Multisignature on:
[Wikipedia]
[Google]
[Amazon]
 A cryptocurrency wallet is a device, physical medium, program or an online service which stores the public and/or private keys for
A cryptocurrency wallet is a device, physical medium, program or an online service which stores the public and/or private keys for
 A simple cryptocurrency wallet contains pairs of public and private cryptographic keys. The keys can be used to track ownership, receipt or spend
A simple cryptocurrency wallet contains pairs of public and private cryptographic keys. The keys can be used to track ownership, receipt or spend
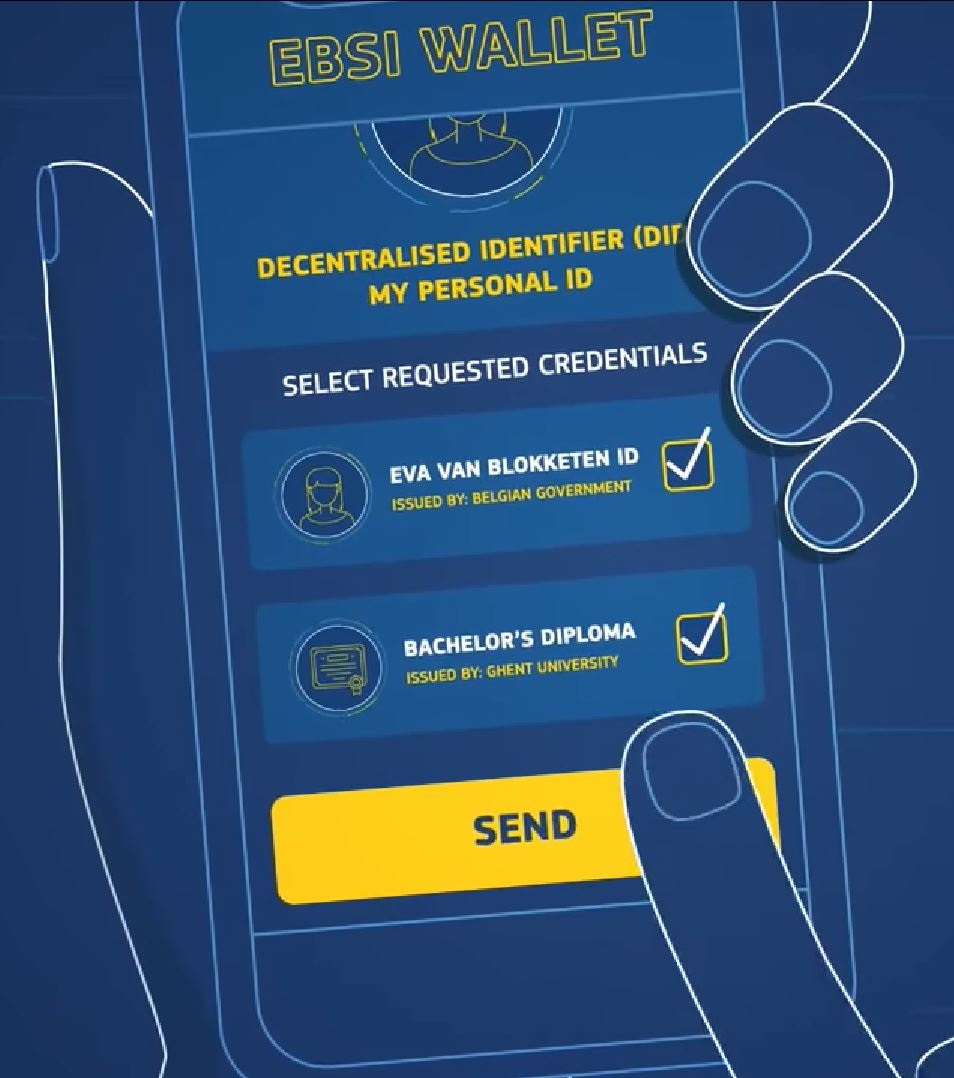 Some wallets are specifically designed to be compatible with a framework. The European Union is creating an
Some wallets are specifically designed to be compatible with a framework. The European Union is creating an
 A sequential deterministic wallet utilizes a simple method of generating addresses from a known starting string or "seed". This would utilize a
A sequential deterministic wallet utilizes a simple method of generating addresses from a known starting string or "seed". This would utilize a
 A cryptocurrency wallet is a device, physical medium, program or an online service which stores the public and/or private keys for
A cryptocurrency wallet is a device, physical medium, program or an online service which stores the public and/or private keys for cryptocurrency
A cryptocurrency (colloquially crypto) is a digital currency designed to work through a computer network that is not reliant on any central authority, such as a government or bank, to uphold or maintain it.
Individual coin ownership record ...
transactions. In addition to this basic function of storing the keys, a cryptocurrency wallet more often offers the functionality of encrypting and/or signing information. Signing can for example result in executing a smart contract
A smart contract is a computer program or a Transaction Protocol Data Unit, transaction protocol that is intended to automatically execute, control or document events and actions according to the terms of a contract or an agreement. The objective ...
, a cryptocurrency transaction (see "bitcoin transaction" image), identification
Identification or identify may refer to:
*Identity document, any document used to verify a person's identity
Arts, entertainment and media
* ''Identify'' (album) by Got7, 2014
* "Identify" (song), by Natalie Imbruglia, 1999
* ''Identification ...
, or legally signing a 'document' (see "application form" image).
History
In 2008 bitcoin was introduced as the first cryptocurrency following the principle outlined bySatoshi Nakamoto
Satoshi Nakamoto ( – 26 April 2011) is the name used by the presumed pseudonymous person or persons who developed bitcoin, authored the bitcoin white paper, and created and deployed bitcoin's original reference implementation. As part of the ...
in the paper “Bitcoin: A Peer-to-Peer Electronic Cash System.” The project was described as an electronic payment system using cryptographic proof instead of trust. It also mentioned using cryptographic proof to verify and record transactions on a blockchain
The blockchain is a distributed ledger with growing lists of Record (computer science), records (''blocks'') that are securely linked together via Cryptographic hash function, cryptographic hashes. Each block contains a cryptographic hash of th ...
.
Software wallets
The first wallet program, simply named ''Bitcoin'', and sometimes referred to as the ''Satoshi client'', was released in January 2009 by Satoshi Nakamoto asopen-source software
Open-source software (OSS) is Software, computer software that is released under a Open-source license, license in which the copyright holder grants users the rights to use, study, change, and Software distribution, distribute the software an ...
. In version 0.5 the client moved from the wxWidgets
wxWidgets (formerly wxWindows) is a widget toolkit and tools library for creating graphical user interfaces (GUIs) for cross-platform applications. wxWidgets enables a program's GUI code to compile and run on several computer platforms with no s ...
user interface toolkit to Qt, and the whole bundle was referred to as ''Bitcoin-Qt''. After the release of version 0.9, the software bundle was renamed ''Bitcoin Core'' to distinguish itself from the underlying network. Bitcoin Core
Bitcoin Core is free and open-source software that serves as a bitcoin node (the set of which form the Bitcoin network) and provides a bitcoin wallet which fully verifies payments. It is considered to be bitcoin's reference implementation. Ini ...
is, perhaps, the best known implementation or client. Forks
In cutlery or kitchenware, a fork (from 'pitchfork') is a Eating utensil, utensil, now usually made of metal, whose long handle terminates in a head that branches into several narrow and often slightly curved tine (structural), tines with whic ...
of Bitcoin Core exist, such as Bitcoin XT, Bitcoin Unlimited, and Parity Bitcoin.
There are several modes in which wallets can operate. They have an inverse relationship with regard to trustlessness and computational requirements.
* ''Full clients'' verify transactions directly by downloading a full copy of the blockchain (over 150 GB ). They do not require trust in any external parties. Full clients check the validity of mined blocks, preventing them from transacting on a chain that breaks or alters network rules. Because of its size and complexity, downloading and verifying the entire blockchain is not suitable for all computing devices.
* ''Lightweight clients'' consult full nodes to send and receive transactions without requiring a local copy of the entire blockchain (see '' simplified payment verification'' – ''SPV''). This makes lightweight clients much faster to set up and allows them to be used on low-power, low-bandwidth devices such as smartphones. When using a lightweight wallet, however, the user must trust full nodes, as it can report faulty values back to the user. Lightweight clients follow the longest blockchain and do not ensure it is valid, requiring trust in full nodes.
Third-party internet services called ''online wallets'' or ''webwallets'' offer similar functionality but may be easier to use. In this case, credentials to access funds are stored with the online wallet provider rather than on the user's hardware. As a result, the user must have complete trust in the online wallet provider. A malicious provider or a breach in server security may cause entrusted bitcoins to be stolen. An example of such a security breach occurred with Mt. Gox in 2011.
Cold storage
Wallet software is targeted by hackers because of the lucrative potential for stealing bitcoins. "Cold storage" simply means keeping the private keys out of reach of hackers by storing or generating them on a device that is not connected to the internet. The credentials necessary to spend bitcoins can be stored offline in a number of different ways, from simple paper printouts of private keys, to specialized hardware wallets.Paper wallets
A paper wallet is created with a keypair generated on a computer with no internet connection; the private key is written or printed onto the paper and then erased from the computer. The paper wallet can then be stored in a safe physical location for later retrieval. Physical wallets can also take the form of metaltoken coin
In numismatics, token coins or trade tokens are coin-like objects used instead of coins. The field of token coins is part of exonumia and token coins are token money. Their denomination is shown or implied by size, color or shape. They are of ...
s with a private key accessible under a security hologram in a recess struck on the reverse side. The security hologram self-destructs when removed from the token, showing that the private key has been accessed. Originally, these tokens were struck in brass and other base metal
A base metal is a common and inexpensive metal, as opposed to a precious metal such as gold or silver. In numismatics, coins often derived their value from the precious metal content; however, base metals have also been used in coins in the past ...
s, but later used precious metal
Precious metals are rare, naturally occurring metallic chemical elements of high Value (economics), economic value. Precious metals, particularly the noble metals, are more corrosion resistant and less reactivity (chemistry), chemically reac ...
s as bitcoin grew in value and popularity. Coins with stored face value as high as ₿1,000 have been struck in gold. The British Museum
The British Museum is a Museum, public museum dedicated to human history, art and culture located in the Bloomsbury area of London. Its permanent collection of eight million works is the largest in the world. It documents the story of human cu ...
's coin collection includes four specimens from the earliest series of funded bitcoin tokens; one is currently on display in the museum's money gallery. In 2013, a Utah
Utah is a landlocked state in the Mountain states, Mountain West subregion of the Western United States. It is one of the Four Corners states, sharing a border with Arizona, Colorado, and New Mexico. It also borders Wyoming to the northea ...
manufacturer of these tokens was ordered by the Financial Crimes Enforcement Network
The Financial Crimes Enforcement Network (FinCEN) is a bureau within the United States Department of the Treasury that collects and analyzes information about financial transactions to combat domestic and international money laundering, terrori ...
(FinCEN) to register as a money services business before producing any more funded bitcoin tokens.
Hardware wallets
A hardware wallet is a small and portable computerperipheral
A peripheral device, or simply peripheral, is an auxiliary hardware device that a computer uses to transfer information externally. A peripheral is a hardware component that is accessible to and controlled by a computer but is not a core compo ...
that signs transactions as requested by the user. These devices store private keys and carry out signing and encryption internally, and do not share any sensitive information with the host computer except already signed (and thus unalterable) transactions. Because hardware wallets never expose their private keys, even computers that may be compromised by malware do not have a vector to access or steal them.The user sets a passcode when setting up a hardware wallet. As hardware wallets are tamper-resistant, without the passcode the assets cannot be accessed.
Technology
Private and public key generation
A cryptocurrency wallet works by a theoretical or random number being generated and used with a length that depends on the algorithm size of the cryptocurrency's technology requirements. The number is converted to a private key using the specific requirements of the cryptocurrency cryptography algorithm requirement. A public key is then generated from the private key using whichever cryptographic algorithm is required. The private key is used by the owner to access and send cryptocurrency and is private to the owner, whereas the public key is to be shared to any third party to receive cryptocurrency. Up to this stage no computer or electronic device is required and all key pairs can be mathematically derived and written down by hand. The private key and public key pair (known as an address) are not known by the blockchain or anyone else. The blockchain will only record the transaction of the public address when cryptocurrency is sent to it, thus recording in the blockchain ledger the transaction of the public address.Duplicate private keys
Collision (two or more wallets having the same private key) is theoretically possible, since keys can be generated without being used for transactions, and are therefore offline until recorded in the blockchain ledger. However, this possibility is effectively negated because the theoretical probability of two or more private keys being the same is extremely low. The number of possible wallets and thus private keys is extremely high, so duplicating or hacking a certain key would be inconceivable.Seed phrases
In modern convention a seed phrase is now utilised which is a random 12 to 24 (or even greater) list of dictionary words which is an unencrypted form of the private key. (Words are easier tomemorize
Memorization (British English: memorisation) is the process of committing something to memory. It is a mental process undertaken in order to store in memory for later recall visual, auditory, or tactical information.
The scientific study of mem ...
than numerals). When online, exchange and hardware wallets are generated using random numbers, and the user is asked to supply a seed phrase. If the wallet is misplaced, damaged or compromised, the seed phrase can be used to re-access the wallet and associated keys and cryptocurrency ''in toto''.
Wallets
A number of technologies known as wallets exist that store the key value pair of private and public key known as wallets. A wallet hosts the details of the key pair making cryptocurrency transactions possible. Multiple methods exist for storing keys or seeds in a wallet. A ' or ''brain wallet'' is a type of wallet in which one memorizes a passcode (a private key or seed phrase). may be attractive due toplausible deniability
Plausible deniability is the ability of people, typically senior officials in a formal or informal chain of command, to deny knowledge or responsibility for actions committed by or on behalf of members of their organizational hierarchy. They may ...
or protection against governmental seizure, but are vulnerable to password guessing (especially large-scale offline guessing). Several hundred exist on the Bitcoin blockchain, but most of them have been drained, sometimes repeatedly.
Crypto wallets vis-à-vis DApp browsers
DApp browsers are specialized software that supports decentralized applications. DApp browsers are considered to be the browsers ofWeb3
Web3 (also known as Web 3.0) is an idea for a new iteration of the World Wide Web which incorporates concepts such as decentralization, blockchain technologies, and token-based economics. This is distinct from Tim Berners-Lee's concept of th ...
and are the gateway to access the decentralized applications which are based on blockchain technology. That means all DApp browsers must have a unique code system to unify all the different codes of the DApps.
While crypto wallets are focused on the exchange, purchase, sale of digital assets and support narrowly targeted applications, the browsers support different kinds of applications of various formats, including exchange, games, NFTs marketplaces, etc.
Characteristics
In addition to the basic function of storing the keys, a cryptocurrency wallet may also have one or more of the following characteristics.Simple cryptocurrency wallet
 A simple cryptocurrency wallet contains pairs of public and private cryptographic keys. The keys can be used to track ownership, receipt or spend
A simple cryptocurrency wallet contains pairs of public and private cryptographic keys. The keys can be used to track ownership, receipt or spend cryptocurrencies
A cryptocurrency (colloquially crypto) is a digital currency designed to work through a computer network that is not reliant on any central authority, such as a government or bank, to uphold or maintain it.
Individual coin ownership records ...
. A public key allows others to make payments to the address derived from it, whereas a private key enables the spending of cryptocurrency from that address.
The cryptocurrency itself is not in the wallet. In the case of bitcoin
Bitcoin (abbreviation: BTC; Currency symbol, sign: ₿) is the first Decentralized application, decentralized cryptocurrency. Based on a free-market ideology, bitcoin was invented in 2008 when an unknown entity published a white paper under ...
and cryptocurrencies derived from it, the cryptocurrency is decentrally stored and maintained in a publicly available distributed ledger
A distributed ledger (also called a shared ledger or distributed ledger technology or DLT) is a system whereby replicated, shared, and synchronized digital data is geographically spread (distributed) across many sites, countries, or institutions. I ...
called the ''blockchain
The blockchain is a distributed ledger with growing lists of Record (computer science), records (''blocks'') that are securely linked together via Cryptographic hash function, cryptographic hashes. Each block contains a cryptographic hash of th ...
''.
Multi-chain cryptocurrency wallet
Multi-chain wallets are designed to support multiple blockchain networks, enabling users to store, manage, and transact different types of cryptocurrencies from a single interface. Unlike single-chain wallets, which are limited to a specific blockchain, multi-chain wallets provide a unified experience for handling various assets. These wallets enhance convenience and security by reducing the need for multiple wallet applications and providing integrated features for multiple digital assets. Features of a multi-chain wallet: * Support for Multiple Blockchains: Users can hold and manage various blockchains such asBitcoin
Bitcoin (abbreviation: BTC; Currency symbol, sign: ₿) is the first Decentralized application, decentralized cryptocurrency. Based on a free-market ideology, bitcoin was invented in 2008 when an unknown entity published a white paper under ...
, Ethereum
Ethereum is a decentralized blockchain with smart contract functionality. Ether (abbreviation: ETH) is the native cryptocurrency of the platform. Among cryptocurrencies, ether is second only to bitcoin in market capitalization. It is open-s ...
, Klever Blockchain, Binance Smart Chain, and more within one wallet.
* Enhanced Security: Typically incorporate advanced security measures including two-factor authentication
Multi-factor authentication (MFA; two-factor authentication, or 2FA) is an electronic authentication method in which a user is granted access to a website or Application software, application only after successfully presenting two or more distin ...
and seed phrase backup.
* Interoperability: Facilitates seamless transactions across different blockchain networks.
* User-friendly Interface: Designed to be accessible and intuitive, making it easier for users to navigate and manage their assets.
Popular multi-chain wallets include Trust Wallet, Klever Wallet and Exodus, each offering unique features and support for multiple blockchains, therefore, hundreds of cryptocurrencies.
eID wallet
 Some wallets are specifically designed to be compatible with a framework. The European Union is creating an
Some wallets are specifically designed to be compatible with a framework. The European Union is creating an eIDAS
The eIDAS Regulation (for "electronic IDentification, Authentication and trust Services") is an regulation (European Union), EU regulation with the stated purpose of governing "electronic identification and trust service provider, trust service ...
compatible European Self-Sovereign Identity Framework (ESSIF) which runs on the European Blockchain Services Infrastructure (EBSI). The EBSI wallet is designed to (securely) provide information, an eID and to sign 'transactions'.
Multisignature wallet
In contrast to simple cryptocurrency wallets requiring just one party to sign a transaction, multi-sig wallets require multiple parties to sign a transaction. Multisignature wallets are designed for increased security. Usually, a multisignature algorithm produces a joint signature that is more compact than a collection of distinct signatures from all users. There are various use cases for using a multisignature wallet like: enhanced security,treasury management
Treasury management (or treasury operations) entails management of an enterprise's financial holdings, focusing on the firm's liquidity, and mitigating its financial-, operational- and reputational risk.
Treasury Management's scope thus inclu ...
, partnership management, escrow
An escrow is a contractual arrangement in which a third party (the stakeholder or escrow agent) receives and disburses money or property for the primary transacting parties, with the disbursement dependent on conditions agreed to by the transact ...
services, inheritance
Inheritance is the practice of receiving private property, titles, debts, entitlements, privileges, rights, and obligations upon the death of an individual. The rules of inheritance differ among societies and have changed over time. Offi ...
planning, regulatory compliance
In general, compliance means conforming to a rule, such as a specification, policy, standard or law. Compliance has traditionally been explained by reference to deterrence theory, according to which punishing a behavior will decrease the viol ...
and backup recovery.
Smart contract
In the cryptocurrency space,smart contract
A smart contract is a computer program or a Transaction Protocol Data Unit, transaction protocol that is intended to automatically execute, control or document events and actions according to the terms of a contract or an agreement. The objective ...
s are digitally signed in the same way a cryptocurrency transaction is signed. The signing keys are held in a cryptocurrency wallet.
Key derivation
Sequential deterministic wallet
 A sequential deterministic wallet utilizes a simple method of generating addresses from a known starting string or "seed". This would utilize a
A sequential deterministic wallet utilizes a simple method of generating addresses from a known starting string or "seed". This would utilize a cryptographic hash function
A cryptographic hash function (CHF) is a hash algorithm (a map (mathematics), map of an arbitrary binary string to a binary string with a fixed size of n bits) that has special properties desirable for a cryptography, cryptographic application: ...
, e.g. SHA-256
SHA-2 (Secure Hash Algorithm 2) is a set of cryptographic hash functions designed by the United States National Security Agency (NSA) and first published in 2001. They are built using the Merkle–Damgård construction, from a one-way compressi ...
(seed + n), where n is an ASCII
ASCII ( ), an acronym for American Standard Code for Information Interchange, is a character encoding standard for representing a particular set of 95 (English language focused) printable character, printable and 33 control character, control c ...
-coded number that starts from 1 and increments as additional keys are needed.
Hierarchical deterministic wallet
The hierarchical deterministic (HD) wallet was publicly described in BIP32. As a deterministic wallet, it also derives keys from a single master root seed, but instead of having a single "chain" of keypairs, an HD wallet supports multiple key pair chains. This allows a single key string to be used to generate an entiretree
In botany, a tree is a perennial plant with an elongated stem, or trunk, usually supporting branches and leaves. In some usages, the definition of a tree may be narrower, e.g., including only woody plants with secondary growth, only ...
of key pairs with a stratified structure.
BIP39 proposed the use of a set of human-readable words to derive the master private key of a wallet. This mnemonic
A mnemonic device ( ), memory trick or memory device is any learning technique that aids information retention or retrieval in the human memory, often by associating the information with something that is easier to remember.
It makes use of e ...
phrase allows for easier wallet backup and recovery, due to all the keys of a wallet being derivable from a single plaintext string.
Non-deterministic wallet
In a non-deterministic wallet, each key is randomly generated on its own accord, and they are not seeded from a common key. Therefore, any backups of the wallet must store each and every single private key used as an address, as well as a buffer of 100 or so future keys that may have already been given out as addresses but not received payments yet.Concerns
A wallet can also have known or unknownvulnerabilities
Vulnerability refers to "the quality or state of being exposed to the possibility of being attacked or harmed, either physically or emotionally." The understanding of social and environmental vulnerability, as a methodological approach, involves ...
. A supply chain attack
A supply chain attack is a cyber-attack that seeks to damage an organization by targeting less secure elements in the supply chain. A supply chain attack can occur in any industry, from the financial sector, oil industry, to a government sector. ...
or side-channel attack
In computer security, a side-channel attack is a type of security exploit that leverages information inadvertently leaked by a system—such as timing, power consumption, or electromagnetic or acoustic emissions—to gain unauthorized access to ...
are ways of introducing vulnerabilities. In extreme cases even a computer which is not connected to any network can be hacked.
To mitigate the risk of crypto wallet hacking, one can choose for a cold wallet, which remains offline and disconnected from the internet. A cold wallet refers to a physical device, such as a pen drive, that is utilized as a secure storage medium for transferring money from a hot wallet.
Security
When using a merchant site that accepts server-side digital wallets, customers enter their name, payment, and delivery information. Following the purchase, the customer is requested to register for a wallet with a user name and password for future purchases. Digital wallets can be dedicated to a single cryptocurrency (examples: Bitcoin, Etherium, Ripple, Litecoin), or they can be multi-currency (Coinomi, CoinSpot, CoinVault, Cryptonator multi-cryptocurrency wallet, Exodus, Gatehub, Holy Transaction, Jaxx Wallet, UberPay Wallet, AnCrypto Wallet, Klever Wallet. Wallets are free for consumers but cost retailers. Wallet sellers may receive a portion of merchant purchases made through their wallets. In other circumstances, digital wallet vendors conduct cardholder-merchant transactions for a set fee.See also
*Cryptocurrency exchange
A cryptocurrency exchange, or a digital currency exchange (DCE), is a business that allows customers to trade cryptocurrencies or digital currencies for other assets, such as conventional fiat money or other digital currencies. Exchanges may acce ...
* Cryptography
Cryptography, or cryptology (from "hidden, secret"; and ''graphein'', "to write", or ''-logy, -logia'', "study", respectively), is the practice and study of techniques for secure communication in the presence of Adversary (cryptography), ...
* Cryptocurrency and security
* Decentralized application
A decentralised application (DApp, dApp, Dapp, or dapp) is an Application software, application that can operate autonomously, typically through the use of smart contracts, that run on a decentralized computing, blockchain or other distributed le ...
* Medium of exchange
In economics, a medium of exchange is any item that is widely acceptable in exchange for goods and services. In modern economies, the most commonly used medium of exchange is currency. Most forms of money are categorised as mediums of exchange, i ...
* Public-key cryptography
Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a public key and a corresponding private key. Key pairs are generated with cryptographic alg ...
* Web3
Web3 (also known as Web 3.0) is an idea for a new iteration of the World Wide Web which incorporates concepts such as decentralization, blockchain technologies, and token-based economics. This is distinct from Tim Berners-Lee's concept of th ...
References
{{Authority control BitcoinWallet
A wallet is a flat case or pouch, often used to carry small personal items such as physical currency, debit cards, and credit cards; identification documents such as driving licence, identification card, club card; photographs, transit pass, b ...
Private currencies
Cryptocurrency exchanges