|
Trust Service Provider
A trust service provider (TSP) is a person or legal entity providing and preserving digital certificates to create and validate electronic signatures and to authenticate their signatories as well as websites in general. Trust service providers are qualified certificate authority, certificate authorities required in the European Union and in Switzerland in the context of regulated electronic signature, electronic signing procedures. History The term ''trust service provider'' was coined by the European Parliament and the European Council as important and relevance (law), relevant authority providing non-repudiation to a regulated electronic signature, electronic signing procedure. It was first brought up in the Electronic Signatures Directive 1999/93/EC and was initially named ''certification-service provider.'' The directive was repealed by the eIDAS Regulation which became official on July 1, 2016. A Regulation (European Union), regulation is a binding legislative act that requires ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Digital Certificate
In cryptography, a public key certificate, also known as a digital certificate or identity certificate, is an electronic document used to prove the validity of a public key. The certificate includes the public key and information about it, information about the identity of its owner (called the subject), and the digital signature of an entity that has verified the certificate's contents (called the issuer). If the device examining the certificate trusts the issuer and finds the signature to be a valid signature of that issuer, then it can use the included public key to communicate securely with the certificate's subject. In email encryption, code signing, and e-signature systems, a certificate's subject is typically a person or organization. However, in Transport Layer Security (TLS) a certificate's subject is typically a computer or other device, though TLS certificates may identify organizations or individuals in addition to their core role in identifying devices. TLS, sometime ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Qualified Digital Certificate
In the context of Regulation (EU) No 910/2014 (eIDAS), a qualified digital certificate is a public key certificate issued by a trust service provider which has government-issued qualifications. The certificate is designed to ensure the authentication, authenticity and data integrity of an electronic signature and its accompanying message and/or attached data. Description eIDAS defines several tiers of electronic signatures that can be used in conducting public sector and private transactions within and across the borders of member state of the European Union, EU member states. A qualified digital certificate, in addition to other specific services provided by a qualified trust service provider, is required to elevate the status of an electronic signature to that of being considered a qualified electronic signature. Using cryptography, the digital certificate, also known as a public key certificate, contains information to link it to its owner and the digital signature of the trust en ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Signature
A signature (; from , "to sign") is a depiction of someone's name, nickname, or even a simple "X" or other mark that a person writes on documents as a proof of identity and intent. Signatures are often, but not always, Handwriting, handwritten or stylized. The writer of a signature is a signatory or signer. Similar to a handwritten signature, a signature work describes the work as readily identifying its creator. A signature may be confused with an autograph, which is chiefly an artistic signature. This can lead to confusion when people have both an autograph and signature and as such some people in the public eye keep their signatures private whilst fully publishing their autograph. Function and types Identification The traditional function of a signature is to permanently affix to a document a person's uniquely personal, undeniable self-identification as physical evidence of that person's personal witness and certification of the content of all, or a specified part, of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Authentication Methods
Authentication (from ''authentikos'', "real, genuine", from αὐθέντης ''authentes'', "author") is the act of proving an assertion, such as the identity of a computer system user. In contrast with identification, the act of indicating a person or thing's identity, authentication is the process of verifying that identity. Authentication is relevant to multiple fields. In art, antiques, and anthropology, a common problem is verifying that a given artifact was produced by a certain person, or in a certain place (i.e. to assert that it is not counterfeit), or in a given period of history (e.g. by determining the age via carbon dating). In computer science, verifying a user's identity is often required to allow access to confidential data or systems. It might involve validating personal identity documents. In art, antiques and anthropology Authentication can be considered to be of three types: The ''first'' type of authentication is accepting proof of identity given by ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Certification Service Provider
A trust service provider (TSP) is a person or legal entity providing and preserving digital certificates to create and validate electronic signatures and to authenticate their signatories as well as websites in general. Trust service providers are qualified certificate authorities required in the European Union and in Switzerland in the context of regulated electronic signing procedures. History The term ''trust service provider'' was coined by the European Parliament and the European Council as important and relevant authority providing non-repudiation to a regulated electronic signing procedure. It was first brought up in the Electronic Signatures Directive 1999/93/EC and was initially named ''certification-service provider.'' The directive was repealed by the eIDAS Regulation which became official on July 1, 2016. A regulation is a binding legislative act that requires all EU member states to follow. Description The trust service provider has the responsibility to assure the i ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mozilla
Mozilla is a free software community founded in 1998 by members of Netscape. The Mozilla community uses, develops, publishes and supports Mozilla products, thereby promoting free software and open standards. The community is supported institutionally by the Nonprofit organization, non-profit Mozilla Foundation and its tax-paying subsidiary, the Mozilla Corporation. List of Mozilla products, Mozilla's current products include the Firefox web browser, Mozilla Thunderbird, Thunderbird e-mail client (now through a subsidiary), the Bugzilla bug tracking system, the Gecko (software), Gecko layout engine, and the Pocket (service), Pocket "read-it-later-online" service. History On January 23, 1998, Netscape announced that its Netscape Communicator browser software would be free, and that its source code would also be free. One day later, Jamie Zawinski of Netscape registered . The project took its name, "Mozilla", from the original code name of the Netscape Navigator browser—a por ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Internet Society
The Internet Society (ISOC) is an American non-profit advocacy organization founded in 1992 with local chapters around the world. It has offices in Reston, Virginia, United States, and Geneva, Switzerland. Organization The Internet Society has regional bureaus worldwide, composed of chapters, organizational members, and, as of July 2020, more than 70,000 individual members. The Internet Society has a staff of more than 100 and was governed by a board of trustees, whose members are appointed or elected by the society's chapters, organization members, and the Internet Engineering Task Force (IETF). The IETF comprised the Internet Society's volunteer base. Its leadership includes Chairman of the Board of Trustees, Ted Hardie; and President and CEO, Sally Wentworth. The Internet Society created the Public Interest Registry (PIR), launched the Internet Hall of Fame, and served as the organizational home of the IETF. The Internet Society Foundation was created in 2017 as its ind ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Certificate Authority
In cryptography, a certificate authority or certification authority (CA) is an entity that stores, signs, and issues digital certificates. A digital certificate certifies the ownership of a public key by the named subject of the certificate. This allows others (relying parties) to rely upon signatures or on assertions made about the private key that corresponds to the certified public key. A CA acts as a trusted third party—trusted both by the subject (owner) of the certificate and by the party relying upon the certificate. The format of these certificates is specified by the X.509 or EMV standard. One particularly common use for certificate authorities is to sign certificates used in HTTPS, the secure browsing protocol for the World Wide Web. Another common use is in issuing identity cards by national governments for use in electronically signing documents. Overview Trusted certificates can be used to create secure connections to a server via the Internet. A certificate is ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
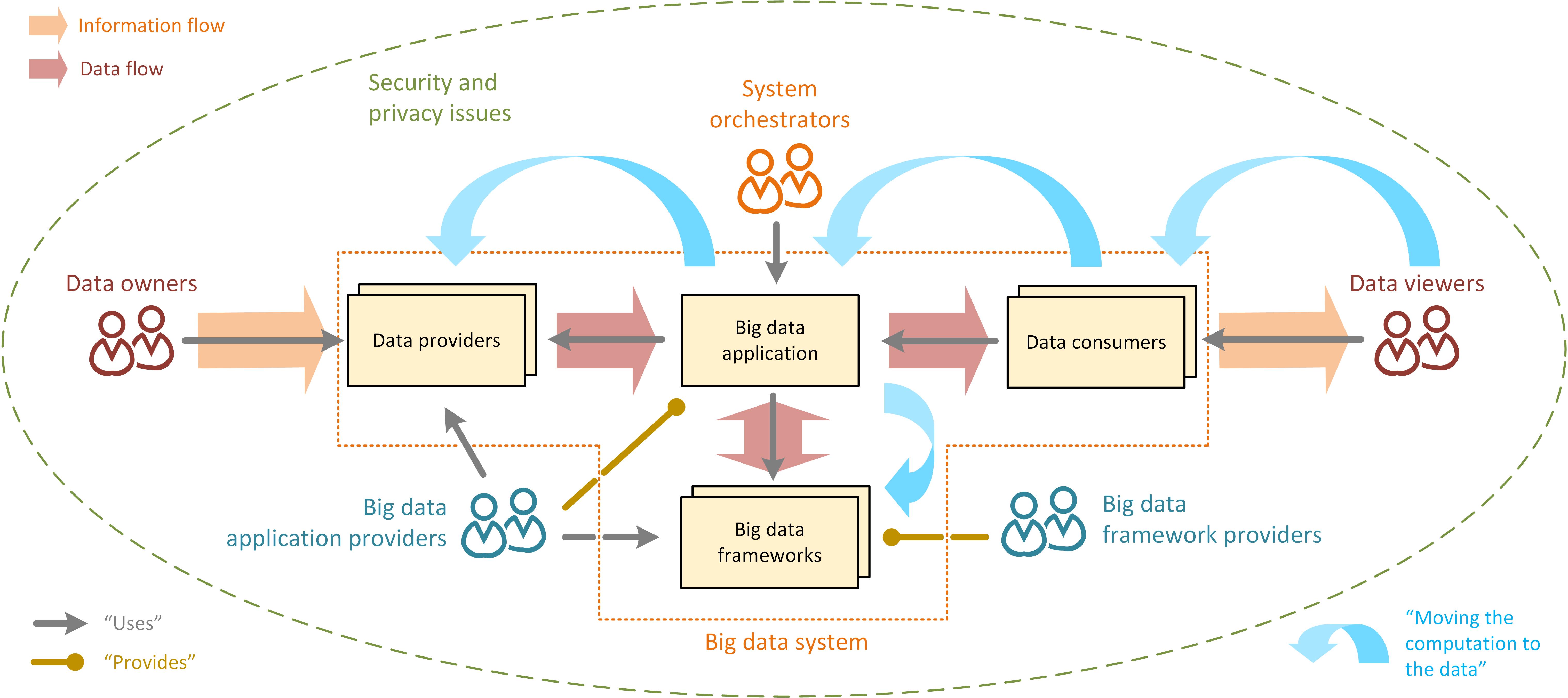
Big Data
Big data primarily refers to data sets that are too large or complex to be dealt with by traditional data processing, data-processing application software, software. Data with many entries (rows) offer greater statistical power, while data with higher complexity (more attributes or columns) may lead to a higher false discovery rate. Big data analysis challenges include Automatic identification and data capture, capturing data, Computer data storage, data storage, data analysis, search, Data sharing, sharing, Data transmission, transfer, Data visualization, visualization, Query language, querying, updating, information privacy, and data source. Big data was originally associated with three key concepts: ''volume'', ''variety'', and ''velocity''. The analysis of big data presents challenges in sampling, and thus previously allowing for only observations and sampling. Thus a fourth concept, ''veracity,'' refers to the quality or insightfulness of the data. Without sufficient investm ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Profiling (information Science)
In information science, profiling refers to the process of construction and application of user profiles generated by computerized data analysis. This is the use of algorithms or other mathematical techniques that allow the discovery of patterns or correlations in large quantities of data, aggregated in databases. When these patterns or correlations are used to identify or represent people, they can be called ''profiles''. Other than a discussion of profiling ''technologies'' or ''population profiling'', the notion of profiling in this sense is not just about the construction of profiles, but also concerns the ''application'' of group profiles to individuals, e. g., in the cases of credit scoring, price discrimination, or identification of security risks . Profiling is being used in fraud prevention, ambient intelligence, consumer analytics, and surveillance. Statistical methods of profiling include Knowledge Discovery in Databases (KDD). The profiling process Th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Digital Signature Algorithm
The Digital Signature Algorithm (DSA) is a Public-key cryptography, public-key cryptosystem and Federal Information Processing Standards, Federal Information Processing Standard for digital signatures, based on the mathematical concept of modular exponentiation and the Discrete logarithm, discrete logarithm problem. In a digital signature system, there is a keypair involved, consisting of a private and a public key. In this system a signing entity that declared their public key can generate a signature using their private key, and a verifier can assert the source if it verifies the signature correctly using the declared public key. DSA is a variant of the Schnorr signature, Schnorr and ElGamal signature scheme, ElGamal signature schemes. The National Institute of Standards and Technology (NIST) proposed DSA for use in their Digital Signature Standard (DSS) in 1991, and adopted it as FIPS 186 in 1994. Five revisions to the initial specification have been released. The newest specifi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
ZertES
ZertES is a Swiss Federal law that regulates the conditions under which trust service providers may use certification services with electronic signatures. Additionally, this law provides a framework that outlines the provider’s obligations and rights as they apply to providing their certification services. Description ZertES was approved into law on December 19, 2003. The law promotes the use of secure services for electronic certification to facilitate the use of qualified electronic signatures. Under this law, the signatures would be equal to a handwritten signature. Switzerland’s ZertES law possesses a similar tiered structure and standards of legal value as the European Union’s eIDAS Regulation. ZertES provides several assurance levels; qualified electronic signatures is the highest level, equivalent to a handwritten signature. For many official documents, it is required that the electronic signatures used be at this qualified electronic signature level. Standards Unde ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |