|
Argon2
Argon2 is a key derivation function that was selected as the winner of the 2015 Password Hashing Competition. It was designed by Alex Biryukov, Daniel Dinu, and Dmitry Khovratovich from the University of Luxembourg. The reference implementation of Argon2 is released under a Creative Commons CC0 license (i.e. public domain) or the Apache License, Apache License 2.0, and provides three related versions: *Argon2d maximizes resistance to GPU Password cracking, cracking attacks. It accesses the memory array in a password dependent order, which reduces the possibility of time–memory trade-off (TMTO) attacks, but introduces possible side-channel attacks. *Argon2i is optimized to resist side-channel attacks. It accesses the memory array in a password independent order. *Argon2id is a hybrid version. It follows the Argon2i approach for the first half pass over memory and the Argon2d approach for subsequent passes. recommends using Argon2id if you do not know the difference between the t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
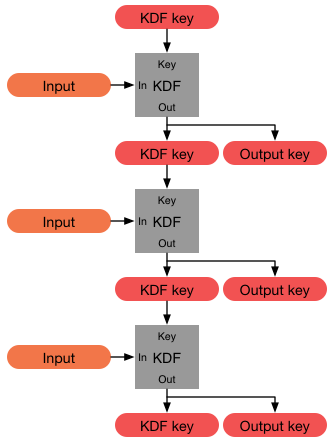
Key Derivation Function
In cryptography, a key derivation function (KDF) is a cryptographic algorithm that derives one or more secret keys from a secret value such as a master key, a password, or a passphrase using a pseudorandom function (which typically uses a cryptographic hash function or block cipher). KDFs can be used to stretch keys into longer keys or to obtain keys of a required format, such as converting a group element that is the result of a Diffie–Hellman key exchange into a symmetric key for use with AES. Keyed cryptographic hash functions are popular examples of pseudorandom functions used for key derivation. History The first deliberately slow (key stretching) password-based key derivation function was called "crypt" (or "crypt(3)" after its man page), and was invented by Robert Morris in 1978. It would encrypt a constant (zero), using the first 8 characters of the user's password as the key, by performing 25 iterations of a modified DES encryption algorithm (in which a 12-b ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Dmitry Khovratovich
Dmitry Khovratovich is a Russian cryptographer, currently a Lead Cryptographer for the Dusk Network, researcher for the Ethereum Foundation, and member of the International Association for Cryptologic Research. Biography Khovratovich, together with Alex Biryukov, developed the Equihash proof-of-work algorithm which is currently being used as consensus mechanism for the Zcash cryptocurrency, and the Argon2 key derivation function, which won the Password Hashing Competition in July 2015. He is the publisher of several cryptanalysis papers for a number of mainstream cyphers, such as the first cryptanalytic attack on full-round Advanced Encryption Standard, AES-192 and AES-256 which is faster than a brute-force attack, an attack on the RadioGatún cryptographic primitive, and also the current best cryptanalysis on Skein, a candidate for the SHA-3 competition. In 2014, he published a research about the deanonymisation of clients in the Bitcoin network, Bitcoin P2P network Selected p ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Alex Biryukov
Alex Biryukov () is a cryptographer, currently a full professor at the University of Luxembourg. Biography His notable work includes the design of the stream cipher LEX, as well as the cryptanalysis of numerous cryptographic primitives. In 1998, he developed impossible differential cryptanalysis together with Eli Biham and Adi Shamir. In 1999, he developed the slide attack together with David Wagner. In 2009 he developed, together with Dmitry Khovratovich, the first cryptanalytic attack on full-round AES-192 and AES-256 that is faster than a brute-force attack. In 2015 he developed the Argon2 key derivation function with Daniel Dinu and Dmitry Khovratovich. Since 1994 Alex Biryukov is a member of the International Association for Cryptologic Research The International Association for Cryptologic Research (IACR) is a non-profit scientific organization that furthers research in cryptology and related fields. The IACR was organized at the initiative of David Chaum at the C ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Password Cracking
In cryptanalysis and computer security, password cracking is the process of guessing passwords protecting a computer system. A common approach (brute-force attack) is to repeatedly try guesses for the password and to check them against an available cryptographic hash of the password. Another type of approach is password spraying, which is often automated and occurs slowly over time in order to remain undetected, using a list of common passwords. The purpose of password cracking might be to help a user recover a forgotten password (due to the fact that installing an entirely new password would involve System Administration privileges), to gain unauthorized access to a system, or to act as a preventive measure whereby system administrators check for easily crackable passwords. On a file-by-file basis, password cracking is utilized to gain access to digital evidence to which a judge has allowed access, when a particular file's permissions restricted. Time needed for password searche ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Blake2
BLAKE is a cryptographic hash function based on Daniel J. Bernstein's ChaCha (cipher), ChaCha stream cipher, but a permuted copy of the input block, XORed with round constants, is added before each ChaCha round. Like SHA-2, there are two variants differing in the Word (computer architecture), word size. ChaCha operates on a 4×4 array of words. BLAKE repeatedly combines an 8-word hash value with 16 message words, truncating the ChaCha result to obtain the next hash value. BLAKE-256 and BLAKE-224 use 32-bit words and produce digest sizes of 256 bits and 224 bits, respectively, while BLAKE-512 and BLAKE-384 use 64-bit words and produce digest sizes of 512 bits and 384 bits, respectively. The #BLAKE2, BLAKE2 hash function, based on BLAKE, was announced in 2012. The #BLAKE3, BLAKE3 hash function, based on BLAKE2, was announced in 2020. History BLAKE was submitted to the NIST hash function competition by Jean-Philippe Aumasson, Luca Henzen, Willi Meier, and Raphael C.-W. Phan. In 2008 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Password Hashing Competition
The Password Hashing Competition was an open competition announced in 2013 to select one or more password hash functions that can be recognized as a recommended standard. It was modeled after the successful Advanced Encryption Standard process and NIST hash function competition, but directly organized by cryptographers and security practitioners. On 20 July 2015, Argon2 was selected as the final PHC winner, with special recognition given to four other password hashing schemes: Catena, Lyra2, yescrypt and Makwa. One goal of the Password Hashing Competition was to raise awareness of the need for strong password hash algorithms, hopefully avoiding a repeat of previous password breaches involving weak or no hashing, such as the ones involving RockYou (2009), JIRA, Gawker (2010), PlayStation Network outage, Battlefield Heroes (2011), eHarmony, LinkedIn, Adobe, ASUS, South Carolina Department of Revenue (2012), Evernote, Ubuntu Forums (2013), etc. Danielle Walker"Black Hat: Crack ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
University Of Luxembourg
The University of Luxembourg (French language, French: ''Université du Luxembourg''; German language, German: ''Universität Luxemburg''; Luxembourgish language, Luxembourgish: ''Universitéit Lëtzebuerg'') is a Public university, public research university in Luxembourg. History The University of Luxembourg was founded in 2003 by combining four existing education and research institutes: the Centre universitaire, Institut supérieur d'études et de recherches pédagogiques, Institut supérieur de technologie, and Institut d'études éducatives et sociales. The university is the only public university in Luxembourg. Description The university has three campuses: the Belval, Luxembourg, Belval Campus, the Kirchberg, Luxembourg, Kirchberg Campus, and the Limpertsberg Campus. The university is governed by a board of governors, a rector, and a university council. The current Rector (academia), rector of the University of Luxembourg is Jens Kreisel. Academics The universit ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Creative Commons CC0
A Creative Commons (CC) license is one of several public copyright licenses that enable the free distribution of an otherwise copyrighted "work". A CC license is used when an author wants to give other people the right to share, use, and build upon a work that the author has created. CC provides an author flexibility (for example, they might choose to allow only non-commercial uses of a given work) and protects the people who use or redistribute an author's work from concerns of copyright infringement as long as they abide by the conditions that are specified in the license by which the author distributes the work. There are several types of Creative Commons licenses. Each license differs by several combinations that condition the terms of distribution. They were initially released on December 16, 2002, by Creative Commons, a U.S. non-profit corporation founded in 2001. There have also been five versions of the suite of licenses, numbered 1.0 through 4.0. Released in November ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Public Domain
The public domain (PD) consists of all the creative work to which no Exclusive exclusive intellectual property rights apply. Those rights may have expired, been forfeited, expressly Waiver, waived, or may be inapplicable. Because no one holds the exclusive rights, anyone can legally use or reference those works without permission. As examples, the works of William Shakespeare, Ludwig van Beethoven, Miguel de Cervantes, Zoroaster, Lao Zi, Confucius, Aristotle, L. Frank Baum, Leonardo da Vinci and Georges Méliès are in the public domain either by virtue of their having been created before copyright existed, or by their copyright term having expired. Some works are not covered by a country's copyright laws, and are therefore in the public domain; for example, in the United States, items excluded from copyright include the formulae of Classical mechanics, Newtonian physics and cooking recipes. Other works are actively dedicated by their authors to the public domain (see waiver) ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Apache License
The Apache License is a permissive free software license written by the Apache Software Foundation (ASF). It allows users to use the software for any purpose, to distribute it, to modify it, and to distribute modified versions of the software under the terms of the license, without concern for royalties. The ASF and its projects release their software products under the Apache License. The license is also used by many non-ASF projects. History Beginning in 1995, the Apache Group (later the Apache Software Foundation) released successive versions of the Apache HTTP Server. Its initial license was essentially the same as the original 4-clause BSD license, with only the names of the organizations changed, and with an additional clause forbidding derivative works from bearing the Apache name. In July 1999, the Berkeley Software Distribution accepted the argument put to it by the Free Software Foundation and retired their ''advertising clause'' (clause 3) to form the new 3-clau ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Side-channel Attack
In computer security, a side-channel attack is a type of security exploit that leverages information inadvertently leaked by a system—such as timing, power consumption, or electromagnetic or acoustic emissions—to gain unauthorized access to sensitive information. These attacks differ from those targeting flaws in the design of cryptographic protocols or algorithms. (Cryptanalysis may identify vulnerabilities relevant to both types of attacks). Some side-channel attacks require technical knowledge of the internal operation of the system, others such as differential power analysis are effective as black-box attacks. The rise of Web 2.0 applications and software-as-a-service has also significantly raised the possibility of side-channel attacks on the web, even when transmissions between a web browser and server are encrypted (e.g. through HTTPS or WiFi encryption), according to researchers from Microsoft Research and Indiana University. Attempts to break a cryptosystem by ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |