usually a pond or a small lake.
A watering hole is "a sunken area of land that fills with water".
Watering holes may be ephemeral or seasonal. Ephemeral ...
attacks on corporate targets.
QR code phishing (quishing)
In "quishing" ( QR code phishing), scammers exploit the convenience of QR codes to trick users into giving up sensitive data, by scanning a code containing an embedded malicious web site link. Unlike traditional phishing, which relies on deceptive emails or websites, quishing uses QR codes to bypass email filters and increase the likelihood that victims will fall for the scam, as people tend to trust QR codes and may not scrutinize them as carefully as a URL or email link. The bogus codes may be sent by email, social media, or in some cases hard copy stickers are placed over legitimate QR codes on such things as advertising posters and car park notices. When victims scan the QR code with their phone or device, they are redirected to a fake website designed to steal personal information, login credentials, or financial details. As QR codes become more widely used for things like payments, event check-ins, and product information, quishing is emerging as a significant concern for digital security. Users are advised to exercise caution when scanning unfamiliar QR codes and ensure they are from trusted sources, although the UK's National Cyber Security Centre rates the risk as lower than other types of lure.Man-in-the-Middle phishing
Traditional phishing attacks are typically limited to capturing user credentials directly inputted into fraudulent websites. However, the advent ofMan-in-the-Middle
In cryptography and computer security, a man-in-the-middle (MITM) attack, or on-path attack, is a cyberattack where the attacker secretly relays and possibly alters the communications between two parties who believe that they are directly communi ...
(MitM) phishing techniques has significantly advanced the sophistication of these attacks, enabling cybercriminals to bypass two-factor authentication
Multi-factor authentication (MFA; two-factor authentication, or 2FA) is an electronic authentication method in which a user is granted access to a website or Application software, application only after successfully presenting two or more distin ...
(2FA) mechanisms during a user's active session on a web service. MitM phishing attacks employ intermediary tools that intercept communication between the user and the legitimate service.
Evilginx, originally created as an open-source tool for penetration testing and ethical hacking, has been repurposed by cybercriminals for MitM attacks. Evilginx works like a middleman, passing information between the victim and the real website without saving passwords or login codes. This makes it harder for security systems to detect, since they usually look for phishing sites that store stolen data. By grabbing login tokens and session cookies instantly, attackers can break into accounts and use them just like the real user, for as long as the session stays active.
Attackers employ various methods, including phishing emails, social engineering tactics, or distributing malicious links via social media platforms. Once the victim interacts with the counterfeit site, the MitM tool intercepts the authentication process, effectively bypassing 2FA protections.
Techniques
Link manipulation
Phishing attacks often involve creating fake links that appear to be from a legitimate organization. These links may use misspelled URLs orsubdomain
In the Domain Name System (DNS) hierarchy, a subdomain is a domain that is a part of another (main) domain. For example, if a domain offered an online store as part of their website it might use the subdomain.
Overview
The Domain Name System ...
s to deceive the user. In the following example URL, , it can appear to the untrained eye as though the URL will take the user to the ''example'' section of the ''yourbank'' website; this URL points to the "''yourbank''" (i.e. phishing subdomain) section of the ''example'' website (fraudster's domain name). Another tactic is to make the displayed text for a link appear trustworthy, while the actual link goes to the phisher's site. To check the destination of a link, many email clients and web browsers will show the URL in the status bar when the mouse
A mouse (: mice) is a small rodent. Characteristically, mice are known to have a pointed snout, small rounded ears, a body-length scaly tail, and a high breeding rate. The best known mouse species is the common house mouse (''Mus musculus'' ...
is hovering over it. However, some phishers may be able to bypass this security measure.
Internationalized domain name
An internationalized domain name (IDN) is an Internet domain name that contains at least one label displayed in software applications, in whole or in part, in non-Latin script or alphabet or in the Latin alphabet-based characters with diacrit ...
s (IDNs) can be exploited via IDN spoofing or homograph attacks to allow attackers to create fake websites with visually identical addresses to legitimate ones. These attacks have been used by phishers to disguise malicious URLs using open URL redirectors on trusted websites. An example of this is in http://www.exаmple.com/ Latin
Latin ( or ) is a classical language belonging to the Italic languages, Italic branch of the Indo-European languages. Latin was originally spoken by the Latins (Italic tribe), Latins in Latium (now known as Lazio), the lower Tiber area aroun ...
letter ' a', but instead the Cyrillic
The Cyrillic script ( ) is a writing system used for various languages across Eurasia. It is the designated national script in various Slavic, Turkic, Mongolic, Uralic, Caucasian and Iranic-speaking countries in Southeastern Europe, Ea ...
character ' а'. When the victim clicks on the link, unaware that the third character is actually the Cyrillic letter 'а', they get redirected to the malicious site http://www.xn--exmple-4nf.com/ Social engineering
 Phishing often uses social engineering techniques to trick users into performing actions such as clicking a link or opening an attachment, or revealing sensitive information. It often involves pretending to be a trusted entity and creating a sense of urgency, like threatening to close or seize a victim's bank or insurance account.
An alternative technique to impersonation-based phishing is the use of
Phishing often uses social engineering techniques to trick users into performing actions such as clicking a link or opening an attachment, or revealing sensitive information. It often involves pretending to be a trusted entity and creating a sense of urgency, like threatening to close or seize a victim's bank or insurance account.
An alternative technique to impersonation-based phishing is the use of fake news
Fake news or information disorder is false or misleading information (misinformation, disinformation, propaganda, and hoaxes) claiming the aesthetics and legitimacy of news. Fake news often has the aim of damaging the reputation of a person ...
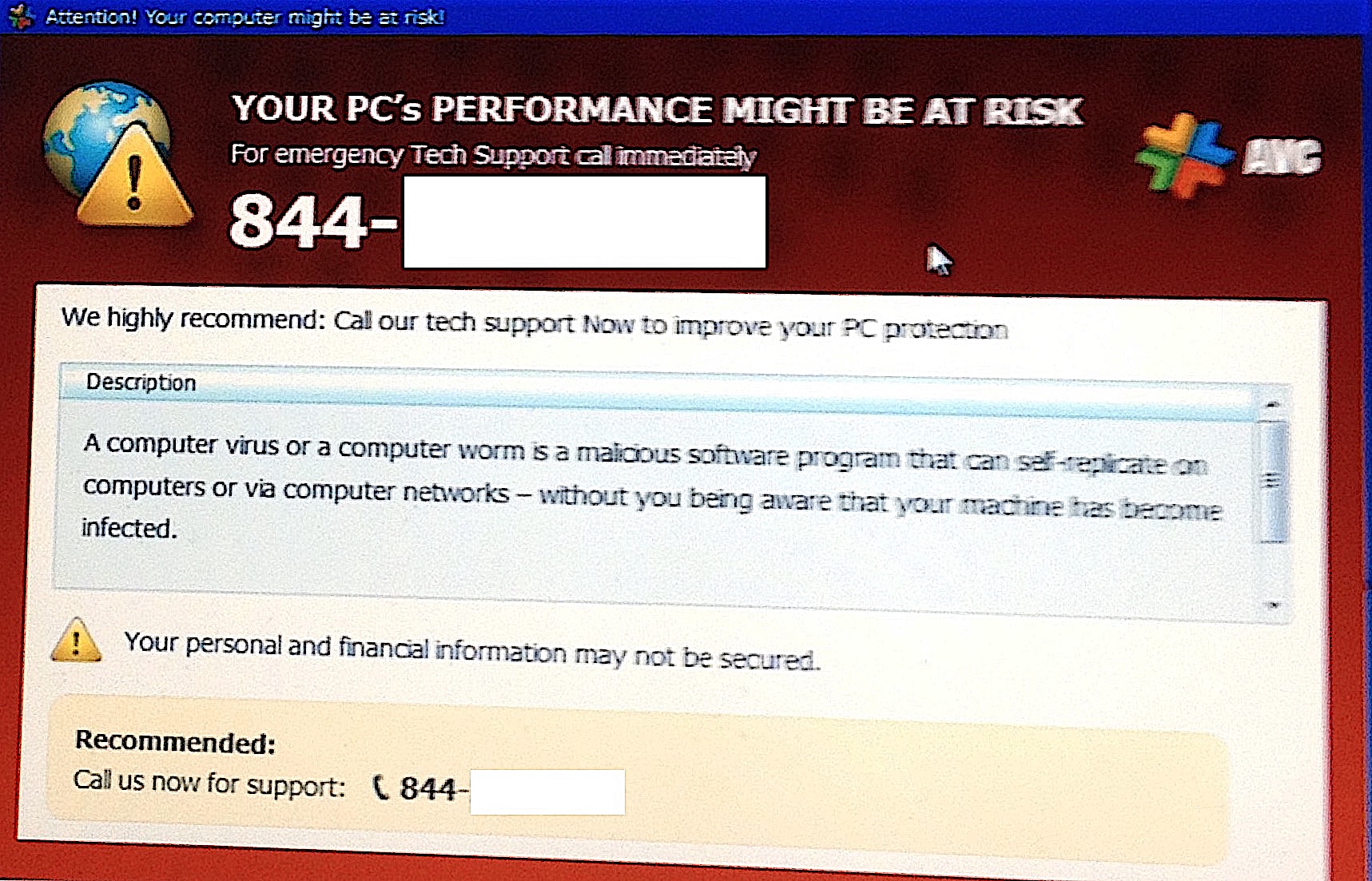
articles to trick victims into clicking on a malicious link. These links often lead to fake websites that appear legitimate, but are actually run by attackers who may try to install malware or present fake "virus" notifications to the victim.
History
Early history
Early phishing techniques can be traced back to the 1990s, when black hat hackers and thewarez
Warez refers to pirated software and other copyrighted digital media—such as video games, movies, music, and e-books—illegally distributed online, often after bypassing digital rights management (DRM). The term, derived from “software wa ...
community used AOL to steal credit card information and commit other online crimes. The term "phishing" is said to have been coined by Khan C. Smith, a well-known spammer and hacker, and its first recorded mention was found in the hacking tool AOHell
AOHell was a Windows application that was used to simplify ' cracking' (computer hacking) using AOL. The program contained a very early use of the term phishing. It was created by a teenager under the pseudonym Da Chronic, whose expressed motiv ...
, which was released in 1994. AOHell allowed hackers to impersonate AOL staff and send instant message
Instant messaging (IM) technology is a type of synchronous computer-mediated communication involving the immediate (real-time) transmission of messages between two or more parties over the Internet or another computer network. Originally involvin ...
s to victims asking them to reveal their passwords. In response, AOL implemented measures to prevent phishing and eventually shut down the warez scene
The Warez scene, often referred to as The Scene, is an underground network of piracy groups specialized in obtaining and illegally releasing digital media before their official release date. The Scene distributes all forms of digital media, incl ...
on their platform.
2000s
In the 2000s, phishing attacks became more organized and targeted. The first known direct attempt against a payment system,E-gold
E-gold or eGold was a digital gold currency operated by Gold & Silver Reserve Inc. (G&SR) that allowed users to make payments, which it called "spends", in grams of gold, silver, and other precious metals. E-gold was launched in 1996 and grew to ...
, occurred in June 2001, and shortly after the September 11 attacks
The September 11 attacks, also known as 9/11, were four coordinated Islamist terrorist suicide attacks by al-Qaeda against the United States in 2001. Nineteen terrorists hijacked four commercial airliners, crashing the first two into ...
, a "post-9/11 id check" phishing attack followed. The first known phishing attack against a retail bank was reported in September 2003. Between May 2004 and May 2005, approximately 1.2 million computer users in the United States suffered losses caused by phishing, totaling approximately . Phishing was recognized as a fully organized part of the black market, and specializations emerged on a global scale that provided phishing software for payment, which were assembled and implemented into phishing campaigns by organized gangs. The United Kingdom
The United Kingdom of Great Britain and Northern Ireland, commonly known as the United Kingdom (UK) or Britain, is a country in Northwestern Europe, off the coast of European mainland, the continental mainland. It comprises England, Scotlan ...
banking sector suffered from phishing attacks, with losses from web banking fraud almost doubling in 2005 compared to 2004. In 2006, almost half of phishing thefts were committed by groups operating through the Russian Business Network based in St. Petersburg. Email scams posing as the Internal Revenue Service
The Internal Revenue Service (IRS) is the revenue service for the Federal government of the United States, United States federal government, which is responsible for collecting Taxation in the United States, U.S. federal taxes and administerin ...
were also used to steal sensitive data from U.S. taxpayers. Social networking sites
A social networking service (SNS), or social networking site, is a type of online social media platform which people use to build social networks or social relationships with other people who share similar personal or career content, interests ...
are a prime target of phishing, since the personal details in such sites can be used in identity theft
Identity theft, identity piracy or identity infringement occurs when someone uses another's personal identifying information, like their name, identifying number, or credit card number, without their permission, to commit fraud or other crimes. ...
; In 2007, 3.6 million adults lost due to phishing attacks. The Anti-Phishing Working Group reported receiving 115,370 phishing email reports from consumers with US and China hosting more than 25% of the phishing pages each in the third quarter of 2009.
2010s
Phishing in the 2010s saw a significant increase in the number of attacks. In 2011, the master keys for RSA SecurID security tokens were stolen through a phishing attack. Chinese phishing campaigns also targeted high-ranking officials in the US and South Korean governments and military, as well as Chinese political activists. According to Ghosh, phishing attacks increased from 187,203 in 2010 to 445,004 in 2012. In August 2013, Outbrain suffered a spear-phishing attack, and in November 2013, 110 million customer and credit card records were stolen fromTarget
Target may refer to:
Warfare and shooting
* Shooting target, used in marksmanship training and various shooting sports
** Bullseye (target), the goal one for which one aims in many of these sports
** Aiming point, in field artille ...
customers through a phished subcontractor account. CEO and IT security staff subsequently fired. In August 2014, iCloud leaks of celebrity photos were based on phishing e-mails sent to victims that looked like they came from Apple or Google. In November 2014, phishing attacks on ICANN
The Internet Corporation for Assigned Names and Numbers (ICANN ) is a global multistakeholder group and nonprofit organization headquartered in the United States responsible for coordinating the maintenance and procedures of several dat ...
gained administrative access to the Centralized Zone Data System; also gained was data about users in the system - and access to ICANN's public Governmental Advisory Committee wiki, blog, and whois information portal. Fancy Bear was linked to spear-phishing attacks against the Pentagon
In geometry, a pentagon () is any five-sided polygon or 5-gon. The sum of the internal angles in a simple polygon, simple pentagon is 540°.
A pentagon may be simple or list of self-intersecting polygons, self-intersecting. A self-intersecting ...
email system in August 2015, and the group used a zero-day exploit of Java in a spear-phishing attack on the White House and NATO. Fancy Bear carried out spear phishing attacks on email addresses associated with the Democratic National Committee in the first quarter of 2016. In August 2016, members of the Bundestag
The Bundestag (, "Federal Diet (assembly), Diet") is the lower house of the Germany, German Federalism in Germany, federal parliament. It is the only constitutional body of the federation directly elected by the German people. The Bundestag wa ...
and political parties such as Linken-faction leader Sahra Wagenknecht, Junge Union, and the CDU of Saarland
Saarland (, ; ) is a state of Germany in the southwest of the country. With an area of and population of 990,509 in 2018, it is the smallest German state in area apart from the city-states of Berlin, Bremen, and Hamburg, and the smallest in ...
were targeted by spear-phishing attacks suspected to be carried out by Fancy Bear. In August 2016, the World Anti-Doping Agency
The World Anti-Doping Agency (WADA; , AMA) is an international organization co-founded by the governments of over 140 nations along with the International Olympic Committee based in Canada to promote, coordinate, and monitor the fight against d ...
reported the receipt of phishing emails sent to users of its database claiming to be official WADA, but consistent with the Russian hacking group Fancy Bear. In 2017, 76% of organizations experienced phishing attacks, with nearly half of the information security
Information security is the practice of protecting information by mitigating information risks. It is part of information risk management. It typically involves preventing or reducing the probability of unauthorized or inappropriate access to data ...
professionals surveyed reporting an increase from 2016. In the first half of 2017, businesses and residents of Qatar were hit with over 93,570 phishing events in a three-month span. In August 2017, customers of Amazon
Amazon most often refers to:
* Amazon River, in South America
* Amazon rainforest, a rainforest covering most of the Amazon basin
* Amazon (company), an American multinational technology company
* Amazons, a tribe of female warriors in Greek myth ...
faced the Amazon Prime Day phishing attack, when hackers sent out seemingly legitimate deals to customers of Amazon. When Amazon's customers attempted to make purchases using the "deals", the transaction would not be completed, prompting the retailer's customers to input data that could be compromised and stolen. In 2018, the company block.one, which developed the EOS.IO blockchain, was attacked by a phishing group who sent phishing emails to all customers aimed at intercepting the user's cryptocurrency wallet key, and a later attack targeted airdrop tokens.
2020s
Phishing attacks have evolved in the 2020s to include elements of social engineering, as demonstrated by the July 15, 2020,Twitter
Twitter, officially known as X since 2023, is an American microblogging and social networking service. It is one of the world's largest social media platforms and one of the most-visited websites. Users can share short text messages, image ...
breach. In this case, a 17-year-old hacker and accomplices set up a fake website resembling Twitter's internal VPN
Virtual private network (VPN) is a network architecture for virtually extending a private network (i.e. any computer network which is not the public Internet) across one or multiple other networks which are either untrusted (as they are not c ...
provider used by remote working employees. Posing as helpdesk staff, they called multiple Twitter employees, directing them to submit their credentials to the fake VPN website. Using the details supplied by the unsuspecting employees, they were able to seize control of several high-profile user accounts, including those of Barack Obama
Barack Hussein Obama II (born August 4, 1961) is an American politician who was the 44th president of the United States from 2009 to 2017. A member of the Democratic Party, he was the first African American president in American history. O ...
, Elon Musk
Elon Reeve Musk ( ; born June 28, 1971) is a businessman. He is known for his leadership of Tesla, SpaceX, X (formerly Twitter), and the Department of Government Efficiency (DOGE). Musk has been considered the wealthiest person in th ...
, Joe Biden
Joseph Robinette Biden Jr. (born November 20, 1942) is an American politician who was the 46th president of the United States from 2021 to 2025. A member of the Democratic Party (United States), Democratic Party, he served as the 47th vice p ...
, and Apple Inc.
Apple Inc. is an American multinational corporation and technology company headquartered in Cupertino, California, in Silicon Valley. It is best known for its consumer electronics, software, and services. Founded in 1976 as Apple Comput ...
's company account. The hackers then sent messages to Twitter followers soliciting Bitcoin
Bitcoin (abbreviation: BTC; Currency symbol, sign: â‚¿) is the first Decentralized application, decentralized cryptocurrency. Based on a free-market ideology, bitcoin was invented in 2008 when an unknown entity published a white paper under ...
, promising to double the transaction value in return. The hackers collected 12.86 BTC (about $117,000 at the time). In the 2020s, phishing as a service (PhaaS) platforms like Darcula allow attackers to easily fake trusted websites.
Anti-phishing
There are anti-phishing websites which publish exact messages that have been recently circulating the internet, such as FraudWatch International and Millersmiles. Such sites often provide specific details about the particular messages. As recently as 2007, the adoption of anti-phishing strategies by businesses needing to protect personal and financial information was low. There are several different techniques to combat phishing, including legislation and technology created specifically to protect against phishing. These techniques include steps that can be taken by individuals, as well as by organizations. Phone, web site, and email phishing can now be reported to authorities, as describedbelow
Below may refer to:
*Earth
*Ground (disambiguation)
*Soil
*Floor
* Bottom (disambiguation)
*Less than
*Temperatures below freezing
*Hell or underworld
People with the surname
* Ernst von Below (1863–1955), German World War I general
* Fred Belo ...
.
User training
 Effective phishing education, including conceptual knowledge and feedback, is an important part of any organization's anti-phishing strategy. While there is limited data on the effectiveness of education in reducing susceptibility to phishing, much information on the threat is available online.
Simulated phishing campaigns, in which organizations test their employees' training by sending fake phishing emails, are commonly used to assess their effectiveness. One example is a study by the
Effective phishing education, including conceptual knowledge and feedback, is an important part of any organization's anti-phishing strategy. While there is limited data on the effectiveness of education in reducing susceptibility to phishing, much information on the threat is available online.
Simulated phishing campaigns, in which organizations test their employees' training by sending fake phishing emails, are commonly used to assess their effectiveness. One example is a study by the National Library of Medicine
The United States National Library of Medicine (NLM), operated by the United States federal government, is the world's largest medical library.
Located in Bethesda, Maryland, the NLM is an institute within the National Institutes of Health. I ...
, in which an organization received 858,200 emails during a 1-month testing period, with 139,400 (16%) being marketing and 18,871 (2%) being identified as potential threats. These campaigns are often used in the healthcare industry, as healthcare data is a valuable target for hackers. These campaigns are just one of the ways that organizations are working to combat phishing.
Nearly all legitimate e-mail messages from companies to their customers contain an item of information that is not readily available to phishers. Some companies, for example PayPal
PayPal Holdings, Inc. is an American multinational financial technology company operating an online payments system in the majority of countries that support E-commerce payment system, online money transfers; it serves as an electronic alter ...
, always address their customers by their username in emails, so if an email addresses the recipient in a generic fashion ("Dear PayPal customer") it is likely to be an attempt at phishing. Furthermore, PayPal offers various methods to determine spoof emails and advises users to forward suspicious emails to their spoof@PayPal.com domain to investigate and warn other customers. However it is unsafe to assume that the presence of personal information alone guarantees that a message is legitimate, and some studies have shown that the presence of personal information does not significantly affect the success rate of phishing attacks; which suggests that most people do not pay attention to such details.
Emails from banks and credit card companies often include partial account numbers, but research has shown that people tend to not differentiate between the first and last digits.
A study on phishing attacks in game environments found that educational game
Educational games are games explicitly designed with educational purposes, or which have incidental or secondary educational value. All types of games may be used in an educational environment, however educational games are games that are design ...
s can effectively educate players against information disclosures and can increase awareness on phishing risk thus mitigating risks.
The Anti-Phishing Working Group
The Anti-Phishing Working Group (APWG) is an international consortium focused on providing guidance and collecting data to reduce the risks of fraud and identity theft caused by phishing and related incidents. It was founded in 2003 by a US-based ...
, one of the largest anti-phishing organizations in the world, produces regular report on trends in phishing attacks.
Technical approaches
A wide range of technical approaches are available to prevent phishing attacks reaching users or to prevent them from successfully capturing sensitive information.Filtering out phishing mail
Specialized spam filters can reduce the number of phishing emails that reach their addressees' inboxes. These filters use a number of techniques includingmachine learning
Machine learning (ML) is a field of study in artificial intelligence concerned with the development and study of Computational statistics, statistical algorithms that can learn from data and generalise to unseen data, and thus perform Task ( ...
and natural language processing
Natural language processing (NLP) is a subfield of computer science and especially artificial intelligence. It is primarily concerned with providing computers with the ability to process data encoded in natural language and is thus closely related ...
approaches to classify phishing emails, and reject email with forged addresses.
Browsers alerting users to fraudulent websites
 Another popular approach to fighting phishing is to maintain a list of known phishing sites and to check websites against the list. One such service is the Safe Browsing service. Web browsers such as
Another popular approach to fighting phishing is to maintain a list of known phishing sites and to check websites against the list. One such service is the Safe Browsing service. Web browsers such as Google Chrome
Google Chrome is a web browser developed by Google. It was first released in 2008 for Microsoft Windows, built with free software components from Apple WebKit and Mozilla Firefox. Versions were later released for Linux, macOS, iOS, iPadOS, an ...
, Internet Explorer
Internet Explorer (formerly Microsoft Internet Explorer and Windows Internet Explorer, commonly abbreviated as IE or MSIE) is a deprecation, retired series of graphical user interface, graphical web browsers developed by Microsoft that were u ...
7, Mozilla Firefox
Mozilla Firefox, or simply Firefox, is a free and open-source web browser developed by the Mozilla Foundation and its subsidiary, the Mozilla Corporation. It uses the Gecko rendering engine to display web pages, which implements curren ...
2.0, Safari
A safari (; originally ) is an overland journey to observe wildlife, wild animals, especially in East Africa. The so-called big five game, "Big Five" game animals of Africa – lion, African leopard, leopard, rhinoceros, African elephant, elep ...
3.2, and Opera
Opera is a form of History of theatre#European theatre, Western theatre in which music is a fundamental component and dramatic roles are taken by Singing, singers. Such a "work" (the literal translation of the Italian word "opera") is typically ...
all contain this type of anti-phishing measure. Firefox 2 used Google
Google LLC (, ) is an American multinational corporation and technology company focusing on online advertising, search engine technology, cloud computing, computer software, quantum computing, e-commerce, consumer electronics, and artificial ...
anti-phishing software. Opera 9.1 uses live blacklists from Phishtank, cyscon and GeoTrust
GeoTrust is a digital certificate provider. The GeoTrust brand was bought by Symantec from Verisign in 2010, but agreed to sell the certificate business (including GeoTrust) in August 2017 to private equity and growth capital firm Thoma Bravo L ...
, as well as live whitelist
A whitelist or allowlist is a list or register of entities that are being provided a particular privilege, service, mobility, access or recognition. Entities on the list will be accepted, approved and/or recognized. Whitelisting is the reverse of ...
s from GeoTrust. Some implementations of this approach send the visited URLs to a central service to be checked, which has raised concerns about privacy
Privacy (, ) is the ability of an individual or group to seclude themselves or information about themselves, and thereby express themselves selectively.
The domain of privacy partially overlaps with security, which can include the concepts of a ...
. According to a report by Mozilla in late 2006, Firefox 2 was found to be more effective than Internet Explorer 7
Windows Internet Explorer 7 (IE7) (codenamed Rincon) is a version of Internet Explorer, a web browser for Windows. It was released by Microsoft on October 18, 2006. It was the first major update to the browser since 2001. It does not support ve ...
at detecting fraudulent sites in a study by an independent software testing company.
An approach introduced in mid-2006 involves switching to a special DNS service that filters out known phishing domains.
To mitigate the problem of phishing sites impersonating a victim site by embedding its images (such as logo
A logo (abbreviation of logotype; ) is a graphic mark, emblem, or symbol used to aid and promote public identification and recognition. It may be of an abstract or figurative design or include the text of the name that it represents, as in ...
s), several site owners have altered the images to send a message to the visitor that a site may be fraudulent. The image may be moved to a new filename and the original permanently replaced, or a server can detect that the image was not requested as part of normal browsing, and instead send a warning image.
Augmenting password logins
TheBank of America
The Bank of America Corporation (Bank of America) (often abbreviated BofA or BoA) is an American multinational investment banking, investment bank and financial services holding company headquartered at the Bank of America Corporate Center in ...
website was one of several that asked users to select a personal image (marketed as SiteKey) and displayed this user-selected image with any forms that request a password. Users of the bank's online services were instructed to enter a password only when they saw the image they selected. The bank has since discontinued the use of SiteKey. Several studies suggest that few users refrain from entering their passwords when images are absent. In addition, this feature (like other forms of two-factor authentication
Multi-factor authentication (MFA; two-factor authentication, or 2FA) is an electronic authentication method in which a user is granted access to a website or Application software, application only after successfully presenting two or more distin ...
) is susceptible to other attacks, such as those suffered by Scandinavian bank Nordea
Nordea Bank Abp, commonly referred to as Nordea, is a Nordic financial services group operating in northern Europe with headquarters in Helsinki, Finland. The name is a blend of the words "Nordic" and "idea". The Nordic countries are considered ...
in late 2005, and Citibank
Citibank, N.A. ("N. A." stands for "National bank (United States), National Association"; stylized as citibank) is the primary U.S. banking subsidiary of Citigroup, a financial services multinational corporation, multinational corporation. Ci ...
in 2006.
A similar system, in which an automatically generated "Identity Cue" consisting of a colored word within a colored box is displayed to each website user, is in use at other financial institutions.
Security skins are a related technique that involves overlaying a user-selected image onto the login form as a visual cue that the form is legitimate. Unlike the website-based image schemes, however, the image itself is shared only between the user and the browser, and not between the user and the website. The scheme also relies on a mutual authentication
Mutual authentication or two-way authentication (not to be confused with two-factor authentication) refers to two parties authenticating each other at the same time in an authentication protocol. It is a default mode of authentication in some prot ...
protocol, which makes it less vulnerable to attacks that affect user-only authentication schemes.
Still another technique relies on a dynamic grid of images that is different for each login attempt. The user must identify the pictures that fit their pre-chosen categories (such as dogs, cars and flowers). Only after they have correctly identified the pictures that fit their categories are they allowed to enter their alphanumeric password to complete the login. Unlike the static images used on the Bank of America website, a dynamic image-based authentication method creates a one-time passcode for the login, requires active participation from the user, and is very difficult for a phishing website to correctly replicate because it would need to display a different grid of randomly generated images that includes the user's secret categories.
Monitoring and takedown
Several companies offer banks and other organizations likely to suffer from phishing scams round-the-clock services to monitor, analyze and assist in shutting down phishing websites. Automated detection of phishing content is still below accepted levels for direct action, with content-based analysis reaching between 80% and 90% of success so most of the tools include manual steps to certify the detection and authorize the response. Individuals can contribute by reporting phishing to both volunteer and industry groups, such as cyscon or PhishTank. Phishing web pages and emails can be reported to Google.Multi-factor authentication
Organizations can implement two factor ormulti-factor authentication
Multi-factor authentication (MFA; two-factor authentication, or 2FA) is an electronic authentication method in which a user is granted access to a website or application only after successfully presenting two or more distinct types of evidence ...
(MFA), which requires a user to use at least 2 factors when logging in. (For example, a user must both present a smart card
A smart card (SC), chip card, or integrated circuit card (ICC or IC card), is a card used to control access to a resource. It is typically a plastic credit card-sized card with an Embedded system, embedded integrated circuit (IC) chip. Many smart ...
and a password
A password, sometimes called a passcode, is secret data, typically a string of characters, usually used to confirm a user's identity. Traditionally, passwords were expected to be memorized, but the large number of password-protected services t ...
). This mitigates some risk, in the event of a successful phishing attack, the stolen password on its own cannot be reused to further breach the protected system. However, there are several attack methods which can defeat many of the typical systems. MFA schemes such as WebAuthn
Web Authentication (WebAuthn) is a web standard published by the World Wide Web Consortium (W3C).
Its primary purpose is to build a system of authentication for web-based applications that solves or mitigates the issues of traditional passwo ...
address this issue by design.
Legal responses
On January 26, 2004, the U.S.Federal Trade Commission
The Federal Trade Commission (FTC) is an independent agency of the United States government whose principal mission is the enforcement of civil (non-criminal) United States antitrust law, antitrust law and the promotion of consumer protection. It ...
filed the first lawsuit against a California
California () is a U.S. state, state in the Western United States that lies on the West Coast of the United States, Pacific Coast. It borders Oregon to the north, Nevada and Arizona to the east, and shares Mexico–United States border, an ...
n teenager suspected of phishing by creating a webpage mimicking America Online
AOL (formerly a company known as AOL Inc. and originally known as America Online) is an American web portal and online service provider based in New York City, and a brand marketed by Yahoo! Inc. (2017–present), Yahoo! Inc.
The service tra ...
and stealing credit card information. Other countries have followed this lead by tracing and arresting phishers. A phishing kingpin, Valdir Paulo de Almeida, was arrested in Brazil
Brazil, officially the Federative Republic of Brazil, is the largest country in South America. It is the world's List of countries and dependencies by area, fifth-largest country by area and the List of countries and dependencies by population ...
for leading one of the largest phishing crime rings, which in two years stole between and . UK authorities jailed two men in June 2005 for their role in a phishing scam, in a case connected to the U.S. Secret Service Operation Firewall, which targeted notorious "carder" websites. In 2006, Japanese police arrested eight people for creating fake Yahoo Japan websites, netting themselves () and the FBI
The Federal Bureau of Investigation (FBI) is the domestic Intelligence agency, intelligence and Security agency, security service of the United States and Federal law enforcement in the United States, its principal federal law enforcement ag ...
detained a gang of sixteen in the U.S. and Europe in Operation Cardkeeper.
Senator Patrick Leahy
Patrick Joseph Leahy ( ; born March 31, 1940) is an American politician and attorney who represented Vermont in the United States Senate from 1975 to 2023. A member of the Democratic Party (United States), Democratic Party, he also was the pr ...
introduced the Anti-Phishing Act of 2005 to Congress
A congress is a formal meeting of the representatives of different countries, constituent states, organizations, trade unions, political parties, or other groups. The term originated in Late Middle English to denote an encounter (meeting of ...
in the United States
The United States of America (USA), also known as the United States (U.S.) or America, is a country primarily located in North America. It is a federal republic of 50 U.S. state, states and a federal capital district, Washington, D.C. The 48 ...
on March 1, 2005. This bill aimed to impose fines of up to $250,000 and prison sentences of up to five years on criminals who used fake websites and emails to defraud consumers. In the UK, the Fraud Act 2006
The Fraud Act 2006 (c 35) is an Act of the Parliament of the United Kingdom which affects England and Wales and Northern Ireland. It was given royal assent on 8 November 2006, and came into effect on 15 January 2007.
Purpose
The Act gives a sta ...
introduced a general offense of fraud punishable by up to ten years in prison and prohibited the development or possession of phishing kits with the intention of committing fraud.
Companies have also joined the effort to crack down on phishing. On March 31, 2005, Microsoft
Microsoft Corporation is an American multinational corporation and technology company, technology conglomerate headquartered in Redmond, Washington. Founded in 1975, the company became influential in the History of personal computers#The ear ...
filed 117 federal lawsuits in the U.S. District Court for the Western District of Washington. The lawsuits accuse "John Doe
John Doe (male) and Jane Doe (female) are multiple-use placeholder names that are used in the British, Canadian, and American legal systems, when the true name of a person is unknown or is being intentionally concealed. In the context of law ...
" defendants of obtaining passwords and confidential information. March 2005 also saw a partnership between Microsoft and the Australian government
The Australian Government, also known as the Commonwealth Government or simply as the federal government, is the national executive government of Australia, a federal parliamentary constitutional monarchy. The executive consists of the pr ...
teaching law enforcement officials how to combat various cyber crimes, including phishing. Microsoft announced a planned further 100 lawsuits outside the U.S. in March 2006, followed by the commencement, as of November 2006, of 129 lawsuits mixing criminal and civil actions. AOL reinforced its efforts against phishing in early 2006 with three lawsuits seeking a total of under the 2005 amendments to the Virginia Computer Crimes Act, and Earthlink
EarthLink is an American Internet service provider.
Earthlink went public on NASDAQ in January 1997. Much of the company's growth was via acquisition. In 2000, ''The New York Times'' described it as the "second largest Internet service provider ...
has joined in by helping to identify six men subsequently charged with phishing fraud in Connecticut
Connecticut ( ) is a U.S. state, state in the New England region of the Northeastern United States. It borders Rhode Island to the east, Massachusetts to the north, New York (state), New York to the west, and Long Island Sound to the south. ...
.
In January 2007, Jeffrey Brett Goodin of California became the first defendant convicted by a jury under the provisions of the CAN-SPAM Act of 2003
The Controlling the Assault of Non-Solicited Pornography And Marketing (CAN-SPAM) Act of 2003 is a law passed in 2003 establishing the United States' first national standards for the sending of commercial e-mail. The law requires the Federal Tra ...
. He was found guilty of sending thousands of emails to AOL users, while posing as the company's billing department, which prompted customers to submit personal and credit card information. Facing a possible 101 years in prison for the CAN-SPAM violation and ten other counts including wire fraud
Mail fraud and wire fraud are terms used in the United States to describe the use of a physical (e.g., the U.S. Postal Service) or electronic (e.g., a phone, a telegram, a fax, or the Internet) mail system to defraud another, and are U.S. fede ...
, the unauthorized use of credit cards, and the misuse of AOL's trademark, he was sentenced to serve 70 months. Goodin had been in custody since failing to appear for an earlier court hearing and began serving his prison term immediately.
Notable incidents
* 2016–2021 literary phishing theftsSee also
* * *Clickjacking
Clickjacking (classified as a user interface redress attack or UI redressing) is a Malware, malicious technique of tricking a User (computing), user into clicking on something different from what the user perceives, thus potentially revealing Con ...
*
*
* Trojan Horse
In Greek mythology, the Trojan Horse () was a wooden horse said to have been used by the Greeks during the Trojan War to enter the city of Troy and win the war. The Trojan Horse is not mentioned in Homer, Homer's ''Iliad'', with the poem ending ...
*
References
External links
Anti-Phishing Working Group
Center for Identity Management and Information Protection
– Utica College
Plugging the "phishing" hole: legislation versus technology
() – '' Duke Law & Technology Review''
Example of a Phishing Attempt with Screenshots and Explanations
– StrategicRevenue.com
A Profitless Endeavor: Phishing as Tragedy of the Commons
– Microsoft Corporation
Database for information on phishing sites reported by the public
– PhishTank
The Impact of Incentives on Notice and Take-down
− Computer Laboratory, University of Cambridge (PDF, 344 kB) {{Authority control Confidence tricks Cybercrime Deception Fraud Identity theft Internet terminology Organized crime activity Social engineering (security) Spamming Types of cyberattacks