|
VPN Service
A virtual private network (VPN) service is a proxy server marketed to help users bypass Internet censorship such as geo-blocking and users who want to protect their communications against data profiling or MitM attacks on hostile networks. A wide variety of entities provide VPN services for several purposes. But depending on the provider and the application, they do not always create a true private network. Instead, many providers simply provide an Internet proxy that uses VPN technologies such as OpenVPN or WireGuard. Commercial VPN services are often used by those wishing to disguise or obfuscate their physical location or IP address, typically as a means to evade Internet censorship or geo-blocking. Providers often market VPN services as privacy-enhancing, citing security features, such as encryption, from the underlying VPN technology. However, users must consider that when the transmitted content is not encrypted ''before'' entering the proxy, that content is visib ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
HTTPS
Hypertext Transfer Protocol Secure (HTTPS) is an extension of the Hypertext Transfer Protocol (HTTP). It uses encryption for secure communication over a computer network, and is widely used on the Internet. In HTTPS, the communication protocol is encrypted using Transport Layer Security (TLS) or, formerly, Secure Sockets Layer (SSL). The protocol is therefore also referred to as HTTP over TLS, or HTTP over SSL. The principal motivations for HTTPS are authentication of the accessed website and protection of the privacy and integrity of the exchanged data while it is in transit. It protects against man-in-the-middle attacks, and the bidirectional block cipher encryption of communications between a client and server protects the communications against eavesdropping and tampering. The authentication aspect of HTTPS requires a trusted third party to sign server-side digital certificates. This was historically an expensive operation, which meant fully authenticated HTTPS conn ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Tracking Cookies
HTTP cookie (also called web cookie, Internet cookie, browser cookie, or simply cookie) is a small block of data created by a web server while a user is browsing a website and placed on the user's computer or other device by the user's web browser. Cookies are placed on the device used to access a website, and more than one cookie may be placed on a user's device during a session. Cookies serve useful and sometimes essential functions on the web. They enable web servers to store stateful information (such as items added in the shopping cart in an online store) on the user's device or to track the user's browsing activity (including clicking particular buttons, logging in, or recording which pages were visited in the past). They can also be used to save information that the user previously entered into form fields, such as names, addresses, passwords, and payment card numbers for subsequent use. Authentication cookies are commonly used by web servers to authenticate that ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Device Fingerprint
A device fingerprint or machine fingerprint is information collected about the software and hardware of a remote computing device for the purpose of identification. The information is usually assimilated into a brief identifier using a fingerprinting algorithm. A browser fingerprint is information collected specifically by interaction with the web browser of the device. Device fingerprints can be used to fully or partially identify individual devices even when persistent cookies (and zombie cookies) cannot be read or stored in the browser, the client IP address is hidden, or one switches to another browser on the same device. This may allow a service provider to detect and prevent identity theft and credit card fraud, but also to compile long-term records of individuals' browsing histories (and deliver targeted advertising or targeted exploits) even when they are attempting to avoid tracking – raising a major concern for internet privacy advocates. History Basic web brows ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
The New York Times
''The New York Times'' (''NYT'') is an American daily newspaper based in New York City. ''The New York Times'' covers domestic, national, and international news, and publishes opinion pieces, investigative reports, and reviews. As one of the longest-running newspapers in the United States, the ''Times'' serves as one of the country's Newspaper of record, newspapers of record. , ''The New York Times'' had 9.13 million total and 8.83 million online subscribers, both by significant margins the List of newspapers in the United States, highest numbers for any newspaper in the United States; the total also included 296,330 print subscribers, making the ''Times'' the second-largest newspaper by print circulation in the United States, following ''The Wall Street Journal'', also based in New York City. ''The New York Times'' is published by the New York Times Company; since 1896, the company has been chaired by the Ochs-Sulzberger family, whose current chairman and the paper's publ ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Consumer Reports
Consumer Reports (CR), formerly Consumers Union (CU), is an American nonprofit consumer organization dedicated to independent product testing, investigative journalism, consumer-oriented research, public education, and consumer advocacy. Founded in 1936, CR was created to serve as a source of information that consumers could use to help assess the safety and performance of products. Since that time, CR has continued its testing and analysis of products and services, and attempted to advocate for the consumer in legislative and rule-making areas. Among the reforms in which CR played a role were the advent of Seat belt legislation, seat belt laws, exposure of the Health effects of tobacco, dangers of cigarettes, and more recently, the enhancement of consumer finance protection and the increase of consumer access to quality health care. The organization has also expanded its reach to a suite of digital platforms. Consumer Reports Advocacy frequently supports environmental causes, inc ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Misinformation
Misinformation is incorrect or misleading information. Misinformation and disinformation are not interchangeable terms: misinformation can exist with or without specific malicious intent, whereas disinformation is distinct in that the information is ''deliberately'' deceptive and propagated. Misinformation can include inaccurate, incomplete, misleading, or false information as well as selective or half-truths. In January 2024, the World Economic Forum identified misinformation and disinformation, propagated by both internal and external interests, to "widen societal and political divides" as the most severe global risks in the short term. The reason is that misinformation can influence people's beliefs about communities, politics, medicine, and more. Research shows that susceptibility to misinformation can be influenced by several factors, including cognitive biases, emotional responses, social dynamics, and media literacy levels. Accusations of misinformation have been used to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Journalist
A journalist is a person who gathers information in the form of text, audio or pictures, processes it into a newsworthy form and disseminates it to the public. This is called journalism. Roles Journalists can work in broadcast, print, advertising, or public relations personnel. Depending on the form of journalism, "journalist" may also describe various categories of people by the roles they play in the process. These include reporters, correspondents, citizen journalists, Editorial board, editors, Editorial board, editorial writers, columnists, and photojournalists. A reporter is a type of journalist who researches, writes and reports on information in order to present using source (journalism), sources. This may entail conducting interviews, information-gathering and/or writing articles. Reporters may split their time between working in a newsroom, from home or outside to witness events or interview people. Reporters may be assigned a specific Beat reporting, beat (area of cov ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Activism
Activism consists of efforts to promote, impede, direct or intervene in social, political, economic or environmental reform with the desire to make Social change, changes in society toward a perceived common good. Forms of activism range from Mandate (politics), mandate building in a community (including writing letters to newspapers), petitioning elected officials, running or contributing to a political campaign, preferential patronage (or boycott) of businesses, and demonstrative forms of activism like rallies, street marches, Strike action, strikes, sit-ins, or hunger strikes. Activism may be performed on a day-to-day basis in a wide variety of ways, including through the creation of art (artivism), computer hacking (hacktivism), or simply in how one chooses to spend their money (economic activism). For example, the refusal to buy clothes or other merchandise from a company as a protest against the Exploitation of labour, exploitation of workers by that company could be cons ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
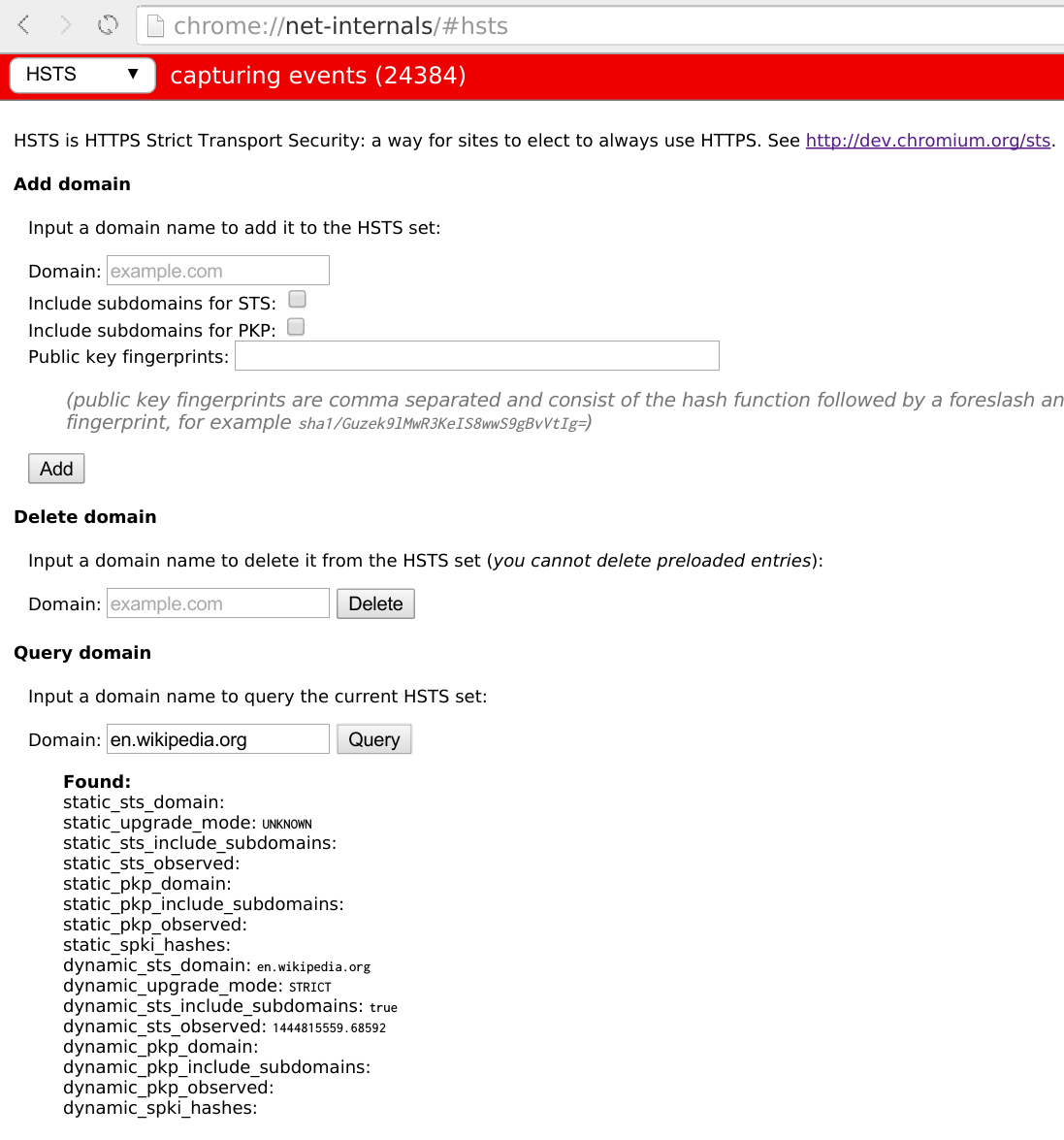
HTTP Strict Transport Security
HTTP Strict Transport Security (HSTS) is a policy mechanism that helps to protect websites against man-in-the-middle attacks such as protocol downgrade attacks and cookie hijacking. It allows web servers to declare that web browsers (or other complying user agents) should automatically interact with it using only HTTPS connections, which provide Transport Layer Security (TLS/SSL), unlike the insecure HTTP used alone. HSTS is an IETF standards track protocol and is specified in . The HSTS Policy is communicated by the server to the user agent via an HTTP response header field named Strict-Transport-Security. HSTS Policy specifies a period of time during which the user agent should only access the server in a secure fashion. Websites using HSTS often do not accept clear text HTTP, either by rejecting connections over HTTP or systematically redirecting users to HTTPS (though this is not required by the specification). The consequence of this is that a user-agent not capable of do ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
5280
''5280'' is an American monthly magazine focused on Denver, Colorado and published by 5280 Publishing, Inc.Circulation statistics , ''Circulation Verification Council'', December 2007. Its name derives from Denver's elevation of 5,280 feet (1609 m / 1 mile) above sea level.Michael Roberts "Altitude Check: As Other Pubs Fall, 5280 Is a Mile High and Rising" , '' Westword'', March 30, 2006. The monthly publication has an audited circulation of 77,027 as of 2011. It is a member of the [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Internet Engineering Task Force
The Internet Engineering Task Force (IETF) is a standards organization for the Internet standard, Internet and is responsible for the technical standards that make up the Internet protocol suite (TCP/IP). It has no formal membership roster or requirements and all its participants are volunteers. Their work is usually funded by employers or other sponsors. The IETF was initially supported by the federal government of the United States but since 1993 has operated under the auspices of the Internet Society, a non-profit organization with local chapters around the world. Organization There is no membership in the IETF. Anyone can participate by signing up to a working group mailing list, or registering for an IETF meeting. The IETF operates in a bottom-up task creation mode, largely driven by working groups. Each working group normally has appointed two co-chairs (occasionally three); a charter that describes its focus; and what it is expected to produce, and when. It is open ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |