|
Security Through Obscurity
In security engineering, security through obscurity is the practice of concealing the details or mechanisms of a system to enhance its security. This approach relies on the principle of hiding something in plain sight, akin to a magician's sleight of hand or the use of camouflage. It diverges from traditional security methods, such as physical locks, and is more about obscuring information or characteristics to deter potential threats. Examples of this practice include disguising sensitive information within commonplace items, like a piece of paper in a book, or altering digital footprints, such as spoofing a web browser's version number. While not a standalone solution, security through obscurity can complement other security measures in certain scenarios. Obscurity in the context of security engineering is the notion that information can be protected, to a certain extent, when it is difficult to access or comprehend. This concept hinges on the principle of making the details ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Security Through Obscurity Hiding A Key On A Car Tyre
Security is protection from, or resilience against, potential harm (or other unwanted coercion). Beneficiaries (technically referents) of security may be persons and social groups, objects and institutions, ecosystems, or any other entity or phenomenon vulnerable to unwanted change. Security mostly refers to protection from hostile forces, but it has a wide range of other senses: for example, as the absence of harm (e.g., freedom from want); as the presence of an essential good (e.g., food security); as resilience against potential damage or harm (e.g. secure foundations); as secrecy (e.g., a secure telephone line); as containment (e.g., a secure room or cell); and as a state of mind (e.g., emotional security). Security is both a feeling and a state of reality. One might feel secure when one is not actually so; or might feel insecure despite being safe. This distinction is usually not very clear to express in the English language. The term is also used to refer to acts and sy ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
United States
The United States of America (USA), also known as the United States (U.S.) or America, is a country primarily located in North America. It is a federal republic of 50 U.S. state, states and a federal capital district, Washington, D.C. The 48 contiguous states border Canada to the north and Mexico to the south, with the semi-exclave of Alaska in the northwest and the archipelago of Hawaii in the Pacific Ocean. The United States asserts sovereignty over five Territories of the United States, major island territories and United States Minor Outlying Islands, various uninhabited islands in Oceania and the Caribbean. It is a megadiverse country, with the world's List of countries and dependencies by area, third-largest land area and List of countries and dependencies by population, third-largest population, exceeding 340 million. Its three Metropolitan statistical areas by population, largest metropolitan areas are New York metropolitan area, New York, Greater Los Angeles, Los Angel ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Steganography
Steganography ( ) is the practice of representing information within another message or physical object, in such a manner that the presence of the concealed information would not be evident to an unsuspecting person's examination. In computing/electronic contexts, a computer file, message, image, or video is concealed within another file, message, image, or video. Generally, the hidden messages appear to be (or to be part of) something else: images, articles, shopping lists, or some other cover text. For example, the hidden message may be in invisible ink between the visible lines of a private letter. Some implementations of steganography that lack a formal shared secret are forms of security through obscurity, while key-dependent steganographic schemes try to adhere to Kerckhoffs's principle. The word ''steganography'' comes from Greek ''steganographia'', which combines the words ''steganós'' (), meaning "covered or concealed", and ''-graphia'' () meaning "writing". The fir ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Deception Technology
Deception technology (also deception and disruption technology) is a category of cyber security defense mechanisms that provide early warning of potential cyber security attacks and alert organizations of unauthorized activity. Deception technology products can detect, analyze, and defend against zero-day and advanced attacks, often in real time. They are automated, accurate, and provide insight into malicious activity within internal networks which may be unseen by other types of cyber defense. Deception technology seeks to deceive an attacker, detect them, and then defeat them. Deception technology considers the point of view of human attackers and method for exploiting and navigating networks to identify and exfiltrate data. It integrates with existing technologies to provide new visibility into the internal networks, share high probability alerts and threat intelligence with the existing infrastructure. Technology: High level view Deception technology automates the creatio ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cybersecurity
Computer security (also cybersecurity, digital security, or information technology (IT) security) is a subdiscipline within the field of information security. It consists of the protection of computer software, systems and networks from threats that can lead to unauthorized information disclosure, theft or damage to hardware, software, or data, as well as from the disruption or misdirection of the services they provide. The significance of the field stems from the expanded reliance on computer systems, the Internet, and wireless network standards. Its importance is further amplified by the growth of smart devices, including smartphones, televisions, and the various devices that constitute the Internet of things (IoT). Cybersecurity has emerged as one of the most significant new challenges facing the contemporary world, due to both the complexity of information systems and the societies they support. Security is particularly crucial for systems that govern large-scale sy ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Operations Security
Operations security (OPSEC) is a process that identifies critical information to determine whether friendly actions can be observed by enemy intelligence, determines if information obtained by adversaries could be interpreted to be useful to them, and then executes selected measures that eliminate or reduce adversary exploitation of friendly critical information. The term "operations security" was coined by the United States military during the Vietnam War. History Vietnam In 1966, United States Admiral Ulysses Sharp established a multidisciplinary security team to investigate the failure of certain combat operations during the Vietnam War. This operation was dubbed Operation Purple Dragon, and included personnel from the National Security Agency and the Department of Defense. When the operation concluded, the Purple Dragon team codified their recommendations. They called the process "Operations Security" in order to distinguish the process from existing processes and e ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Open Security
Open security is the use of open source philosophies and methodologies to approach computer security and other information security challenges. Traditional application security is based on the premise that any application or service (whether it is malware or desirable) relies on security through obscurity. Open source approaches have created technology such as Linux (and to some extent, the Android operating system). Additionally, open source approaches applied to documents have inspired wikis and their largest example, Wikipedia. Open security suggests that security breaches and vulnerabilities can be better prevented or ameliorated when users facing these problems collaborate using open source philosophies. This approach requires that users be legally allowed to collaborate, so relevant software would need to be released under a license that is widely accepted to be open source; examples include the Massachusetts Institute of Technology (MIT) license, the Apache 2.0 license, the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Security By Design
Secure by design, in software engineering, means that software products and capabilities have been designed to be foundationally secure. Alternate security strategies, tactics and patterns are considered at the beginning of a software design, and the best are selected and enforced by the architecture, and they are used as guiding principles for developers. It is also encouraged to use strategic design patterns that have beneficial effects on security, even though those design patterns were not originally devised with security in mind. Secure by Design is increasingly becoming the mainstream development approach to ensure security and privacy of software systems. In this approach, security is considered and built into the system at every layer and starts with a robust architecture design. Security architectural design decisions are based on well-known security strategies, tactics, and patterns defined as reusable techniques for achieving specific quality concerns. Security tact ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Arms Race
An arms race occurs when two or more groups compete in military superiority. It consists of a competition between two or more State (polity), states to have superior armed forces, concerning production of weapons, the growth of a military, and the aim of superior military technology. Unlike a racing, sporting race, which constitutes a specific event with winning interpretable as the outcome of a singular project, arms races constitute spiralling systems of on-going and potentially open-ended behavior. The existing scholarly literature is divided as to whether arms races correlate with war. International-relations scholars explain arms races in terms of the security dilemma, engineering spiral models, states with Revisionist state, revisionist aims, and Deterrence theory, deterrence models. Examples Pre-First World War naval arms race From 1897 to 1914, a Anglo-German naval arms race, naval arms race between the United Kingdom and German Empire, Germany took place. Br ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
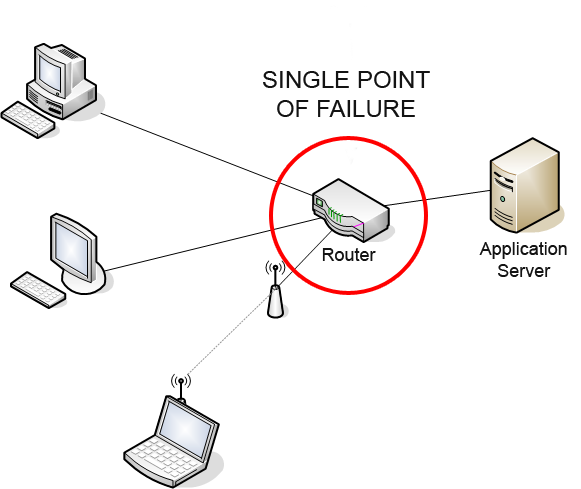
Single Point Of Failure
A single point of failure (SPOF) is a part of a system that would Cascading failure, stop the entire system from working if it were to fail. The term single point of failure implies that there is not a backup or redundant option that would enable the system to continue to function without it. SPOFs are undesirable in any system with a goal of high availability or Reliability engineering, reliability, be it a business practice, software application, or other industrial system. If there is a SPOF present in a system, it produces a potential interruption to the system that is substantially more disruptive than an error would elsewhere in the system. Overview Systems can be made robust by adding Redundancy (engineering), redundancy in all potential SPOFs. Redundancy can be achieved at various levels. The assessment of a potential SPOF involves identifying the critical components of a complex system that would provoke a total systems failure in case of wikt:malfunction, malfunction. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Terrestrial Trunked Radio
Tetra is the common name of many small freshwater characiform fishes. Tetras come from Africa, Central America, and South America, belonging to the biological families Characidae, Alestidae (the "African tetras"), Lepidarchidae, Lebiasinidae, Acestrorhynchidae, Stevardiidae, and Acestrorhamphidae. In the past, all of these families were placed in the Characidae. The Characidae and their allies are distinguished from other fish by the presence of a small adipose fin between the dorsal and caudal fins. Many of these, such as the neon tetra (''Paracheirodon innesi''), are brightly colored and easy to keep in captivity. Consequently, they are extremely popular for home aquaria. ''Tetra'' is no longer a taxonomic, phylogenetic term. It is short for '' Tetragonopterus'', a genus name formerly applied to many of these fish, which is Greek for "square-finned" (literally, four-sided-wing). Because of the popularity of tetras in the fishkeeping hobby A hobby is ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
GPRS
General Packet Radio Service (GPRS), also called 2.5G, is a mobile data standard on the 2G cellular communication network's Global System for Mobile Communications, global system for mobile communications (GSM). Networks and mobile devices with GPRS started to roll out around the year 2001; it offered, for the first time on GSM networks, seamless data transmission using Packet switching, packet data for an "always-on" connection (eliminating the need to "dial-up"), so providing improved Internet access for World Wide Web, web, email, Wireless Application Protocol, WAP services, Multimedia Messaging Service (MMS) and others. Up until the rollout of GPRS, only circuit switched data was used in cellular networks, meaning that one or more radio channels were occupied for the entire duration of a data connection. On the other hand, on GPRS networks, data is broken into small packets and transmitted through available channels. This increased efficiency also gives it theoretical data ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |