|
News.admin.net-abuse.email
news.admin.net-abuse.email (sometimes abbreviated nanae or n.a.n-a.e, and often incorrectly spelled with a hyphen in "email") is a Usenet newsgroup devoted to discussion of the abuse of email systems, specifically through E-mail spam, email spam and similar attacks. According to a timeline compiled by Keith Lynch, news.admin.net-abuse.email was the first widely available electronic forum for discussing spam. Steve Linford, the founder of The Spamhaus Project, sometimes posts in the newsgroup. Topics covered In its original charter the following examples of "on-topic" areas were listed: *Chain letters *DoS attacks *Email address list *Email bomb *Email viruses *Filtering software *Large-scale mailings *Listserv bombs *Mailing list abuse *Pyramid schemes *Spamming, Unsolicited email Eventually, by mutual consent, it was also determined that the following were also "on-topic": *Cats (on a superficial/anecdotal level) History The group was officially proposed (i.e. its request for ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
The Spamhaus Project
The Spamhaus Project is an international organisation based in the Principality of Andorra, founded in 1998 by Steve Linford to track email spammers and spam-related activity. The name ''spamhaus'', a pseudo-German expression, was coined by Linford to refer to an internet service provider, or other firm, which spams or knowingly provides service to spammers. Anti-spam lists The Spamhaus Project is responsible for compiling several widely used anti-spam lists. Many internet service providers and email servers use the lists to reduce the amount of spam that reaches their users. In 2006, the Spamhaus services protected 650 million email users, including the European Parliament, US Army, the White House and Microsoft, from billions of spam emails a day. Spamhaus distributes the lists in the form of DNS-based blocklists (DNSBLs). The lists are offered as a free public service to low-volume mail server operators on the internet. Commercial spam filtering services and other sites p ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
E-mail Spam
Email spam, also referred to as junk email, spam mail, or simply spam, refers to unsolicited messages sent in bulk via email. The term originates from a Monty Python sketch, where the name of a canned meat product, "Spam," is used repetitively, mirroring the intrusive nature of unwanted emails. Since the early 1990s, spam has grown significantly, with estimates suggesting that by 2014, it comprised around 90% of all global email traffic. Spam is primarily a financial burden for the recipient, who may be required to manage, filter, or delete these unwanted messages. Since the expense of spam is mostly borne by the recipient, it is effectively a form of " postage due" advertising, where the recipient bears the cost of unsolicited messages. This cost imposed on recipients, without compensation from the sender, makes spam an example of a " negative externality" (a side effect of an activity that affects others who are not involved in the decision). The legal definition and status of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Spamming
Spamming is the use of messaging systems to send multiple unsolicited messages (spam) to large numbers of recipients for the purpose of commercial advertising, non-commercial proselytizing, or any prohibited purpose (especially phishing), or simply repeatedly sending the same message to the same user. While the most widely recognized form of spam is email spam, the term is applied to similar abuses in other media: instant messaging spam, Usenet newsgroup spam, Web search engine spam, spam in blogs, wiki spam, online classified ads spam, mobile phone messaging spam, Internet forum spam, junk fax transmissions, social spam, spam mobile apps, television advertising and file sharing spam. It is named after Spam, a luncheon meat, by way of a Monty Python sketch about a restaurant that has Spam in almost every dish in which Vikings annoyingly sing "Spam" repeatedly. Spamming remains economically viable because advertisers have no operating costs beyond the management of th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Usenet
Usenet (), a portmanteau of User's Network, is a worldwide distributed discussion system available on computers. It was developed from the general-purpose UUCP, Unix-to-Unix Copy (UUCP) dial-up network architecture. Tom Truscott and Jim Ellis (computing), Jim Ellis conceived the idea in 1979, and it was established in 1980.''From Usenet to CoWebs: interacting with social information spaces'', Christopher Lueg, Danyel Fisher, Springer (2003), , Users read and post messages (called ''articles'' or ''posts'', and collectively termed ''news'') to one or more topic categories, known as Usenet newsgroup, newsgroups. Usenet resembles a bulletin board system (BBS) in many respects and is the precursor to the Internet forums that have become widely used. Discussions are Threaded discussion, threaded, as with web forums and BBSes, though posts are stored on the server sequentially. [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Lawsuit
A lawsuit is a proceeding by one or more parties (the plaintiff or claimant) against one or more parties (the defendant) in a civil court of law. The archaic term "suit in law" is found in only a small number of laws still in effect today. The term "lawsuit" is used with respect to a civil action brought by a plaintiff (a party who claims to have incurred loss as a result of a defendant's actions) who requests a legal remedy or equitable remedy from a court. The defendant is required to respond to the plaintiff's complaint or else risk default judgment. If the plaintiff is successful, judgment is entered in favor of the plaintiff, and the court may impose the legal or equitable remedies available against the defendant (respondent). A variety of court orders may be issued in connection with or as part of the judgment to enforce a right, award damages or restitution, or impose a temporary or permanent injunction to prevent an act or compel an act. A declaratory judgmen ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Western (genre)
The Western is a genre of fiction typically Setting (narrative), set in the American frontier (commonly referred to as the "Old West" or the "Wild West") between the California Gold Rush of 1849 and the closing of the frontier in 1890, and commonly associated with Americana (culture), folk tales of the Western United States, particularly the Southwestern United States, as well as Northern Mexico and Western Canada. The frontier is depicted in Western media as a sparsely populated hostile region patrolled by cowboys, Outlaw (stock character), outlaws, sheriffs, and numerous other Stock character, stock Gunfighter, gunslinger characters. Western narratives often concern the gradual attempts to tame the crime-ridden American West using wider themes of justice, freedom, rugged individualism, manifest destiny, and the national history and identity of the United States. Native Americans in the United States, Native American populations were often portrayed as averse foes or Savage ( ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Bulletproof Hosting
Bulletproof hosting (BPH) is technical infrastructure service provided by an internet hosting service that is resilient to complaints of illicit activities, which serves criminal actors as a basic building block for streamlining various cyberattacks. BPH providers allow online gambling, illegal pornography, botnet command and control servers, spam, copyrighted materials, hate speech and misinformation, despite takedown court orders and law enforcement subpoenas, allowing such material in their acceptable use policies. BPH providers usually operate in jurisdictions which have lenient laws against such conduct. Most non-BPH service providers prohibit transferring materials over their network that would be in violation of their terms of service and the local laws of the incorporated jurisdiction, and oftentimes any abuse reports would result in takedowns to avoid their autonomous system's IP address block being blacklisted by other providers and by Spamhaus. History B ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cartoon
A cartoon is a type of visual art that is typically drawn, frequently Animation, animated, in an realism (arts), unrealistic or semi-realistic style. The specific meaning has evolved, but the modern usage usually refers to either: an image or series of images intended for satire, caricature, or humor; or a motion picture that relies on a sequence of illustrations for its animation. Someone who creates cartoons in the first sense is called a ''cartoonist'', and in the second sense they are usually called an ''animator''. The concept originated in the Middle Ages, and first described a preparatory drawing for a piece of art, such as a painting, fresco, tapestry, or stained glass window. In the 19th century, beginning in ''Punch (magazine), Punch'' magazine in 1843, cartoon came to refer – ironically at first – to humorous artworks in magazines and newspapers. Then it also was used for political cartoons and comic strips. When the medium developed, in the early 20th century, it ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Attorney At Law
Attorney at law or attorney-at-law, usually abbreviated in everyday speech to attorney, is the preferred term for a practising lawyer in certain jurisdictions, including South Africa (for certain lawyers), Sri Lanka, the Philippines, and the United States. In Canada, it is used only in Quebec as the English term for . The term has its roots in the verb '' to attorn'', meaning to transfer one's rights and obligations to another. England and Wales and Ireland The ''attorney'', in the sense of a lawyer who acts on behalf of a client, has an ancient pedigree in English law. The Statute of Merton 1235 uses the Latin expression in a phrase rendered into English by ''The Statutes of the Realm'' as The term was formerly used in England and Wales and Ireland for lawyers who practised in the common law courts. They were officers of the courts and were under judicial supervision.A. H. Manchester, ''A Modern Legal History of England and Wales, 1750–1850'', Butterworths: London, 1980 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Trailer (vehicle)
A trailer is an unpowered vehicle Towing, towed by a powered vehicle. It is commonly used for the transport of goods and materials. There are two general categories of trailers: the full trailer and the semitrailer. A full trailer is a type of trailer whose entire weight is supported by its own wheels, with no weight transferred to the towing vehicle. In contrast, a semi-trailer is designed so that a portion of its weight is carried by its own wheels, while the remaining weight is borne by the towing vehicle. Sometimes recreational vehicles, travel trailers, or mobile homes with limited living facilities where people can camp or stay have been referred to as trailers. In earlier days, many such vehicles were towable trailers. Trailers have been used for thousands of years, predating the invention of the automobile. Before the advent of the wheel, early humans employed the concept of trailering by using drag sleds to transport goods. While the two wheel war chariot is one of the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
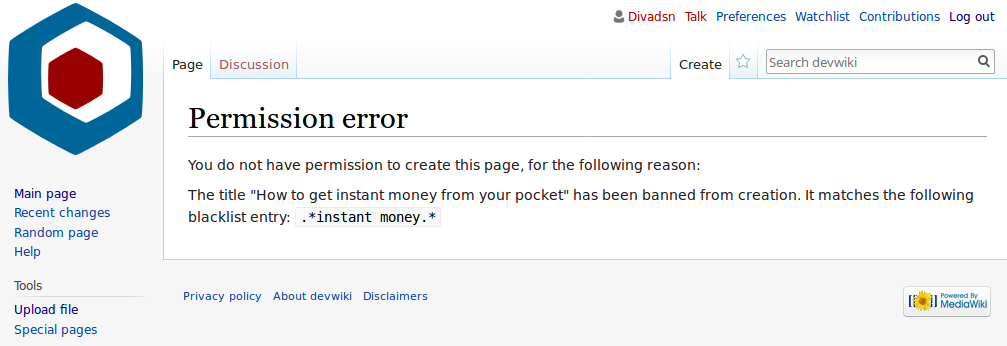
Blacklist (computing)
In computing, a blacklist, disallowlist, blocklist, or denylist is a basic access control mechanism that allows through all elements (email addresses, users, passwords, URLs, IP addresses, domain names, file hashes, etc.), except those explicitly mentioned. Those items on the list are denied access. The opposite is a whitelist, allowlist, or passlist, in which only items on the list are let through whatever gate is being used. A greylist contains items that are temporarily blocked (or temporarily allowed) until an additional step is performed. Blacklists can be applied at various points in a security architecture, such as a host, web proxy, DNS servers, email server, firewall, directory servers or application authentication gateways. The type of element blocked is influenced by the access control location. DNS servers may be well-suited to block domain names, for example, but not URLs. A firewall is well-suited for blocking IP addresses, but less so for blocking maliciou ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
News
News is information about current events. This may be provided through many different Media (communication), media: word of mouth, printing, Mail, postal systems, broadcasting, Telecommunications, electronic communication, or through the testimony of Witness, observers and witnesses to events. News is sometimes called "hard news" to differentiate it from soft media. Subject matters for news reports include war, government, politics, education, health, economy, business, fashion, sport, entertainment, and the Climate change, environment, as well as quirky or unusual events. Government proclamations, concerning Monarchy, royal ceremonies, laws, taxes, public health, and Crime, criminals, have been dubbed news since ancient times. Technology, Technological and Social change, social developments, often driven by government communication and espionage networks, have increased the speed with which news can spread, as well as influenced its content. Throughout history, people have ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |