Bombes on:
[Wikipedia]
[Google]
[Amazon]
 The bombe () was an
The bombe () was an

 The Enigma is an
The Enigma is an  Although 105,456 is a large number, it does not guarantee security. A brute-force attack is possible: one could imagine using 100 code clerks who each tried to decode a message using 1000 distinct rotor settings. The Poles developed card catalogs so they could easily find rotor positions; Britain built "
Although 105,456 is a large number, it does not guarantee security. A brute-force attack is possible: one could imagine using 100 code clerks who each tried to decode a message using 1000 distinct rotor settings. The Poles developed card catalogs so they could easily find rotor positions; Britain built "

 The following settings of the Enigma machine must be discovered to decipher German military Enigma messages. Once these are known, all the messages for that network for that day (or pair of days in the case of the German navy) could be decrypted.
Internal settings (that required the lid of the Enigma machine to be opened)
* The selection of rotors in use in the Enigma's scrambler, and their positions on the spindle (''Walzenlage'' or "wheel order"). Possible wheel orders numbered 60 (three rotors from a choice of five) for army and air force networks and 336 (three rotors from a choice of eight) for the naval networks.
* The positions of the alphabet rings' turnover notch in relation to the core of each rotor in use (''Ringstellung'' or "ring settings"). There are 26 possible ring settings for each rotor.
External settings (that could be changed without opening the Enigma machine)
* The plugboard connections (''Steckerverbindungen'' or "stecker values"). The ten leads could be arranged in different combinations (approximately 151 trillion).
* The scrambler rotor positions at the start of enciphering the message key (the ''Grundstellung'' or "indicator-setting") — up to May 1940; or thereafter the initial positions of each rotor at the start of enciphering the message (the "message key") from which the indicator-setting could be derived. There are possible three-letter keys.
The bombe identified possible initial positions of the rotor cores and the ''stecker partner'' of a specified letter for a set of wheel orders. Manual techniques were then used to complete the decryption process. In the words of
The following settings of the Enigma machine must be discovered to decipher German military Enigma messages. Once these are known, all the messages for that network for that day (or pair of days in the case of the German navy) could be decrypted.
Internal settings (that required the lid of the Enigma machine to be opened)
* The selection of rotors in use in the Enigma's scrambler, and their positions on the spindle (''Walzenlage'' or "wheel order"). Possible wheel orders numbered 60 (three rotors from a choice of five) for army and air force networks and 336 (three rotors from a choice of eight) for the naval networks.
* The positions of the alphabet rings' turnover notch in relation to the core of each rotor in use (''Ringstellung'' or "ring settings"). There are 26 possible ring settings for each rotor.
External settings (that could be changed without opening the Enigma machine)
* The plugboard connections (''Steckerverbindungen'' or "stecker values"). The ten leads could be arranged in different combinations (approximately 151 trillion).
* The scrambler rotor positions at the start of enciphering the message key (the ''Grundstellung'' or "indicator-setting") — up to May 1940; or thereafter the initial positions of each rotor at the start of enciphering the message (the "message key") from which the indicator-setting could be derived. There are possible three-letter keys.
The bombe identified possible initial positions of the rotor cores and the ''stecker partner'' of a specified letter for a set of wheel orders. Manual techniques were then used to complete the decryption process. In the words of

 The bombe was an electro-mechanical device that replicated the action of several Enigma machines wired together. A standard German Enigma employed, at any one time, a set of three
The bombe was an electro-mechanical device that replicated the action of several Enigma machines wired together. A standard German Enigma employed, at any one time, a set of three
 A bombe run involved a cryptanalyst first obtaining a '' crib'' — a section of
A bombe run involved a cryptanalyst first obtaining a '' crib'' — a section of
 The cryptanalyst hypothesised one plugboard interconnection for the bombe to test. The other stecker values and the ring settings were worked out by hand methods.
The cryptanalyst hypothesised one plugboard interconnection for the bombe to test. The other stecker values and the ring settings were worked out by hand methods.
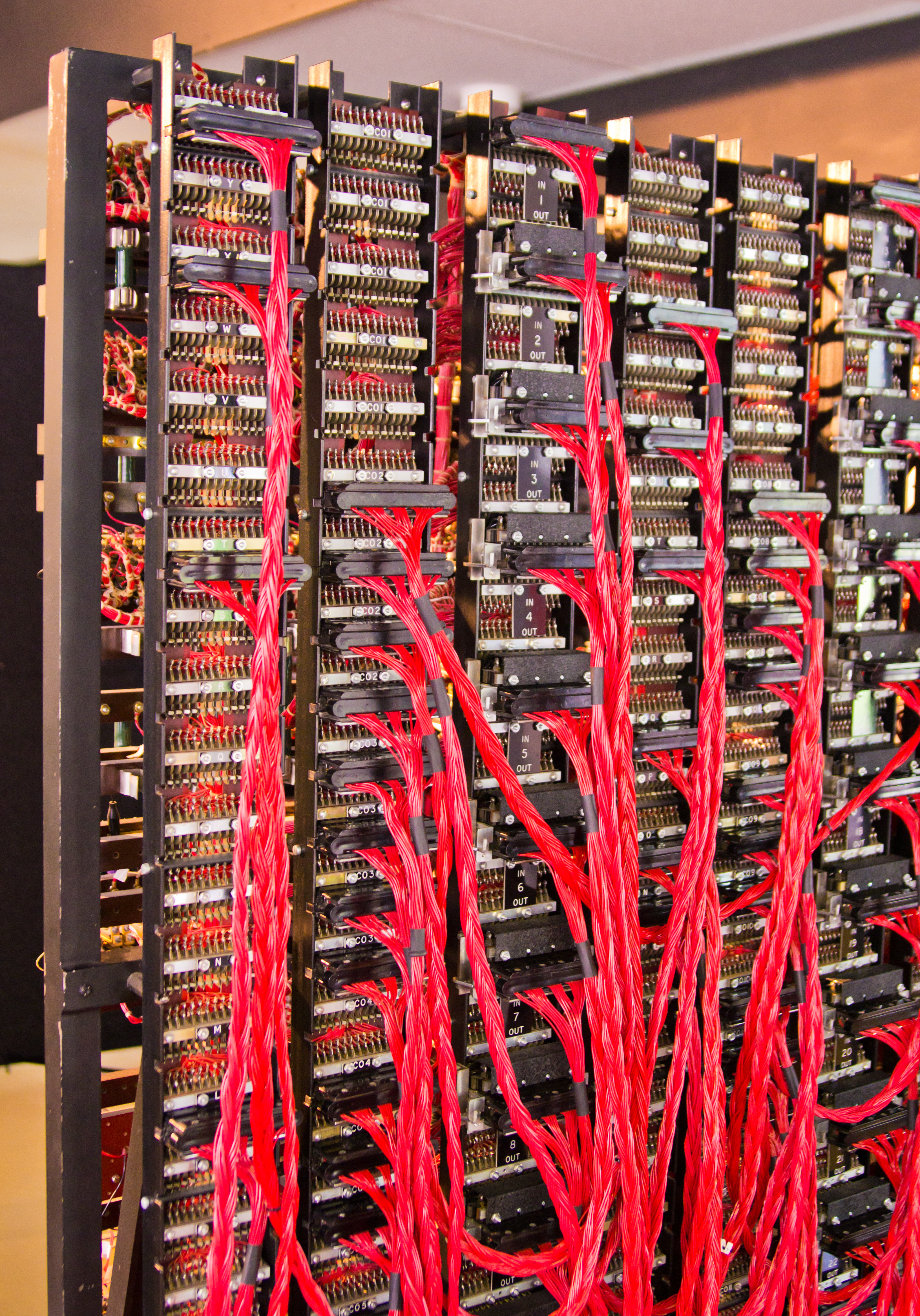 A £100,000 budget for the construction of Turing's machine was acquire
A £100,000 budget for the construction of Turing's machine was acquire
 The bombe () was an
The bombe () was an electro-mechanical
In engineering, electromechanics combines processes and procedures drawn from electrical engineering and mechanical engineering. Electromechanics focuses on the interaction of electrical and mechanical systems as a whole and how the two system ...
device used by British cryptologist
This is a list of cryptographers. Cryptography is the practice and study of techniques for secure communication in the presence of third parties called adversaries.
Pre twentieth century
* Al-Khalil ibn Ahmad al-Farahidi: wrote a (now lost) book ...
s to help decipher German Enigma-machine-encrypted secret messages during World War II
World War II or the Second World War, often abbreviated as WWII or WW2, was a world war that lasted from 1939 to 1945. It involved the World War II by country, vast majority of the world's countries—including all of the great power ...
. The US Navy
The United States Navy (USN) is the maritime service branch of the United States Armed Forces and one of the eight uniformed services of the United States. It is the largest and most powerful navy in the world, with the estimated tonnage ...
and US Army
The United States Army (USA) is the land service branch of the United States Armed Forces. It is one of the eight U.S. uniformed services, and is designated as the Army of the United States in the U.S. Constitution.Article II, section 2, c ...
later produced their own machines to the same functional specification, albeit engineered differently both from each other and from Polish and British bombes.
The British bombe was developed from a device known as the " bomba" ( pl, bomba kryptologiczna), which had been designed in Poland at the Biuro Szyfrów
The Cipher Bureau, in Polish: ''Biuro Szyfrów'' (), was the interwar Polish General Staff's Second Department's unit charged with SIGINT and both cryptography (the ''use'' of ciphers and codes) and cryptanalysis (the ''study'' of ciphers and ...
(Cipher Bureau) by cryptologist Marian Rejewski
Marian Adam Rejewski (; 16 August 1905 – 13 February 1980) was a Polish mathematician and cryptography, cryptologist who in late 1932 reconstructed the sight-unseen German military Enigma machine, Enigma cipher machine, aided by limited docu ...
, who had been breaking German Enigma
Enigma may refer to:
*Riddle, someone or something that is mysterious or puzzling
Biology
*ENIGMA, a class of gene in the LIM domain
Computing and technology
* Enigma (company), a New York-based data-technology startup
* Enigma machine, a family ...
messages for the previous seven years, using it and earlier machines. The initial design of the British bombe was produced in 1939 at the UK Government Code and Cypher School
Government Communications Headquarters, commonly known as GCHQ, is an intelligence and security organisation responsible for providing signals intelligence (SIGINT) and information assurance (IA) to the government and armed forces of the Unit ...
(GC&CS) at Bletchley Park
Bletchley Park is an English country house and estate in Bletchley, Milton Keynes (Buckinghamshire) that became the principal centre of Allied code-breaking during the Second World War. The mansion was constructed during the years following ...
by Alan Turing
Alan Mathison Turing (; 23 June 1912 – 7 June 1954) was an English mathematician, computer scientist, logician, cryptanalyst, philosopher, and theoretical biologist. Turing was highly influential in the development of theoretical c ...
, with an important refinement devised in 1940 by Gordon Welchman
William Gordon Welchman (15 June 1906 – 8 October 1985) was a British mathematician. During World War II, he worked at Britain's secret codebreaking centre, "Station X" at Bletchley Park, where he was one of the most important contributors. ...
. The engineering design and construction was the work of Harold Keen
Harold Hall "Doc" Keen (1894–1973) was a British engineer who produced the engineering design, and oversaw the construction of, the British bombe, a codebreaking machine used in World War II to read German messages sent using the Enigma machi ...
of the British Tabulating Machine Company
__NOTOC__
The British Tabulating Machine Company (BTM) was a firm which manufactured and sold Hollerith unit record equipment and other data-processing equipment. During World War II, BTM constructed some 200 " bombes", machines used at Bletchle ...
. The first bombe, code-named ''Victory'', was installed in March 1940 while the second version, ''Agnus Dei'' or ''Agnes'', incorporating Welchman's new design, was working by August 1940.
The bombe was designed to discover some of the daily settings of the Enigma machines on the various German military networks
Network, networking and networked may refer to:
Science and technology
* Network theory, the study of graphs as a representation of relations between discrete objects
* Network science, an academic field that studies complex networks
Mathematics
...
: specifically, the set of rotors
Rotor may refer to:
Science and technology
Engineering
* Rotor (electric), the non-stationary part of an alternator or electric motor, operating with a stationary element so called the stator
*Helicopter rotor, the rotary wing(s) of a rotorcraft ...
in use and their positions in the machine; the rotor core start positions for the message—the message key
Key or The Key may refer to:
Common meanings
* Key (cryptography), a piece of information that controls the operation of a cryptography algorithm
* Key (lock), device used to control access to places or facilities restricted by a lock
* Key (ma ...
—and one of the wirings of the plugboard
A plugboard or control panel (the term used depends on the application area) is an array of jacks or sockets (often called hubs) into which patch cords can be inserted to complete an electrical circuit. Control panels are sometimes used to di ...
.
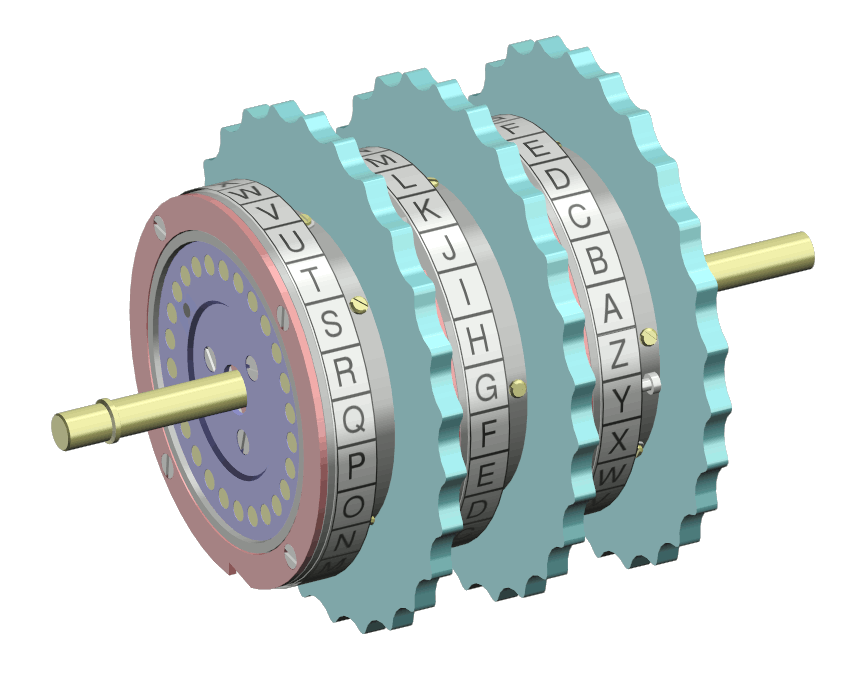
The Enigma machine

 The Enigma is an
The Enigma is an electro-mechanical
In engineering, electromechanics combines processes and procedures drawn from electrical engineering and mechanical engineering. Electromechanics focuses on the interaction of electrical and mechanical systems as a whole and how the two system ...
rotor machine
In cryptography, a rotor machine is an electro-mechanical stream cipher device used for encrypting and decrypting messages. Rotor machines were the cryptographic state-of-the-art for much of the 20th century; they were in widespread use in the 1 ...
used for the encryption
In cryptography, encryption is the process of encoding information. This process converts the original representation of the information, known as plaintext, into an alternative form known as ciphertext. Ideally, only authorized parties can dec ...
and decryption of secret messages. It was developed in Germany in the 1920s. The repeated changes of the electrical pathway from the keyboard to the lampboard implement a polyalphabetic substitution
A polyalphabetic cipher substitution, using multiple substitution alphabets. The Vigenère cipher is probably the best-known example of a polyalphabetic cipher, though it is a simplified special case. The Enigma machine is more complex but is st ...
cipher, which turns plaintext
In cryptography, plaintext usually means unencrypted information pending input into cryptographic algorithms, usually encryption algorithms. This usually refers to data that is transmitted or stored unencrypted.
Overview
With the advent of com ...
into ciphertext
In cryptography, ciphertext or cyphertext is the result of encryption performed on plaintext using an algorithm, called a cipher. Ciphertext is also known as encrypted or encoded information because it contains a form of the original plaintext ...
and back again. The Enigma's scrambler contains rotors with 26 electrical contacts on each side, whose wiring diverts the current to a different position on the two sides. When a key is pressed on the keyboard, an electric current flows through an entry drum at the right-hand end of the scrambler, then through the set of rotors to a reflecting drum (or reflector) which turns it back through the rotors and entry drum, and out to illuminate one of the lamps on the lampboard.
At each key depression, the right-hand or "fast" rotor advances one position, which causes the encipherment to change. In addition, once per rotation, the right-hand rotor causes the middle rotor to advance; the middle rotor similarly causes the left-hand (or "slow") rotor to advance. Each rotor's position is indicated by a letter of the alphabet showing through a window. The Enigma operator rotates the wheels by hand to set the start position for enciphering or deciphering a message. The three-letter sequence indicating the start position of the rotors is the "message key". There are 263 17,576 different message keys and different positions of the set of three rotors. By opening the lid of the machine and releasing a compression bar, the set of three rotors on their spindle can be removed from the machine and their sequence (called the "wheel order" at Bletchley Park) altered. Multiplying 17,576 by the six possible wheel orders gives 105,456 different ways that the scrambler can be set up.
 Although 105,456 is a large number, it does not guarantee security. A brute-force attack is possible: one could imagine using 100 code clerks who each tried to decode a message using 1000 distinct rotor settings. The Poles developed card catalogs so they could easily find rotor positions; Britain built "
Although 105,456 is a large number, it does not guarantee security. A brute-force attack is possible: one could imagine using 100 code clerks who each tried to decode a message using 1000 distinct rotor settings. The Poles developed card catalogs so they could easily find rotor positions; Britain built "''EINS''" (a common German word, meaning the number one) catalogs. Less intensive methods were also possible. If all message traffic for a day used the same rotor starting position, then frequency analysis for each position could recover the polyalphabetic substitutions. If different rotor starting positions were used, then overlapping portions of a message could be found using the index of coincidence
In cryptography, coincidence counting is the technique (invented by William F. Friedman) of putting two texts side-by-side and counting the number of times that identical letters appear in the same position in both texts. This count, either as a ...
. Many major powers (including the Germans) could break Enigma traffic if they knew the rotor wiring. The German military knew the Enigma was weak.
In 1930, the German army introduced an additional security feature, a plugboard (''Steckerbrett'' in German; each plug is a ''Stecker'', and the British cryptologists also used the word) that further scrambled the letters. The Enigma encryption is a self-inverse function, meaning that it substitutes letters reciprocally: if A is transformed into R, then R is transformed into A. The plugboard transformation maintained the self-inverse quality, but the plugboard wiring, unlike the rotor positions, does not change during the encryption. This regularity was exploited by Welchman's "diagonal board" enhancement to the bombe, which vastly increased its efficiency. With six plug leads in use (leaving 14 letters "unsteckered"), there were 100,391,791,500 possible ways of setting up the plugboard.
An important feature of the machine from a cryptanalyst's point of view, and indeed Enigma's Achilles' heel
An Achilles' heel (or Achilles heel) is a weakness in spite of overall strength, which can lead to downfall. While the mythological origin refers to a physical vulnerability, idiomatic references to other attributes or qualities that can lead to ...
, was that the reflector in the scrambler prevented a letter from being enciphered as itself. Any putative solution that gave, for any location, the same letter in the proposed plaintext and the ciphertext could therefore be eliminated.
In the lead-up to World War II
World War II or the Second World War, often abbreviated as WWII or WW2, was a world war that lasted from 1939 to 1945. It involved the World War II by country, vast majority of the world's countries—including all of the great power ...
, the Germans made successive improvements to their military Enigma machines. By January 1939, additional rotors had been introduced so that three rotors were chosen from a set of five (hence there were now 60 possible wheel orders) for the army and air force Enigmas, and three out of eight (making 336 possible wheel orders) for the navy machines. In addition, ten leads were used on the plugboard, leaving only six letters unsteckered. This meant that the air force and army Enigmas could be set up in 1.5×1019 ways. In 1941 the German navy introduced a version of Enigma with a rotatable reflector (the M4 or Four-rotor Enigma) for communicating with its U-boat
U-boats were naval submarines operated by Germany, particularly in the First and Second World Wars. Although at times they were efficient fleet weapons against enemy naval warships, they were most effectively used in an economic warfare ro ...
s. This could be set up in 1.8×1020 different ways.
Four-rotor Enigma
By late 1941 a change in German Navy fortunes in theBattle of the Atlantic
The Battle of the Atlantic, the longest continuous military campaign in World War II, ran from 1939 to the defeat of Nazi Germany in 1945, covering a major part of the naval history of World War II. At its core was the Allied naval blocka ...
, combined with intelligence reports, convinced Admiral Karl Dönitz
Karl Dönitz (sometimes spelled Doenitz; ; 16 September 1891 24 December 1980) was a Nazi Germany, German admiral who briefly succeeded Adolf Hitler as head of state in May 1945, holding the position until the dissolution of the Flensburg Gov ...
that the Allies were able to read the German Navy's coded communications, and a fourth rotor with unknown wiring was added to German Navy Enigmas used for U-boat communications, producing the ''Triton'' system, known at Bletchley Park as ''Shark''. This was coupled with a thinner reflector design to make room for the extra rotor. The Triton was designed in such a way that it remained compatible with three-rotor machines when necessary: one of the extra 'fourth' rotors, the 'beta', was designed so that when it was paired with the thin 'B' reflector, and the rotor and ring were set to 'A', the pair acted as a 'B' reflector coupled with three rotors. Fortunately for the Allies, in December 1941, before the machine went into official service, a submarine accidentally sent a message with the fourth rotor in the wrong position, and then retransmitted the message with the rotor in the correct position to emulate the three-rotor machine. In February 1942 the change in the number of rotors used became official, and the Allies' ability to read German submarines' messages ceased until a snatch from a captured U-boat revealed not only the four-rotor machine's ability to emulate a three-rotor machine, but also that the fourth rotor did not move during a message. This along with the aforementioned retransmission eventually allowed the code breakers to figure out the wiring of both the 'beta' and 'gamma' fourth rotors.
The first half of 1942 was the "Second Happy Time
The "Second Happy Time" (; officially Operation Paukenschlag ("Operation Drumbeat"), and also known among German submarine commanders as the "American Shooting Season") was a phase in the Battle of the Atlantic during which Axis submarines a ...
" for the German U-boats, with renewed success in attacking Allied shipping. This was due to the security of the new Enigma and the Germans' ability to read Allied convoy messages sent in Naval Cipher No. 3. Between January and March 1942, German submarines sank 216 ships off the US east coast. In May 1942 the US began using the convoy system and requiring a blackout of coastal cities so that ships would not be silhouetted against their lights, but this yielded only slightly improved security for Allied shipping. The Allies' failure to change their cipher for three months, together with the fact that Allied messages never contained any raw Enigma decrypts (or even mentioned that they were decrypting messages), helped convince the Germans that their messages were secure. Conversely, the Allies learned that the Germans had broken the naval cipher almost immediately from Enigma decrypts, but lost many ships due to the delay in changing the cipher.
The principle of the bombe

 The following settings of the Enigma machine must be discovered to decipher German military Enigma messages. Once these are known, all the messages for that network for that day (or pair of days in the case of the German navy) could be decrypted.
Internal settings (that required the lid of the Enigma machine to be opened)
* The selection of rotors in use in the Enigma's scrambler, and their positions on the spindle (''Walzenlage'' or "wheel order"). Possible wheel orders numbered 60 (three rotors from a choice of five) for army and air force networks and 336 (three rotors from a choice of eight) for the naval networks.
* The positions of the alphabet rings' turnover notch in relation to the core of each rotor in use (''Ringstellung'' or "ring settings"). There are 26 possible ring settings for each rotor.
External settings (that could be changed without opening the Enigma machine)
* The plugboard connections (''Steckerverbindungen'' or "stecker values"). The ten leads could be arranged in different combinations (approximately 151 trillion).
* The scrambler rotor positions at the start of enciphering the message key (the ''Grundstellung'' or "indicator-setting") — up to May 1940; or thereafter the initial positions of each rotor at the start of enciphering the message (the "message key") from which the indicator-setting could be derived. There are possible three-letter keys.
The bombe identified possible initial positions of the rotor cores and the ''stecker partner'' of a specified letter for a set of wheel orders. Manual techniques were then used to complete the decryption process. In the words of
The following settings of the Enigma machine must be discovered to decipher German military Enigma messages. Once these are known, all the messages for that network for that day (or pair of days in the case of the German navy) could be decrypted.
Internal settings (that required the lid of the Enigma machine to be opened)
* The selection of rotors in use in the Enigma's scrambler, and their positions on the spindle (''Walzenlage'' or "wheel order"). Possible wheel orders numbered 60 (three rotors from a choice of five) for army and air force networks and 336 (three rotors from a choice of eight) for the naval networks.
* The positions of the alphabet rings' turnover notch in relation to the core of each rotor in use (''Ringstellung'' or "ring settings"). There are 26 possible ring settings for each rotor.
External settings (that could be changed without opening the Enigma machine)
* The plugboard connections (''Steckerverbindungen'' or "stecker values"). The ten leads could be arranged in different combinations (approximately 151 trillion).
* The scrambler rotor positions at the start of enciphering the message key (the ''Grundstellung'' or "indicator-setting") — up to May 1940; or thereafter the initial positions of each rotor at the start of enciphering the message (the "message key") from which the indicator-setting could be derived. There are possible three-letter keys.
The bombe identified possible initial positions of the rotor cores and the ''stecker partner'' of a specified letter for a set of wheel orders. Manual techniques were then used to complete the decryption process. In the words of Gordon Welchman
William Gordon Welchman (15 June 1906 – 8 October 1985) was a British mathematician. During World War II, he worked at Britain's secret codebreaking centre, "Station X" at Bletchley Park, where he was one of the most important contributors. ...
, "... the task of the bombe was simply to reduce the assumptions of wheel order and scrambler positions that required 'further analysis' to a manageable number".
Structure

 The bombe was an electro-mechanical device that replicated the action of several Enigma machines wired together. A standard German Enigma employed, at any one time, a set of three
The bombe was an electro-mechanical device that replicated the action of several Enigma machines wired together. A standard German Enigma employed, at any one time, a set of three rotors
Rotor may refer to:
Science and technology
Engineering
* Rotor (electric), the non-stationary part of an alternator or electric motor, operating with a stationary element so called the stator
*Helicopter rotor, the rotary wing(s) of a rotorcraft ...
, each of which could be set in any of 26 positions. The standard British bombe contained 36 Enigma equivalents, each with three drums wired to produce the same scrambling effect as the Enigma rotors. A bombe could run two or three jobs simultaneously.
Each job would have a menu
In a restaurant, the menu is a list of food and beverages offered to customers and the prices. A menu may be à la carte – which presents a list of options from which customers choose – or table d'hôte, in which case a pre-established seque ...
that had to be run against a number of different wheel orders. If the menu contained 12 or fewer letters, three different wheel orders could be run on one bombe; if more than 12 letters, only two.
In order to simulate Enigma rotors, each rotor drum of the bombe had two complete sets of contacts, one for input towards the reflector and the other for output from the reflector, so that the reflected signal could pass back through a separate set of contacts. Each drum had 104 wire brushes, which made contact with the plate onto which they were loaded. The brushes and the corresponding set of contacts on the plate were arranged in four concentric circles of 26. The outer pair of circles (input and output) were equivalent to the current in an Enigma passing in one direction through the scrambler, and the inner pair equivalent to the current flowing in the opposite direction.
The interconnections within the drums between the two sets of input and output contacts were both identical to those of the relevant Enigma rotor. There was permanent wiring between the inner two sets of contacts of the three input/output plates. From there, the circuit continued to a plugboard located on the left-hand end panel, which was wired to imitate an Enigma reflector and then back through the outer pair of contacts. At each end of the "double-ended Enigma", there were sockets on the back of the machine, into which 26-way cables could be plugged.
The bombe drums were arranged with the top one of the three simulating the left-hand rotor of the Enigma scrambler, the middle one the middle rotor, and the bottom one the right-hand rotor. The top drums were all driven in synchrony by an electric motor. For each full rotation of the top drums, the middle drums were incremented by one position, and likewise for the middle and bottom drums, giving the total of 26 × 26 × 26 = positions of the 3-rotor Enigma scrambler.
The drums were colour-coded according to which Enigma rotor they emulated: I red; II maroon; III green; IV yellow; V brown; VI cobalt (blue); VII jet (black); VIII silver.
At each position of the rotors, an electric current would or would not flow in each of the 26 wires, and this would be tested in the bombe's comparator unit. For a large number of positions, the test would lead to a logical contradiction, ruling out that setting. If the test did not lead to a contradiction, the machine would stop.
The operator would record the candidate solution by reading the positions of the indicator drums and the indicator unit on the Bombe's right-hand end panel. The operator then restarted the run. The candidate solutions, ''stops'' as they were called, were processed further to eliminate as many false stops as possible. Typically, there were many false bombe stops before the correct one was found.
The candidate solutions for the set of wheel orders were subject to extensive further cryptanalytical work. This progressively eliminated the false stops, built up the set of plugboard connections and established the positions of the rotor alphabet rings. Eventually, the result would be tested on a Typex machine that had been modified to replicate an Enigma, to see whether that decryption
In cryptography, encryption is the process of encoding information. This process converts the original representation of the information, known as plaintext, into an alternative form known as ciphertext. Ideally, only authorized parties can dec ...
produced German language
German ( ) is a West Germanic language mainly spoken in Central Europe. It is the most widely spoken and official or co-official language in Germany, Austria, Switzerland, Liechtenstein, and the Italian province of South Tyrol. It is als ...
.
Bombe menu
plaintext
In cryptography, plaintext usually means unencrypted information pending input into cryptographic algorithms, usually encryption algorithms. This usually refers to data that is transmitted or stored unencrypted.
Overview
With the advent of com ...
that was thought to correspond to the ciphertext
In cryptography, ciphertext or cyphertext is the result of encryption performed on plaintext using an algorithm, called a cipher. Ciphertext is also known as encrypted or encoded information because it contains a form of the original plaintext ...
. Finding cribs was not at all straightforward; it required considerable familiarity with German military jargon and the communication habits of the operators. However, the codebreakers were aided by the fact that the Enigma would never encrypt a letter to itself. This helped in testing a possible crib against the ciphertext, as it could rule out a number of cribs and positions, where the same letter occurred in the same position in both the plaintext and the ciphertext. This was termed a ''crash'' at Bletchley Park.
Once a suitable crib had been decided upon, the cryptanalyst would produce a ''menu'' for wiring up the bombe to test the crib against the ciphertext. The following is a simplified explanation of the process of constructing a menu. Suppose that the crib is ATTACKATDAWN to be tested against a certain stretch of ciphertext, say, WSNPNLKLSTCS. The letters of the crib and the ciphertext were compared to establish pairings between the ciphertext and the crib plaintext. These were then graphed as in the diagram. It should be borne in mind that the relationships are reciprocal so that A in the plaintext associated with W in the ciphertext is the same as W in the plaintext associated with A in the ciphertext. At position 1 of the plaintext-ciphertext comparison, the letter A is associated with W, but A is also associated with P at position 4, K at position 7 and T at position 10. Building up these relationships into such a diagram provided the menu from which the bombe connections and drum start positions would be set up.
In the illustration, there are three sequences of letters which form loops (or ''cycles'' or ''closures''), ATLK, TNS and TAWCN. The more loops in the menu, the more candidate rotor settings the bombe could reject, and hence the fewer false stops.
Alan Turing conducted a very substantial analysis (without any electronic aids) to estimate how many bombe stops would be expected according to the number of letters in the menu and the number of loops. Some of his results are given in the following table. Recent bombe simulations have shown similar results.
Stecker values
The German military Enigma included a plugboard (''Steckerbrett'' in German) which swapped letters (indicated here by ) before and after the main scrambler's change (indicated by ). The plugboard connections were known to the cryptanalysts as Stecker values. If there had been no plugboard, it would have been relatively straightforward to test a rotor setting; a Typex machine modified to replicate Enigma could be set up and the crib letter encrypted on it, and compared with the ciphertext, . If they matched, the next letter would be tried, checking that encrypted to and so on for the entire length of the crib. If at any point the letters failed to match, the initial rotor setting would be rejected; most incorrect settings would be ruled out after testing just two letters. This test could be readily mechanised and applied to all settings of the rotors. However, with the plugboard, it was much harder to perform trial encryptions because it was unknown what the crib and ciphertext letters were transformed to by the plugboard. For example, in the first position, and were unknown because the plugboard settings were unknown. Turing's solution to working out the stecker values (plugboard connections) was to note that, even though the values for, say, or , were unknown, the crib still provided known relationships amongst these values; that is, the values after the plugboard transformation. Using these relationships, a cryptanalyst could reason from one to another and, potentially, derive a logical contradiction, in which case the rotor setting under consideration could be ruled out. A worked example of such reasoning might go as follows: a cryptanalyst might suppose that . Looking at position 10 of the crib:ciphertext comparison, we observe that encrypts to , or, expressed as a formula: : = Due to the function being its own inverse, we can apply it to both sides of the equation and obtain the following: : This gives us a relationship between and . If = , and for the rotor setting under consideration = (say), we can deduce that : = = While the crib does not allow us to determine what the values after the plugboard are, it does provide a constraint between them. In this case, it shows how is completely determined if is known. Likewise, we can also observe that encrypts to at position 8. Using , we can deduce the steckered value for as well using a similar argument, to get, say, : = = Similarly, in position 6, encrypts to . As the Enigma machine is self-reciprocal, this means that at the same position would also encrypt to . Knowing this, we can apply the argument once more to deduce a value for , which might be: : = And again, the same sort of reasoning applies at position 7 to get: : = However, in this case, we have derived acontradiction
In traditional logic, a contradiction occurs when a proposition conflicts either with itself or established fact. It is often used as a tool to detect disingenuous beliefs and bias. Illustrating a general tendency in applied logic, Aristotle' ...
, since, by hypothesis, we assumed that = at the outset. This means that the initial assumption must have been incorrect, and so that (for this rotor setting) ≠ (this type of argument is termed ''reductio ad absurdum
In logic, (Latin for "reduction to absurdity"), also known as (Latin for "argument to absurdity") or ''apagogical arguments'', is the form of argument that attempts to establish a claim by showing that the opposite scenario would lead to absu ...
'' or "proof by contradiction").
Automated deduction
To automate these logical deductions, the bombe took the form of an electrical circuit. Current flowed around the circuit near-instantaneously, and represented all the possible logical deductions which could be made at that position. To form this circuit, the bombe used several sets of Enigma rotor stacks wired up together according to the instructions given on a menu, derived from a crib. Because each Enigma machine had 26 inputs and outputs, the replica Enigma stacks are connected to each other using 26-way cables. In addition, each Enigma stack rotor setting is offset a number of places as determined by its position in the crib; for example, an Enigma stack corresponding to the fifth letter in the crib would be four places further on than that corresponding to the first letter.In practice
Practical bombes used several stacks of rotors spinning together to test multiple hypotheses about possible setups of the Enigma machine, such as the order of the rotors in the stack. While Turing's bombe worked in theory, it required impractically long cribs to rule out sufficiently large numbers of settings.Gordon Welchman
William Gordon Welchman (15 June 1906 – 8 October 1985) was a British mathematician. During World War II, he worked at Britain's secret codebreaking centre, "Station X" at Bletchley Park, where he was one of the most important contributors. ...
came up with a way of using the symmetry of the Enigma stecker to increase the power of the bombe. His suggestion was an attachment called the ''diagonal board'' that further improved the bombe's effectiveness.
The British Bombe
The Polish cryptologic '' bomba'' (Polish: ''bomba kryptologiczna''; plural ''bomby'') had been useful only as long as three conditions were met. First, the form of the indicator had to include the repetition of the message key; second, the number of rotors available had to be limited to three, giving six different "wheel orders" (the three rotors and their order within the machine); and third, the number of plug-board leads had to remain relatively small so that the majority of letters were ''unsteckered''. Six machines were built, one for each possible rotor order. The ''bomby'' were delivered in November 1938, but barely a month later the Germans introduced two additional rotors for loading into the Enigma scrambler, increasing the number of wheel orders by a factor of ten. Building another 54 ''bomby'' was beyond the Poles' resources. Also, on 1 January 1939, the number of plug-board leads was increased to ten. The Poles therefore had to return to manual methods, theZygalski sheets
The method of Zygalski sheets was a cryptologic technique used by the Polish Cipher Bureau before and during World War II, and during the war also by British cryptologists at Bletchley Park, to decrypt messages enciphered on German Enigma mach ...
.
Alan Turing
Alan Mathison Turing (; 23 June 1912 – 7 June 1954) was an English mathematician, computer scientist, logician, cryptanalyst, philosopher, and theoretical biologist. Turing was highly influential in the development of theoretical c ...
designed the British bombe on a more general principle, the assumption of the presence of text, called a ''crib'', that cryptanalysts could predict was likely to be present at a defined point in the message. This technique is termed a ''known plaintext attack
The known-plaintext attack (KPA) is an attack model for cryptanalysis where the attacker has access to both the plaintext (called a crib), and its encrypted version (ciphertext). These can be used to reveal further secret information such as secr ...
'' and had been used to a limited extent by the Poles, e.g., the Germans' use of "ANX" — "AN", German for "To", followed by "X" as a spacer.
 A £100,000 budget for the construction of Turing's machine was acquire
A £100,000 budget for the construction of Turing's machine was acquire