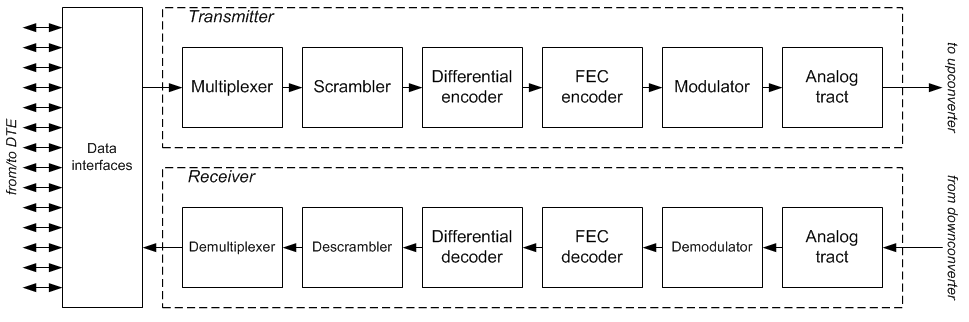
|
Satellite Modem
A satellite modem or satmodem is a modem used to establish data transfers using a communications satellite as a relay. A satellite modem's main function is to transform an input bitstream to a radio signal and vice versa. There are some devices that include only a demodulator (and no modulator, thus only allowing data to be downloaded by satellite) that are also referred to as "satellite modems." These devices are used in satellite Internet access (in this case uploaded data is transferred through a conventional PSTN modem or an ADSL modem). Satellite link A satellite modem is not the only device needed to establish a communication channel. Other equipment that is essential for creating a satellite link include satellite antennas and frequency converters. Data to be transmitted are transferred to a modem from data terminal equipment (e.g. a computer). The modem usually has intermediate frequency (IF) output (that is, 50-200 MHz), however, sometimes the signal is modulated ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Modem
The Democratic Movement (, ; MoDem ) is a centre to centre-right political party in France, whose main ideological trends are liberalism and Christian democracy, and that is characterised by a strong pro-Europeanist stance. MoDem was established by François Bayrou to succeed the Union for French Democracy (UDF) and contest the 2007 legislative election, after his strong showing in the 2007 presidential election. Initially named the Democratic Party (''Parti démocrate''), the party was renamed "Democratic Movement", because there was already a small Democratic Party in France. MoDem secured an agreement with La République En Marche! (LRM) — later Renaissance (RE) — in the 2017 legislative election after Bayrou had endorsed the candidacy of Emmanuel Macron in February. The two parties have since been in alliance, as of late named Ensemble. The party's founder and leader Bayrou has served as Prime Minister of France since December 2024. History Background MoDem tr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Error Correction
In information theory and coding theory with applications in computer science and telecommunications, error detection and correction (EDAC) or error control are techniques that enable reliable delivery of digital data over unreliable communication channels. Many communication channels are subject to channel noise, and thus errors may be introduced during transmission from the source to a receiver. Error detection techniques allow detecting such errors, while error correction enables reconstruction of the original data in many cases. Definitions ''Error detection'' is the detection of errors caused by noise or other impairments during transmission from the transmitter to the receiver. ''Error correction'' is the detection of errors and reconstruction of the original, error-free data. History In classical antiquity, copyists of the Hebrew Bible were paid for their work according to the number of stichs (lines of verse). As the prose books of the Bible were hardly ever w ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Reed–Solomon Error Correction
In information theory and coding theory, Reed–Solomon codes are a group of error-correcting codes that were introduced by Irving S. Reed and Gustave Solomon in 1960. They have many applications, including consumer technologies such as MiniDiscs, CDs, DVDs, Blu-ray discs, QR codes, Data Matrix, data transmission technologies such as DSL and WiMAX, Broadcasting, broadcast systems such as satellite communications, Digital Video Broadcasting, DVB and ATSC Standards, ATSC, and storage systems such as RAID 6. Reed–Solomon codes operate on a block of data treated as a set of finite field, finite-field elements called symbols. Reed–Solomon codes are able to detect and correct multiple symbol errors. By adding check symbols to the data, a Reed–Solomon code can detect (but not correct) any combination of up to erroneous symbols, ''or'' locate and correct up to erroneous symbols at unknown locations. As an erasure code, it can correct up to erasures at locations that are known and ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Sequential Decoder
Recognised by John Wozencraft, sequential decoding is a limited memory technique for decoding tree codes. Sequential decoding is mainly used as an approximate decoding algorithm for long constraint-length convolutional codes. This approach may not be as accurate as the Viterbi algorithm but can save a substantial amount of computer memory. It was used to decode a convolutional code in 1968 Pioneer 9 mission. Sequential decoding explores the tree code in such a way to try to minimise the computational cost and memory requirements to store the tree. There is a range of sequential decoding approaches based on the choice of metric and algorithm. Metrics include: *Fano metric *Zigangirov metric *Gallager metric Algorithms include: *Stack algorithm *Fano algorithm *Creeper algorithm Fano metric Given a partially explored tree (represented by a set of nodes which are limit of exploration), we would like to know the best node from which to explore further. The Fano metric (named aft ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Fano Algorithm
Fano () is a city and ''comune'' of the province of Pesaro and Urbino in the Marche region of Italy. It is a beach resort southeast of Pesaro, located where the ''Via Flaminia'' reaches the Adriatic Sea. It is the third city in the region by population after Ancona and Pesaro. History An ancient town of Marche, it was known as Fanum Fortunae after a temple of Fortuna located there. Its first mention in history dates from 49 BC, when Julius Caesar held it, along with Pisaurum and Ancona. Caesar Augustus established a '' colonia'', and built a wall, some parts of which remain. In 2 AD Augustus also built an arch (which is still standing) at the entrance to the town. In January 271, the Roman Army defeated the Alamanni in the Battle of Fano that took place on the banks of the Metauro river just inland of Fano. Fano was destroyed by Vitiges' Ostrogoths in AD 538. It was rebuilt by the Byzantines, becoming the capital of the maritime Pentapolis ("Five Cities") that ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Viterbi Decoder
A Viterbi decoder uses the Viterbi algorithm for decoding a bitstream that has been encoded using a convolutional code or trellis code. There are other algorithms for decoding a convolutionally encoded stream (for example, the Fano algorithm). The Viterbi algorithm is the most resource-consuming, but it does the maximum likelihood decoding. It is most often used for decoding convolutional codes with constraint lengths k≤3, but values up to k=15 are used in practice. Viterbi decoding was developed by Andrew J. Viterbi and published in the paper There are both hardware (in modems) and software implementations of a Viterbi decoder. Viterbi decoding is used in the iterative Viterbi decoding algorithm. Hardware implementation A hardware Viterbi decoder for basic (not punctured) code usually consists of the following major blocks: *Branch metric unit (BMU) *Path metric unit (PMU) *Traceback unit (TBU) Branch metric unit (BMU) A branch metric unit's function is to cal ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Viterbi Algorithm
The Viterbi algorithm is a dynamic programming algorithm for obtaining the maximum a posteriori probability estimate of the most likely sequence of hidden states—called the Viterbi path—that results in a sequence of observed events. This is done especially in the context of Markov information sources and hidden Markov models (HMM). The algorithm has found universal application in decoding the convolutional codes used in both CDMA and GSM digital cellular, dial-up modems, satellite, deep-space communications, and 802.11 wireless LANs. It is now also commonly used in speech recognition, speech synthesis, diarization, keyword spotting, computational linguistics, and bioinformatics. For example, in speech-to-text (speech recognition), the acoustic signal is treated as the observed sequence of events, and a string of text is considered to be the "hidden cause" of the acoustic signal. The Viterbi algorithm finds the most likely string of text given the acoustic signal. His ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Constraint Length
Constraint may refer to: * Constraint (computer-aided design), a demarcation of geometrical characteristics between two or more entities or solid modeling bodies * Constraint (mathematics), a condition of an optimization problem that the solution must satisfy * Constraint (mechanics), a relation between coordinates and momenta * Constraint (computational chemistry) * Constraint (information theory), the degree of statistical dependence between or among variables * ''Constraints'' (journal), a scientific journal * Constraint (database), a concept in relational database Particular types of constraint * Biological constraints, factors which make populations resistant to evolutionary change * Carrier's constraint on lung function in long thin animals * Finite domain constraint, in mathematical solution-finding * Integrity constraints in databases ** Check constraint ** Foreign key constraint * Specific types of mechanical constraints: ** First-class constraint and second-class ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Convolutional Code
In telecommunication, a convolutional code is a type of error-correcting code that generates parity symbols via the sliding application of a boolean polynomial function to a data stream. The sliding application represents the 'convolution' of the encoder over the data, which gives rise to the term 'convolutional coding'. The sliding nature of the convolutional codes facilitates trellis decoding using a time-invariant trellis. Time invariant trellis decoding allows convolutional codes to be maximum-likelihood soft-decision decoded with reasonable complexity. The ability to perform economical maximum likelihood soft decision decoding is one of the major benefits of convolutional codes. This is in contrast to classic block codes, which are generally represented by a time-variant trellis and therefore are typically hard-decision decoded. Convolutional codes are often characterized by the base code rate and the depth (or memory) of the encoder ,k,K/math>. The base code rate is ty ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Quadrature Amplitude Modulation
Quadrature amplitude modulation (QAM) is the name of a family of digital modulation methods and a related family of analog modulation methods widely used in modern telecommunications to transmit information. It conveys two analog message signals, or two digital bit streams, by changing (''modulating'') the amplitudes of two carrier waves, using the amplitude-shift keying (ASK) digital modulation scheme or amplitude modulation (AM) analog modulation scheme. The two carrier waves are of the same frequency and are out of phase with each other by 90°, a condition known as orthogonality or Quadrature phase, quadrature. The transmitted signal is created by adding the two carrier waves together. At the receiver, the two waves can be coherently separated (demodulated) because of their orthogonality. Another key property is that the modulations are low-frequency/low-bandwidth waveforms compared to the carrier frequency, which is known as the In-phase and quadrature components#Narrowband ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
8PSK
Phase-shift keying (PSK) is a digital modulation process which conveys data by changing (modulating) the phase of a constant frequency carrier wave. The modulation is accomplished by varying the sine and cosine inputs at a precise time. It is widely used for wireless LANs, RFID and Bluetooth communication. Any digital modulation scheme uses a finite number of distinct signals to represent digital data. PSK uses a finite number of phases, each assigned a unique pattern of binary digits. Usually, each phase encodes an equal number of bits. Each pattern of bits forms the symbol that is represented by the particular phase. The demodulator, which is designed specifically for the symbol-set used by the modulator, determines the phase of the received signal and maps it back to the symbol it represents, thus recovering the original data. This requires the receiver to be able to compare the phase of the received signal to a reference signal such a system is termed coherent (and referred ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |