|
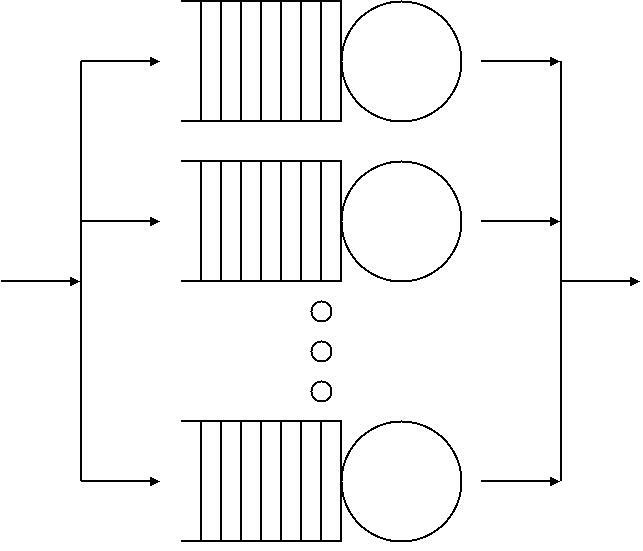
Leaky Bucket
The leaky bucket is an algorithm based on an analogy of how a bucket with a constant leak will overflow if either the average rate at which water is poured in exceeds the rate at which the bucket leaks or if more water than the capacity of the bucket is poured in all at once. It can be used to determine whether some sequence of discrete events Conformance testing, conforms to defined limits on their average and peak rates or frequencies, e.g. to limit the actions associated with these events to these rates or delay them until they do conform to the rates. It may also be used to check conformance or limit to an average rate alone, i.e. remove any variation from the average. It is used in packet-switched computer networks and telecommunications networks in both the traffic policing (communications), traffic policing, traffic shaping and network scheduler, scheduling of data transmissions, in the form of Network packet, packets, to defined limits on Bandwidth (computing), bandwi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Leaky Bucket Analogy
Leakey may refer to: *Leakey, Texas, U.S., a city *Leakey (crater), a lunar impact crater *Leakey (surname) *7958 Leakey, an asteroid *Leakey Independent School District The Leakey Independent School District is a public school district based in Leakey, Texas, US. The district is located primarily in Real County with a small portion extending into north central Uvalde County. The unincorporated community of ..., a public school district based in Leakey, Texas See also * Leak (other) * * {{disambig ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Asynchronous Transfer Mode
Asynchronous Transfer Mode (ATM) is a telecommunications standard defined by the American National Standards Institute and International Telecommunication Union Telecommunication Standardization Sector (ITU-T, formerly CCITT) for digital transmission of multiple types of traffic. ATM was developed to meet the needs of the Broadband Integrated Services Digital Network as defined in the late 1980s, and designed to integrate telecommunication networks. It can handle both traditional high-throughput data traffic and Real-time computing, real-time, low-latency content such as telephony (voice) and video.ATM Forum, The User Network Interface (UNI), v. 3.1, , Prentice Hall PTR, 1995, page 2. ATM is a cell switching technology, providing functionality that combines features of circuit switching and packet switching networks by using asynchronous communication, asynchronous time-division multiplexing.McDysan (1999), p. 287. ATM was seen in the 1990s as a competitor to Ethernet and networ ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Queueing Theory
Queueing theory is the mathematical study of waiting lines, or queues. A queueing model is constructed so that queue lengths and waiting time can be predicted. Queueing theory is generally considered a branch of operations research because the results are often used when making business decisions about the resources needed to provide a service. Queueing theory has its origins in research by Agner Krarup Erlang, who created models to describe the system of incoming calls at the Copenhagen Telephone Exchange Company. These ideas were seminal to the field of teletraffic engineering and have since seen applications in telecommunications, traffic engineering, computing, project management, and particularly industrial engineering, where they are applied in the design of factories, shops, offices, and hospitals. Spelling The spelling "queueing" over "queuing" is typically encountered in the academic research field. In fact, one of the flagship journals of the field is '' Queue ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Leaky Bucket As A Meter-shaping
Leakey may refer to: *Leakey, Texas, U.S., a city *Leakey (crater), a lunar impact crater *Leakey (surname) *7958 Leakey, an asteroid *Leakey Independent School District The Leakey Independent School District is a public school district based in Leakey, Texas, US. The district is located primarily in Real County with a small portion extending into north central Uvalde County. The unincorporated community of ..., a public school district based in Leakey, Texas See also * Leak (other) * * {{disambig ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
User–network Interface
In telecommunications, a user–network interface (UNI) is a demarcation point between the responsibility of the service provider and the responsibility of the subscriber. This is distinct from a network-to-network interface (NNI) that defines a similar interface between provider networks. Specifications defining a UNI Metro Ethernet Forum The Metro Ethernet Forum's Metro Ethernet Network UNI specification defines a bidirectional Ethernet reference point for Ethernet service delivery. Optical Internetworking Forum The Optical Internetworking Forum defines a UNI software interface for user systems to request a network connection from an ASON/GMPLS control plane. See also * Network termination External linksMetro Ethernet Forum {{DEFAULTSORT:User-network interface Network management ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
ATM Forum
The ATM Forum was a non-profit industry consortium founded in 1991 to promote Asynchronous Transfer Mode technology. The founding president and chairman was Fred Sammartino of Sun Microsystems. The ATM Forum created over 200 implementation agreements. History In 1996 ATM technology stabilized with the "Anchorage Accord", which established the baseline of ATM implementations. While ATM did not live up to every expectation, it remained an important core network technology. The Frame Relay Forum (promoting Frame Relay) also started in 1991. The MPLS Forum (which supported Multiprotocol Label Switching had begun in 2000. Those two merged in 2003 to become the MPLS and Frame Relay Alliance (MFA). In 2005, the ATM Forum joined forces with the MFA to form the MFA Forum, which was renamed to be the IP/MPLS Forum. In May 2009 the IP/MPLS Forum merged with the Broadband Forum. Sampling of specifications * ATM-MPLS Network Interworking * Multi-Protocol Over ATM * TM 4.1 * User-Network ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
ITU-T
The International Telecommunication Union Telecommunication Standardization Sector (ITU-T) is one of the three Sectors (branches) of the International Telecommunication Union (ITU). It is responsible for coordinating Standardization, standards for telecommunications and Information Communication Technology, such as X.509 for cybersecurity, Y.3172 and Y.3173 for machine learning, and H.264/MPEG-4 AVC for video compression, between its Member States, Private Sector Members, and Academia Members. The World Telecommunication Standardization Assembly (WTSA), the sector's governing conference, convenes every four years. ITU-T has a permanent Secretariat (administrative office), secretariat called the Telecommunication Standardization Bureau (TSB), which is based at the ITU headquarters in Geneva, Switzerland. The current director of the TSB is Seizo Onoe (of Japan), whose 4-year term commenced on 1 January 2023. Seizo Onoe succeeded Chaesub Lee of South Korea, who was director from 1 J ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Jonathan S
Jonathan may refer to: *Jonathan (name), a masculine given name Media * ''Jonathan'' (1970 film), a German film directed by Hans W. Geißendörfer * ''Jonathan'' (2016 film), a German film directed by Piotr J. Lewandowski * ''Jonathan'' (2018 film), an American film directed by Bill Oliver * ''Jonathan'' (Buffy comic), a 2001 comic book based on the ''Buffy the Vampire Slayer'' television series *Jonathan (TV show), a Welsh-language television show hosted by ex-rugby player Jonathan Davies People and biblical figures Bible * Jonathan (1 Samuel), son of King Saul of Israel and friend of David, in the Books of Samuel * Jonathan (Judges), in the Book of Judges * Jonathan (son of Abiathar), in 2 Samuel and 1 Kings Judaism *Jonathan Apphus, fifth son of Mattathias and leader of the Hasmonean dynasty of Judea from 161 to 143 BCE * Rabbi Jonathan, 2nd century * Jonathan (High Priest), a High Priest of Israel in the 1st century Footballers * Jonathan (footballer, born 1991) * Jonat ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Leaky Bucket As A Meter-policing
Leakey may refer to: *Leakey, Texas Leakey ( ) is a city in and the county seat of Real County, Texas, United States. The population was 315 at the 2020 census. The city is named for John H. Leakey (1824–1900), a pioneer from Tennessee. The Alto Frio Baptist Encampment is locat ..., U.S., a city * Leakey (crater), a lunar impact crater * Leakey (surname) * 7958 Leakey, an asteroid * Leakey Independent School District, a public school district based in Leakey, Texas See also * Leak (other) * * {{disambig ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
FIFO (computing And Electronics)
Representation of a FIFO queue In computing and in systems theory, first in, first out (the first in is the first out), acronymized as FIFO, is a method for organizing the manipulation of a data structure (often, specifically a data buffer) where the oldest (first) entry, or "head" of the queue, is processed first. Such processing is analogous to servicing people in a queue area on a first-come, first-served (FCFS) basis, i.e. in the same sequence in which they arrive at the queue's tail. FCFS is also the jargon term for the FIFO operating system scheduling algorithm, which gives every process central processing unit (CPU) time in the order in which it is demanded. FIFO's opposite is LIFO, last-in-first-out, where the youngest entry or "top of the stack" is processed first. A priority queue is neither FIFO or LIFO but may adopt similar behaviour temporarily or by default. Queueing theory encompasses these methods for processing data structures, as well as interactions be ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Token Bucket
The token bucket is an algorithm used in packet-switched and telecommunications networks. It can be used to check that data transmissions, in the form of packets, conform to defined limits on bandwidth and burstiness (a measure of the unevenness or variations in the traffic flow). It can also be used as a scheduling algorithm to determine the timing of transmissions that will comply with the limits set for the bandwidth and burstiness: see network scheduler. Overview The token bucket algorithm is based on an analogy of a fixed capacity bucket into which tokens, normally representing a unit of bytes or a single packet of predetermined size, are added at a fixed rate. When a packet is to be checked for conformance to the defined limits, the bucket is inspected to see if it contains sufficient tokens at that time. If so, the appropriate number of tokens, e.g. equivalent to the length of the packet in bytes, are removed ("cashed in"), and the packet is passed, e.g., for transm ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Network Interface Card
A network interface controller (NIC, also known as a network interface card, network adapter, LAN adapter and physical network interface) is a computer hardware component that connects a computer to a computer network. Early network interface controllers were commonly implemented on expansion cards that plugged into a computer bus. The low cost and ubiquity of the Ethernet standard means that most newer computers have a network interface built into the motherboard, or is contained into a USB-connected dongle, although network cards remain available. Modern network interface controllers offer advanced features such as interrupt and Direct memory access, DMA interfaces to the host processors, support for multiple receive and transmit queues, partitioning into multiple logical interfaces, and on-controller network traffic processing such as the TCP offload engine. Purpose The network controller implements the electronic circuitry required to communicate using a specific physica ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |