|
Source Routing
In computer networking, source routing, also called path addressing, allows a sender of a data packet to partially or completely specify the route the packet takes through the network. In contrast, in conventional routing, routers in the network determine the path incrementally based on the packet's destination. Another routing alternative, label switching, is used in connection-oriented networks such as X.25, Frame Relay, Asynchronous Transfer Mode and Multiprotocol Label Switching. Source routing allows easier troubleshooting, improved traceroute, and enables a node to discover all the possible routes to a host. It does not allow a source to directly manage network performance by forcing packets to travel over one path to prevent congestion on another. Many high-performance interconnects including Myrinet, Quadrics, IEEE 1355, and SpaceWire support source routing. Internet Protocol In the Internet Protocol, two header options are available which are rarely used: " strict so ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Networking
A computer network is a collection of communicating computers and other devices, such as printers and smart phones. In order to communicate, the computers and devices must be connected by wired media like copper cables, optical fibers, or by wireless communication. The devices may be connected in a variety of network topologies. In order to communicate over the network, computers use agreed-on rules, called communication protocols, over whatever medium is used. The computer network can include personal computers, Server (computing), servers, networking hardware, or other specialized or general-purpose Host (network), hosts. They are identified by network addresses and may have hostnames. Hostnames serve as memorable labels for the nodes and are rarely changed after initial assignment. Network addresses serve for locating and identifying the nodes by communication protocols such as the Internet Protocol. Computer networks may be classified by many criteria, including the tr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Internet Protocol Options
There are a number of optional parameters that may be present in an Internet Protocol version 4 datagram. They typically configure a number of behaviors such as for the method to be used during source routing, some control and probing facilities and a number of experimental features. Available options The possible options that can be put in the IPv4 header are as follows: The table below shows the defined options for IPv4. The ''Option Type'' column is derived from the ''Copied'', ''Option Class'', and ''Option Number'' bits as defined above. Loose source routing Loose Source Routing is an IP option which can be used for address translation. LSR is also used to implement mobility in IP networks. Loose source routing uses a source routing option in IP to record the set of routers a packet must visit. The destination of the packet is replaced with the next router the packet must visit. By setting the forwarding agent (FA) to one of the routers that the packet must visit, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Scalable Source Routing
Scalable Source Routing (SSR) is a routing protocol for unstructured networks such as mobile ad hoc networks, mesh networks, or sensor networks. It combines source routing with routing along a virtual ring, and is based on the idea of "pushing Chord into the underlay". Concepts Virtual ring SSR operates on a flat address space which is organized as a virtual ring. This is a popular concept in peer-to-peer overlay networks like Chord. The common knowledge about the ring structure enables nodes to route packets without knowing the topology of the underlying physical network. While the physical network can be very dynamic, the structure of the virtual ring remains rather static. Therefore, flooding the physical network can be avoided. Packets travel along the ring so that they decrease the virtual distance to the destination (that is, the absolute difference of the addresses). When each node knows its correct predecessor and successor in the virtual ring, delivery to the correct ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Policy-based Routing
In computer networking, policy-based routing (PBR) is a technique used to make routing decisions based on policies set by the network administrator. When a router (computing), router receives a packet it normally decides where to forward it based on the destination address in the packet, which is then used to look up an entry in a routing table. However, in some cases, there may be a need to forward the packet based on other criteria. For example, a network administrator might want to forward a packet based on the source address, not the destination address. This permits routing of packets originating from different sources to different networks even when the destinations are the same and can be useful when interconnecting several private networks. Policy-based routing may also be based on the size of the packet, the protocol of the payload, or other information available in a packet header or payload. In the Cisco IOS, PBR is implemented using ''route maps''. Linux supports m ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Dynamic Source Routing
Dynamic Source Routing (DSR) is a routing protocol for wireless mesh networks. It is similar to AODV in that it forms a route on-demand when a transmitting node requests one. However, it uses source routing instead of relying on the routing table at each intermediate device. Usually, in environments where infrastructure like routers and access points are absent, DSR enables efficient data packet routing by relying on the cooperation of individual nodes to relay messages to the intended destinations. This protocol plays a crucial role in mobile ad hoc networks (MANETs), where network topology can frequently change due to node mobility, leading to the need for adaptive, efficient routing. Background Determining the source route requires accumulating the address of each device between the source and destination during route discovery. The accumulated path information is cached by nodes processing the route discovery packets. The learned paths are used to route packet ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Bang Path
UUCP (Unix-to-Unix Copy) is a suite of computer programs and protocols allowing remote execution of commands and transfer of files, email and netnews between computers. A command named is one of the programs in the suite; it provides a user interface for requesting file copy operations. The UUCP suite also includes (user interface for remote command execution), (the communication program that performs the file transfers), (reports statistics on recent activity), (execute commands sent from remote machines), and (reports the UUCP name of the local system). Some versions of the suite include / (convert 8-bit binary files to 7-bit text format and vice versa). Although UUCP was originally developed on Unix in the 1970s and 1980s, and is most closely associated with Unix-like systems, UUCP implementations exist for several non-Unix-like operating systems, including DOS, OS/2, OpenVMS (for VAX hardware only), AmigaOS, classic Mac OS, and even CP/M. History UUCP was original ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
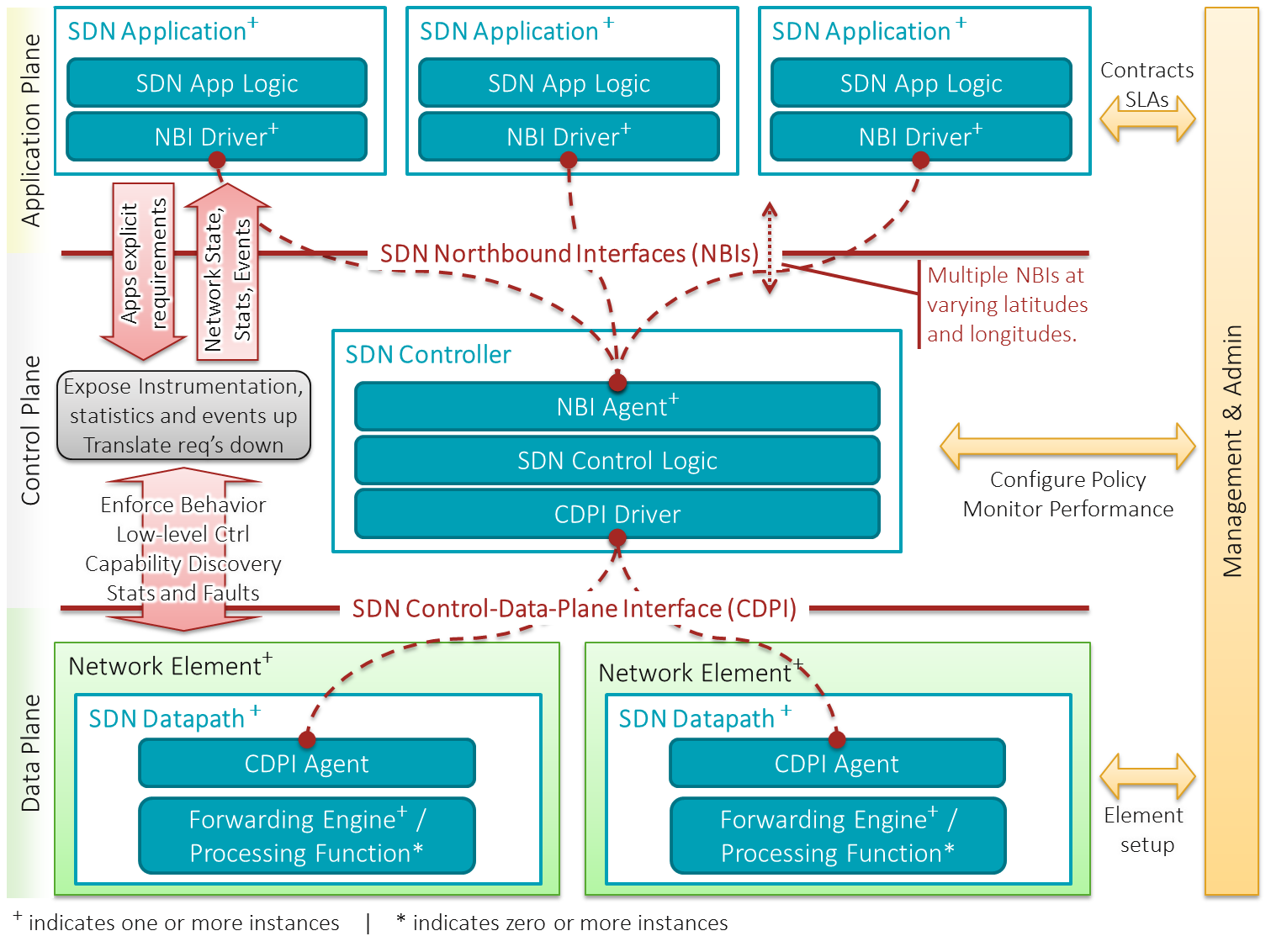
Software-defined Networking
Software-defined networking (SDN) is an approach to network management that uses abstraction to enable dynamic and programmatically efficient network configuration to create grouping and segmentation while improving network performance and monitoring in a manner more akin to cloud computing than to traditional network management. SDN is meant to improve the static architecture of traditional networks and may be employed to centralize network intelligence in one network component by disassociating the forwarding process of network packets ( data plane) from the routing process ( control plane). The control plane consists of one or more controllers, which are considered the brains of the SDN network, where the whole intelligence is incorporated. However, centralization has certain drawbacks related to security, scalability and elasticity. SDN was commonly associated with the OpenFlow protocol for remote communication with network plane elements to determine the path of network pac ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Segment Routing
Segment routing, a form of computer networking, is a modern variant of source routing that is being developed within thSPRINGand IPv6 working groups of the IETF. In a segment routed network, an ingress node may prepend a header to packets that contain a list of segments, which are instructions that are executed on subsequent nodes in the network. These instructions may be forwarding instructions, such as an instruction to forward a packet to a specific destination or interface. Segment routing works either on top of a MPLS network or on an IPv6 network. In an MPLS network, segments are encoded as MPLS labels. Under IPv6, a new header called a Segment Routing Header (SRH) is used. Segments in a SRH are encoded in a list of IPv6 addresses. The ''5f00::/16'' prefix has been allocated for this purpose as part of an Internet-Draft. See also * Bang path * Dynamic Source Routing Dynamic Source Routing (DSR) is a routing protocol for wireless mesh networks. It is similar to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
IETF
The Internet Engineering Task Force (IETF) is a standards organization for the Internet standard, Internet and is responsible for the technical standards that make up the Internet protocol suite (TCP/IP). It has no formal membership roster or requirements and all its participants are volunteers. Their work is usually funded by employers or other sponsors. The IETF was initially supported by the federal government of the United States but since 1993 has operated under the auspices of the Internet Society, a non-profit organization with local chapters around the world. Organization There is no membership in the IETF. Anyone can participate by signing up to a working group mailing list, or registering for an IETF meeting. The IETF operates in a bottom-up task creation mode, largely driven by working groups. Each working group normally has appointed two co-chairs (occasionally three); a charter that describes its focus; and what it is expected to produce, and when. It is open ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Attack (computing)
A cyberattack (or cyber attack) occurs when there is an unauthorized action against computer infrastructure that compromises the confidentiality, integrity, or availability of its content. The rising dependence on increasingly complex and interconnected computer systems in most domains of life is the main factor that causes vulnerability to cyberattacks, since virtually all computer systems have bugs that can be exploited by attackers. Although it is impossible or impractical to create a perfectly secure system, there are many defense mechanisms that can make a system more difficult to attack, making information security a field of rapidly increasing importance in the world today. Perpetrators of a cyberattack can be criminals, hacktivists, or states. They attempt to find weaknesses in a system, exploit them and create malware to carry out their goals, and deliver it to the targeted system. Once installed, the malware can have a variety of effects depending on its purpose. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
IPv6
Internet Protocol version 6 (IPv6) is the most recent version of the Internet Protocol (IP), the communication protocol, communications protocol that provides an identification and location system for computers on networks and routes traffic across the Internet. IPv6 was developed by the Internet Engineering Task Force (IETF) to deal with the long-anticipated problem of IPv4 address exhaustion, and was intended to replace IPv4. In December 1998, IPv6 became a Draft Standard for the IETF, which subsequently ratified it as an Internet Standard on 14 July 2017. Devices on the Internet are assigned a unique IP address for identification and location definition. With the rapid growth of the Internet after commercialization in the 1990s, it became evident that far more addresses would be needed to connect devices than the 4,294,967,296 (232) IPv4 address space had available. By 1998, the IETF had formalized the successor protocol, IPv6 which uses 128-bit addresses, theoretically all ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
IP Address Spoofing
In computer networking, IP address spoofing or IP spoofing is the creation of Internet Protocol (IP) packets with a false source IP address, for the purpose of impersonating another computing system. Background The basic protocol for sending data over the Internet network and many other computer networks is the Internet Protocol (IP). The protocol specifies that each IP packet must have a header which contains (among other things) the IP address of the sender of the packet. The source IP address is normally the address that the packet was sent from, but the sender's address in the header can be altered, so that to the recipient it appears that the packet came from another source. The protocol requires the receiving computer to send back a response to the source IP address therefore spoofing is mainly used when the sender can anticipate the network response or does not care about the response. The source IP address provides only limited information about the sender. It may pr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |