|
Redacted
Redaction or sanitization is the process of removing sensitive information from a document so that it may be distributed to a broader audience. It is intended to allow the selective disclosure of information. Typically, the result is a document that is suitable for publication or for dissemination to others rather than the intended audience of the original document. When the intent is secrecy protection, such as in dealing with classified information, redaction attempts to reduce the document's classification level, possibly yielding an unclassified document. When the intent is privacy protection, it is often called data anonymization. Originally, the term ''sanitization'' was applied to printed documents; it has since been extended to apply to computer files and the problem of data remanence. Government secrecy In the context of government documents, redaction (also called sanitization) generally refers more specifically to the process of removing sensitive or classified inform ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Privacy
Privacy (, ) is the ability of an individual or group to seclude themselves or information about themselves, and thereby express themselves selectively. The domain of privacy partially overlaps with security, which can include the concepts of appropriate use and Information security, protection of information. Privacy may also take the form of bodily integrity. Throughout history, there have been various conceptions of privacy. Most cultures acknowledge the right of individuals to keep aspects of their personal lives out of the public domain. The right to be free from unauthorized invasions of privacy by governments, corporations, or individuals is enshrined in the privacy laws of many countries and, in some instances, their constitutions. With the rise of technology, the debate regarding privacy has expanded from a bodily sense to include a digital sense. In most countries, the right to digital privacy is considered an extension of the original right to privacy, and many count ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
National Security Agency
The National Security Agency (NSA) is an intelligence agency of the United States Department of Defense, under the authority of the director of national intelligence (DNI). The NSA is responsible for global monitoring, collection, and processing of information and data for global intelligence and counterintelligence purposes, specializing in a discipline known as signals intelligence (SIGINT). The NSA is also tasked with the protection of U.S. communications networks and information systems. The NSA relies on a variety of measures to accomplish its mission, the majority of which are clandestine. The NSA has roughly 32,000 employees. Originating as a unit to decipher coded communications in World War II, it was officially formed as the NSA by President Harry S. Truman in 1952. Between then and the end of the Cold War, it became the largest of the U.S. intelligence organizations in terms of personnel and budget. Still, information available as of 2013 indicates that the C ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Classified Information
Classified information is confidential material that a government deems to be sensitive information which must be protected from unauthorized disclosure that requires special handling and dissemination controls. Access is restricted by law or regulation to particular groups of individuals with the necessary security clearance with a need to know. A formal security clearance is required to view or handle classified material. The clearance process requires a satisfactory background investigation. Documents and other information must be properly marked "by the author" with one of several (hierarchical) levels of sensitivity—e.g. Confidential (C), Secret (S), and Top Secret (S). All classified documents require designation markings on the technical file which is usually located either on the cover sheet, header and footer of page. The choice of level is based on an impact assessment; governments have their own criteria, including how to determine the classification of an inf ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Information Sensitivity
Information sensitivity is the control of access to information or knowledge that might result in loss of an advantage or level of security if disclosed to others. Loss, misuse, modification, or Access control, unauthorized access to sensitive information can adversely affect the privacy or welfare of an individual, trade secrets of a business or even the national security, security and international relations of a nation depending on the level of sensitivity and nature of the information. Non-sensitive information Public information This refers to information that is already a matter of public record or knowledge. With regard to government and private organizations, access to or release of such information may be requested by any member of the public, and there are often formal processes laid out for how to do so. The accessibility of government-held public records is an important part of government transparency, accountability to its citizens, and the values of democracy. Publ ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Feature (software Design)
A feature is "a prominent or distinctive user-visible aspect, quality, or characteristic of a software system or systems", as defined by Kang et al. At the implementation level, "it is a structure that extends and modifies the structure of a given software in order to satisfy a stakeholder’s requirement, to implement and encapsulate a design decision, and to offer a configuration option", as defined by Apel et al. Context The term feature means the same for software as it does for any kind of system. For example, the British Royal Navy's HMS Dreadnought (1906) was considered an important milestone in naval technology because of its advanced features that did not exist in pre-dreadnought battleships. Feature also applies to computer hardware. In the early history of computers, devices such as Digital Equipment Corporation's PDP-7 minicomputer (created in 1964) was noted for having a wealth of features, such as being the first version of the PDP minicomputer series to use ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Computer Storage
Computer data storage or digital data storage is a technology consisting of computer components and Data storage, recording media that are used to retain digital data. It is a core function and fundamental component of computers. The central processing unit (CPU) of a computer is what manipulates data by performing computations. In practice, almost all computers use a storage hierarchy, which puts fast but expensive and small storage options close to the CPU and slower but less expensive and larger options further away. Generally, the fast technologies are referred to as "memory", while slower persistent technologies are referred to as "storage". Even the first computer designs, Charles Babbage's Analytical Engine and Percy Ludgate's Analytical Machine, clearly distinguished between processing and memory (Babbage stored numbers as rotations of gears, while Ludgate stored numbers as displacements of rods in shuttles). This distinction was extended in the Von Neumann archite ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Disk Storage
Disc or disk may refer to: * Disk (mathematics) In geometry, a disk (Spelling of disc, also spelled disc) is the region in a plane (geometry), plane bounded by a circle. A disk is said to be ''closed'' if it contains the circle that constitutes its boundary, and ''open'' if it does not. Fo ..., a two dimensional shape, the interior of a circle * Disk storage * Optical disc * Floppy disk Music * Disc (band), an American experimental music band * ''Disk'' (album), a 1995 EP by Moby Other uses * Disc harrow, a farm implement * Discus throw or disc throw, a track and field event involving a heavy disc * Intervertebral disc, a cartilage between vertebrae * Disk (functional analysis), a subset of a vector space * ''Disc'' (magazine), a British music magazine * Disk, a part of a flower * Disc number, numbers assigned to Inuit by the Government of Canada * Galactic disc, a disc-shaped group of stars Abbreviations * Death-inducing signaling complex * DISC assessmen ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Random Access Memory
Random-access memory (RAM; ) is a form of electronic computer memory that can be read and changed in any order, typically used to store working data and machine code. A random-access memory device allows data items to be read or written in almost the same amount of time irrespective of the physical location of data inside the memory, in contrast with other direct-access data storage media (such as hard disks and magnetic tape), where the time required to read and write data items varies significantly depending on their physical locations on the recording medium, due to mechanical limitations such as media rotation speeds and arm movement. In today's technology, random-access memory takes the form of integrated circuit (IC) chips with MOS (metal–oxide–semiconductor) memory cells. RAM is normally associated with volatile types of memory where stored information is lost if power is removed. The two main types of volatile random-access semiconductor memory are static ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
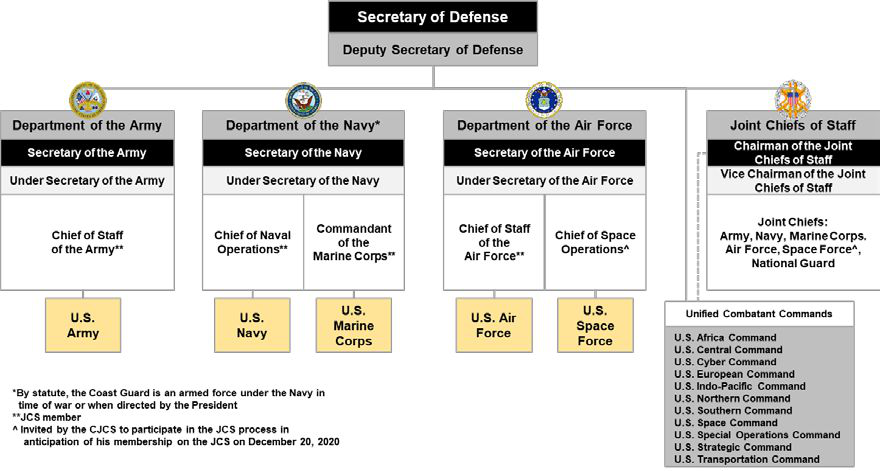
United States Department Of Defense
The United States Department of Defense (DoD, USDOD, or DOD) is an United States federal executive departments, executive department of the federal government of the United States, U.S. federal government charged with coordinating and supervising the six U.S. armed services: the United States Army, Army, United States Navy, Navy, United States Marine Corps, Marines, United States Air Force, Air Force, United States Space Force, Space Force, the United States Coast Guard, Coast Guard for some purposes, and related functions and agencies. As of November 2022, the department has over 1.4 million active-duty uniformed personnel in the six armed services. It also supervises over 778,000 National Guard (United States), National Guard and reservist personnel, and over 747,000 civilians, bringing the total to over 2.91 million employees. Headquartered at the Pentagon in Arlington County, Virginia, just outside Washington, D.C., the Department of Defense's stated mission is "to provid ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Backup
In information technology, a backup, or data backup is a copy of computer data taken and stored elsewhere so that it may be used to restore the original after a data loss event. The verb form, referring to the process of doing so, is "wikt:back up, back up", whereas the noun and adjective form is "wikt:backup, backup". Backups can be used to data recovery, recover data after its loss from File deletion, data deletion or Data corruption, corruption, or to recover data from an earlier time. Backups provide a simple form of IT disaster recovery; however not all backup systems are able to reconstitute a computer system or other complex configuration such as a computer cluster, active directory server, or database server. A backup system contains at least one copy of all data considered worth saving. The computer data storage, data storage requirements can be large. An information repository model may be used to provide structure to this storage. There are different types of data stor ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Undo
Undo is an interaction technique which is implemented in many computer programs. It erases the last change done to the document, reverting it to an older state. In some more advanced programs, such as graphic processing, undo will negate the last command done to the file being edited. With the possibility of undo, users can explore and work without fear of making mistakes, because they can easily be undone. The expectations for undo are easy to understand: to have a predictable functionality, and to include all "undoable" commands. Usually undo is available until the user undoes all executed operations. But there are some actions which are not stored in the undo list, and thus they cannot be undone. For example, ''save file'' is not undoable, but is queued in the list to show that it was executed. Another action which is usually not stored, and thus not undoable, is ''scrolling'' or ''selection''. The opposite of to undo is to redo. The redo command reverses the undo or advances ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Espionage
Espionage, spying, or intelligence gathering, as a subfield of the intelligence field, is the act of obtaining secret or confidential information ( intelligence). A person who commits espionage on a mission-specific contract is called an ''espionage agent'' or ''spy''. A person who commits espionage as a fully employed officer of a government is called an intelligence officer. Any individual or spy ring (a cooperating group of spies), in the service of a government, company, criminal organization, or independent operation, can commit espionage. The practice is clandestine, as it is by definition unwelcome. In some circumstances, it may be a legal tool of law enforcement and in others, it may be illegal and punishable by law. Espionage is often part of an institutional effort by a government or commercial concern. However, the term tends to be associated with state spying on potential or actual enemies for military purposes. Spying involving corporations is known as c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |