|
Tabnabbing
Tabnabbing is a computer exploit and phishing attack, which persuades users to submit their login details and passwords to popular websites by impersonating those sites and convincing the user that the site is genuine. The attack's name was coined in early 2010 by Aza Raskin, a security researcher and design expert. The attack takes advantage of user trust and inattention to detail in regard to tabs, and the ability of browsers to navigate across a page's origin in inactive tabs a long time after the page is loaded. Tabnabbing is different from most phishing attacks in that the user no longer remembers that a certain tab was the result of a link unrelated to the login page, because the fake login page is loaded in one of the long-lived open tabs in their browser. The attack causes the browser to navigate to the impersonated page after the page has been left unattended for some time. A user who returns after a while and sees the login page may be induced to believe the page is le ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Aza Raskin
Aza Raskin (born February 1, 1984) is the co-founder of the Center for Humane Technology and of the Earth Species Project. He is also a writer, entrepreneur, inventor, and interface designer. He is the son of Jef Raskin, a human–computer interface expert who was the initiator of the Macintosh project at Apple. Raskin is an advocate for the ethical use of technology, and has been critical of the effects that modern technology has on everyday lives and society. In the podcast ''Your Undivided Attention'', along with Tristan Harris, Raskin has talked extensively about the power of information technology and the dangers it potentially poses to modern society. In 2019, he became a member of the World Economic Forum's Global AI Council. Raskin coined the phrase, " freedom of speech is not freedom of reach," which was the title of an article that he wrote with Renée DiResta. The phrase is now widely used to refer to the large-scale implications of platform amplification and free sp ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Exploit (computer Security)
An exploit (from the English verb ''to exploit'', meaning "to use something to one’s own advantage") is a piece of software, a chunk of data, or a sequence of commands that takes advantage of a bug or vulnerability to cause unintended or unanticipated behavior to occur on computer software, hardware, or something electronic (usually computerized). Such behavior frequently includes things like gaining control of a computer system, allowing privilege escalation, or a denial-of-service (DoS or related DDoS) attack. In lay terms, some exploit is akin to a 'hack'. Classification There are several methods of classifying exploits. The most common is by how the exploit communicates to the vulnerable software. A ''remote exploit'' works over a network and exploits the security vulnerability without any prior access to the vulnerable system. A ''local exploit'' requires prior access to the vulnerable system and usually increases the privileges of the person running the exploit past t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
HTML Attribute
HTML attributes are special words used inside the opening tag to control the element's behaviour. HTML attributes are a modifier of an ''HTML element type''. An attribute either modifies the default functionality of an element type or provides functionality to certain element types unable to function correctly without them. In HTML syntax, an attribute is added to an '' HTML start tag''. Several basic attributes types have been recognized, including: (1) ''required attributes'', needed by a particular element type for that element type to function correctly; (2) ''optional attributes'', used to modify the default functionality of an element type; (3) ''standard attributes'', supported by many element types; and (4) ''event attributes'', used to cause element types to specify scripts to be run under specific circumstances. Some attribute types function differently when used to modify different element types. For example, the attribute ''name'' is used by several element types, but ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hacker (computer Security)
A security hacker is someone who explores methods for breaching defenses and exploiting weaknesses in a computer system or network. Hackers may be motivated by a multitude of reasons, such as profit, protest, information gathering, challenge, recreation, or evaluation of a system weaknesses to assist in formulating defenses against potential hackers. The subculture that has evolved around hackers is often referred to as the "computer underground". Longstanding controversy surrounds the meaning of the term " hacker." In this controversy, computer programmers reclaim the term ''hacker'', arguing that it refers simply to someone with an advanced understanding of computers and computer networks and that ''cracker'' is the more appropriate term for those who break into computers, whether computer criminals (black hats) or computer security experts ( white hats). A 2014 article noted that "the black-hat meaning still prevails among the general public". History Birth of subc ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Phishing
Phishing is a type of social engineering where an attacker sends a fraudulent (e.g., spoofed, fake, or otherwise deceptive) message designed to trick a person into revealing sensitive information to the attacker or to deploy malicious software on the victim's infrastructure like ransomware. Phishing attacks have become increasingly sophisticated and often transparently mirror the site being targeted, allowing the attacker to observe everything while the victim is navigating the site, and transverse any additional security boundaries with the victim. As of 2020, phishing is by far the most common attack performed by cybercriminals, the FBI's Internet Crime Complaint Centre recording over twice as many incidents of phishing than any other type of computer crime. The first recorded use of the term "phishing" was in the cracking toolkit AOHell created by Koceilah Rekouche in 1995; however, it is possible that the term was used before this in a print edition of the hacker maga ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Citibank
Citibank, N. A. (N. A. stands for " National Association") is the primary U.S. banking subsidiary of financial services multinational Citigroup. Citibank was founded in 1812 as the City Bank of New York, and later became First National City Bank of New York. The bank has 2,649 branches in 19 countries, including 723 branches in the United States and 1,494 branches in Mexico operated by its subsidiary Banamex. The U.S. branches are concentrated in six metropolitan areas: New York, Chicago, Los Angeles, San Francisco, Washington, D.C., and Miami. It was founded as City Bank of New York and became National City Bank of New York. It has had an important role in war bonds. It has had a role in international events including the U.S. invasion of Haiti. History Early history The City Bank of New York was founded on June 16, 1812. The first president of the City Bank was the statesman and retired Colonel, Samuel Osgood. After Osgood's death in August 1813, William Few beca ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
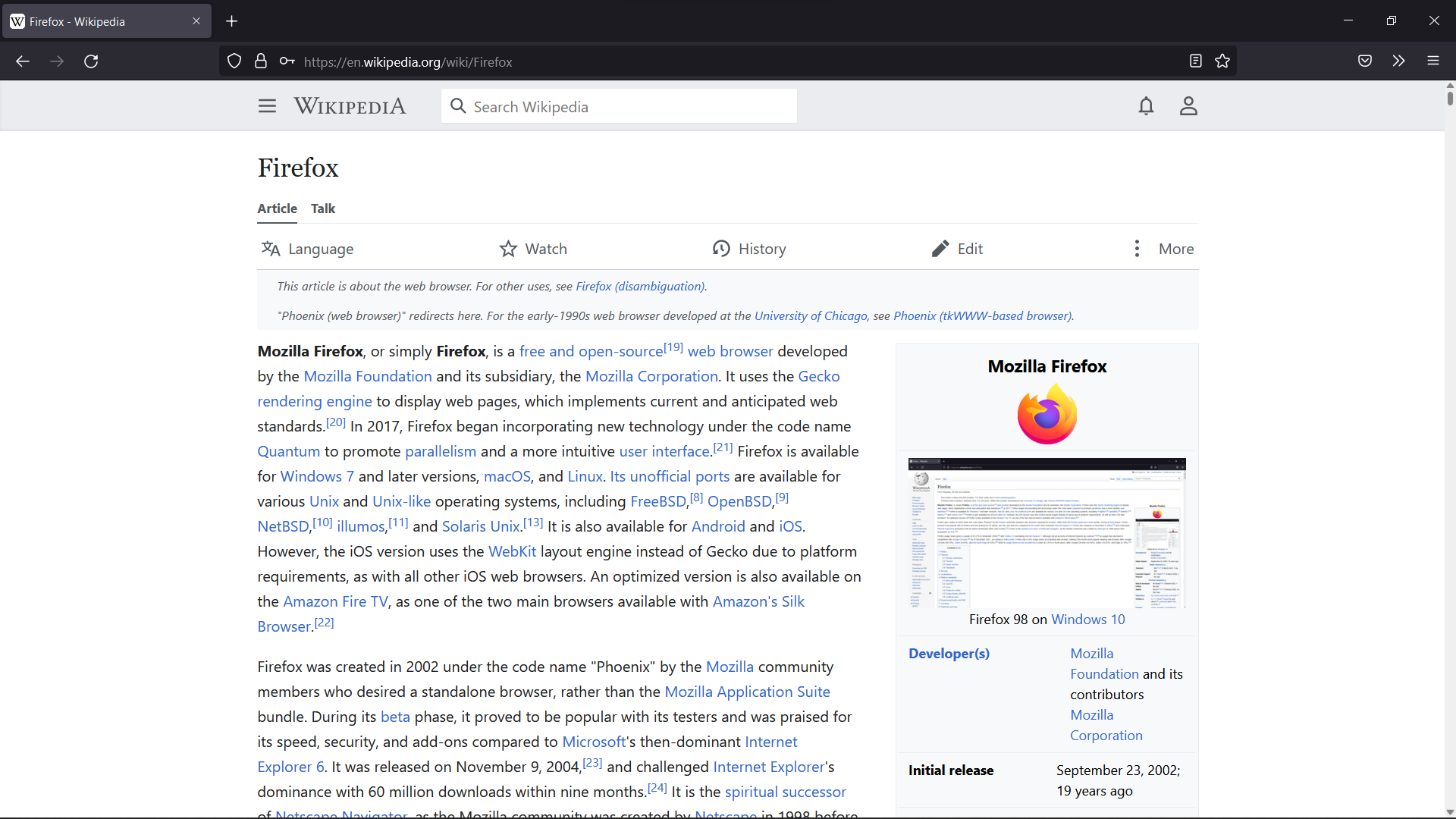
Firefox
Mozilla Firefox, or simply Firefox, is a free and open-source web browser developed by the Mozilla Foundation and its subsidiary, the Mozilla Corporation. It uses the Gecko rendering engine to display web pages, which implements current and anticipated web standards. In November 2017, Firefox began incorporating new technology under the code name " Quantum" to promote parallelism and a more intuitive user interface. Firefox is available for Windows 7 and later versions, macOS, and Linux. Its unofficial ports are available for various Unix and Unix-like operating systems, including FreeBSD, OpenBSD, NetBSD, illumos, and Solaris Unix. It is also available for Android and iOS. However, as with all other iOS web browsers, the iOS version uses the WebKit layout engine instead of Gecko due to platform requirements. An optimized version is also available on the Amazon Fire TV as one of the two main browsers available with Amazon's Silk Browser. Firefox was created in 2002 unde ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mozilla
Mozilla (stylized as moz://a) is a free software community founded in 1998 by members of Netscape. The Mozilla community uses, develops, spreads and supports Mozilla products, thereby promoting exclusively free software and open standards, with only minor exceptions. The community is supported institutionally by the non-profit Mozilla Foundation and its tax-paying subsidiary, the Mozilla Corporation. Mozilla's current products include the Firefox web browser, Thunderbird e-mail client (now through a subsidiary), Bugzilla bug tracking system, Gecko layout engine, Pocket "read-it-later-online" service, and others. History On January 23, 1998, Netscape made two announcements. First, that Netscape Communicator would be free; second, that the source code would also be free. One day later, Jamie Zawinski from Netscape registered . The project took its name "Mozilla", after the original code name of the Netscape Navigator browser—a portmanteau of "Mosaic and Godzill ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
NoScript
NoScript (or NoScript Security Suite) is a free software extension for Mozilla Firefox, SeaMonkey, other Mozilla-based web browsers and Google Chrome, written and maintained by Giorgio Maone, an Italian software developer and member of the Mozilla Security Group. Features Active content blocking By default, NoScript blocks active (executable) web content, which can be wholly or partially unblocked by allowlisting a site or domain from the extension's toolbar menu or by clicking a placeholder icon. In the default configuration, active content is globally denied, although the user may turn this around and use NoScript to block specific unwanted content. The allowlist may be permanent or temporary (until the browser closes or the user revokes permissions). Active content may consist of JavaScript, web fonts, media codecs, WebGL, and Flash. The add-on also offers specific countermeasures against security exploits. Because many web browser attacks require active content that th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Meta Element
Meta elements are tags used in HTML and XHTML documents to provide structured metadata about a Web page. They are part of a web page's head section. Multiple Meta elements with different attributes can be used on the same page. Meta elements can be used to specify page description, keywords and any other metadata not provided through the other head elements and attributes. The meta element has two uses: either to emulate the use of an HTTP response header field, or to embed additional metadata within the HTML document. With HTML up to and including HTML 4.01 and XHTML, there were four valid attributes: content, http-equiv, name and scheme. Under HTML 5, charset has been added and scheme has been removed. http-equiv is used to emulate an HTTP header, and name to embed metadata. The value of the statement, in either case, is contained in the content attribute, which is the only required attribute unless charset is given. charset is used to indicate the character set of the do ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Phishing
Phishing is a type of social engineering where an attacker sends a fraudulent (e.g., spoofed, fake, or otherwise deceptive) message designed to trick a person into revealing sensitive information to the attacker or to deploy malicious software on the victim's infrastructure like ransomware. Phishing attacks have become increasingly sophisticated and often transparently mirror the site being targeted, allowing the attacker to observe everything while the victim is navigating the site, and transverse any additional security boundaries with the victim. As of 2020, phishing is by far the most common attack performed by cybercriminals, the FBI's Internet Crime Complaint Centre recording over twice as many incidents of phishing than any other type of computer crime. The first recorded use of the term "phishing" was in the cracking toolkit AOHell created by Koceilah Rekouche in 1995; however, it is possible that the term was used before this in a print edition of the hacker maga ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Meta Refresh
Meta refresh is a method of instructing a web browser to automatically refresh the current web page or frame after a given time interval, using an HTML meta element with the http-equiv parameter set to "refresh" and a content parameter giving the time interval in seconds. It is also possible to instruct the browser to fetch a different URL when the page is refreshed, by including the alternative URL in the content parameter. By setting the refresh time interval to zero (or a very low value), meta refresh can be used as a method of URL redirection. History This feature was originally introduced by Netscape Navigator 1.1 (circa 1995), in a form of HTTP header and corresponding HTML meta HTTP-equivalent element, which allows document author to signal client to automatically reload the document or change to a specified URL after a specified timeout. It is the earliest polling mechanism available for the web, allowing a user to see the latest update in a frequently-changing webpage, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |