Nethack Falcons Eye Class Selection on:
[Wikipedia]
[Google]
[Amazon]
''NetHack'' is an
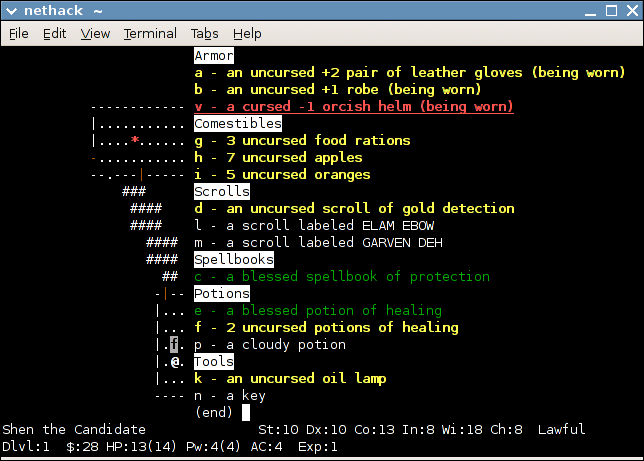 ''NetHack'' features a variety of items:
''NetHack'' features a variety of items: ' s identification of items is almost identical to '' Rogue''' s. For example, a newly discovered potion may be referred to as a "pink potion" with no other clues as to its identity. Players can perform a variety of actions and tricks to deduce, or at least narrow down, the identity of the potion. The most obvious is the somewhat risky tactic of simply drinking it. All items of a certain type will have the same description. For instance, all "scrolls of enchant weapon" may be labeled "TEMOV", and once one has been identified, all "scrolls of enchant weapon" found later will be labeled unambiguously as such. Starting a new game will scramble the items' descriptions again, so the "silver ring" that is a "ring of levitation" in one game might be a "ring of hunger" in another.
File:NetHack for Windows Screenshot.png, ''NetHack'' for Microsoft Windows in "tiles mode"
File:Vultures-2.1.0 screenshot.jpg, ''Vulture's Eye'' offers an isometric perspective.
File:NeXTSTEP Nethack.png, ''NetHack'' on
A Guide to the Mazes of Menace (Guidebook for ''NetHack'')
*
*
The NetHack Wiki
NAO website
/dev/null NetHack Tournament
*
''NetHack''
at SourceForge.net
Hall of Fame – ''NetHack''
at
open source
Open source is source code that is made freely available for possible modification and redistribution. Products include permission to use and view the source code, design documents, or content of the product. The open source model is a decentrali ...
single-player roguelike
Roguelike (or rogue-like) is a style of role-playing game traditionally characterized by a dungeon crawl through procedurally generated levels, turn-based gameplay, grid-based movement, and permanent death of the player character. Most ro ...
video game
A video game or computer game is an electronic game that involves interaction with a user interface or input device (such as a joystick, game controller, controller, computer keyboard, keyboard, or motion sensing device) to generate visual fe ...
, first released in 1987 and maintained by the NetHack DevTeam. The game is a fork
In cutlery or kitchenware, a fork (from 'pitchfork') is a utensil, now usually made of metal, whose long handle terminates in a head that branches into several narrow and often slightly curved tines with which one can spear foods either to h ...
of the 1984 game ''Hack
Hack may refer to:
Arts, entertainment, and media Games
* Hack (Unix video game), ''Hack'' (Unix video game), a 1984 roguelike video game
* .hack (video game series), ''.hack'' (video game series), a series of video games by the multimedia fran ...
'', itself inspired by the 1980 game '' Rogue''. The player takes the role of one of several pre-defined character class
In tabletop games and video games, a character class is an occupation, profession, or role assigned to a game character to highlight and differentiate their capabilities and specializations.
In role-playing games (RPGs), character classes ag ...
es to descend through multiple dungeon floors, fighting monsters and collecting treasure, to recover the "Amulet of Yendor" at the lowest floor and then escape.
As an exemplar of the traditional "roguelike" game, ''NetHack'' features turn-based
Timekeeping is relevant to many types of games, including video games, tabletop role-playing games, board games, and sports. The passage of time must be handled in a way that players find fair and easy to understand. In many games, this is don ...
, grid-based hack and slash
Hack and slash, also known as hack and slay (H&S or HnS) or slash 'em up, refers to a type of gameplay that emphasizes combat with melee-based weapons (such as swords or blades). They may also feature projectile-based weapons as well (such as ...
and dungeon crawl
A dungeon crawl is a type of scenario in fantasy role-playing games (RPGs) in which heroes navigate a labyrinth environment (a "dungeon"), battling various monsters, avoiding traps, solving puzzles, and looting any treasure they may find. Video g ...
ing gameplay, procedurally generated
In computing, procedural generation is a method of creating data algorithmically as opposed to manually, typically through a combination of human-generated content and algorithms coupled with computer-generated randomness and processing power. I ...
dungeons and treasure, and permadeath
Permadeath or permanent death is a game mechanic in both tabletop games and video games in which player characters who lose all of their health are considered dead and cannot be used anymore. Depending on the situation, this could require the p ...
, requiring the player to restart the game anew should the player character
A player character (also known as a playable character or PC) is a fictional Character (arts), character in a video game or tabletop role-playing game whose actions are controlled by a player rather than the rules of the game. The characters tha ...
die. The game uses simple ASCII
ASCII ( ), an acronym for American Standard Code for Information Interchange, is a character encoding standard for representing a particular set of 95 (English language focused) printable character, printable and 33 control character, control c ...
graphics by default so as to display readily on a wide variety of computer displays
A computer monitor is an output device that displays information in pictorial or textual form. A discrete monitor comprises a electronic visual display, visual display, support electronics, power supply, Housing (engineering), housing, electri ...
, but can use curses
A curse (also called an imprecation, malediction, execration, malison, anathema, or commination) is any expressed wish that some form of adversity or misfortune will befall or attach to one or more persons, a place, or an object. In particular ...
with box-drawing character
Box-drawing characters, also known as line-drawing characters, are a form of semigraphics widely used in text user interfaces to draw various geometric frames and boxes. These characters are characterized by being designed to be connected horiz ...
s, as well as substitute graphical tilesets on machines with graphics. While ''Rogue'', ''Hack'' and other earlier roguelikes stayed true to a high fantasy
High fantasy, or epic fantasy, is a subgenre of fantasy defined by the epic nature of its setting or by the epic stature of its characters, themes, or plot. Brian Stableford, ''The A to Z of Fantasy Literature'', (p. 198), Scarecrow Pres ...
setting, ''NetHack'' introduced humorous and anachronistic
An anachronism (from the Greek , 'against' and , 'time') is a chronological inconsistency in some arrangement, especially a juxtaposition of people, events, objects, language terms and customs from different time periods. The most common typ ...
elements over time, including popular cultural reference to works such as ''Discworld
''Discworld'' is a comic fantasy"Humorous Fantasy" in David Pringle, ed., ''The Ultimate Encyclopedia of Fantasy'' (pp.31-33). London, Carlton,2006. book series written by the English author Sir Terry Pratchett, set on the Discworld, a fl ...
'' and ''Raiders of the Lost Ark
''Raiders of the Lost Ark'' is a 1981 American action-adventure film directed by Steven Spielberg and written by Lawrence Kasdan, based on a story by George Lucas and Philip Kaufman. Set in 1936, the film stars Harrison Ford as Indiana ...
''.
It is identified as one of the "major roguelikes" by John Harris. Comparing it with ''Rogue'', ''Engadget
Engadget ( ) is a technology news, reviews and analysis website offering daily coverage of gadgets, consumer electronics, video games, gaming hardware, apps, social media, streaming, AI, space, robotics, electric vehicles and other potentially ...
''s Justin Olivetti wrote that it took its exploration aspect and "made it far richer with an encyclopedia of objects, a larger vocabulary, a wealth of pop culture mentions, and a puzzler's attitude." In 2000, ''Salon
Salon may refer to:
Common meanings
* Beauty salon
A beauty salon or beauty parlor is an establishment that provides Cosmetics, cosmetic treatments for people. Other variations of this type of business include hair salons, spas, day spas, ...
'' described it as "one of the finest gaming experiences the computing world has to offer".
Gameplay
Before starting a game, players choose their character's race,role
A role (also rôle or social role) is a set of connected behaviors, rights, obligations, beliefs, and norms as conceptualized by people in a social situation. It is an
expected or free or continuously changing behavior and may have a given indi ...
, sex
Sex is the biological trait that determines whether a sexually reproducing organism produces male or female gametes. During sexual reproduction, a male and a female gamete fuse to form a zygote, which develops into an offspring that inheri ...
, and alignment
Alignment may refer to:
Archaeology
* Alignment (archaeology), a co-linear arrangement of features or structures with external landmarks
* Stone alignment, a linear arrangement of upright, parallel megalithic standing stones
Biology
* Struc ...
, or allow the game to assign the attributes randomly. There are traditional fantasy roles such as knight
A knight is a person granted an honorary title of a knighthood by a head of state (including the pope) or representative for service to the monarch, the church, or the country, especially in a military capacity.
The concept of a knighthood ...
, wizard, rogue, and priest
A priest is a religious leader authorized to perform the sacred rituals of a religion, especially as a mediatory agent between humans and one or more deity, deities. They also have the authority or power to administer religious rites; in parti ...
; but there are also unusual roles, including archaeologist
Archaeology or archeology is the study of human activity through the recovery and analysis of material culture. The archaeological record consists of Artifact (archaeology), artifacts, architecture, biofact (archaeology), biofacts or ecofacts, ...
, tourist
Tourism is travel for pleasure, and the commercial activity of providing and supporting such travel. UN Tourism defines tourism more generally, in terms which go "beyond the common perception of tourism as being limited to holiday activity on ...
, and caveman
The caveman is a stock character representative of primitive humans in the Paleolithic. The popularization of the type dates to the early 20th century, when Neanderthals were influentially described as " simian" or " ape-like" by Marcellin B ...
. The player character
A player character (also known as a playable character or PC) is a fictional Character (arts), character in a video game or tabletop role-playing game whose actions are controlled by a player rather than the rules of the game. The characters tha ...
's role and alignment dictate which deity
A deity or god is a supernatural being considered to be sacred and worthy of worship due to having authority over some aspect of the universe and/or life. The ''Oxford Dictionary of English'' defines ''deity'' as a God (male deity), god or god ...
the character serves and is supported by in the game, "how other monsters react toward you", as well as character skills and attributes.
After the player character is created, the main objective is introduced. To win the game, the player must retrieve the Amulet of Yendor, found at the lowest level of the dungeon, and offer it to their deity. Successful completion of this task rewards the player with the gift of immortality
Immortality is the concept of eternal life. Some species possess "biological immortality" due to an apparent lack of the Hayflick limit.
From at least the time of the Ancient Mesopotamian religion, ancient Mesopotamians, there has been a con ...
, and the player is said to "ascend", attaining the status of demigod
A demigod is a part-human and part-divine offspring of a deity and a human, or a human or non-human creature that is accorded divine status after death, or someone who has attained the "divine spark" (divine illumination). An immortality, immor ...
. Along the path to the amulet, a number of sub-quests must be completed, including one class-specific quest.
There are three major antagonists in NetHack: the Lucifer
The most common meaning for Lucifer in English is as a name for the Devil in Christian theology.
He appeared in the King James Version of the Bible in Isaiah and before that in the Vulgate (the late-4th-century Latin translation of the Bib ...
esque god Moloch
Moloch, Molech, or Molek is a word which appears in the Hebrew Bible several times, primarily in the Book of Leviticus. The Greek Septuagint translates many of these instances as "their king", but maintains the word or name ''Moloch'' in others, ...
, who stole the Amulet of Yendor from the creator god
A creator deity or creator god is a deity responsible for the creation of the Earth, world, and universe in human religion and mythology. In monotheism, the single God is often also the creator. A number of monolatristic traditions separate a ...
Marduk
Marduk (; cuneiform: Dingir, ᵈAMAR.UTU; Sumerian language, Sumerian: "calf of the sun; solar calf"; ) is a god from ancient Mesopotamia and patron deity of Babylon who eventually rose to prominence in the 1st millennium BC. In B ...
; the high priest (or priestess) of Moloch, who holds the Amulet of Yendor; and the most prominent antagonist, the Wizard of Yendor, who will stalk the player throughout the rest of the game after the first encounter by resurrecting and attacking them periodically. The game's final bosses in the Astral Plane
The astral plane, also called the astral realm, or the astral world, or the soul realm, or the spirit realm, is a plane of existence postulated by classical, medieval, oriental, esoteric, and New Age philosophies and mystery religions.G. R. S. ...
are the Riders: three of the Four Horsemen of the Apocalypse
The Four Horsemen of the Apocalypse are figures in the Book of Revelation in the New Testament of the Bible, a piece of apocalypse literature attributed to John of Patmos, and generally regarded as dating from about AD 95. Similar allusions a ...
, Death, Famine and Pestilence. It is often proposed that the player character represents the fourth horseman, War.
The player's character is, unless they opt not to be, accompanied by a pet animal, typically a kitten
A kitten is a Juvenile (organism), juvenile cat. After being born, kittens display primary altriciality and are fully dependent on their mothers for #Establishing immunity, survival. They normally do not open their eyes for seven to ten days. A ...
or little dog, although knights begin with a saddle
A saddle is a supportive structure for a rider of an animal, fastened to an animal's back by a girth. The most common type is equestrian. However, specialized saddles have been created for oxen, camels and other animals.
It is not know ...
d pony
A pony is a type of small horse, usually measured under a specified height at maturity. Ponies often have thicker coats, manes and tails, compared to larger horses, and proportionally shorter legs, wider barrels, heavier , thicker necks and s ...
. Pets grow from fighting, and they can be changed by various means. Most of the other monsters may also be tamed using magic or food.
Dungeon levels
''NetHacks dungeon spans about fifty primary levels, most of which areprocedurally generated
In computing, procedural generation is a method of creating data algorithmically as opposed to manually, typically through a combination of human-generated content and algorithms coupled with computer-generated randomness and processing power. I ...
when the player character enters them for the first time. A typical level contains a way "up" and "down" to other levels. These may be stairways, ladders, trapdoors, etc. Levels also contain several "rooms" joined by corridors. These rooms are randomly generated rectangles (as opposed to the linear corridors) and may contain features such as altars, shops, fountains, traps, thrones, pools of water, and sinks based on the randomly generated features of the room. Some specific levels follow one of many fixed designs or contain fixed elements. Later versions of the game added special branches of dungeon levels. These are optional routes that may feature more challenging monsters but can reward more desirable treasure to complete the main dungeon. Levels, once generated, persist throughout a single game, in contrast to the non-persistent levels in ''Moria
Moria may refer to:
Arts and entertainment
* Moria (Middle-earth), fictional location in the works of J. R. R. Tolkien
* ''Moria: The Dwarven City'', a 1984 fantasy role-playing game supplement
* Moria (1978 video game), ''Moria'' (1978 video gam ...
''-style games.
Items and tools
 ''NetHack'' features a variety of items:
''NetHack'' features a variety of items: weapon
A weapon, arm, or armament is any implement or device that is used to deter, threaten, inflict physical damage, harm, or kill. Weapons are used to increase the efficacy and efficiency of activities such as hunting, crime (e.g., murder), law ...
s (melee or ranged), armor
Armour (Commonwealth English) or armor (American English; see American and British English spelling differences#-our, -or, spelling differences) is a covering used to protect an object, individual, or vehicle from physical injury or damage, e ...
to protect the player, scroll
A scroll (from the Old French ''escroe'' or ''escroue''), also known as a roll, is a roll of papyrus, parchment, or paper containing writing.
Structure
A scroll is usually partitioned into pages, which are sometimes separate sheets of papyru ...
s and spellbooks to read, potion
A potion is a liquid "that contains medicine, poison, or something that is supposed to have magic powers." It derives from the Latin word ''potio'' which refers to a drink or the act of drinking. The term philtre is also used, often specifica ...
s to quaff, wands, rings, amulets, and an assortment of tool
A tool is an Physical object, object that can extend an individual's ability to modify features of the surrounding environment or help them accomplish a particular task. Although many Tool use by animals, animals use simple tools, only human bei ...
s, such as keys and lamps.
''NetHack''Blessings and curses
As in many other roguelike games, all items in ''NetHack'' are either " blessed", "uncursed", or "curse
A curse (also called an imprecation, malediction, execration, malison, anathema, or commination) is any expressed wish that some form of adversity or misfortune will befall or attach to one or more persons, a place, or an object. In particular, ...
d". The majority of items are found uncursed, but the blessed or cursed status of an item is unknown until it is identified or detected through other means. Such statuses can be changed (blessed to uncursed, uncursed to cursed, and vice versa) depending on player interaction.
Generally, a blessed item will be more powerful than an uncursed item, and a cursed item will be less powerful, with the added disadvantage that once it has been equipped by the player, it cannot be easily unequipped. Where an object would bestow an effect upon the character, a curse will generally make the effect harmful, or increase the amount of harm done. However, there are very specific exceptions. For example, drinking a cursed "potion of gain level" will make the character literally rise through the ceiling to the level above, instead of gaining an experience level
An experience point (often abbreviated as exp or XP) is a unit of measurement used in some tabletop role-playing games (RPGs) and role-playing video games to quantify a player character's life experience and progression through the game. Experien ...
.
Character death
As in other roguelike games, ''NetHack'' featurespermadeath
Permadeath or permanent death is a game mechanic in both tabletop games and video games in which player characters who lose all of their health are considered dead and cannot be used anymore. Depending on the situation, this could require the p ...
: expired characters cannot be revived.
Although ''NetHack'' can be completed without any artificial limitations, experienced players can attempt "conducts" for an additional challenge. These are voluntary restrictions on actions taken, such as using no wishes, following a vegetarian
Vegetarianism is the practice of abstaining from the Eating, consumption of meat (red meat, poultry, seafood, insects as food, insects, and the flesh of any other animal). It may also include abstaining from eating all by-products of animal slau ...
or vegan
Veganism is the practice of abstaining from the use of animal products and the consumption of animal source foods, and an associated philosophy that rejects the commodity status of animals. A person who practices veganism is known as a ve ...
diet, or even killing no monsters. While conducts are generally tracked by the game and are displayed at death or ascension, unofficial conducts are practiced within the community.
When a player dies, the cause of death and score is created and added to the list where the player's character is ranked against other previous characters. The prompt "Do you want your possessions identified?" is given by default at the end of any game, allowing the player to learn any unknown properties of the items in their inventory at death. The player's attributes (such as resistances, luck, and others), conduct (usually self-imposed challenges, such as playing as an atheist or a vegetarian), and a tally of creatures killed, may also be displayed.
The game sporadically saves a level on which a character has died and then integrates that level into a later game. This is done via "bones files", which are saved on the computer hosting the game. A player using a publicly hosted copy of the game can thus encounter the remains and possessions of many other players, although many of these possessions may have become cursed.
Because of the numerous ways that a player-character could die between a combination of their own actions as well as from reactions from the game's interacting systems, players frequently refer to untimely deaths as "Yet Another Stupid Death" (YASD). Such deaths are considered part of learning to play ''NetHack'' as to avoid conditions where the same death may happen again.
''NetHack'' does allow players to save the game so that one does not have to complete the game in one session, but on opening a new game, the previous save file is subsequently wiped as to enforce the permadeath option. One option some players use is to make a backup copy of the save game file before playing a game, and, should their character die, restoring from the copied version, a practice known as "save scumming". Additionally, players can also manipulate the "bones files" in a manner not intended by the developers. While these help the player to learn the game and get around limits of permadeath, both are considered forms of cheating the game.
Culture around spoilers
''NetHack'' is largely based on discovering secrets and tricks during gameplay. It can take years for one to become well-versed in them, and even experienced players routinely discover new ones. A number of ''NetHack'' fan sites and discussion forums offer lists of game secrets known as "spoilers".Interface
''NetHack'' was originally created with only a simple ASCIItext-based user interface
In computing, text-based user interfaces (TUI) (alternately terminal user interfaces, to reflect a dependence upon the properties of computer terminals and not just text), is a retronym describing a type of user interface (UI) common as an ear ...
, although the option to use something more elaborate was added later in its development. Interface elements such as the environment, entities, and objects are represented by arrangements of ASCII
ASCII ( ), an acronym for American Standard Code for Information Interchange, is a character encoding standard for representing a particular set of 95 (English language focused) printable character, printable and 33 control character, control c ...
or Extended ASCII
Extended ASCII is a repertoire of character encodings that include (most of) the original 96 ASCII character set, plus up to 128 additional characters. There is no formal definition of "extended ASCII", and even use of the term is sometimes critic ...
glyphs, " DECgraphics", or " IBMgraphics" mode. In addition to the environment, the interface also displays character and situational information.
A detailed example:
You see here a silver ring.
------------
##....._.....,
, ...........# ------
#..........., , ....,
--------------- ###------------ , ...(,
, ..%..........., ########## ###-@...,
, ...%...........### # ## , ....,
+.......<......, ### ### , ..!.,
--------------- # # ------
### ###
# #
---.----- ###
, ......., #
, ........####
, .......,
, .......,
---------
Hacker the Conjurer St:11 Dx:13 Co:12 In:11 Wi:18 Ch:11 Neutral
Dlvl:3 $:120 HP:39(41) Pw:36(36) AC:6 Exp:5 T:1073
The player (the '@' sign, a wizard in this case) has entered the level via the stairs (the '<' sign) and killed a few monsters, leaving their corpses (the '%' signs) behind. Exploring, the player has uncovered three rooms joined by corridors (the '#' signs): one with an altar (the '_' sign), another empty, and the final one (that the player is currently in) containing a potion (the '!' sign) and chest (the '(' sign). The player has just moved onto a square containing a silver ring. Parts of the level are still unexplored (probably accessible through the door to the west (the '+' sign)) and the player has yet to find the downstairs (a '>' sign) to the next level.
Apart from the original termcap
Termcap ("terminal capability") is a legacy software library (computing), library and database used on Unix-like computers that enables programs to use display computer terminals in a terminal-independent manner, which greatly simplifies the proc ...
interface shown above, there are other interfaces that replace standard screen representations with two-dimensional
A two-dimensional space is a mathematical space with two dimensions, meaning points have two degrees of freedom: their locations can be locally described with two coordinates or they can move in two independent directions. Common two-dimension ...
images, or tiles
Tiles are usually thin, square or rectangular coverings manufactured from hard-wearing material such as ceramic, stone, metal, baked clay, or even glass. They are generally fixed in place in an array to cover roofs, floors, walls, edges, or ot ...
, collectively known as "tiles mode". Graphic interfaces of this kind have been successfully implemented on the Amiga
Amiga is a family of personal computers produced by Commodore International, Commodore from 1985 until the company's bankruptcy in 1994, with production by others afterward. The original model is one of a number of mid-1980s computers with 16-b ...
, the X Window System
The X Window System (X11, or simply X) is a windowing system for bitmap displays, common on Unix-like operating systems.
X originated as part of Project Athena at Massachusetts Institute of Technology (MIT) in 1984. The X protocol has been at ...
, the Microsoft Windows
Windows is a Product lining, product line of Proprietary software, proprietary graphical user interface, graphical operating systems developed and marketed by Microsoft. It is grouped into families and subfamilies that cater to particular sec ...
GUI, the Qt toolkit
Qt ( pronounced "cute") is a cross-platform application development framework for creating graphical user interfaces as well as Cross-platform software, cross-platform applications that run on various software and hardware platforms such as L ...
, and the GNOME
A gnome () is a mythological creature and diminutive spirit in Renaissance magic and alchemy, introduced by Paracelsus in the 16th century and widely adopted by authors, including those of modern fantasy literature. They are typically depict ...
libraries.
Enhanced graphical options also exist, such as the isometric perspective of '' Falcon's Eye'' and ''Vulture's Eye'', or the three-dimensional
In geometry, a three-dimensional space (3D space, 3-space or, rarely, tri-dimensional space) is a mathematical space in which three values (''coordinates'') are required to determine the position (geometry), position of a point (geometry), poi ...
rendering that noegnud offers. ''Vulture's Eye'' is a fork
In cutlery or kitchenware, a fork (from 'pitchfork') is a utensil, now usually made of metal, whose long handle terminates in a head that branches into several narrow and often slightly curved tines with which one can spear foods either to h ...
of the now defunct Falcon's Eye project. ''Vulture's Eye'' adds additional graphics, sounds, bug fixes and performance enhancements and is under active development in an open collaborative environment.
OPENSTEP
OpenStep is an object-oriented application programming interface (API) specification developed by NeXT. It provides a framework for building graphical user interfaces (GUIs) and developing software applications. OpenStep was designed to be plat ...
/NeXTSTEP
NeXTSTEP is a discontinued object-oriented, multitasking operating system based on the Mach kernel and the UNIX-derived BSD. It was developed by NeXT, founded by Steve Jobs, in the late 1980s and early 1990s and was initially used for its ...
History and development
''NetHack'' is a software derivative of ''Hack'', which itself was inspired by ''Rogue''. ''Hack'' was created by students Jay Fenlason, Kenny Woodland, Mike Thome, and Jonathan Payne atLincoln-Sudbury Regional High School
Lincoln-Sudbury Regional High School (LSRHS or LS) is a public regional high school in Sudbury, Massachusetts, with a 99% graduation rate. The school was founded in 1954, and the building was replaced prior to the 2004–2005 academic year, wit ...
as part of a computer class, after seeing and playing ''Rogue'' at the University of California, Berkeley
The University of California, Berkeley (UC Berkeley, Berkeley, Cal, or California), is a Public university, public Land-grant university, land-grant research university in Berkeley, California, United States. Founded in 1868 and named after t ...
computer labs.Craddock 2015, Chapter 5: "When the Inmates Run the Asylum - Hack-ing at Lincoln-Sudbury High School" The group had tried to get the source code of ''Rogue'' from Glenn Wichman and Michael Toy to build upon, but Wichman and Toy had refused, forcing the students to build the dungeon-creation routines on their own. As such, the game was named ''Hack'' in part for the hack-and-slash gameplay and that the code to generate the dungeons was considered a programming hack. After their classes ended, the students' work on the program also ended, though they had a working game. Fenlason provided the source code
In computing, source code, or simply code or source, is a plain text computer program written in a programming language. A programmer writes the human readable source code to control the behavior of a computer.
Since a computer, at base, only ...
to a local USENIX
USENIX is an American 501(c)(3) nonprofit membership organization based in Berkeley, California and founded in 1975 that supports advanced computing systems, operating system (OS), and computer networking research. It organizes several confe ...
conference, and eventually it was uploaded to USENET
Usenet (), a portmanteau of User's Network, is a worldwide distributed discussion system available on computers. It was developed from the general-purpose UUCP, Unix-to-Unix Copy (UUCP) dial-up network architecture. Tom Truscott and Jim Elli ...
newsgroups. The code drew the attention of many players who started working to modify and improve the game as well as port it to other computer systems. ''Hack'' did not have any formal maintainer and while one person was generally recognized to hold the main code to the current version of ''Hack'', many software forks emerged from the unorganized development of the game.
Eventually, Mike Stephenson took on the role as maintainer of the ''Hack'' source code. At this point, he decided to create a new fork of the game, bringing in novel ideas from Izchak Miller, a philosophy professor at University of Pennsylvania
The University of Pennsylvania (Penn or UPenn) is a Private university, private Ivy League research university in Philadelphia, Pennsylvania, United States. One of nine colonial colleges, it was chartered in 1755 through the efforts of f ...
, and Janet Walz, another computer hacker. They called themselves the DevTeam and renamed their branch ''NetHack'' since their collaboration work was done over the Internet.Craddock 2015, Chapter 6: "It Takes a Village: Raising NetHack" They expanded the bestiary and other objects in the game, and drew from other sources outside of the high fantasy setting, such as from ''Discworld
''Discworld'' is a comic fantasy"Humorous Fantasy" in David Pringle, ed., ''The Ultimate Encyclopedia of Fantasy'' (pp.31-33). London, Carlton,2006. book series written by the English author Sir Terry Pratchett, set on the Discworld, a fl ...
'' with the introduction of the tourist character class. Knowing of the multiple forks of ''Hack'' that existed, the DevTeam established a principle that while the game was open source and anyone could create a fork as a new project, only a few select members in the DevTeam could make modifications to the main source repository of the game, so that players could be assured that the DevTeam's release was the legitimate version of ''NetHack''.
Release history
The DevTeam's first release of ''NetHack'' was on 28 July 1987. The core DevTeam had expanded with the release of ''NetHack'' 3.0 in July 1989. By that point, they had established a tight-lipped culture, revealing little, if anything, between releases. Owing to the ever-increasing depth and complexity found in each release, the development team enjoys a near-mythical status among fans. This perceived omniscience is captured in the initialism TDTTOE, "The DevTeam Thinks of Everything", in that many of the possibleemergent gameplay
Emergent gameplay refers to complex situations in video games, board games, or role-playing games that emerge from the interaction of relatively simple game mechanics.
Designers have attempted to encourage emergent play by providing tools to play ...
elements that could occur due to the behavior of the complex game systems had already been programmed in by the DevTeam. Since version 3.0, the DevTeam has typically kept to minor bug fix updates, represented by a change in the third version number (e.g. v3.0.1 over v3.0.0), and only releases major updates (v3.1.0 over v3.0.0) when significant new features are added to the game, including support for new platforms. Many of those from the community that helped with the ports to other systems were subsequently invited to be part of the DevTeam as the team's needs grew, with Stephenson remaining the key member currently.
Updates to the game were generally regular from around 1987 through 2003, with the DevTeam releasing v3.4.3 in December 2003. Subsequent updates from the DevTeam included new tilesets and compatibility with variants of Mac OS, but no major updates to the game had been made. In the absence of new releases from the developers, several community-made updates to the code and variants developed by fans emerged.
On 7 December 2015, version 3.6.0 was released, the first major release in over a decade. While the patch did not add major new gameplay features, the update was designed to prepare the game for expansion in the future, with the DevTeam's patch notes stating: "This release consists of a series of foundational changes in the team, underlying infrastructure and changes to the approach to game development". Stephenson said that despite the number of roguelike titles that had emerged since the v3.4.3 release, they saw that ''NetHack'' was still being talked about online in part due to its high degree of portability, and decided to continue its development. According to DevTeam member Paul Winner, they looked to evaluate what community features had been introduced in the prior decade to improve the game while maintaining the necessary balance. The update came shortly after the death of Terry Pratchett
Sir Terence David John Pratchett (28 April 1948 – 12 March 2015) was an English author, humorist, and Satire, satirist, best known for the ''Discworld'' series of 41 comic fantasy novels published between 1983 and 2015, and for the Apocalyp ...
, whose ''Discworld'' had been influential on the game, and the new update included a tribute to him. With the v3.6.0 release, ''NetHack'' remains "one of the oldest games still being developed".
A public read-only mirror of ''NetHack'' git
Git () is a distributed version control system that tracks versions of files. It is often used to control source code by programmers who are developing software collaboratively.
Design goals of Git include speed, data integrity, and suppor ...
repository was made available on 10 February 2016. Since v3.6.0, the DevTeam has continued to push updates to the title, with the latest being v3.6.7 on 16 February 2023. Version 3.7.0 is currently in development.
, the official source release supports the following systems: Windows
Windows is a Product lining, product line of Proprietary software, proprietary graphical user interface, graphical operating systems developed and marketed by Microsoft. It is grouped into families and subfamilies that cater to particular sec ...
, Linux
Linux ( ) is a family of open source Unix-like operating systems based on the Linux kernel, an kernel (operating system), operating system kernel first released on September 17, 1991, by Linus Torvalds. Linux is typically package manager, pac ...
, macOS
macOS, previously OS X and originally Mac OS X, is a Unix, Unix-based operating system developed and marketed by Apple Inc., Apple since 2001. It is the current operating system for Apple's Mac (computer), Mac computers. With ...
, Windows CE
Windows CE, later known as Windows Embedded CE and Windows Embedded Compact, is a discontinued operating system developed by Microsoft for mobile and embedded devices. It was part of the Windows Embedded family and served as the software foun ...
, OS/2
OS/2 is a Proprietary software, proprietary computer operating system for x86 and PowerPC based personal computers. It was created and initially developed jointly by IBM and Microsoft, under the leadership of IBM software designer Ed Iacobucci, ...
, Unix
Unix (, ; trademarked as UNIX) is a family of multitasking, multi-user computer operating systems that derive from the original AT&T Unix, whose development started in 1969 at the Bell Labs research center by Ken Thompson, Dennis Ritchie, a ...
(BSD
The Berkeley Software Distribution (BSD), also known as Berkeley Unix or BSD Unix, is a discontinued Unix operating system developed and distributed by the Computer Systems Research Group (CSRG) at the University of California, Berkeley, beginni ...
, System V
Unix System V (pronounced: "System Five") is one of the first commercial versions of the Unix operating system. It was originally developed by AT&T and first released in 1983. Four major versions of System V were released, numbered 1, 2, 3, an ...
, Solaris
Solaris is the Latin word for sun.
It may refer to:
Arts and entertainment Literature, television and film
* ''Solaris'' (novel), a 1961 science fiction novel by Stanisław Lem
** ''Solaris'' (1968 film), directed by Boris Nirenburg
** ''Sol ...
, HP-UX
HP-UX (from "Hewlett Packard Unix") is a proprietary software, proprietary implementation of the Unix operating system developed by Hewlett Packard Enterprise; current versions support HPE Integrity Servers, based on Intel's Itanium architect ...
), BeOS
BeOS is a discontinued operating system for personal computers that was developed by Be Inc. It was conceived for the company's BeBox personal computer which was released in 1995. BeOS was designed for multitasking, multithreading, and a graph ...
, and VMS.
Licensing, ports, and derivative ports
''NetHack'' is released under the NetHack General Public License, which was written in 1989 by Mike Stephenson, patterned after the GNU bison license (which was written byRichard Stallman
Richard Matthew Stallman ( ; born March 16, 1953), also known by his initials, rms, is an American free software movement activist and programmer. He campaigns for software to be distributed in such a manner that its users have the freedom to ...
in 1988). Like the Bison license, and Stallman's later GNU General Public License
The GNU General Public Licenses (GNU GPL or simply GPL) are a series of widely used free software licenses, or ''copyleft'' licenses, that guarantee end users the freedom to run, study, share, or modify the software. The GPL was the first ...
, the ''NetHack'' license was written to allow the free sharing and modification of the source code
In computing, source code, or simply code or source, is a plain text computer program written in a programming language. A programmer writes the human readable source code to control the behavior of a computer.
Since a computer, at base, only ...
under its protection. At the same time, the license explicitly states that the source code is not covered by any warranty
In law, a warranty is an expressed or implied promise or assurance of some kind. The term's meaning varies across legal subjects. In property law, it refers to a covenant by the grantor of a deed. In insurance law, it refers to a promise by the ...
, thus protecting the original authors from litigation
A lawsuit is a proceeding by one or more parties (the plaintiff or claimant) against one or more parties (the defendant) in a civil court of law. The archaic term "suit in law" is found in only a small number of laws still in effect today. ...
. The NetHack General Public License is a copyleft
Copyleft is the legal technique of granting certain freedoms over copies of copyrighted works with the requirement that the same rights be preserved in derivative works. In this sense, ''freedoms'' refers to the use of the work for any purpose, ...
software license
A software license is a legal instrument governing the use or redistribution of software.
Since the 1970s, software copyright has been recognized in the United States. Despite the copyright being recognized, most companies prefer to sell lic ...
certified as an open source license
Open-source licenses are software licenses that allow content to be used, modified, and shared. They facilitate free and open-source software (FOSS) development. Intellectual property (IP) laws restrict the modification and sharing of creative ...
by the Open Source Initiative
The Open Source Initiative (OSI) is a California public benefit corporation "actively involved in Open Source community-building, education, and public advocacy to promote awareness and the importance of non-proprietary software".
Governance
The ...
.
The NetHack General Public License allows anyone to port
A port is a maritime facility comprising one or more wharves or loading areas, where ships load and discharge cargo and passengers. Although usually situated on a sea coast or estuary, ports can also be found far inland, such as Hamburg, Manch ...
the game to a platform not supported by the official DevTeam, provided that they use the same license. Over the years this licensing has led to a large number of ports and internationalized versions in German, Japanese, and Spanish. The license also allows for software forks as long as they are distributed under the same license, except that the creator of a derivative work is allowed to offer warranty protection on the new work. The derivative work is required to indicate the modifications made and the dates of changes. In addition, the source code of the derivative work must be made available, free of charge except for nominal distribution fees. This has also allowed source code forks of ''NetHack'' including '' Slash'EM'', ''UnNetHack'', and ''dNethack''.
Online support
Bugs, humorous messages, stories, experiences, and ideas for the next version are discussed on theUsenet
Usenet (), a portmanteau of User's Network, is a worldwide distributed discussion system available on computers. It was developed from the general-purpose UUCP, Unix-to-Unix Copy (UUCP) dial-up network architecture. Tom Truscott and Jim Elli ...
newsgroup
A Usenet newsgroup is a repository usually within the Usenet system for messages posted from users in different locations using the Internet. They are not only discussion groups or conversations, but also a repository to publish articles, start ...
rec.games.roguelike.nethack.
A public server at nethack.alt.org, commonly known as "NAO", gives players access to NetHack through a Telnet
Telnet (sometimes stylized TELNET) is a client-server application protocol that provides access to virtual terminals of remote systems on local area networks or the Internet. It is a protocol for bidirectional 8-bit communications. Its main ...
or SSH
The Secure Shell Protocol (SSH Protocol) is a cryptographic network protocol for operating network services securely over an unsecured network. Its most notable applications are remote login and command-line execution.
SSH was designed for Un ...
interface. A browser-based client is also available on the same site. Ebonhack connects to NAO with a graphical tiles-based interface.
During the whole month of November, the annual /dev/null NetHack Tournament took place every year from 1999 to 2016. The November NetHack Tournament, initially conceived as a one-time tribute to devnull, has taken place each year since 2018. The Junethack Cross-Variant Summer Tournament has taken place annually since 2011.
NetHack Learning Environment
TheFacebook
Facebook is a social media and social networking service owned by the American technology conglomerate Meta Platforms, Meta. Created in 2004 by Mark Zuckerberg with four other Harvard College students and roommates, Eduardo Saverin, Andre ...
artificial intelligence
Artificial intelligence (AI) is the capability of computer, computational systems to perform tasks typically associated with human intelligence, such as learning, reasoning, problem-solving, perception, and decision-making. It is a field of re ...
(AI) research team, along with researchers at the University of Oxford
The University of Oxford is a collegiate university, collegiate research university in Oxford, England. There is evidence of teaching as early as 1096, making it the oldest university in the English-speaking world and the List of oldest un ...
, New York University
New York University (NYU) is a private university, private research university in New York City, New York, United States. Chartered in 1831 by the New York State Legislature, NYU was founded in 1832 by Albert Gallatin as a Nondenominational ...
, the Imperial College London
Imperial College London, also known as Imperial, is a Public university, public research university in London, England. Its history began with Prince Albert of Saxe-Coburg and Gotha, Prince Albert, husband of Queen Victoria, who envisioned a Al ...
, and University College London
University College London (Trade name, branded as UCL) is a Public university, public research university in London, England. It is a Member institutions of the University of London, member institution of the Federal university, federal Uni ...
, developed an open-source platform called the NetHack Learning Environment, designed to teach AI agents to play ''NetHack''. The base environment is able to maneuver the agent and fight its way through dungeons, but the team seeks community help to build an AI on the complexities of ''NetHack'' interconnected systems, using implicit knowledge that comes from player-made resources, thus giving a means for programmers to hook into the environment with additional resources. Facebook's research led the company to pose ''NetHack'' as a grand challenge in AI in June 2021, in part due to the game's permadeath and inability to experiment with the environment without creating a reaction. The competition at the 2021 Conference on Neural Information Processing Systems
The Conference and Workshop on Neural Information Processing Systems (abbreviated as NeurIPS and formerly NIPS) is a machine learning and computational neuroscience conference held every December. Along with ICLR and ICML, it is one of the thre ...
involved agents of various designs attempting to ascend. None of the agents managed this; the results were ranked by median in-game score, with the highest-ranked agent (Team AutoAscend) using a symbolic (non-machine-learning) design.
Legacy
''NetHack'' has influenced '' ADOM'', ''Minecraft
''Minecraft'' is a 2011 sandbox game developed and published by the Swedish video game developer Mojang Studios. Originally created by Markus Persson, Markus "Notch" Persson using the Java (programming language), Java programming language, the ...
'', ''Spelunky
''Spelunky'' is a 2008 platform video game created by independent developer Derek Yu and released as source-available freeware for Microsoft Windows. It was remade for the Xbox 360 in 2012, with ports of the new version following for various ...
'', '' Diablo'' and ''Mystery Dungeon
''Mystery Dungeon'', known in Japan as is a series of roguelike role-playing video games. Most were developed by Chunsoft, now Spike Chunsoft since the merging in 2012, and select games were developed by other companies with Chunsoft's permiss ...
''. ''Time
Time is the continuous progression of existence that occurs in an apparently irreversible process, irreversible succession from the past, through the present, and into the future. It is a component quantity of various measurements used to sequ ...
'' included ''NetHack'' in its top 100 video games list in 2012. The game was part of the video game exhibit "Never Alone", in the Museum of Modern Art
The Museum of Modern Art (MoMA) is an art museum located in Midtown Manhattan, New York City, on 53rd Street (Manhattan), 53rd Street between Fifth Avenue, Fifth and Sixth Avenues. MoMA's collection spans the late 19th century to the present, a ...
's collection, which ran from September 2022 to July 2023.
See also
*List of open-source video games
This is a list of notable open-source video games. Open-source video games are assembled from and are themselves open-source software, including public domain games with public domain source code. This list also includes games in which the engine ...
* List of roguelikes
References
*Citations
External links
* *A Guide to the Mazes of Menace (Guidebook for ''NetHack'')
*
*
The NetHack Wiki
NAO website
/dev/null NetHack Tournament
*
''NetHack''
at SourceForge.net
Hall of Fame – ''NetHack''
at
GameSpy
GameSpy was an American provider of online multiplayer and matchmaking middleware for video games founded in 1999 by Mark Surfas. After the release of a multiplayer server browser for Quake, QSpy, Surfas licensed the software under the GameS ...
{{DEFAULTSORT:Nethack
1987 video games
Acorn Archimedes games
Amiga games
Android (operating system) games
Atari ST games
Cross-platform software
Fantasy video games
Free and open-source Android software
Games with concealed rules
GP2X games
Linux games
Classic Mac OS games
Open-source video games
MacOS games
Roguelike video games
Role-playing video games
Video games with textual graphics
Windows games
Video games using procedural generation