M-94 on:
[Wikipedia]
[Google]
[Amazon]
 The M-94 was a piece of cryptographic equipment used by the
The M-94 was a piece of cryptographic equipment used by the
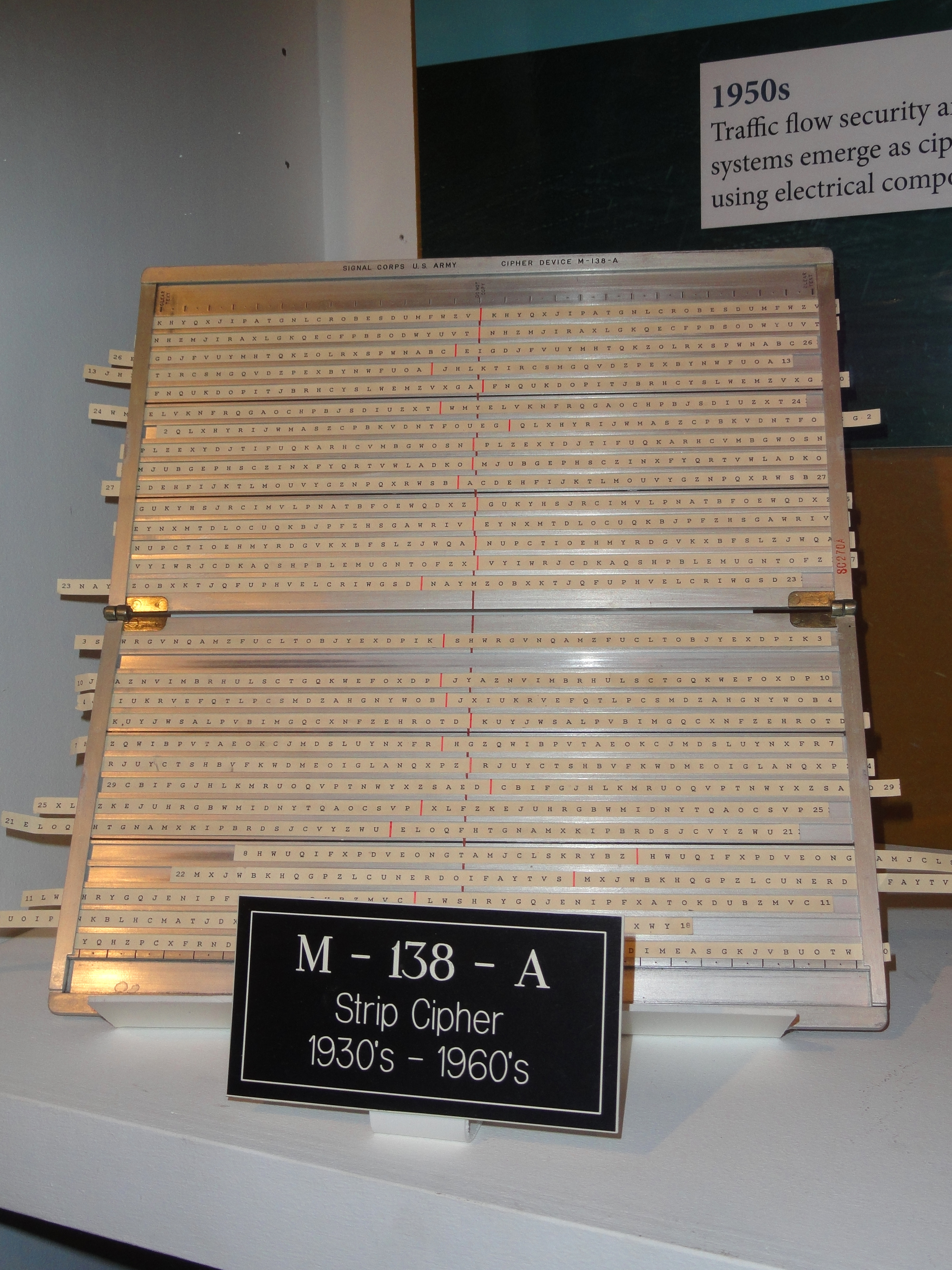 In an extension of the same general principle, the M-138-A strip cipher machine, used by the US Army, Navy (as CSP-845), Coast Guard and State Department through World War II, featured hundreds of flat cardboard strips. Each strip contained a scrambled alphabet, repeated twice, that could be slid back and forth in a frame; with 30 being selected for each cipher session. The strip cipher could interoperate with the M-94 if suitable strips were provided.
The original design used an aluminum base. William F. Friedman describes the problem of getting them manufactured and how it was overcome:
In an extension of the same general principle, the M-138-A strip cipher machine, used by the US Army, Navy (as CSP-845), Coast Guard and State Department through World War II, featured hundreds of flat cardboard strips. Each strip contained a scrambled alphabet, repeated twice, that could be slid back and forth in a frame; with 30 being selected for each cipher session. The strip cipher could interoperate with the M-94 if suitable strips were provided.
The original design used an aluminum base. William F. Friedman describes the problem of getting them manufactured and how it was overcome:
DESCRIPTION OF CSP-488 a.k.a. M-94
{{Cryptography navbox , machines Classical ciphers Encryption devices World War II military equipment of the United States Cryptographic hardware
 The M-94 was a piece of cryptographic equipment used by the
The M-94 was a piece of cryptographic equipment used by the United States Army
The United States Army (USA) is the primary Land warfare, land service branch of the United States Department of Defense. It is designated as the Army of the United States in the United States Constitution.Article II, section 2, clause 1 of th ...
, consisting of several lettered discs arranged as a cylinder
A cylinder () has traditionally been a three-dimensional solid, one of the most basic of curvilinear geometric shapes. In elementary geometry, it is considered a prism with a circle as its base.
A cylinder may also be defined as an infinite ...
. It was also employed by the US Navy
The United States Navy (USN) is the naval warfare, maritime military branch, service branch of the United States Department of Defense. It is the world's most powerful navy with the largest Displacement (ship), displacement, at 4.5 millio ...
, under the name CSP 488.
The device was conceived by Colonel Parker Hitt and then developed by Major Joseph Mauborgne in 1917; based on a system invented by Thomas Jefferson
Thomas Jefferson (, 1743July 4, 1826) was an American Founding Fathers of the United States, Founding Father and the third president of the United States from 1801 to 1809. He was the primary author of the United States Declaration of Indepe ...
and Etienne Bazeries. Officially adopted in 1922, it remained in use until circa 1942, when it was replaced by more complex and secure electromechanical rotor machine
In cryptography, a rotor machine is an electro-mechanical stream cipher device used for encrypting and decrypting messages. Rotor machines were the cryptographic state-of-the-art for much of the 20th century; they were in widespread use from ...
s, particularly the M-209.
Principle
The device consisted of 25aluminium
Aluminium (or aluminum in North American English) is a chemical element; it has chemical symbol, symbol Al and atomic number 13. It has a density lower than that of other common metals, about one-third that of steel. Aluminium has ...
discs attached to a four-and-a-half inch long rod, each disc containing the 26 letters of the Roman alphabet in scrambled order around its circumference
In geometry, the circumference () is the perimeter of a circle or ellipse. The circumference is the arc length of the circle, as if it were opened up and straightened out to a line segment. More generally, the perimeter is the curve length arou ...
(with the exception of the 17th disc, which began with the letters "ARMY OF THE US"). Each wheel had a different arrangement of the alphabet, and was stamped with an identifying number and letter; wheels were identified according to the letter following "A" on that wheel, from "B 1" to "Z 25". The wheels could be assembled on the rod in any order; the ordering used during encoding comprised the key. There were ''25! (25 factorial
In mathematics, the factorial of a non-negative denoted is the Product (mathematics), product of all positive integers less than or equal The factorial also equals the product of n with the next smaller factorial:
\begin
n! &= n \times ...
) = 15,511,210,043,330,985,984,000,000'' (more than 15 septillion) possible keys, which can be expressed as about an 84-bit key size
In cryptography, key size or key length refers to the number of bits in a key used by a cryptographic algorithm (such as a cipher).
Key length defines the upper-bound on an algorithm's security (i.e. a logarithmic measure of the fastest known a ...
.
Messages were encrypted 25 letters at a time. Turning the discs individually, the operator aligned the letters in the message horizontally. Then, any one of the remaining lines around the circumference of the cylinder was sent as the ciphertext
In cryptography, ciphertext or cyphertext is the result of encryption performed on plaintext using an algorithm, called a cipher. Ciphertext is also known as encrypted or encoded information because it contains a form of the original plaintext ...
. To decrypt, the wheels were turned until one line matched a 25 letter block of ciphertext. The plaintext
In cryptography, plaintext usually means unencrypted information pending input into cryptographic algorithms, usually encryption algorithms. This usually refers to data that is transmitted or stored unencrypted.
Overview
With the advent of comp ...
would then appear on one of the other lines, which could be visually located easily, as it would be the only one likely to "read."
The principle upon which the M-94/CSP-488 is based was first invented by Thomas Jefferson
Thomas Jefferson (, 1743July 4, 1826) was an American Founding Fathers of the United States, Founding Father and the third president of the United States from 1801 to 1809. He was the primary author of the United States Declaration of Indepe ...
in 1795 in his "wheel cypher" but did not become well known, and was independently invented by Etienne Bazeries a century later.
M-138-A
"It soon became apparent to both Army and Navy cryptologists that a great increase in cryptosecurity would be obtained if the alphabets of the M-94 device could be made variant instead of invariant. There began efforts in both services to develop a practical instrument based upon this principle. I won't take time to show all these developments but only the final form of the one adopted by the Army, Strip Cipher Device Type, M-138-A. This form used an aluminum base into which channels with overhanging edges were cut to hold cardboard strips of alphabets which could be slid easily within the channels. It may be of interest to you to learn that after I had given up in my attempts to find a firm which would or could make such aluminum grooved devices in quantity, Mrs. Friedman, by womanly wiles and cajolery on behalf of her own group in the U.S. Coast Guard, succeeded in inducing or enticing one firm to make them for her. And it's how the first models of strip cipher devices made of aluminum by the extrusion process came about, and how the U.S. Army, by administrative cooperation on an inter-Service level and technical cooperation on a marital level, found it practical to develop and produce in quantity its Strip Cipher Device, Type M-138-A. This was used from 1935 to 1941 or 1942 by the Army, the Navy, the Marine Corps, the Coast Guard, et al, including the Treasury and State Departments. It was used as a back-up system even after the Armed Services as well as the Department of State began employing much better and more sophisticated cipher machines of high speed and security."Another problem was that aluminum was in short supply early in the war and attempts were made to make the strip cipher bases out of plastic or mahogany, with limited success. Fortunately, aluminum became available again for this use in the fall of 1943.Display text at National Cryptologic Museum Besides the military,
Department of State
The United States Department of State (DOS), or simply the State Department, is an executive department of the U.S. federal government responsible for the country's foreign policy and relations. Equivalent to the ministry of foreign affairs ...
and many other civilian agencies (like OSS) were using it for most important messages, and despite it being a powerful method in theory, made many mistakes so the system was compromised, letting multiple Axis countries decipher it.
Cryptanalysis
Like mostclassical cipher
In cryptography, a classical cipher is a type of cipher that was used historically but for the most part, has fallen into disuse. In contrast to modern cryptographic algorithms, most classical ciphers can be practically computed and solved by hand ...
s, strip ciphers can be easily cracked if there is enough intercepted ciphertext. However, this takes time and specialized skills, so the M-94 was still good enough during the early years of World War II
World War II or the Second World War (1 September 1939 – 2 September 1945) was a World war, global conflict between two coalitions: the Allies of World War II, Allies and the Axis powers. World War II by country, Nearly all of the wo ...
for its intended use as a "tactical cipher"; in a similar way to the more modern DRYAD
A dryad (; , sing. ) is an oak tree nymph or oak tree spirit in Greek mythology; ''Drys'' (δρῦς) means "tree", and more specifically " oak" in Greek. Today the term is often used to refer to tree nymphs in general.
Types
Daphnaie
Thes ...
and BATCO. The M-138-A was stronger because slips with new alphabets could be issued periodically, even by radio using more secure systems like SIGABA, however this was not practiced until the US found out that their strips were compromised in early 1943. Both were replaced by the M-209 mechanical rotor machine as these became available.
The main method of M-138-A cryptanalysis
Cryptanalysis (from the Greek ''kryptós'', "hidden", and ''analýein'', "to analyze") refers to the process of analyzing information systems in order to understand hidden aspects of the systems. Cryptanalysis is used to breach cryptographic se ...
practiced by Axis, besides physically capturing the systems, was exploiting its vulnerability to the known-plaintext attack
The known-plaintext attack (KPA) is an attack model for cryptanalysis where the attacker has access to both the plaintext (called a crib) and its encrypted version (ciphertext). These can be used to reveal secret keys and code books. The term " ...
(e. g., when the same text was published in press releases), as well as the fact that the embassies used too little keys and strips.
See also
*Jefferson disk
The Jefferson disk, also called the Bazeries cylinder or wheel cypher, is a cipher system commonly attributed to Thomas Jefferson that uses a set of wheels or disks, each with letters of the alphabet arranged around their edge in an order, whic ...
References
External links
DESCRIPTION OF CSP-488 a.k.a. M-94
{{Cryptography navbox , machines Classical ciphers Encryption devices World War II military equipment of the United States Cryptographic hardware