|
Broadcast Encryption
Broadcast encryption is the cryptographic problem of delivering encrypted content (e.g. TV programs or data on DVDs) over a broadcast channel in such a way that only qualified users (e.g. subscribers who have paid their fees or DVD players conforming to a specification) can decrypt the content. The challenge arises from the requirement that the set of qualified users can change in each broadcast emission, and therefore revocation of individual users or user groups should be possible using broadcast transmissions, only, and without affecting any remaining users. As efficient revocation is the primary objective of broadcast encryption, solutions are also referred to as revocation schemes. Rather than directly encrypting the content for qualified users, broadcast encryption schemes distribute keying information that allows qualified users to reconstruct the content encryption key whereas revoked users find insufficient information to recover the key. The typical setting considered i ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
 |
Cryptography
Cryptography, or cryptology (from "hidden, secret"; and ''graphein'', "to write", or ''-logy, -logia'', "study", respectively), is the practice and study of techniques for secure communication in the presence of Adversary (cryptography), adversarial behavior. More generally, cryptography is about constructing and analyzing Communication protocol, protocols that prevent third parties or the public from reading private messages. Modern cryptography exists at the intersection of the disciplines of mathematics, computer science, information security, electrical engineering, digital signal processing, physics, and others. Core concepts related to information security (confidentiality, data confidentiality, data integrity, authentication, and non-repudiation) are also central to cryptography. Practical applications of cryptography include electronic commerce, Smart card#EMV, chip-based payment cards, digital currencies, password, computer passwords, and military communications. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
Content Scramble System
The Content Scramble System (CSS) is a digital rights management (DRM) and encryption system employed on many commercially produced DVD-Video discs. CSS utilizes a proprietary 40-bit stream cipher algorithm. The system was introduced around 1996 and was first compromised in 1999. CSS is one of several complementary systems designed to restrict DVD-Video access. It has been superseded by newer DRM schemes such as Content Protection for Recordable Media (CPRM), or by Advanced Encryption Standard (AES) in the Advanced Access Content System (AACS) DRM scheme used by HD DVD and Blu-ray Disc, which have 56-bit and 128-bit key sizes, respectively, providing a much higher level of security than the less secure 40-bit key size of CSS. Preliminary note The content scramble system (CSS) is a collection of proprietary protection mechanisms for DVD-Video discs. CSS attempts to restrict access to the content only for licensed applications. According to the DVD Copy Control Assoc ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
|
Applications Of Cryptography
Application may refer to: Mathematics and computing * Application software, computer software designed to help the user to perform specific tasks ** Application layer, an abstraction layer that specifies protocols and interface methods used in a communications network * Function application, in mathematics and computer science Processes and documents * Application for employment, a form or forms that an individual seeking employment must fill out * College application, the process by which prospective students apply for entry into a college or university * Patent application A patent application is a request pending at a patent office for the grant of a patent for an invention described in the patent specification and a set of one or more claim (patent), claims stated in a formal document, including necessary officia ..., a document filed at a patent office to support the grant of a patent Other uses * Application (virtue), a characteristic encapsulated in diligence * Topica ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
|
Copy Protection
Copy protection, also known as content protection, copy prevention and copy restriction, is any measure to enforce copyright by preventing the reproduction of software, films, music, and other media. Copy protection is most commonly found on videotapes, DVDs, Blu-ray discs, HD-DVDs, computer software discs, video game discs and cartridges, audio CDs and some VCDs. It also may be incorporated into digitally distributed versions of media and software. Some methods of copy protection have also led to criticism because it caused inconvenience for paying consumers or secretly installed additional or unwanted software to detect copying activities on the consumer's computer. Making copy protection effective while protecting consumer rights remains a problem with media publication. Terminology Media corporations have always used the term copy protection, but critics argue that the term tends to sway the public into identifying with the publishers, who favor restriction technolog ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
|
Threshold Cryptosystem
A threshold cryptosystem, the basis for the field of threshold cryptography, is a cryptosystem that protects information by encrypting it and distributing it among a cluster of fault-tolerant computers. The message is encrypted using a public key, and the corresponding private key is shared among the participating parties. With a threshold cryptosystem, in order to decrypt an encrypted message or to sign a message, several parties (more than some threshold number) must cooperate in the decryption or signature protocol. History Perhaps the first system with complete threshold properties for a trapdoor function (such as RSA) and a proof of security was published in 1994 by Alfredo De Santis, Yvo Desmedt, Yair Frankel, and Moti Yung. Historically, only organizations with very valuable secrets, such as certificate authorities, the military, and governments made use of this technology. One of the earliest implementations was done in the 1990s by Certco for the planned deployment ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
|
Television Encryption
Television encryption, often referred to as scrambling, is encryption used to control access to pay television services, usually cable, satellite, or Internet Protocol television (IPTV) services. History Pay television exists to make revenue from subscribers, and sometimes those subscribers do not pay. The prevention of ''piracy'' on cable and satellite networks has been one of the main factors in the development of Pay TV encryption systems. The early cable-based Pay TV networks used no security. This led to problems with people connecting to the network without paying. Consequently, some methods were developed to frustrate these self-connectors. The early Pay TV systems for cable television were based on a number of simple measures. The most common of these was a channel-based filter that would effectively stop the channel being received by those who had not subscribed. These filters would be added or removed according to the subscription. As the number of television channels ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
|
Multicast Encryption
Multicast encryption is the use of encryption to ensure that only the chosen recipient(s) has access to multicast data. Multicasting Multicast is what enables a node on a network to address one unit of data to a specific group of receivers.Micciancio, Daniele and Saurabh Panjwani“Multicast Encryption: How to maintain secrecy in large, dynamic groups?”/ref> In interactive multicast at the data link or network layer, such as IP multicast, Ethernet multicast or MBMS service over cellular network, receivers may join and leave the group using an interaction channel. Only one copy of the data is sent from the source, and while copies are created and sent to the desired recipients by network infrastructure nodes. In for example IP multicast, a multicast group is identified by a class D IP address. A host enters or exits a group using IGMP (Internet Group Management Protocol). A message sent via multicast is sent to all nodes on the network, but only the intended nodes accept the mul ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
 |
Digital Rights Management
Digital rights management (DRM) is the management of legal access to digital content. Various tools or technological protection measures, such as access control technologies, can restrict the use of proprietary hardware and copyrighted works. DRM technologies govern the use, modification and distribution of copyrighted works (e.g. software, multimedia content) and of systems that enforce these policies within devices. DRM technologies include licensing agreements and encryption. Laws in many countries criminalize the circumvention of DRM, communication about such circumvention, and the creation and distribution of tools used for such circumvention. Such laws are part of the United States' Digital Millennium Copyright Act (DMCA), and the European Union's Information Society Directive – with the French DADVSI an example of a member state of the European Union implementing that directive. Copyright holders argue that DRM technologies are necessary to protect intellectual proper ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
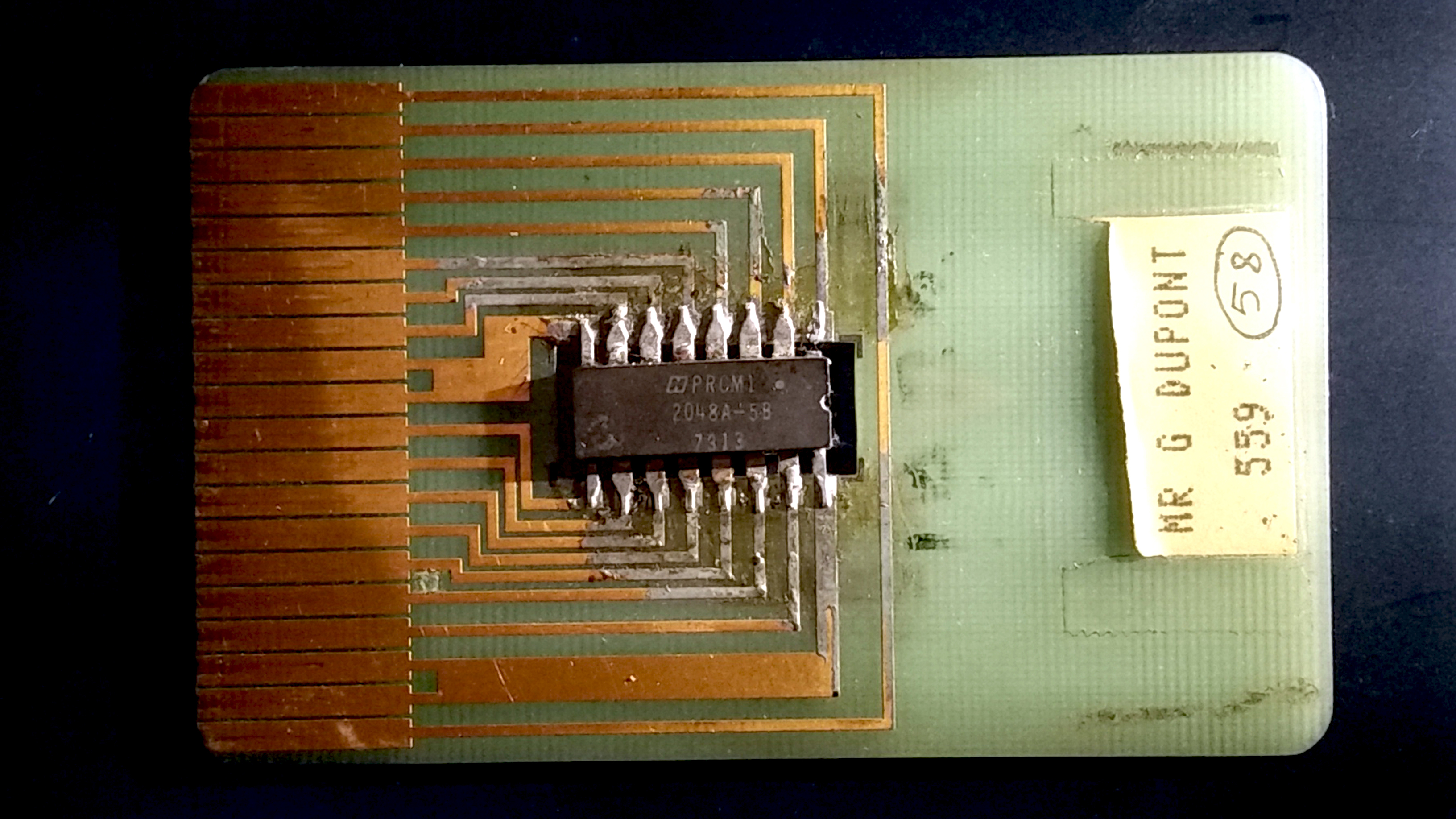 |
Smart Card
A smart card (SC), chip card, or integrated circuit card (ICC or IC card), is a card used to control access to a resource. It is typically a plastic credit card-sized card with an Embedded system, embedded integrated circuit (IC) chip. Many smart cards include a pattern of metal contacts to electrically connect to the internal chip. Others are Contactless smart card, contactless, and some are both. Smart cards can provide personal identification, authentication, data storage, and application processing. Applications include identification, financial, public transit, computer security, schools, and healthcare. Smart cards may provide strong security authentication for single sign-on (SSO) within organizations. Numerous nations have deployed smart cards throughout their populations. The universal integrated circuit card (UICC) for mobile phones, installed as pluggable SIM card or embedded eSIM, is also a type of smart card. , 10.5billion smart card IC chips are manufactured annually ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
 |
Tamper Resistance
Tamperproofing is a methodology used to hinder, deter or detect unauthorised access to a device or circumvention of a security system. Since any device or system can be foiled by a person with sufficient knowledge, equipment, and time, the term "tamperproof" is a misnomer unless some limitations on the tampering party's resources is explicit or assumed. Tamper resistance is resistance to intentional malfunction or sabotage by either the normal users of a product, package, or system or others with physical access to it. Tamper resistance ranges from simple features like screws with special drives and tamper-evident seals to more complex devices that render themselves inoperable or encrypt all data transmissions between individual chips, use of materials needing special tools and knowledge. Tamper-resistant devices or features are common on packages to deter package or product tampering or enable its detection. Anti-tamper devices have one or more components: tamper resistance, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
Set-top Box
A set-top box (STB), also known as a cable converter box, cable box, receiver, or simply box, and historically television decoder or a converter, is an information appliance device that generally contains a Tuner (radio)#Television, TV tuner input and displays output to a television set, turning the source signal into media (communications), content in a form that can then be displayed on the television screen or other display device. It is designed to be placed alongside or "on top" (hence the name) of a television set. Set-top boxes are used in cable television, satellite television, terrestrial television and Internet Protocol television systems, as well as other uses such as digital media players ("streaming boxes"). Alternatives to set-top boxes are the smaller dongles, and television sets with built-in TV tuners. TV signal sources The signal source might be an Ethernet cable, a satellite dish, a coaxial cable (see cable television), a telephone line (including Digital subs ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
|
Pay TV
Pay television, also known as subscription television, premium television or, when referring to an individual service, a premium channel, refers to subscription-based television services, usually provided by multichannel television providers, but also increasingly via digital terrestrial and streaming television. In the United States, subscription television began in the late 1970s and early 1980s in the form of encrypted analog over-the-air broadcast television which could be decrypted with special equipment. The concept rapidly expanded through the multi-channel transition and into the post-network era. Other parts of the world beyond the United States, such as France and Latin America have also offered encrypted analog terrestrial signals available for subscription. The term is most synonymous with premium entertainment services focused on films or general entertainment programming such as, in the United States, Cinemax, HBO, MGM+, Showtime, and Starz, but such servic ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |