|
Data Haven
A data haven, like a corporate haven or tax haven, is a refuge for uninterrupted or unregulated data. Data havens are locations with legal environments that are friendly to the concept of a computer network freely holding data and even protecting its content and associated information. They tend to fit into three categories: a physical locality with weak information-system enforcement and extradition laws, a physical locality with intentionally strong protections of data, and virtual domains designed to secure data via technical means (such as encryption) regardless of any legal environment. Tor's onion space, I2P (both hidden services), HavenCo (centralized), and Freenet (decentralized) are four models of modern-day virtual data havens. Purposes of data havens Reasons for establishing data havens include access to free political speech for users in countries where censorship of the Internet is practiced. Other reasons can include: * Whistleblowing * Distributing software, d ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
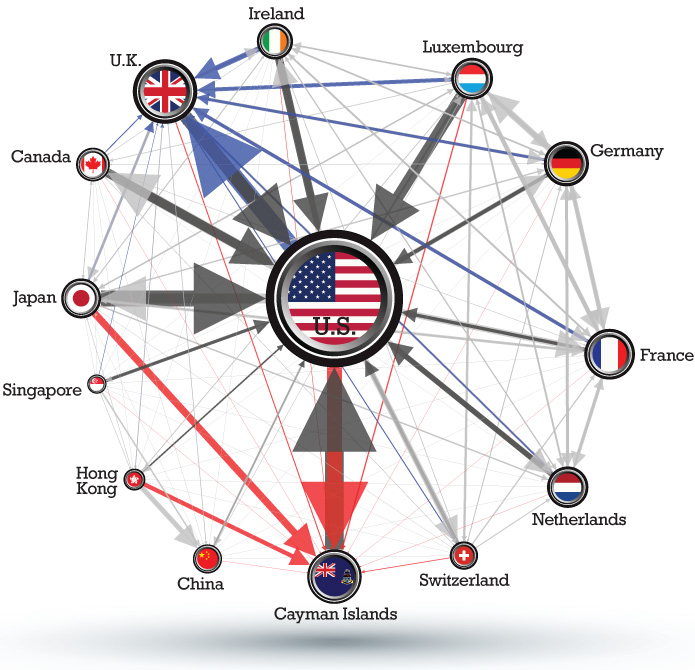
Corporate Haven
Corporate haven, corporate tax haven, or multinational tax haven is used to describe a jurisdiction that multinational corporations find attractive for establishing subsidiaries or Incorporation (business), incorporation of regional or main company headquarters, mostly due to favourable tax regimes (not just the headline tax rate), and/or favourable secrecy laws (such as the avoidance of regulations or disclosure of tax schemes), and/or favourable regulatory regimes (such as weak data-protection or employment laws). Unlike traditional tax havens, modern corporate tax havens reject they have anything to do with near-zero Corporation tax in the Republic of Ireland#Effective tax rate (ETR), effective tax rates, due to their need to encourage jurisdictions to enter into bilateral Tax treaty, tax treaties that accept the haven's base erosion and profit shifting (BEPS) tools. CORPNET show each corporate tax haven is strongly connected with specific traditional tax havens (via additional ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Software
Software consists of computer programs that instruct the Execution (computing), execution of a computer. Software also includes design documents and specifications. The history of software is closely tied to the development of digital computers in the mid-20th century. Early programs were written in the machine language specific to the hardware. The introduction of high-level programming languages in 1958 allowed for more human-readable instructions, making software development easier and more portable across different computer architectures. Software in a programming language is run through a compiler or Interpreter (computing), interpreter to execution (computing), execute on the architecture's hardware. Over time, software has become complex, owing to developments in Computer network, networking, operating systems, and databases. Software can generally be categorized into two main types: # operating systems, which manage hardware resources and provide services for applicat ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Islands In The Net
''Islands in the Net'' is a 1988 science fiction novel by American writer Bruce Sterling. It won the John W. Campbell Memorial Award for Best Science Fiction Novel in 1989, and was nominated for both the Hugo and Locus Awards that same year. It offers a view of an early 21st century world, apparently peaceful, with delocalised, networking corporations. The protagonist, swept up in events beyond her control, finds herself in places that are off the net, from a datahaven in Grenada, to a Singapore under terrorist attack, to the poorest and most disaster-struck parts of Africa. In the story, the fictional book ''The Lawrence Doctrine and Postindustrial Insurgency'', named after Lawrence of Arabia, is banned because it deals directly with methods and tactics of an insurgent rebellion. Plot summary The action takes place in 2023–2025 in Galveston, Texas; Atlanta, Georgia; Grenada, an island on the northeast coast of South America; Singapore; and Africa. Protagonist Laura Webs ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mona Lisa Overdrive
''Mona Lisa Overdrive'' is a science fiction novel by American-Canadian writer William Gibson, published in 1988. It is the final novel of the cyberpunk Sprawl trilogy, following ''Neuromancer'' and ''Count Zero'', taking place eight years after the events of the latter. The novel was nominated for the Nebula Award for Best Novel, the Hugo Award for Best Novel, and the Locus Award for Best Science Fiction Novel in 1989. Plot Taking place eight years after the events of ''Count Zero'' and fifteen years after ''Neuromancer'', the story is formed from several interconnecting plot threads, and also features characters from Gibson's previous works (such as Molly Millions, the razor-fingered mercenary from ''Neuromancer''). Thread one: concerns Mona, a teen prostitute who has a more-than-passing resemblance to famed Simstim superstar Angie Mitchell. Mona is hired by shady individuals for a "gig" which later turns out to be part of a plot to abduct Angie. Thread two: focuses on ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Count Zero
''Count Zero'' is a science fiction novel by American-Canadian writer William Gibson, originally published in 1986. It presents a near future whose technologies include a network of supercomputers that created a "matrix" in "cyberspace", an accessible, virtual, three-dimensionally active "inner space", which, for Gibson—writing these decades earlier—was seen as being dominated by violent competition between small numbers of very rich individuals and multinational corporations. The novel is composed of a trio of plot lines that ultimately converge. ''Count Zero'' is the second volume of the Sprawl trilogy, which began with ''Neuromancer'' and concludes with '' Mona Lisa Overdrive''. It was serialized in the January through March 1986 monthly issues of '' Isaac Asimov's Science Fiction Magazine''; the January cover was devoted to the story, with art by Hisaki Yasuda. According to Gibson, the magazine version was edited with his permission to allow access to youth audiences i ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
William Gibson
William Ford Gibson (born March 17, 1948) is an American-Canadian speculative fiction writer and essayist widely credited with pioneering the science fiction subgenre known as cyberpunk. Beginning his writing career in the late 1970s, his early works were noir, near-future stories that explored the effects of technology, cybernetics, and computer networks on humans, a "combination of Low-life, lowlife and high tech"—and helped to create an iconography for the Information Age before the ubiquity of the Internet in the 1990s. Gibson coined the term "cyberspace" for "widespread, interconnected digital technology" in his short story "Burning Chrome" (1982), and later popularized the concept in his acclaimed debut novel ''Neuromancer'' (1984). These early works of Gibson's have been credited with "renovating" science fiction literature in the 1980s. After expanding on the story in ''Neuromancer'' with two more novels (''Count Zero'' in 1986 and ''Mona Lisa Overdrive'' in 1988), t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
New Scientist
''New Scientist'' is a popular science magazine covering all aspects of science and technology. Based in London, it publishes weekly English-language editions in the United Kingdom, the United States and Australia. An editorially separate organisation publishes a monthly Dutch-language edition. First published on 22 November 1956, ''New Scientist'' has been available in online form since 1996. Sold in retail outlets (paper edition) and on subscription (paper and/or online), the magazine covers news, features, reviews and commentary on science, technology and their implications. ''New Scientist'' also publishes speculative articles, ranging from the technical to the philosophical. ''New Scientist'' was acquired by Daily Mail and General Trust (DMGT) in March 2021. History Ownership The magazine was founded in 1956 by Tom Margerison, Max Raison and Nicholas Harrison as ''The New Scientist'', with Issue 1 on 22 November 1956, priced at one shilling (). An article in the magazi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Privacy
Privacy (, ) is the ability of an individual or group to seclude themselves or information about themselves, and thereby express themselves selectively. The domain of privacy partially overlaps with security, which can include the concepts of appropriate use and Information security, protection of information. Privacy may also take the form of bodily integrity. Throughout history, there have been various conceptions of privacy. Most cultures acknowledge the right of individuals to keep aspects of their personal lives out of the public domain. The right to be free from unauthorized invasions of privacy by governments, corporations, or individuals is enshrined in the privacy laws of many countries and, in some instances, their constitutions. With the rise of technology, the debate regarding privacy has expanded from a bodily sense to include a digital sense. In most countries, the right to digital privacy is considered an extension of the original right to privacy, and many count ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cybercrime
Cybercrime encompasses a wide range of criminal activities that are carried out using digital devices and/or Computer network, networks. It has been variously defined as "a crime committed on a computer network, especially the Internet"; Cybercriminals may exploit vulnerabilities in computer systems and networks to gain unauthorized access, steal sensitive information, disrupt services, and cause financial or reputational harm to individuals, organizations, and governments. In 2000, the tenth United Nations Congress on the Prevention of Crime and the Treatment of Offenders classified cyber crimes into five categories: unauthorized access, damage to computer data or programs, sabotage to hinder the functioning of a computer system or network, unauthorized interception of data within a system or network, and computer espionage. Internationally, both state and non-state actors engage in cybercrimes, including espionage, financial theft, and other cross-border crimes. Cybercrimes c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Pornography
Pornography (colloquially called porn or porno) is Sexual suggestiveness, sexually suggestive material, such as a picture, video, text, or audio, intended for sexual arousal. Made for consumption by adults, pornographic depictions have evolved from cave paintings, some forty millennia ago, to modern-day Virtual reality pornography, virtual reality presentations. A general distinction of adults-only sexual content is made, classifying it as pornography or erotica. The oldest Artifact (archaeology), artifacts considered pornographic were discovered in Germany in 2008 and are dated to be at least 35,000 years old. Human enchantment with sexual imagery representations has been a constant throughout history of erotic depictions, history. However, the reception of such imagery varied according to the historical, cultural, and national contexts. The Indian Sanskrit text ''Kama Sutra'' (3rd century CE) contained prose, poetry, and illustrations regarding sexual behavior, and the book ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Online Gambling
Online gambling (also known as iGaming or iGambling) is any kind of gambling conducted on the internet. This includes virtual poker, casinos, and sports betting. The first online gambling venue opened to the general public was ticketing for the Liechtenstein International Lottery in October 1994. Today, the market is worth around $40 billion globally each year, according to various estimates. Many countries restrict or ban online gambling. However, it is legal in some states of the United States, some provinces in Canada, most countries in the European Union, and several nations in the Caribbean. In many legal markets, online gambling service providers are required by law to have some form of license to provide services or advertise to residents there. Examples of such authorities include the United Kingdom Gambling Commission or the Pennsylvania Gaming Control Board in the US. Many online casinos and gambling companies around the world choose to base themselves in tax ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |