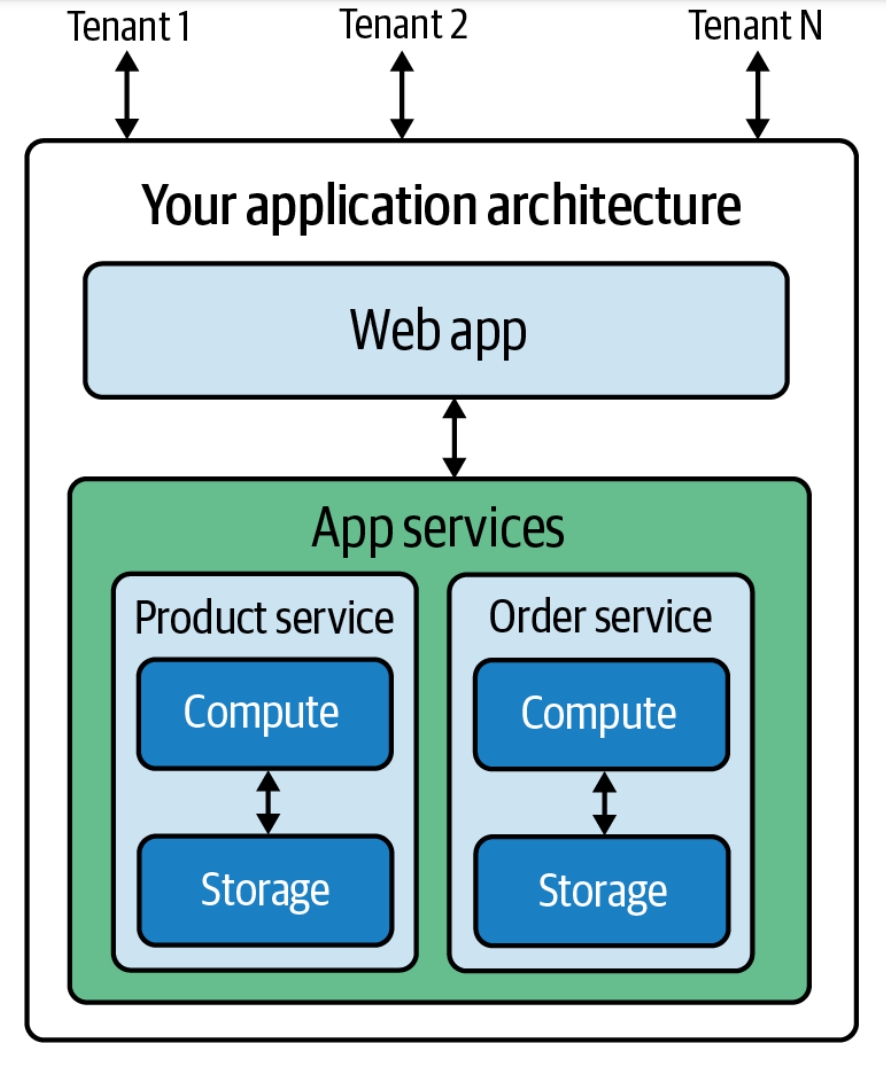
|
Remote Monitoring And Management
Remote monitoring and management (RMM) is the process of supervising and controlling IT systems (such as network devices, desktops, servers and mobile devices) by means of locally installed agents that can be accessed by a management service provider. Functions include the ability to: * install new or updated software remotely (including patches, updates and configuration changes) * detect new devices and automatically install the RMM agent and configure the device * observe the behavior of the managed device and software for performance and diagnostic tasks * perform alerting and provide reports and dashboards Traditionally this function has been done on site at a company but many MSPs are performing this function remotely using integrated Software as a Service (SaaS) platforms. See also * Network management * Network monitoring * Application service management * Application performance management * Managed services * Information technology outsourcing Outsourcing is a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Software Agents
In computer science, a software agent is a computer program that acts for a user or another program in a relationship of agency. The term ''agent'' is derived from the Latin ''agere'' (to do): an agreement to act on one's behalf. Such "action on behalf of" implies the authority to decide which, if any, action is appropriate. Some agents are colloquially known as ''bots'', from ''robot''. They may be embodied, as when execution is paired with a robot body, or as software such as a chatbot executing on a computer, such as a mobile device, e.g. Siri. Software agents may be autonomous or work together with other agents or people. Software agents interacting with people (e.g. chatbots, human-robot interaction environments) may possess human-like qualities such as natural language understanding and speech, personality or embody humanoid form (see Asimo). Related and derived concepts include ''intelligent agents'' (in particular exhibiting some aspects of artificial intelligence, such ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Software As A Service
Software as a service (SaaS ) is a cloud computing service model where the provider offers use of application software to a client and manages all needed physical and software resources. SaaS is usually accessed via a web application. Unlike other software delivery models, it separates "the possession and ownership of software from its use". SaaS use began around 2000, and by 2023 was the main form of software application deployment. Unlike most self-hosted software products, only one version of the software exists and only one operating system and configuration is supported. SaaS products typically run on rented infrastructure as a service (IaaS) or platform as a service (PaaS) systems including hardware and sometimes operating systems and middleware, to accommodate rapid increases in usage while providing instant and continuous availability to customers. SaaS customers have the abstraction of limitless computing resources, while economy of scale drives down the cost. Sa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Network Management
Network management is the process of administering and managing computer networks. Services provided by this discipline include fault analysis, performance management, provisioning of networks and maintaining quality of service. Network management software is used by network administrators to help perform these functions. Technologies A small number of accessory methods exist to support network and network device management. Network management allows IT professionals to monitor network components within large network area. Access methods include the SNMP, command-line interface (CLI), custom XML, CMIP, Windows Management Instrumentation (WMI), Transaction Language 1 (TL1), CORBA, NETCONF, RESTCONF and the Java Management Extensions (JMX). Schemas include the Structure of Management Information (SMI), YANG, WBEM, the Common Information Model ( CIM Schema), and MTOSI amongst others. Value Effective network management can provide positive strategic impacts. For ex ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Network Monitoring
Network monitoring is the use of a system that constantly monitors a computer network for slow or failing components and that notifies the network administrator (via email, SMS or other alarms) in case of outages or other trouble. Network monitoring is part of network management. Details While an intrusion detection system monitors a network threats from the outside, a network monitoring system monitors the network for problems caused by overloaded or crashed servers, network connections or other devices. For example, to determine the status of a web server, monitoring software may periodically send an HTTP request to fetch a page. For email servers, a test message might be sent through SMTP and retrieved by IMAP or POP3. Commonly measured metrics are response time, availability and uptime, although both consistency and reliability metrics are starting to gain popularity. The widespread addition of WAN optimization devices is having an adverse effect on most network monitorin ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Application Service Management
Application service management (ASM) is an emerging discipline within systems management that focuses on monitoring and managing the performance and quality of service of business transactions. ASM can be defined as a well-defined process and use of related tools to detect, diagnose, remedy, and report the service quality of complex business transactions to ensure that they meet or exceed end-users Performance measurements relate to how fast transactions are completed or information is delivered to the end-user by the aggregate of applications, operating systems, hypervisors (if applicable), hardware platforms, and network interconnects. The critical components of ASM include application discovery & mapping, application "health" measurement & management, transaction-level visibility, and incident-related triage. Thus, the ASM tools and processes are commonly used by such roles as Sysop, DevOps, and AIOps. ASM is related to application performance management (APM) but serves as a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Application Performance Management
In the fields of information technology and systems management, application performance management (APM) is the monitoring and management of the performance and availability of software applications. APM strives to detect and diagnose complex application performance problems to maintain an expected level of service. APM is "the translation of IT metrics into business meaning ( .e.value)." Measuring application performance Two sets of performance metrics are closely monitored. The first set of performance metrics defines the performance experienced by end-users of the application. One example of performance is average response times under peak load. The components of the set include load and response times: :* The load is the volume of transactions processed by the application, e.g., transactions per second, requests per second, pages per second. Without being loaded by computer-based demands (e.g. searches, calculations, transmissions), most applications are fast enough, whic ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Managed Services
Managed services is the practice of outsourcing the responsibility for maintaining, and anticipating need for, a range of processes and functions, ostensibly for the purpose of improved operations and reduced budgetary expenditures through the reduction of directly-employed staff. It is an alternative to the break/fix or on-demand outsourcing model where the service provider performs on-demand services and bills the customer only for the work done. The external organization is referred to as a managed service(s) provider (MSP). Definitions A managed IT services provider is a third-party service provider that proactively monitors & manages a customer's server/network/system infrastructure, cybersecurity and end-user systems against a clearly defined Service Level Agreement (SLA). Small and medium-sized businesses (SMBs), nonprofits and government agencies hire MSPs to perform a defined set of day-to-day management services so they can focus on improving their services witho ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Information Technology Outsourcing
Outsourcing is a business practice in which companies use external providers to carry out business processes that would otherwise be handled internally. Outsourcing sometimes involves transferring employees and assets from one firm to another. The term ''outsourcing'', which came from the phrase ''outside resourcing'', originated no later than 1981 at a time when industrial jobs in the United States were being moved overseas, contributing to the economic and cultural collapse of small, industrial towns. In some contexts, the term smartsourcing is also used. The concept, which ''The Economist'' says has "made its presence felt since the time of the Second World War", often involves the contracting out of a business process (e.g., payroll processing, claims processing), operational, and/or non-core functions, such as manufacturing, facility management, call center/call center support. The practice of handing over control of public services to private enterprises (privatization ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |